If you have multiple virtual networks in the same Azure region, you can connect them with a high bandwidth, low-latency connection via virtual network peering. Create a hub and spoke architecture with all spoke VNETs peered to a central VNET containing the CloudGen Firewall VMs. The subnets in the spoke VNETs are associated with an Azure route table using the firewall VM in the central VNET as the next hop device. In this way, all traffic passes through the firewall, thereby allowing you to centrally apply security policies. Using the firewall as the next hop device also allows you to forward traffic between VNETs that are not directly peered with each other. The route table using the firewalls as nexthop routes must be associated with at least one (backend) subnet in the central hub, otherwise the routes will not be rewritten. The hub can contain not only the firewalls, but also additional backend subnets for services shared by all spoke VNETs. By default, you can create up to 10 VNET peerings per virtual network. Contact Microsoft Azure support to increase this limit to up to 50 peerings.
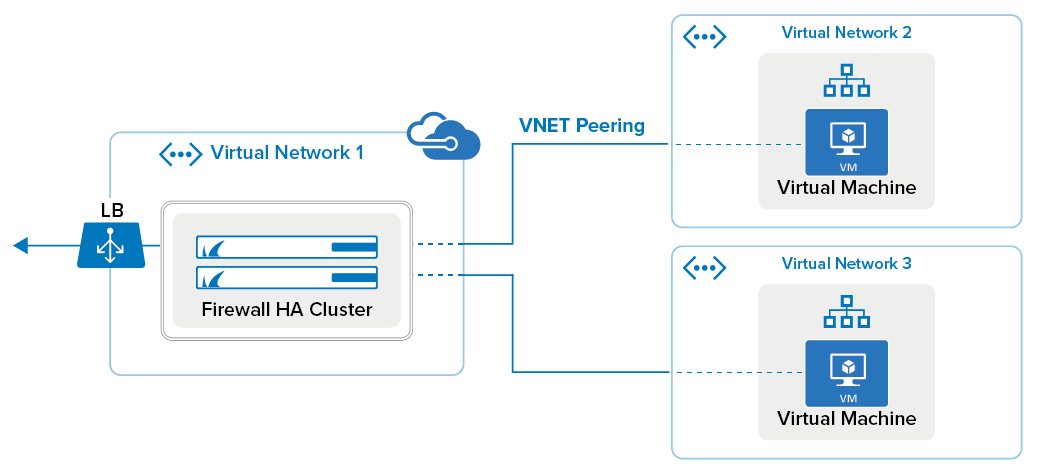
Limitations for VNET Peering with the CloudGen Firewall
- The virtual networks must be in the same Azure region.
- The virtual networks must use the same Azure subscription.
- The networks of the hub VNET and the spoke VNETs may not overlap.
- The Azure route table must be associated with at least one (backend) subnet in the hub VNET for the routes to be updated.
- All virtual networks must use the Azure Resource Manger deployment mode.
Before You Begin
- Deploy a high availability firewall cluster. This virtual network is used as the hub. For more information, see High Availability in Azure.
- Configure Cloud Integration for the firewall cluster. For more information, see Cloud Integration for Azure.
- Create an Azure route table and user defined routes (UDR). For more information, see How to Configure Azure Route Tables (UDR) using Azure Portal and ARM.
Step 1. Create Spoke Virtual Networks
Create the virtual networks that will be peered to the central virtual network.
- Go to the Azure Portal: https://portal.azure.com.
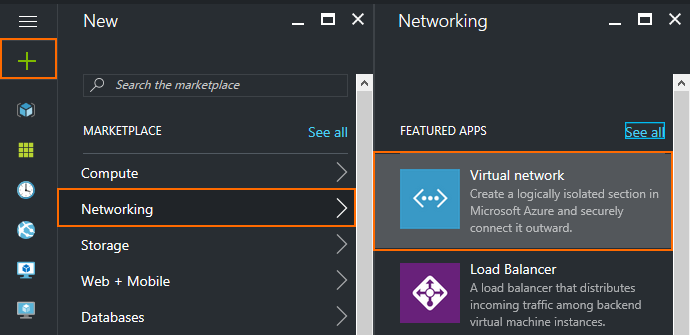
- In the upper left corner, click NEW.
- In the NEW blade, click Networking.
- In the Networking blade, click Virtual network.
- In the Virtual network blade, select Resource Manager from the deployment model drop-down list.
- Click Create.
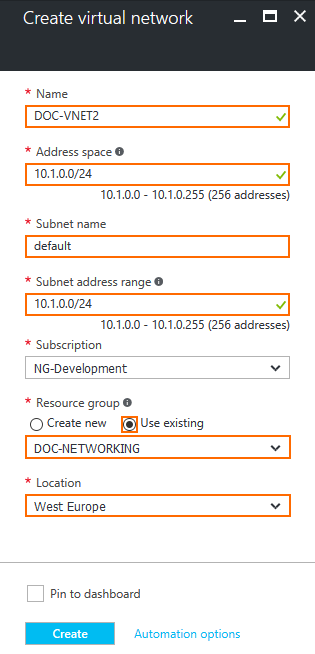
- In the Create virtual network blade, enter:
- Name – Enter a unique name for the virtual network.
