Using a configuration profile, the administrator can pre-configure the macOS network stack with a VPN profile so that upon installation of CloudGen Access on end user devices, the user is not prompted to approve/accept installation of software or policies. This profile does not represent an MDM enrollment profile, and thus can only be deployed via MDM after a device has been enrolled.
The .mobileconfig configuration profile can be copied and pasted from this page, and can then be uploaded to any MDM solution to be used for deployment. Before deploying this profile to all of your managed devices, test it on a local machine as described below.
Using the Tamperproof feature
To use the Tamperproof feature mentioned below, you must use the CloudGen Access App version 2.2.0 or later. Deploying via MDM when using the Tamperproof feature requires using a specific .mobileconfig configuration profile and, in the case of macOS devices, a plist file is required as well. Both file types can be copied and pasted from this page and stored on your macOS or iOS devices.
Test the Configuration Profile On a Local macOS Device
- Make sure the device does not have CloudGen Access installed.
- If you are using the Tamperproof feature:
- Copy and paste the contents of the macOS configuration file as shown in mobilconfigmacOSTamperproofsection of this article, and name the file .
mobilconfig. Download this configuration profile to your test macOS device. If you are using Tamperproof, the mobilecconfig file is set to prevent uninstall of the VPN profile, and to make sure that the user cannot bypass web filtering by recreating a connection on the VPN when a connection is initiated.
Skip to step 4.
- Copy and paste the contents of the macOS configuration file as shown in mobilconfigmacOSTamperproofsection of this article, and name the file .
- If you are not using the Tamperproof feature, copy and paste the contents of the macOS configuration file as shown in mobilconfigConfigurationNOTTamperproofsection of this article, and name the file .
mobilconfig. Download this configuration profile to your test macOS device. Skip to step 5. - If you are using Tamperproof and macOS, you also need to copy and paste the plistFileTamperproofmacOS and store it under
