With Microsoft Entra ID (formerly Azure Active Directory) Single Sign-On (SSO), users sign in once using their primary organizational account to securely access web and SaaS applications. SSO enables users to authenticate to applications using their single organizational account.
The SSO environment protects defined resources (websites and applications) by requiring the following steps before granting access:
- Authentication: Authentication verifies the identity of a user using login credentials.
- Authorization: Authorization applies permissions to determine if this user may access the requested resource.
Adding the Email Gateway Defense app to your enterprise applications list in the Azure Portal allows end users to sign in using their Microsoft Entra ID credentials. This will also avoid consent screens appearing for users during the login process.
Once logged in, users can view their quarantine messages.
Add the Email Gateway Defense App to Your Enterprise Apps in the Azure Portal
Adding the Email Gateway Defense App to your enterprise applications list in the Azure Portal allows you to grant consent for the entire organization. This will also avoid consent screens appearing for users during the login process. For more information, see User Consent Flows.
- Log into the Microsoft Entra admin center (formerly Azure Active Directory) as a global administrator for the directory.
- Navigate to Enterprise applications > All applications. Select New application.
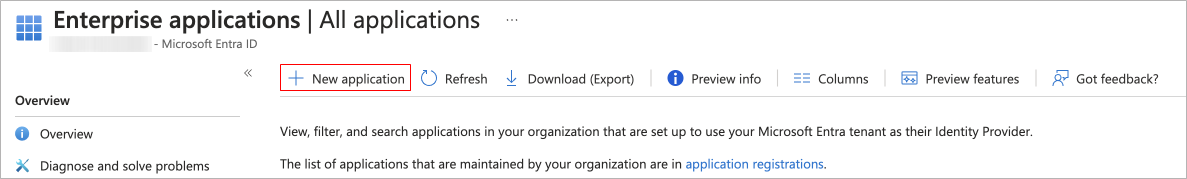
- On the Browse Microsoft Entra Gallery pane, type in "Email Gateway Defense" in the search box. Select Barracuda Email Gateway Defense.
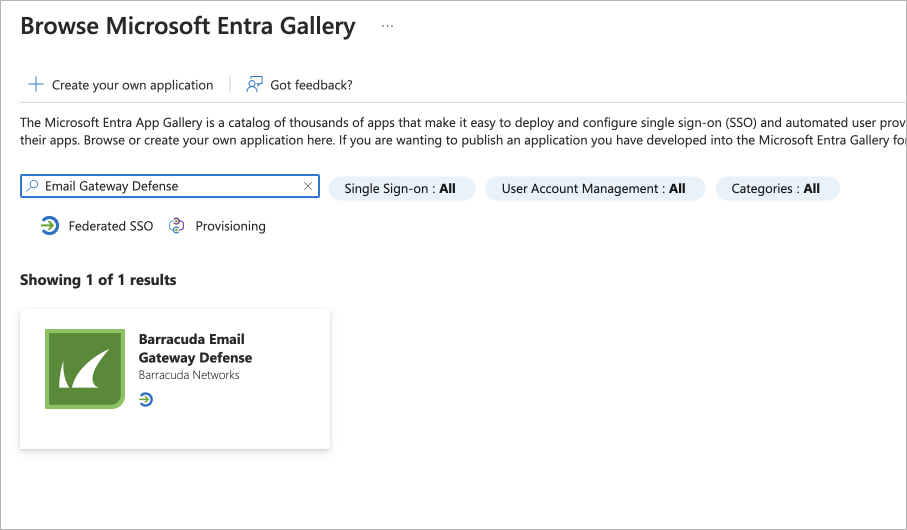
- Click Sign up for Barracuda Email Gateway Defense.
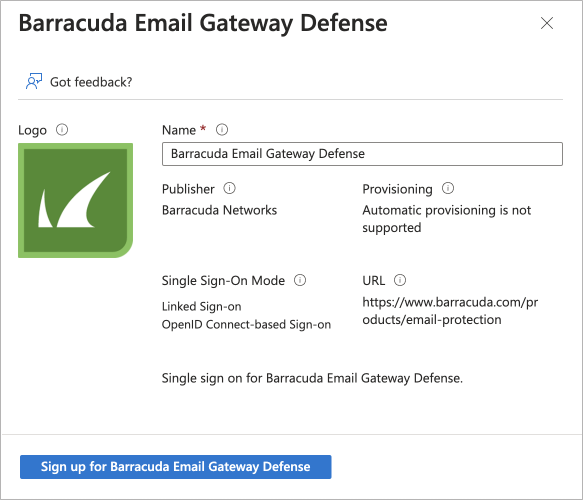
You will be prompted to sign into your Microsoft 365 account.