- Address space – Use either a large network not overlapping with the other virtual networks, or your on-premises networks.
- Subnet name – Enter a name for the first subnet in the virtual network.
- Subnet address range – Enter the network for the subnet. It must be a subnet of the network entered as the address space.
- Subscription – Select the Azure subscription.
- Resource Group – Click Select Existing and select the resource group the hub virtual network is in.
- Location – Select the location the other virtual networks are in.
- Click Create.
You now have at least two virtual networks in the same resource group. The route table created for the CloudGen Firewall HA cluster must also be in the same resource group.
Step 2. Peer Hub Virtual Network with Spoke Virtual Networks
Create the VNET peering between the hub virtual network and the spoke virtual networks. This will initialize, but not yet connect, the VNET peering. Create a VNET peering for every spoke VNET:
- Go to the Azure Portal: https://portal.azure.com.
- Select the resource group containing the virtual networks.
- Select the Hub VNET.
- In the left menu of the virtual network blade, select Peerings.
- Click Add to add a new peering relationship.
- In the Add peering blade, enter the peering settings:
- Name – Enter a name.
- Peer details – Select Resource manager.
- Subscription – Select the Azure subscription.
- Virtual network – Click and select the spoke VNET you want to peer with.
- Allow virtual network access – Select Enabled to allow access to the virtual network.
- Allow forward traffic – Enable to allow virtual machines to forward traffic
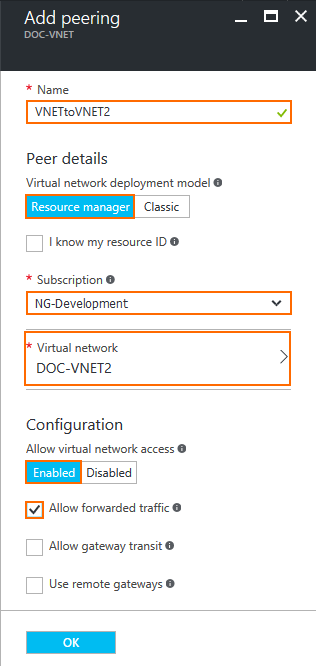
- Click OK.
Repeat this process for every spoke VNET. The VNET Peering Status in the Virtual network blade is now Initiated.
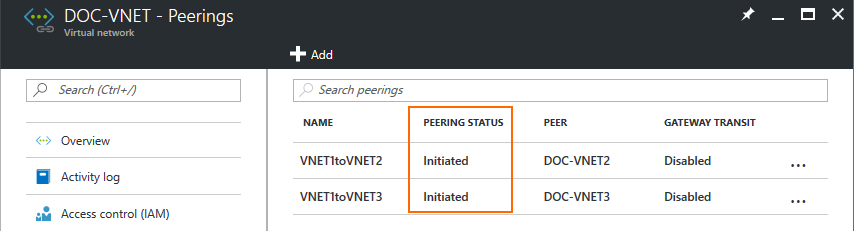
Step 3. Peer Spoke Virtual Networks with the Hub Virtual Network
Create the VNET peering between the spoke virtual networks and the hub virtual networks. This will change the peering state to Connected from Initialized. Repeat this step for every spoke VNET.
- Go to the Azure Portal: https://portal.azure.com.
- Select the resource group containing the virtual networks.
- Select a spoke VNET.
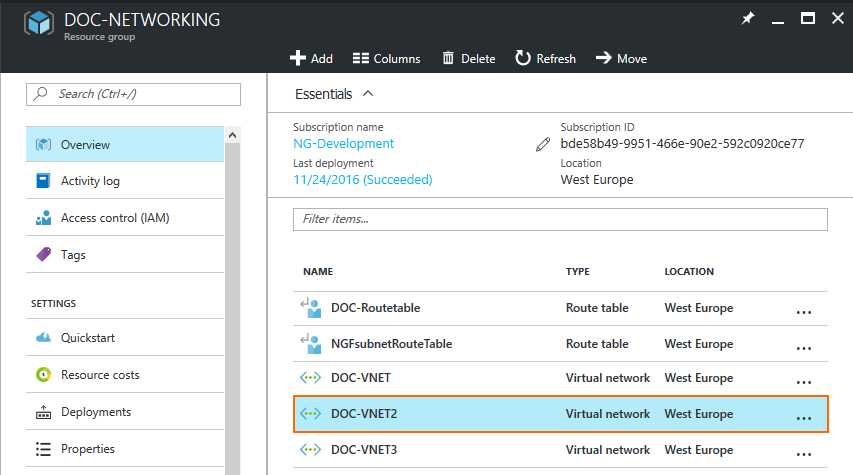
- In the left menu of the virtual network blade select Peerings and click Add.
