Barracuda SecureEdge monitoring
Users who have a Network Security license can now integrate with Barracuda SecureEdge. This integration expands Barracuda XDR's coverage into another one of the most popular security products of our users.
New Security Detections
We've added the following new detections in the Network Security and Server Security categories:
Network Security
- Watchguard Threat Detected and Not Blocked - Encompasses all allowed events by the Intrusion Prevention System (IPS) and other threat-related activities identified by the Watchguard firewall. This includes but is not limited to, detecting DDoS attacks, botnet traffic, and file vulnerabilities, providing a comprehensive overview of potential security threats permitted through the firewall.
- FortiGate Admin Login from Public IP - Fully automated detection looks for successful external logins from potentially malicious public IP addresses to the FortiGate Firewall interface. Leveraging our robust threat intelligence and the Barracuda XDR risk score, we determine the legitimacy and reputation of these IP addresses.
- Enhancement: Communication with Threat Intel IP - Fully automated firewall-based detection monitors for successful inbound or outbound connections to or from malicious external source IPs. Using Barracuda XDR, this detection now correlates such traffic with a comprehensive threat intelligence database containing over 10 billion IOCs.
- External Permitted Malicious Traffic - Fully automated Barracuda XDR IDS (Instruction Detection System) based detection monitors both inbound and outbound traffic for connections to known malicious external IP addresses. Also, by employing baseline analysis, we determine if the IDS signature generated is anomalous for the customer's environment. Furthermore, using Barracuda XDR's comprehensive threat intelligence database, we assess the risk score of the traffic based on the reputation of the external IP.
- SecureEdge ATP Threat Detected - Fully automated detection monitors for SecureEdge Advanced Threat Protection (ATP) events, providing protection against advanced malware, zero-day exploits, and targeted attacks. ATP employs scanning mechanisms to assess the legitimacy of files. Among others, ATP scans include Microsoft Office files, PDF documents, and ZIP files.
- SecureEdge IPS Threat Detected - Fully automated detection monitors for allowed SecureEdge Intrusion Prevention System (IPS) events are designed to scan both local and forwarded traffic for malicious activities. The SecureEdge IPS engine analyzes network traffic and continuously compares the bitstream against its internal signature database to detect patterns of malicious code. This detection capability encompasses over 1000 IPS signatures within the SecureEdge database.
Server Security
Seven new detections have been added for Windows monitoring, enhancing security against a range of potential threats. These include but are not limited to, detecting PowerShell-based activities like Kerberos ticket dumping, possible process injections, disabling firewalls, and turning off Defender security settings. Our detections monitor the creation of temporary scheduled tasks, which could signify unauthorized changes or activities in the system. These enhancements significantly bolster our ability to detect and respond to sophisticated threats in Windows environments.
- PowerShell Kerberos Ticket Dump
- Potential Process Injection via PowerShell
- Firewall Disabled via PowerShell
- Defender Security Settings Disabled via PowerShell
- Volume Shadow Copy Deletion via PowerShell
- RDP Enabled via Registry
- Temporary Scheduled Task Creation
Alert Enhancements: Alert Correlation for Automated Alerts
This feature not only streamlines the alert investigation process but also helps resolve alerts. When a new alert is generated, this feature automatically correlates and compiles all relevant alerts from the previous three days, integrating this comprehensive information directly into the ticket. It uses search parameters like related source/destination IPs, source/target usernames, and hostnames for thorough correlation.
This advanced functionality not only provides customers with immediate access to extensive contextual data, enabling quicker and more efficient investigations but also assists in the effective resolution of alerts.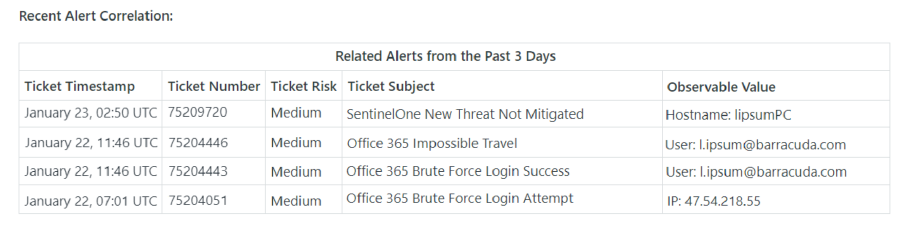
Managed Endpoint enhancements
Self-service Allow List
Now users can quickly add threats to the Allow List without having to contact the SOC.
