Conditional access policies are, at their most basic, an if-then statement combining signals to make decisions, and to enforce organization policies. Zero Trust Access to Microsoft 365 applications can be configured by integrating CloudGen Access with the Microsoft Entra Conditional Access feature. Note that conditional access requires an extended Azure license (Microsoft Entra ID Premium).
With conditional access on, the end user will see an error from Microsoft when accessing M365 without proxying the traffic through CloudGen Access. This is to prevent access that do not meet CloudGen Access policies.
This deployment option requires a proxy with a public IP address. You need to deploy and host proxy.
Create a named location.
Locations are found under Protection > Conditional Access > Named locations.Create a location with proxy IP addresses.
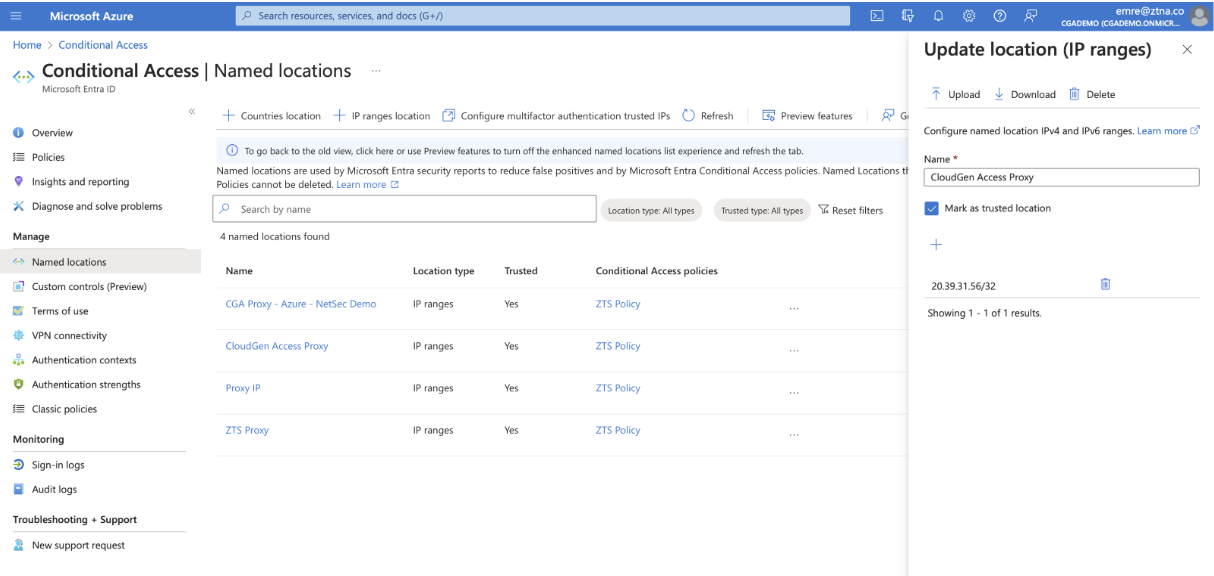
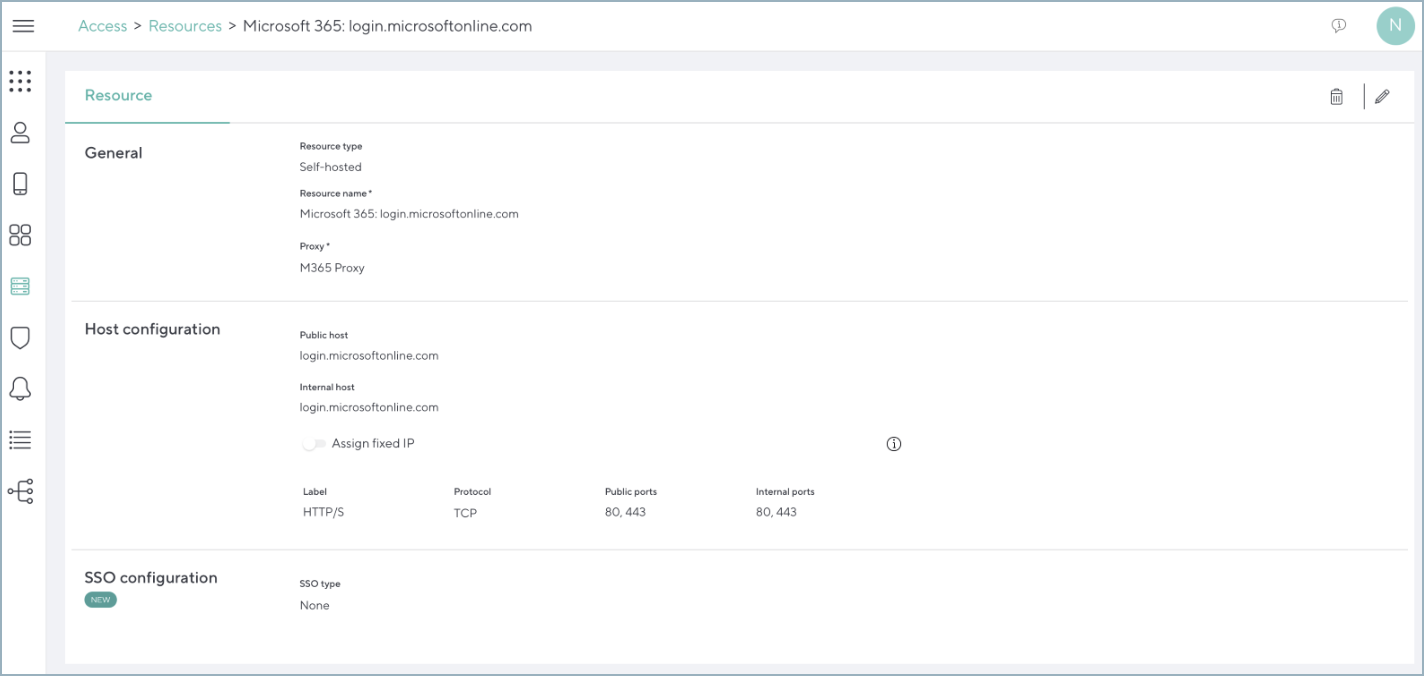
Create the below resources.
Create self-hosted web resources from the CloudGen Access management console:*.aadg.akadns.net
*.msidentity.com
outlook.office365.com
*.aadg.trafficmanager.net
login.microsoftonline.com
Login.windows.net
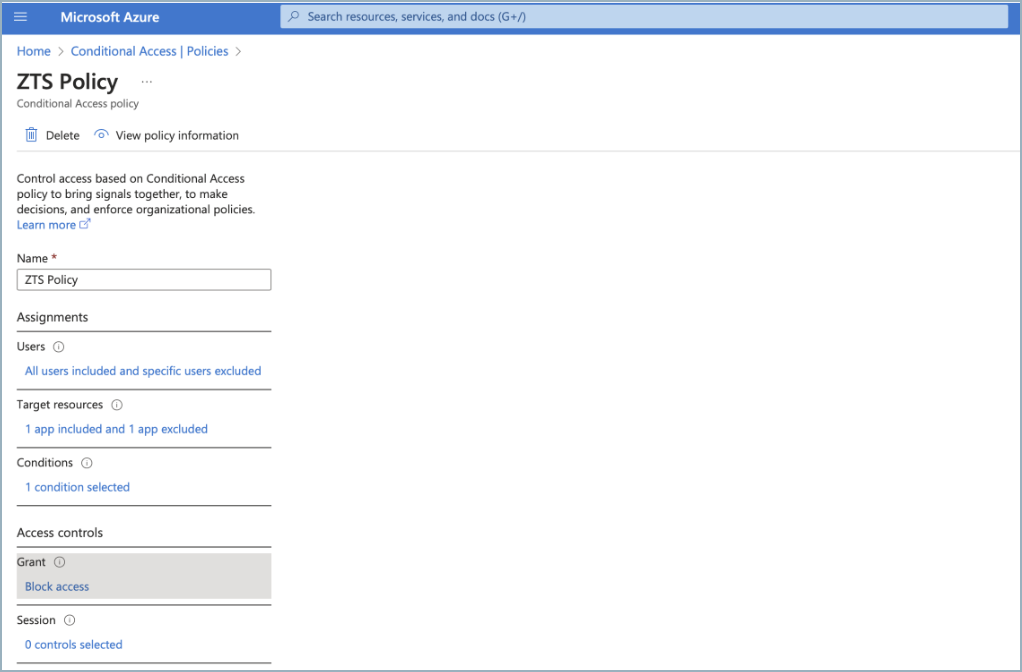
Create a policy.