Check the Consent on behalf of your organization box. Click Accept.
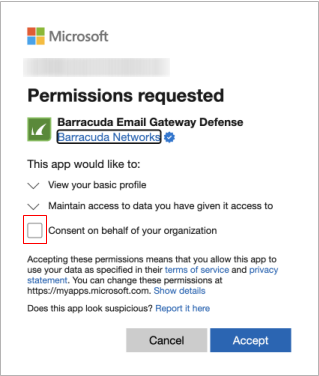
You are redirected to the Email Gateway Defense end user page where you are logged into Email Gateway Defense.
To check that the app is added to your enterprise applications, go back to the Enterprise applications > All applications page and refresh the page. You should now see the app in the list.
Access the Email Gateway Defense App in the My Apps Portal
By adding the Email Gateway Defense app to the My Apps portal, users can access the app via the My Apps portal with a single click once authenticated with their Azure credentials. Note that only the applications to which a user has access to will appear in the My Apps portal. Access to apps in the portal is subject to the access permissions established by your organization. For more information on the My Apps portal, see https://learn.microsoft.com/en-us/entra/identity/enterprise-apps/myapps-overview.
- Log into https://myapps.microsoft.com with Microsoft Entra ID credentials.
The Apps page appears with the apps available for your account, including the app.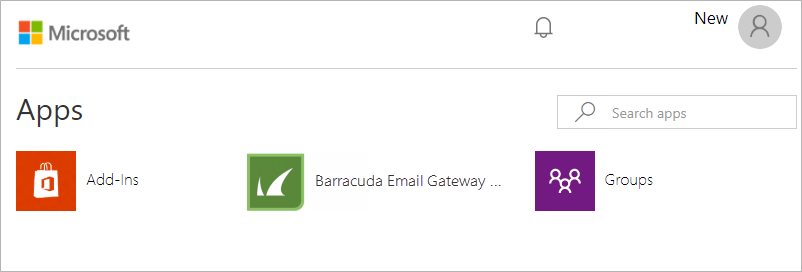
- Click the Barracuda Email Gateway Defense app.
Remove the Email Gatewway Defense App
To remove the Barracuda Networks app in Microsoft Entra ID:
- Log into the Microsoft Entra admin center (formerly Azure Active Directory) as a global administrator for the directory.
- Navigate to Enterprise applications > All applications.
- On the Enterprise applications - All applications pane, you see a list of the apps you can manage. Select Email Gateway Defense.
- Select Manage > Properties in the left menu.
- At the top of the Properties pane, select Delete, and then select Yes to confirm you want to delete the application from your Microsoft Entra tenant.
User Consent Flows
End users will see one of the below user consent flows based on the security consent policies set in the Azure Portal by the administrator. For more information, see Viewing and Changing Consent Policies in the Azure Portal.
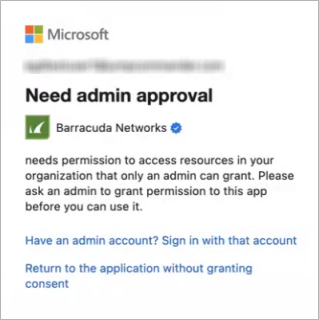
Do not allow user consent – Users will be blocked from granting consent to any application. Users can sign into applications that administrators have granted consent to on their behalf, but they cannot consent to new permissions to applications on their own. Users will need to contact their administrator to grant access. They will not be able to access the application until the administrator grants consent.
Allow user consent for apps from verified publishers, for selected permissions (Recommended) – Users will see the consent prompt to accept the permissions only for an application from a verified publisher or an application added to your tenant. It is safe to click Accept to gain access to the application.
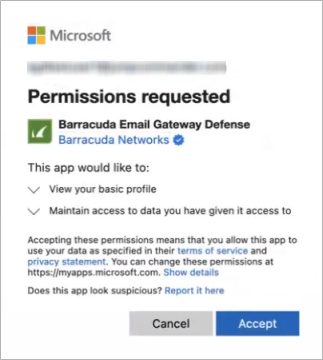
Allow user consent for apps – Users will see the consent prompt to accept the permissions for any application. Users can consent to any permissions for any application, regardless of publisher or status (verified or unverified).

End users are now logged into Email Gateway Defense and can see their Message Log page.
