Customers with a configured Microsoft Entra ID in Barracuda Cloud Control can now log into Barracuda Cloud Control using their Microsoft Entra ID credentials. This means that customers using multi-factor authentication (MFA) with Microsoft Entra can now use that same process for signing into Barracuda Cloud Control. This provides users with a secure, smooth login experience to Barracuda Cloud Control.
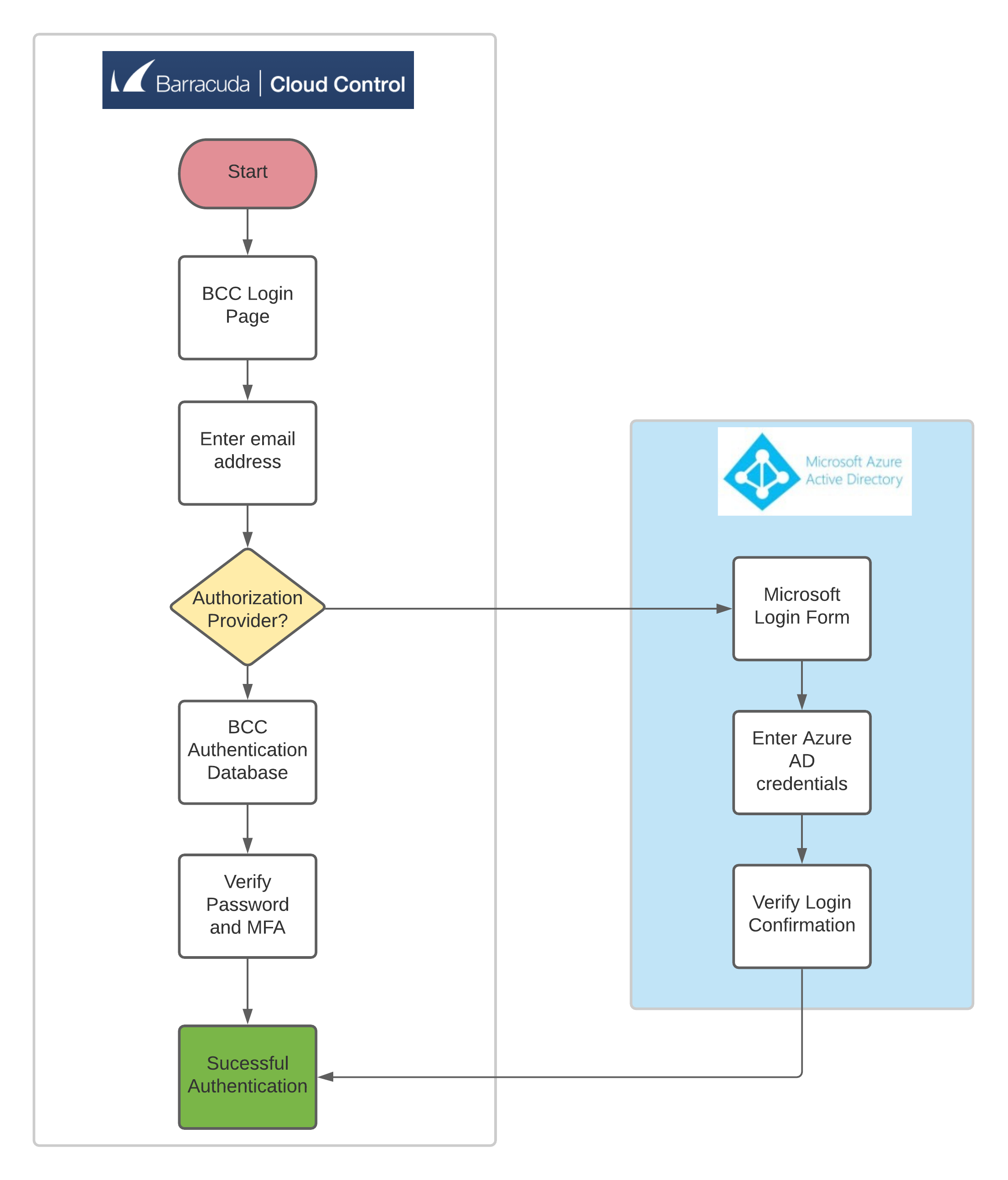
Upon signing into Barracuda Cloud Control, Microsoft Entra users will be redirected to Microsoft for authentication. After users are authenticated with Microsoft, they are signed into Barracuda Cloud Control.
What is Single Sign-On?
With Microsoft Entra ID Single Sign-On (SSO), users sign in once using their primary organizational account to securely access web and SaaS applications. SSO enables users to authenticate applications using their single organizational account.
The SSO environment protects defined resources (websites and applications) by requiring the following steps before granting access:
- Authentication: Authentication verifies the identity of a user using login credentials.
