Barracuda SecureEdge allows administrative users with appropriate permissions to configure policies to protect internal resources and to secure access from and to the company network. Policies, rules, and access control lists are (pre-)defined rules for handling network traffic and are centrally managed throug https://se.barracudanetworks.com. Policies are automatically applied to all site appliances. Since updates are pulled from the site appliances in 1-minute intervals, it might take up to 8 minutes until the updates apply.
Network Policies
Configure network policies to allow or deny access based on source and destination. You can create access control lists (ACLs) for networks, users, and sites, using either predefined or custom applications. For more information on custom applications, see How to Create Custom Applications. If you want to select users or groups in the policies, you must first connect your Azure Active Directory. For more information, see How to Connect Your Azure Active Directory with Barracuda Cloud Control.
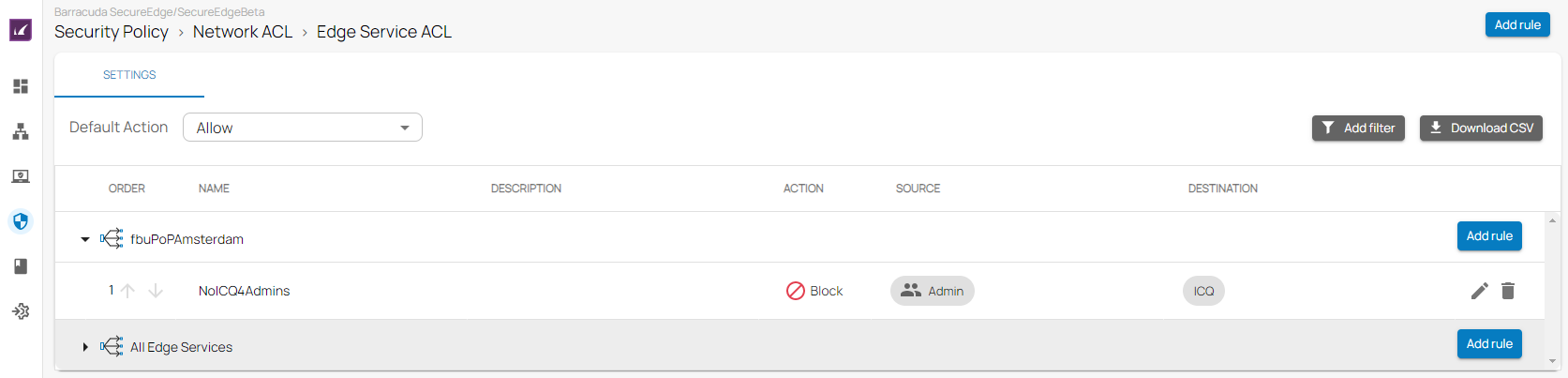
The following access control lists are available:
- Edge Service ACL
- Site ACL
For more information, see Network Policies.
SD-WAN Policies
Barracuda SecureEdge provides a default configuration for SD-WAN Policies using a predefined application database to cover the most common use cases. For the default configuration, Barracuda Networks has defined an SLA for each application and protocol. The SLA decides how the application is routed according to its needs. You can create explicit policies to change the default behaviour, or you can create additional policies specifically matching your requirements. In addition, you can add applications to the database using custom applications, which allow you to extend the predefined application database used by both the SD-WAN policies and security policies.
The matching algorithm works as follows:
- An application is detected. Custom application definitions take precedence over predefined applications. For more information, see How to Create Custom Applications.
- If there is an explicit policy for that application, the explicit policy is used. For more information, see SD-WAN Policies.
- Otherwise, the algorithm looks up the SD-WAN category and applies the Quality of Service / intelligent routing defined in the policy.