/Library/LaunchAgents/. Theplistfile is used to restart the CloudGen Access app if it is closed. This file is not required for iOS. - Double-click on the .
mobileconfigfile and follow the installation instructions on screen. This profile is unsigned, so it will be marked accordingly as Unsigned: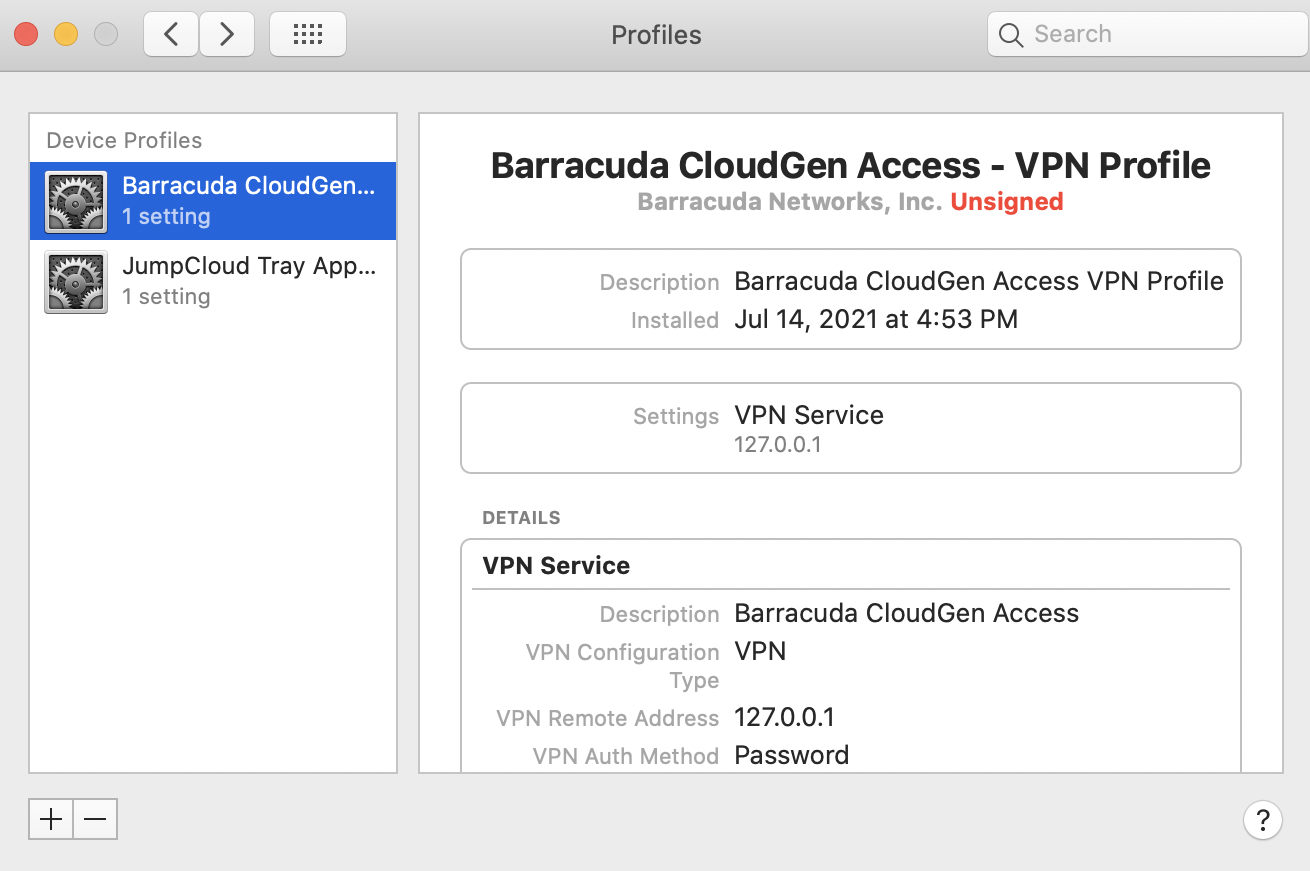
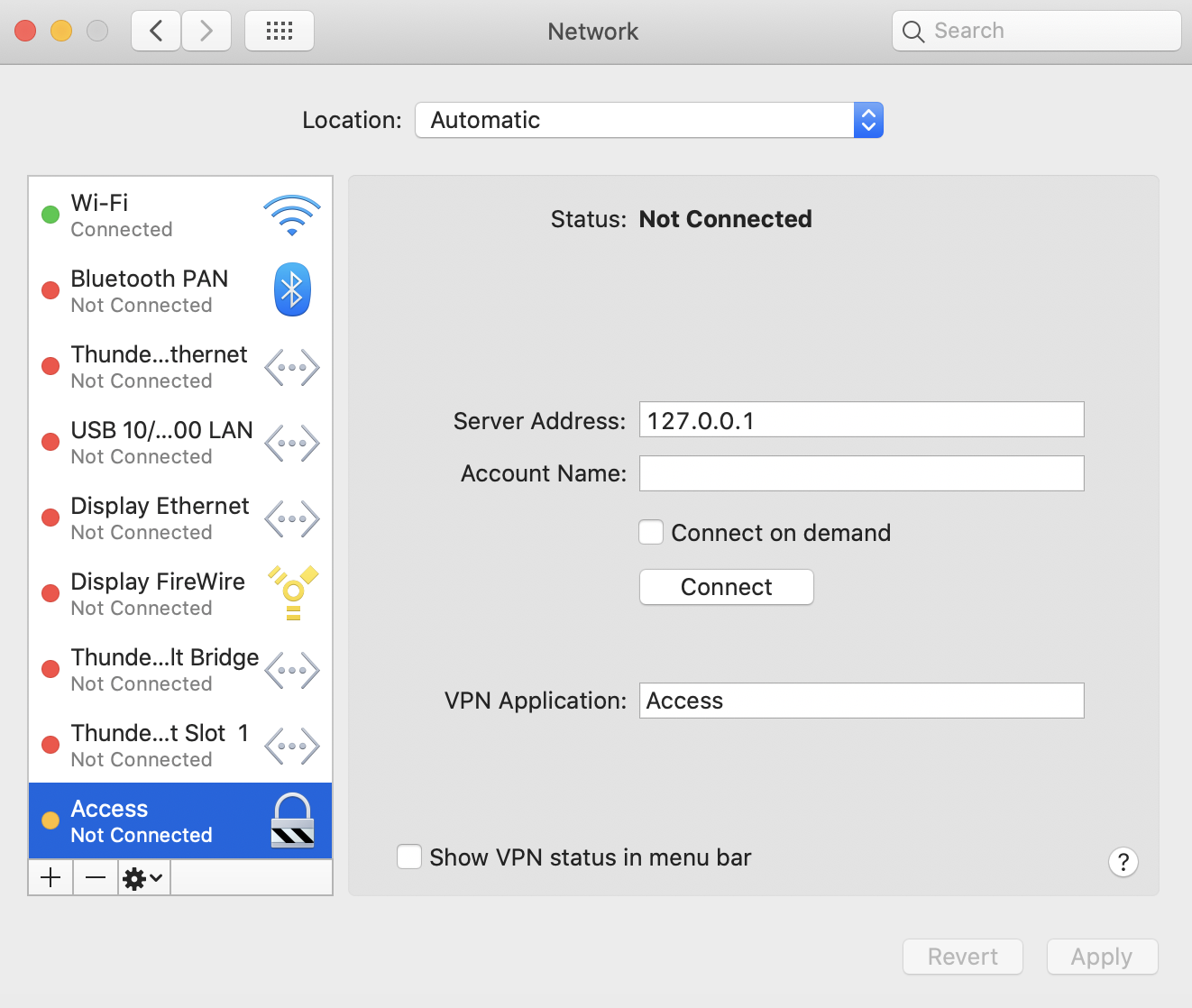
- Check under Settings > Network Preferences for Access to show up as Not Connected.
- Open the App Store and install Barracuda CG Access.
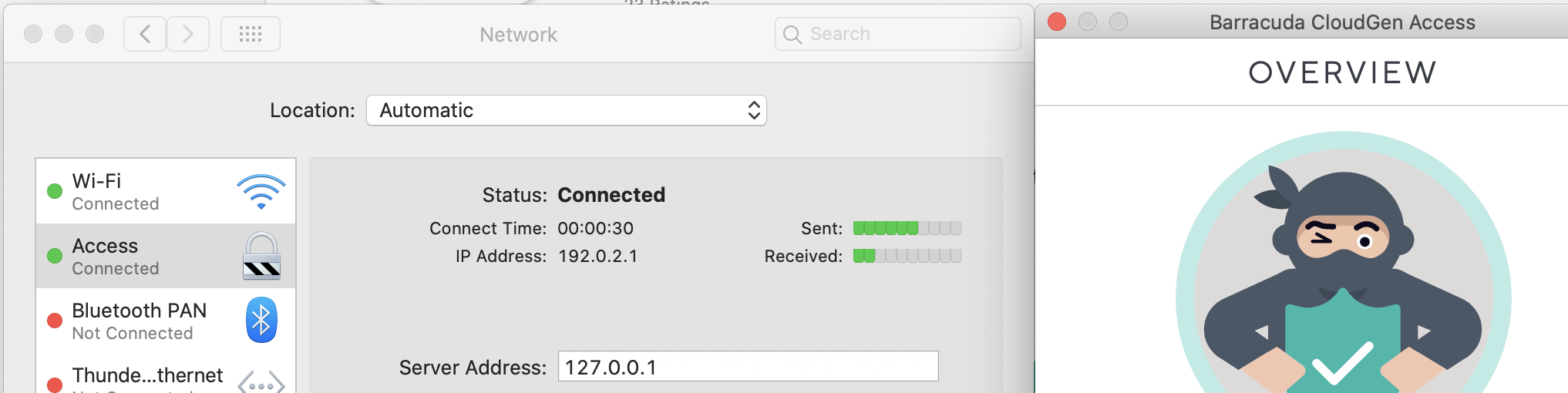
- After installation, check the Network Preferences again for Access. It should now be in Connected state and show as active.
Deploy Using Your MDM
- Make sure that your have enrolled your device for MDM before proceeding (check your MDM provider for device enrollment instructions).
- To create an MDM policy for CloudGen Access, use the payload respective to the target OS from The .mobileconfig Configuration Profiles for macOS and iOS section below. Be sure to choose the correct config file(s) as instructed above, depending on whether or not you want to use the Tamperproof feature for user devices.