- Authorization: Authorization applies permissions to determine if this user may access the requested resource.
Users are signed into Barracuda Cloud Control automatically if they are already signed into Microsoft Entra. This reduces the number of times a user must enter their credentials into their applications, increasing their productivity. To learn more, see the Microsoft article What is single sign-on (SSO).
How to Configure Single Sign-On with Microsoft Entra ID
The following steps must be done by a Barracuda Cloud Control User Administrator. For more information about users and user privileges in Barracuda Cloud Control, see How to Add Users and Configure Product Entitlements and Permissions.
- Log into Barracuda Cloud Control as the account administrator, and go to Home > Admin > Directories.
- Click the Add Directory button.
- Select Azure Active Directory (now Microsoft Entra ID).
- On the INFO tab, specify a new Directory Name. For example, “Office 365”.
- Click CONNECT TO MICROSOFT to sign into Microsoft and authorize Barracuda Cloud Control to connect to your Microsoft Entra ID.
- Log in with your Microsoft administrator credentials.
- Accept the permissions required for Barracuda Cloud Control to access Microsoft Entra ID.
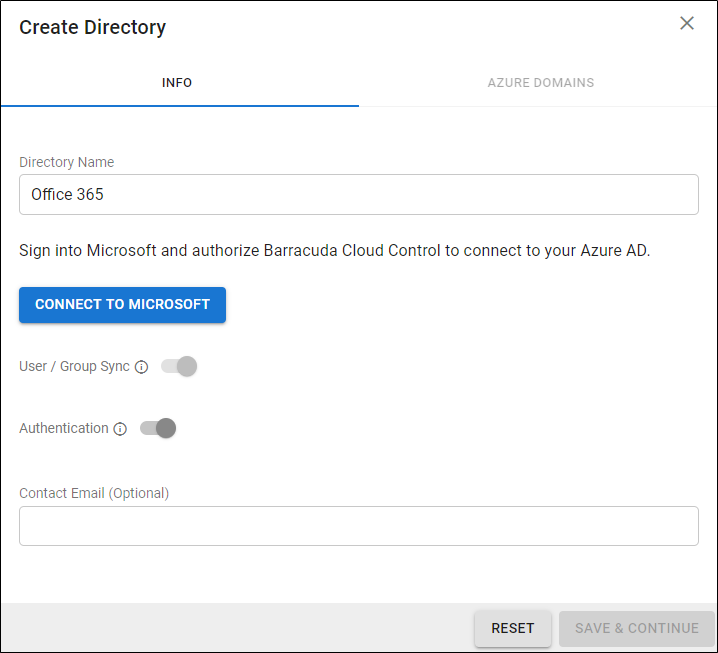
Activate/Enable the Authentication option to have users authenticate to Barracuda Cloud Control using their Microsoft Entra ID credentials. If this option is disabled, users will not be redirected to Microsoft for authentication and will authenticate with Barracuda Cloud Control.
After you are redirected back to Barracuda Cloud Control, your domains are queried and shown on the AZURE DOMAINS tab.
- Click Save.
- After a successful sync of the new directory, users in the directory can now enter their company-provided email address in the Barracuda Cloud Control login page. When Barracuda Cloud Control detects that the email address matches one of the users in the Microsoft Entra ID setup, Barracuda Cloud Control will redirect the user in their web browser to Microsoft to complete authentication and return the user to Barracuda Cloud Control.
User Authentication Flow Chart
Authentication with Barracuda Networks products and Known Issues
At this time, single sign-on support with Microsoft Entra ID is only supported by Barracuda Cloud Control (BCC). All authentication and product access must use the BCC login page and redirect to Microsoft for authentication.
If you access a Barracuda Networks product login page outside of BCC, for example, sentinel.barracudanetworks.com, authentication is only handled using the default BCC authentication method which requires an email address and password. Organizations that have MFA configured with Microsoft will encounter login failures because users do not redirect to Microsoft for authentication, and we are unable to meet Microsoft’s MFA requirement. To avoid this issue, log into BCC at https://auth.barracudanetworks.com/ and then access the desired Barracuda Networks product. If this is not feasible, contact Barracuda Networks Technical Support to apply a patch on your account that bypasses the MFA requirement from Microsoft and allow you to login with just an email address and password.
Troubleshooting
This table contains troubleshooting information on possible issues and how to fix them.
| Failure | Possible Causes | Possible Solutions |
|---|---|---|
| Error after returning from Microsoft when connecting to a new Active Directory. |
|
|
| Error fetching domains after initial connection to Microsoft. |
|
|
| Error returned during syncing of users and groups. |
|
|
Error returned during sign-in attempt for Microsoft Entra ID user. Examples of user-facing errors:
|
|
|
