For the firewall instance running in the Google Cloud to be able to access the API and to use the gcloud tool installed on the firewall, you must create a service account and assign a custom role to the account.
Step 1. Create a Custom Role
Create a custom role that includes all permissions needed by your API calls / gcloud commands running on the firewall instances. The permissions included in this step are sufficient to run the High Availability route rewriting script.
- Log into the Google Cloud Platform: https://console.cloud.google.com/
- Click the hamburger menu in the upper-left corner.
- Click IAM & admin.
- In the left menu, click Roles.
- Click Create role.
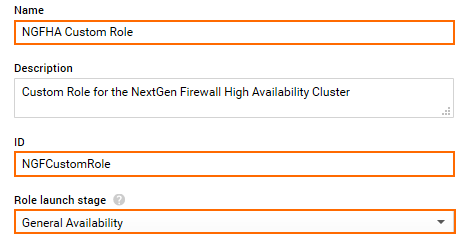
- Configure the role:
- Name – Enter the name.
- ID – Enter a unique ID.
- Role launch stage – Select General Availability.
- Click Add Permissions.
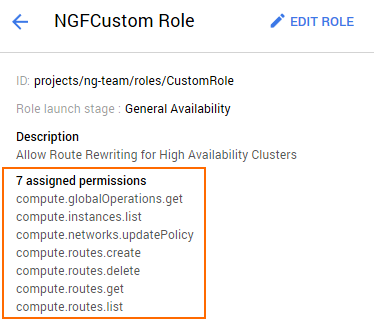
- Filter for compute and routes, and add the following permissions from the list:
- compute.routes.create
- compute.routes.delete
- compute.routes.get
- compute.routes.list
- compute.instances.list
- compute.networks.updatePolicy
- compute.globalOperations.get
- Click Add Permissions.
- Click Create.
The role now lists all assigned permissions.
Step 2. Create a Service Account
Create the service account and assign the custom role to it.
- Log into the Google Cloud Platform: https://console.cloud.google.com/
- Click the hamburger menu in the upper-left corner.
- Click IAM & admin.
- In the left menu, click Service accounts.
- Click Create Service Account.
- Configure the Service account:
- Service account name – Enter a unique service account name.
- Role – Select the custom role created in Step 1 from the drop-down menu. Custom roles are in the Custom category.
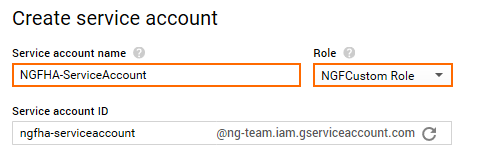
- Click Create.
You can now use the service account to launch your High Availability cluster in the cloud.