- Upload the configuration to the MDM provider in use. Each provider has its own method of inputting the content of this payload, so follow your provider's instructions. For example, both Jamf and JumpCloud MDM providers sign the profile payload before pushing them to target devices.
- Create an MDM policy to use Barracuda CG Access from the App Store to push to the device.
- Apply both policies to the target group of devices.
The .mobileconfig Configuration Profiles for macOS and iOS
The .mobileconfig Configuration Profile for macOS – NOT using the Tamperproof Feature
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>OnDemandMatchAppEnabled</key>
<false/>
<key>PayloadDescription</key>
<string>Configures Barracuda CloudGen Access VPN profile.</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access</string>
<key>PayloadIdentifier</key>
<string>com.apple.vpn.managed.190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadUUID</key>
<string>190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Proxies</key>
<dict/>
<key>UserDefinedName</key>
<string>Access</string>
<key>VPN</key>
<dict>
<key>AuthenticationMethod</key>
<string>Password</string>
<key>OnDemandEnabled</key>
<false/>
<key>ProviderBundleIdentifier</key>
<string>com.fyde.guardian.macos.extension</string>
<key>ProviderType</key>
<string>packet-tunnel</string>
<key>RemoteAddress</key>
<string>127.0.0.1</string>
</dict>
<key>VPNSubType</key>
<string>com.fyde.guardian.macos</string>
<key>VPNType</key>
<string>VPN</string>
<key>VPNUUID</key>
<string>4812F41C-374A-4859-9106-1D881205A63E</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>Barracuda CloudGen Access VPN Profile</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access - VPN Profile</string>
<key>PayloadIdentifier</key>
<string>543CC1DE-AC7A-4227-B45B-2055ACDD0AF4</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>D337E9D4-40FB-4602-8284-F4AEBB298439</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>The .mobileconfig Configuration Profile for iOS – NOT using the Tamperproof Feature
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>OnDemandMatchAppEnabled</key>
<false/>
<key>PayloadDescription</key>
<string>Configures Barracuda CloudGen Access VPN profile.</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access</string>
<key>PayloadIdentifier</key>
<string>com.apple.vpn.managed.190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadUUID</key>
<string>190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Proxies</key>
<dict/>
<key>UserDefinedName</key>
<string>Access</string>
<key>VPN</key>
<dict>
<key>AuthenticationMethod</key>
<string>Password</string>
<key>OnDemandEnabled</key>
<false/>
<key>ProviderBundleIdentifier</key>
<string>com.fyde.guardian.ios.extension</string>
<key>ProviderType</key>
<string>packet-tunnel</string>
<key>RemoteAddress</key>
<string>127.0.0.1</string>
</dict>
<key>VPNSubType</key>
<string>com.fyde.guardian.ios</string>
<key>VPNType</key>
<string>VPN</string>
<key>VPNUUID</key>
<string>4812F41C-374A-4859-9106-1D881205A63E</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>Barracuda CloudGen Access VPN Profile</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access - VPN Profile</string>
<key>PayloadIdentifier</key>
<string>543CC1DE-AC7A-4227-B45B-2055ACDD0AF4</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>2D042D06-9981-46BB-BE0A-A5FBC0631A5D</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>The .mobileconfig Configuration Profile for macOS – USING the Tamperproof Feature
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>OnDemandMatchAppEnabled</key>
<false/>
<key>PayloadDescription</key>
<string>Configures Barracuda CloudGen Access VPN profile.</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access</string>
<key>PayloadIdentifier</key>
<string>com.apple.vpn.managed.190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadUUID</key>
<string>2C0D7638-6071-4ECB-A8D1-CAFAD3F8E679</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>UserDefinedName</key>
<string>Access</string>
<key>VPN</key>