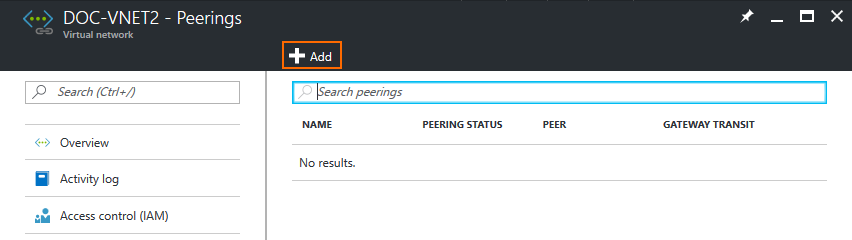
- In the Add peering blade, enter the peering settings:
- Name – Enter a name.
- Peer details – Select Resource manager.
- Subscription – Select the Azure subscription.
- Virtual network – Click and select the hub VNET.
- Allow virtual network access – Select Enabled to allow access to the virtual network.
- Allow forward traffic – Enable to allow virtual machines to forward traffic
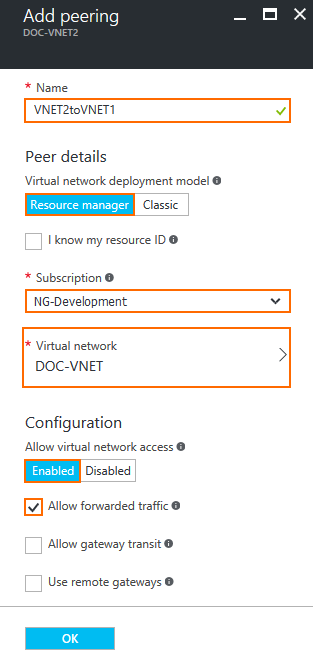
- Click OK.
Repeat this process for every spoke VNET. The VNET Peering Status in the Virtual network blade is now Connected.
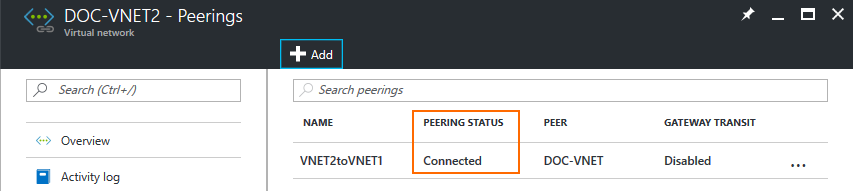
Step 4. Associate the Route Table with Spoke Subnets
To send traffic over the firewall in the peered subnet, associate the Azure route table containing the UDR routes with the subnets. Repeat this for each spoke VNET.
- Go to the Azure Portal: https://portal.azure.com.
- Select the resource group containing the virtual networks.
- Select a spoke VNET.

- In the left menu of the blade, click Subnets.
- Select the subnet. A blade with the subnet name opens.
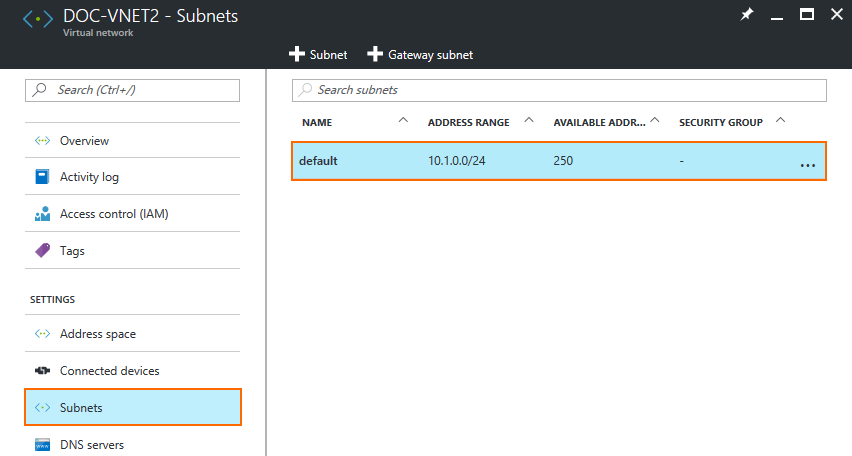
- Click Route Table and select the route table created for the hub VNET.