Example policy: This policy blocks access to Microsoft 365 applications from all locations, excluding the “named location (Proxy IP)” for all or selected users and groups.Select users of the policy.
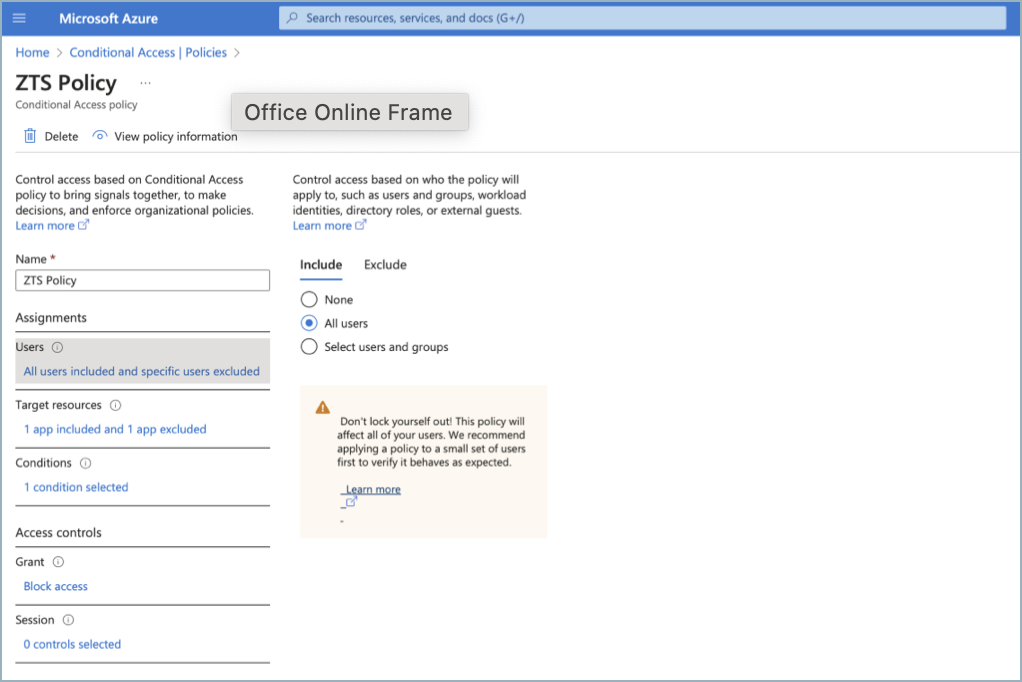
Select the Office 365 application.