<dict>
<key>AuthenticationMethod</key>
<string>Password</string>
<key>OnDemandEnabled</key>
<integer>1</integer>
<key>OnDemandRules</key>
<array>
<dict>
<key>Action</key>
<string>Connect</string>
<key>InterfaceTypeMatch</key>
<string>WiFi</string>
</dict>
</array>
<key>ProviderBundleIdentifier</key>
<string>com.fyde.guardian.macos.extension</string>
<key>ProviderType</key>
<string>packet-tunnel</string>
<key>RemoteAddress</key>
<string>127.0.0.1</string>
</dict>
<key>VPNSubType</key>
<string>com.fyde.guardian.macos</string>
<key>VPNType</key>
<string>VPN</string>
<key>VPNUUID</key>
<string>4812F41C-374A-4859-9106-1D881205A63E</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>Barracuda CloudGen Access VPN Profile</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access - VPN Profile</string>
<key>PayloadIdentifier</key>
<string>543CC1DE-AC7A-4227-B45B-2055ACDD0AF4</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>A4797083-FC34-4D22-B622-A386141FDAD2</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>RemovalDate</key>
<date>2024-03-21T15:37:24Z</date>
</dict>
</plist>
The .mobileconfig Configuration Profiles for iOS – USING the Tamperproof Feature
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDescription</key>
<string>Configures Barracuda CloudGen Access VPN profile.</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access</string>
<key>PayloadIdentifier</key>
<string>com.apple.vpn.managed.190B5F98-6340-4B70-B2CE-11913B298611</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadType</key>
<string>com.apple.vpn.managed</string>
<key>PayloadUUID</key>
<string>A7B29D29-6CA5-4343-A41A-D2DBEB7BDEE1</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>UserDefinedName</key>
<string>Barracuda Access VPN</string>
<key>VPN</key>
<dict>
<key>AuthenticationMethod</key>
<string>Password</string>
<key>OnDemandEnabled</key>
<integer>1</integer>
<key>OnDemandUserOverrideDisabled</key>
<integer>1</integer>
<key>ProviderBundleIdentifier</key>
<string>com.fyde.guardian.ios.extension</string>
<key>ProviderType</key>
<string>packet-tunnel</string>
<key>RemoteAddress</key>
<string>127.0.0.1</string>
</dict>
<key>VPNSubType</key>
<string>com.fyde.guardian.ios</string>
<key>VPNType</key>
<string>VPN</string>
</dict>
</array>
<key>PayloadDescription</key>
<string>Barracuda CloudGen Access VPN Profile</string>
<key>PayloadDisplayName</key>
<string>Barracuda CloudGen Access - VPN Profile</string>
<!-- identifier for profiles command -->
<key>PayloadIdentifier</key>
<string>543CC1DE-AC7A-4227-B45B-2055ACDD0AF4</string>
<key>PayloadOrganization</key>
<string>Barracuda Networks, Inc.</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<!-- uuid for profiles command -->
<key>PayloadUUID</key>
<string>E6CB1F7E-1083-439C-91EA-DD782BCCBDC7</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>RemovalDate</key>
<date>2024-03-21T15:37:24Z</date>
</dict>
</plist>
The . plist file for macOS USING the Tamperproof Feature
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>KeepAlive</key>
<true/>
<key>Label</key>
<string>com.barracuda.cga</string>
<key>LimitLoadToSessionType</key>
<string>Aqua</string>
<key>ProgramArguments</key>
<array>
<string>open</string>
<string>--wait-apps</string>
<string>/Applications/Access.app</string>
</array>
<key>RunAtLoad</key>
<true/>
</dict>
</plist>Using MDM
The process described here uses the example of JumpCloud, which is similar to Jamf and other MDM providers. First, import the custom profile by either uploading the .mobileconfig profile, or by copying the content from the .mobileconfig profile payload shown above into the provided MDM user interface.
- Follow your MDM provider's instructions to set up the custom configuration profile by first uploading the
.mobileconfigfile to the MDM. - After saving, on the client, go into Settings→Profiles to look for the CloudGen Access VPN profile - it show up as Verified when pushed through the MDM (your MDM provider should sign the profile using the APNS certificate you configured in their portal when setting up the MDM).