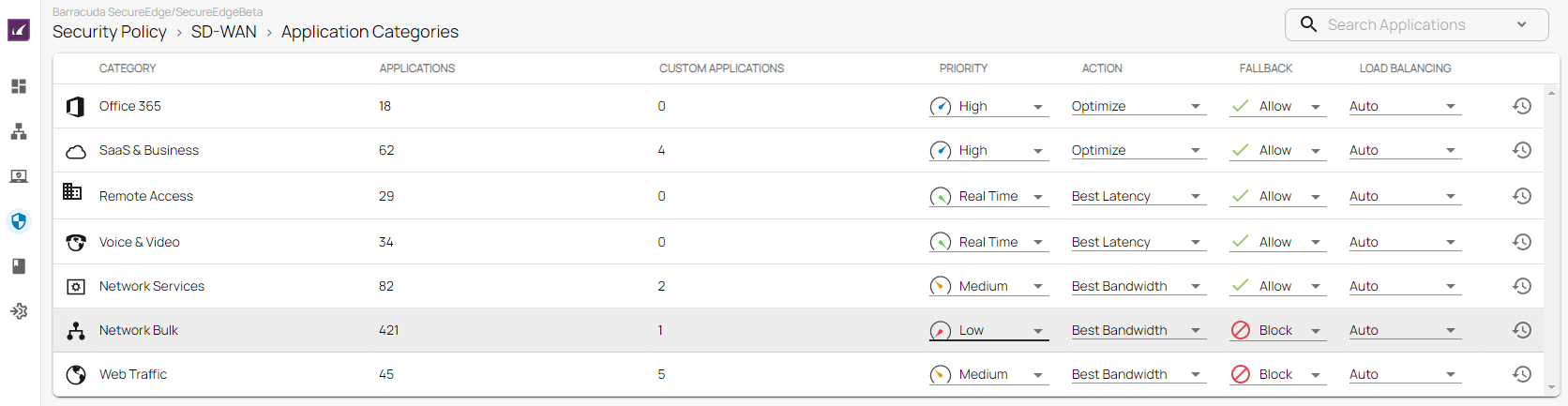
The following SD-WAN options are available:
For more information, see SD-WAN Policies.
Security Policies
The default action of a security policy can, for example, be either to block all and define exceptions that are allowed, or to allow all and define exceptions that are blocked. You can change the default action for all security polices individually. For example, web filtering is set to allow all and define exceptions that are blocked, and ACL is set to block all with exceptions that are allowed.
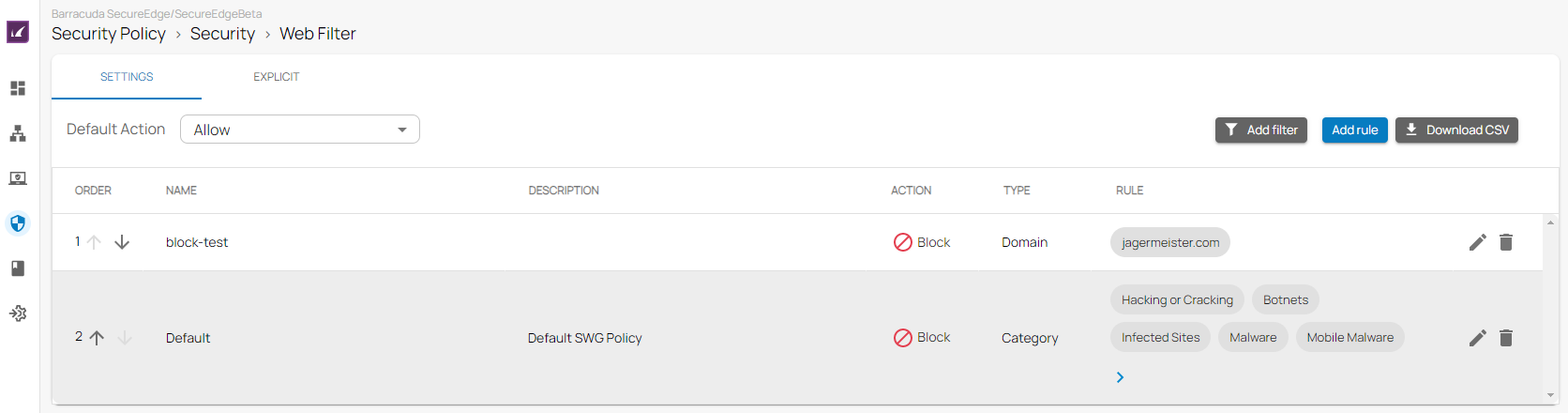
The following security policies are available:
- Web Filter
- Advanced Threat Protection
- Malware
- SSL Inspection
- IPS
Some policies come with preconfigured default rules. In this case, explicit rules have precedence over predefined ones.
The matching algorithm of the rules works as follows:
- All rules (explicit and default) apply top down. That means the first rule in the list that matches applies. Rules below the first match will not apply.
- First, the explicit rules are searched for matches. If there is an explicit rule that matches, this explicit rule will be used.
- Otherwise, the default rules are searched, and if there is a rule that matches, this rule will be used.
For more information, see Security Policies.