Note: If you are using Microsoft Entra ID as an Identity Provider for CloudGen Access, the application that was automatically created during the Entra ID integration process should be excluded from the target resources.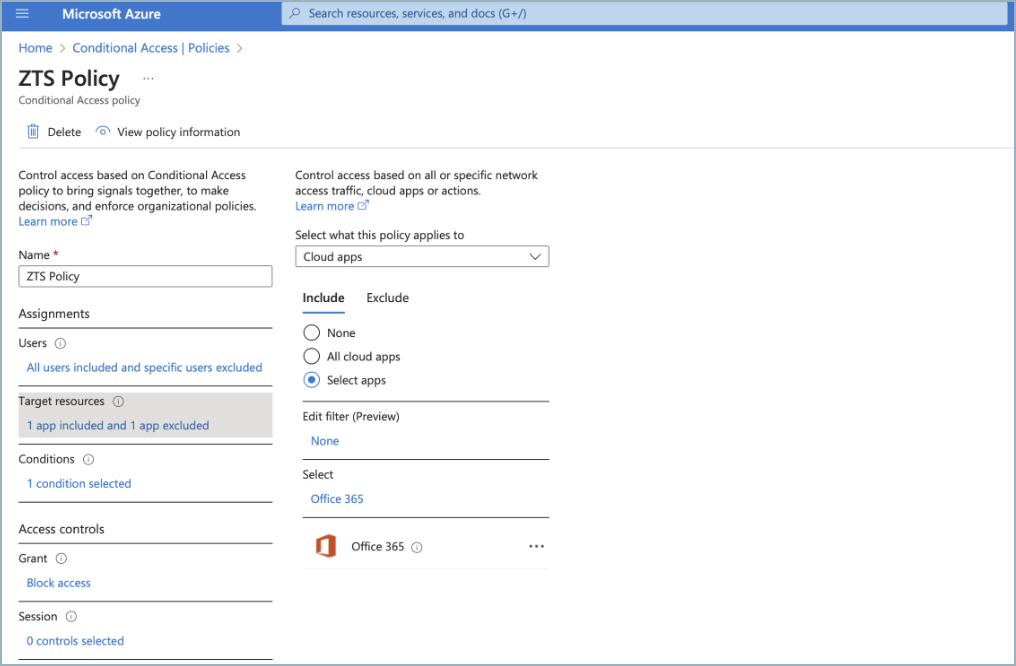
Set conditions. You can enforce this policy to all locations, excluding the “named location” you created.
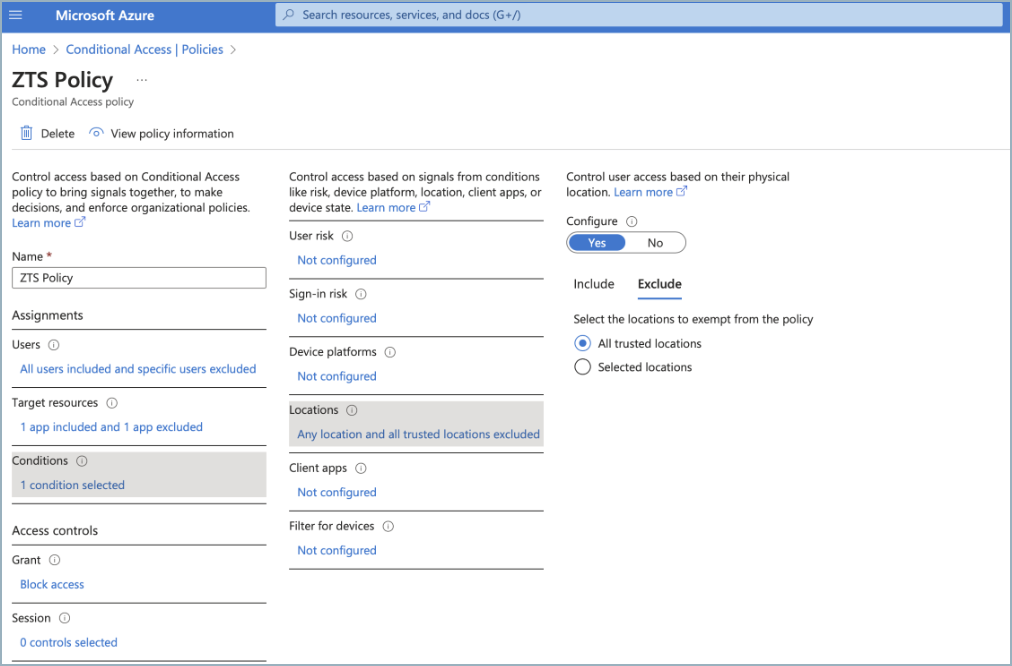
Finally, select Block Access next to Grant.