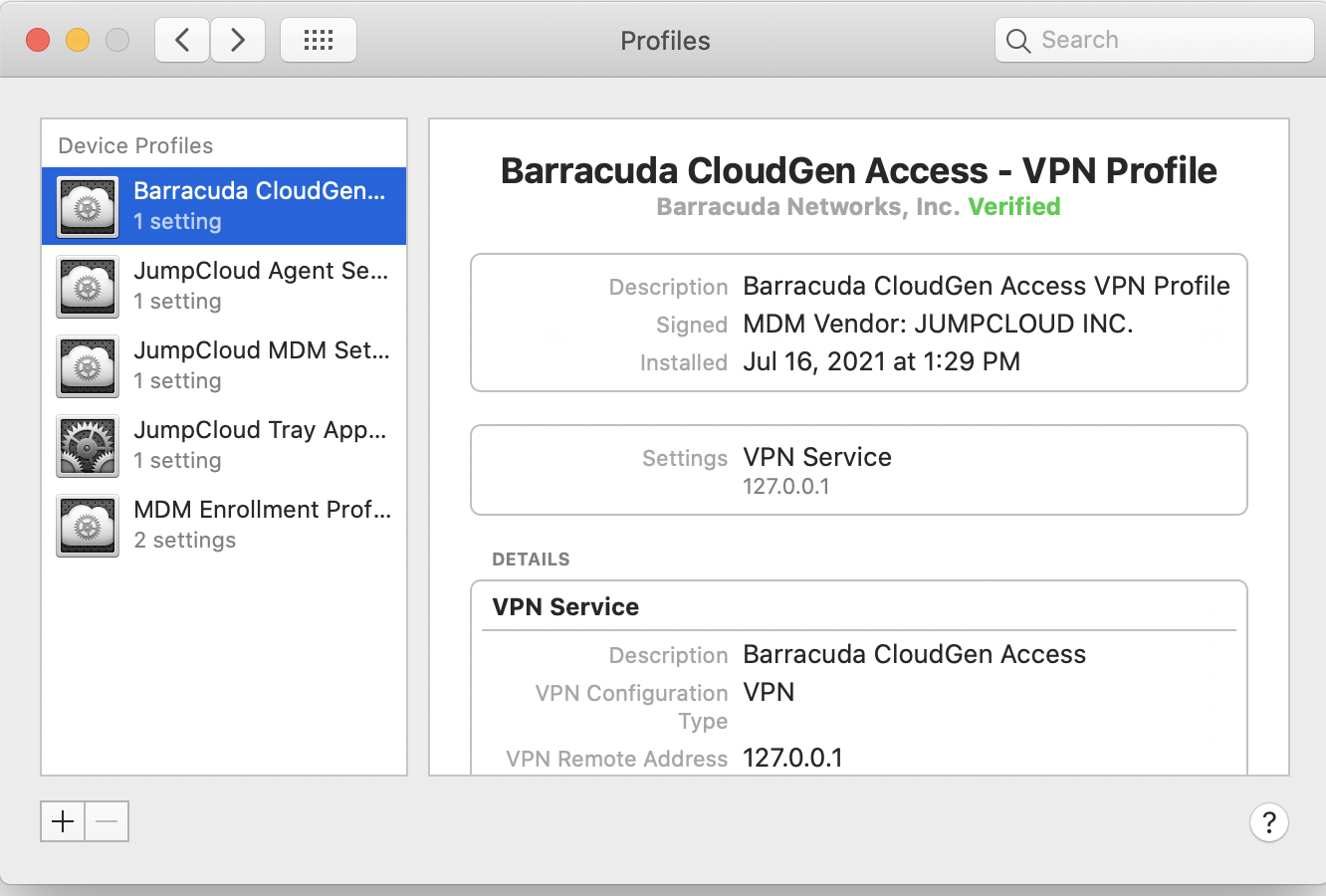
- Open Settings→Network to verify that a new VPN configuration is there with the name Access. It should be in the Not Connected state since the CloudGen Access app has yet to be installed.

- After the CloudGen Access app is installed, it uses this pre-configured configuration profile instead of creating its own so that this VPN will show as Connected as soon as CloudGen Access is started.
