The Detected Common Vulnerabilities & Exploits (CVEs) page provides a way to identify the security vulnerabilities that impact your devices so you can easily research and address them.
This page of the Barracuda Security Scanner doesn't provide an additional scan or find additional vulnerabilities. Instead, it organizes the results of the existing scan, specifically the Patch Security results, and expresses them in terms of MITRE Corporation's defined CVEs. Expressing the scan results in terms of CVEs means you can:
- Identify the existing vulnerabilities
- Assess the severity of each vulnerability
- Easily find mitigation strategies
This page lets you discover more information on:
- Which specific vulnerabilities affect each device
- The severity of the vulnerability
- Which devices are affected
- The affected vendor and product
What are CVEs?
CVEs stands for Common Vulnerabilities and Exposures, which is a program from The MITRE Corporation with the following purpose of identifying, defining, and cataloging publicly disclosed cybersecurity vulnerabilities. CVEs define specific cybersecurity vulnerabilities or exposures and catalog them to streamline the vulnerability disclosure process and to give security professionals common language for discussion.
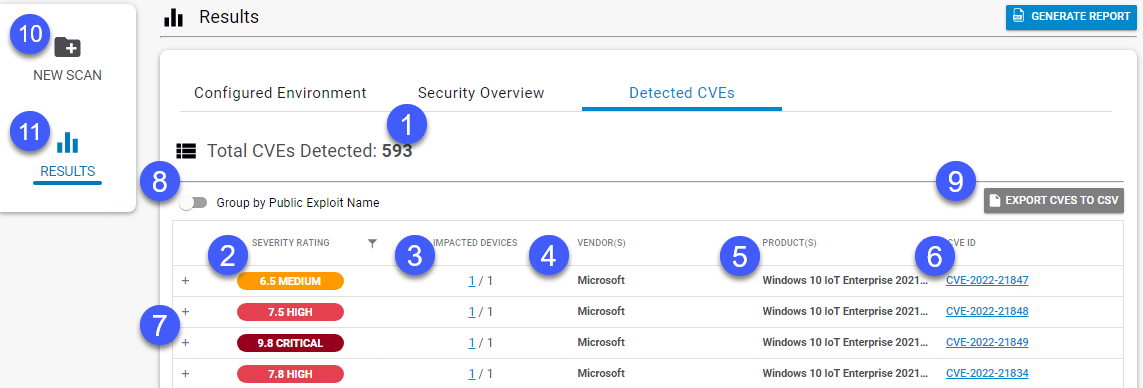
- This area displays the total number of CVEs detected on your devices.
This icon's color, number, and label indicate the severity of the CVE. The highest severity is 10, the lowest is 0. Possible severities are: Critical, High, Medium, and Low. Reserved indicates the severity is unknown. Not Available indicates the severity is not available. Click the filter icon
 to sort or filter on these severities.
to sort or filter on these severities.- The Impacted Devices column indicates how many devices are affected, as a fraction of the total assets scanned. Click the link for more details on the impacted devices, including the device names, their Operating Systems, and their IP Addresses.
- The Vendor column displays the name of the software publisher. Click the filter icon
 to sort or filter on vendor name, including filtering on partial names, excluding names, and other Boolean filtering options.
to sort or filter on vendor name, including filtering on partial names, excluding names, and other Boolean filtering options. - The Product column displays the name of the impacted product or products. Click the filter icon
 to sort or filter on product name, including filtering on partial names, excluding names, and other Boolean filtering options.
to sort or filter on product name, including filtering on partial names, excluding names, and other Boolean filtering options. - The CVE ID column displays the CVE ID. Click this ID to go to The MITRE Corporation's published report on the CVE.
- Click the plus icon
 next to any row in the table to see a description of the CVE, any potential exploits, and any missing patches that are associated with the CVE.
next to any row in the table to see a description of the CVE, any potential exploits, and any missing patches that are associated with the CVE. This slider lets you group CVEs by their Public Exploit Name. A public exploit name is the name the exploit is commonly called, as opposed to the official CVE name. For example, CVE-2021-44228 is known to the public as "Log4j". Many CVEs do not have public exploit names. When you group by public exploit name, CVEs without a public exploit name are listed under CVEs Without Public Name .
- Click Export CVEs to CSV to output a comma separated file of the table that you can open in a spreadsheet application. If the Group by Public Exploit Name is On, the CSV is organized by Public Exploit Names.
- Click New Scan to return to the New Scan/Configuration page and run another scan.
- Click Results to return to the Results page, which displays the scan results organized by categories.