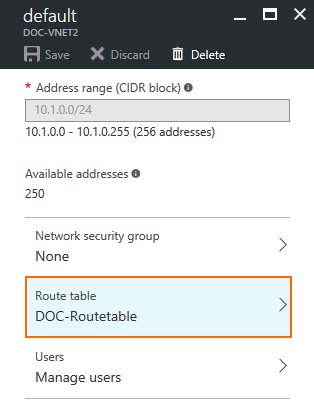
- Click Save.
- Repeat for the other subnets in this virtual network that are allowed to send traffic to other VNETs or need access to the Internet.
Traffic from VMs are now routed over the firewall VM in the hub VNET.
Step 5. Create Access Rules to Allow Traffic between Spoke VNETs
Create access rules to allow traffic between the spoke VNETS
- Log into the primary firewall.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- From the Edit Rule menu in the left menu, click New. The New Rule window opens.
- Enter a Name E.g.,
VNET1-to-VNET2 - In the New Rule window, configure the settings to allow traffic between both systems:
- Action – Select Pass.
- Bi-Directional – Select the check box to apply the rule in both directions.
- Source – Enter the network of the first spoke VNET.
- Service – Select the services allowed to access the tunnel. Default: Any
- Destination – Enter the network of the second spoke VNET.
- Connection Method – Select Original Source IP.
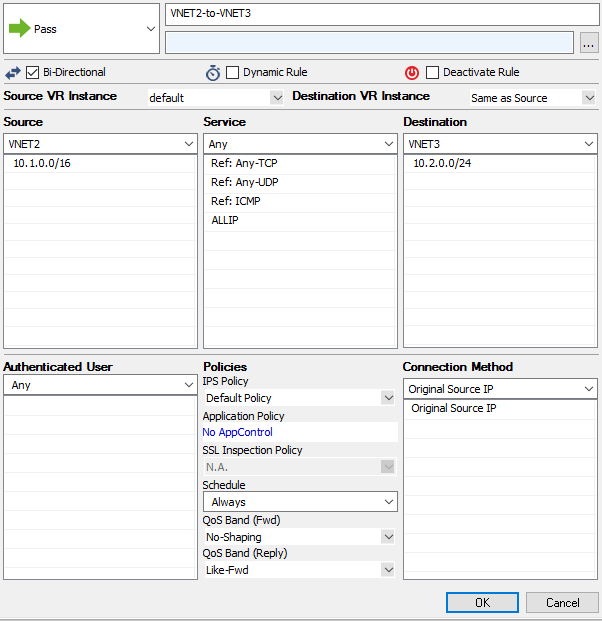
- Click OK.
- Reorder the access rule by dragging it to the correct position in the forwarding firewall's ruleset.
- Click Send Changes and Activate.
The VMs in the first spoke VNET can now access the VMs in the second spoke. Replace this access rule with more specific rules to lock down traffic between the spokes further.
Step 6. (optional) Create an Access Rule to Allow Spoke VNETs Access to the Internet
Create an access rule that allows VMs in the spoke VNETs access to the Internet:
- Log into the primary firewall.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- From the Edit Rule menu in the left menu, click New. The New Rule window opens.
- Enter a Name E.g.,
SpokeVNETs-2-INTERNET - In the New Rule window, configure the settings to allow traffic between both systems:
- Action – Select Pass.
- Source – Enter the networks for the spoke VNETs.
- Service – Select the services allowed to access the tunnel. Default: Any
- Destination – Select Internet.
- Connection Method – Select Dynamic NAT.
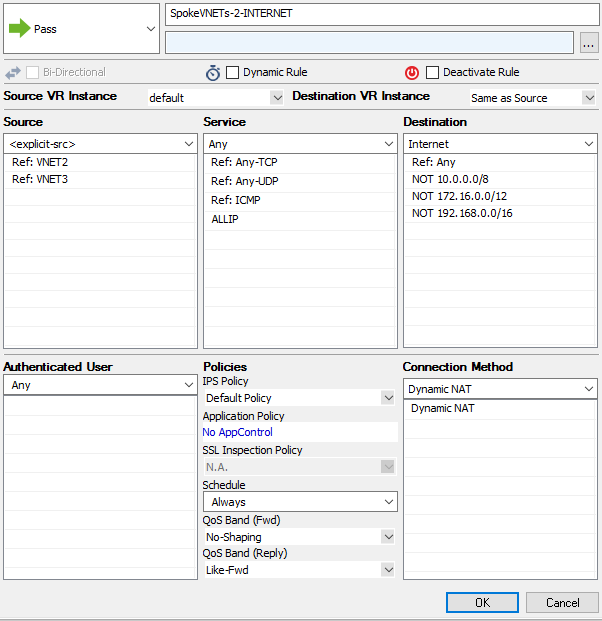
- Click OK.
- Reorder the access rule by dragging it to the correct position in the forwarding firewall's ruleset.
- Click Send Changes and Activate.
All traffic from the subnets in the spoke VNETs is now passing through the high availability firewall cluster in the hub VNET.