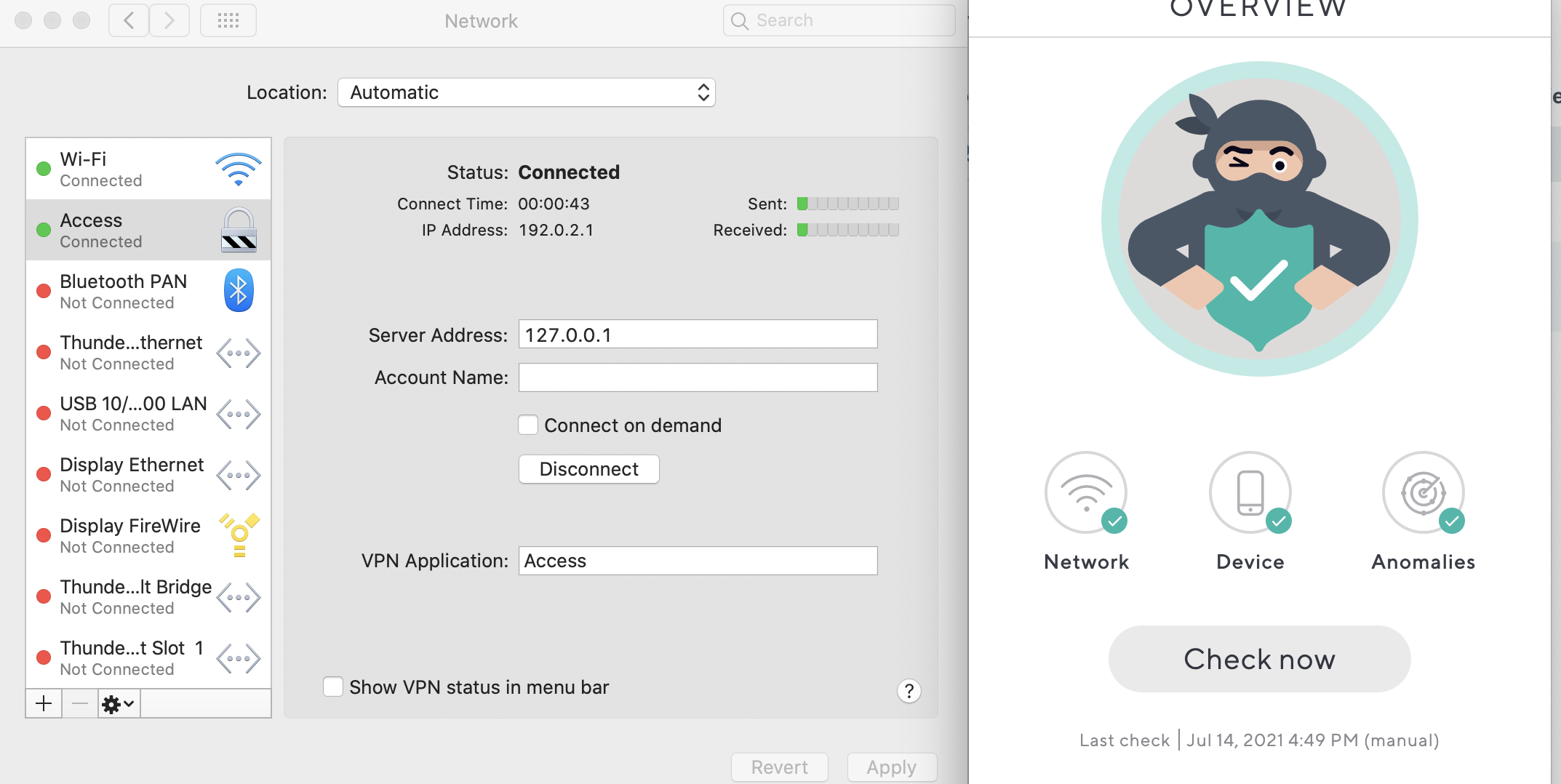
In order to remove the Cloudgen Access VPN configuration from the device, make sure CloudGen Access is uninstalled beforehand.
Pushing an MDM profile to a machine that already has CloudGen Access installed
If a machine already has CloudGen Access installed when you push the new MDM profile, you will temporarily see an Access configuration as well as an Access 1 configuration as duplicates in Settings→Network. This is not a problem; the app will continue to work and the second Access VPN disappears as soon as you restart Cloudgen Access, or upon a reboot. Only one Access VPN Configuration will remain on the machine.
