The use case for test is disabling Azure multi-factor authentication (MFA) for an Azure user.
Barracuda XDR Azure Security Monitoring is a managed, cloud-native security product that detects ransomware, credential dumping, connections to malicious IP addresses, and other breaches. The Azure product catches threats and malware by identifying known threat signatures and using AI/machine learning. This activity identifies when multi-factor authentication is disabled for an Azure user account. An adversary may disable MFA for a user account in order to weaken the authentication requirements for the account.
Test Workflow
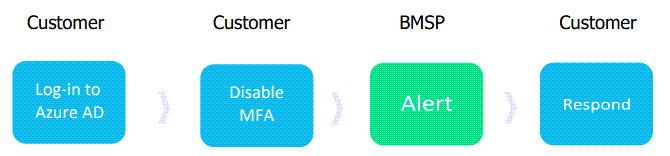
How to Test
- Sign into the Azure portal as an administrator.
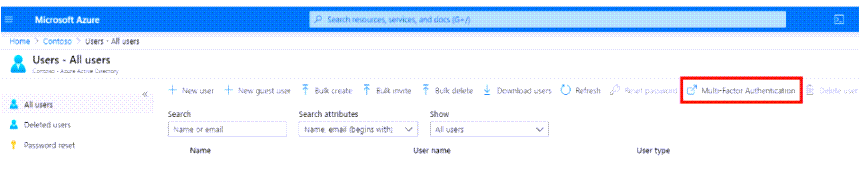
- Search for and select Azure Active Directory, then select Users > All users.
- Scroll right and select Multi-Factor Authentication.
A new page opens, displaying users and their MFA status, as shown below.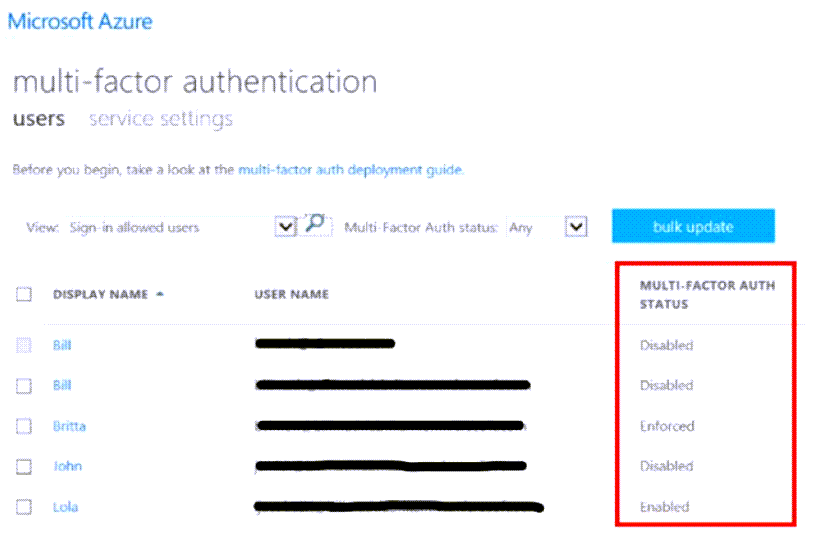
- Select the box next to the name of the user(s) whose MFA you want to disable.
- Click Disable.
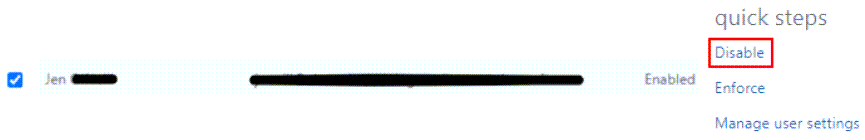
- In the pop-up window, confirm your selection.
An Azure Multi-Factor Authentication Disabled for an Azure User alarm triggers to the Barracuda XDR SOC.