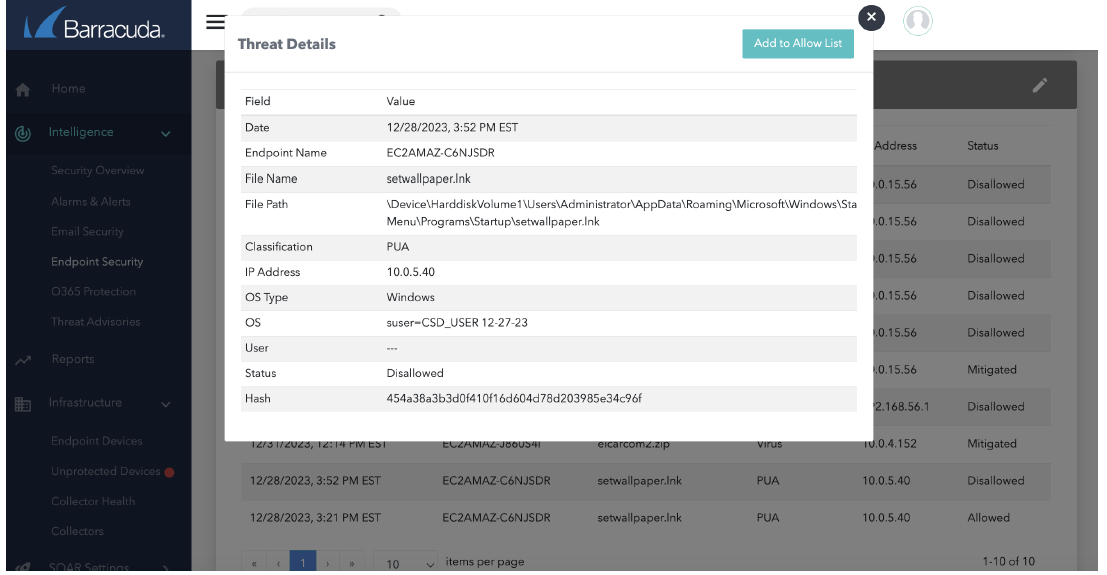
Self-service Allow Lists let users quickly mark threats as legitimate activity so they are ignored in the future. Threats are listed under Intelligence > Endpoint Security, and can be allowed by clicking the threat, then clicking the Add to Allow List button in the dialog box.
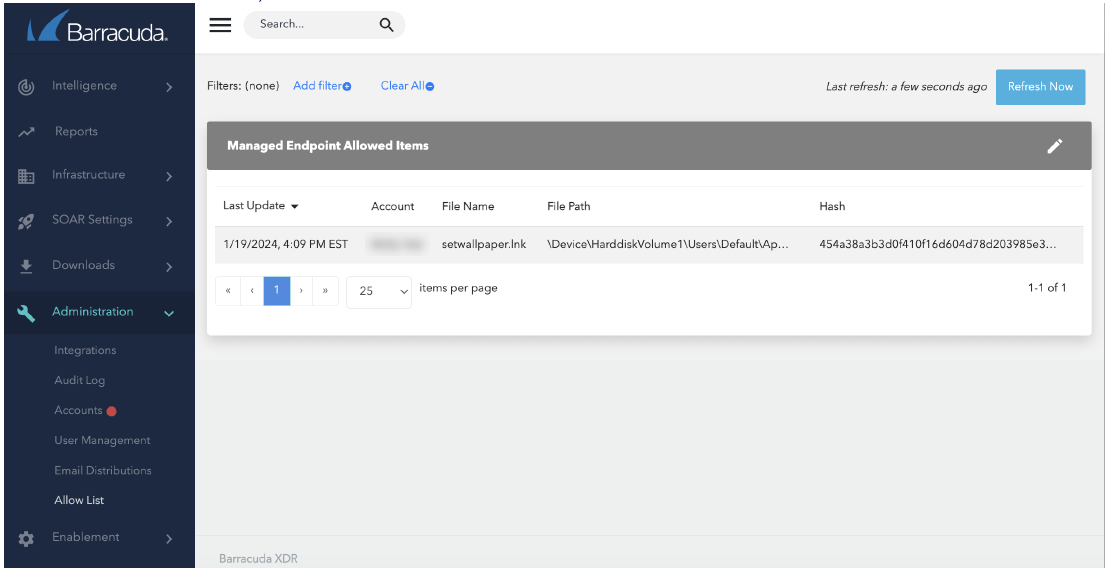
Once marked as allowed, the list of items can be found under Administration > Allow List.
Export device list
Users can now export the list of Endpoint Devices to a CSV file letting you easily report on what is being monitored. On the Infrastructure > Endpoint Devices page, click the Export Devices button on the right in the Endpoint Devices table.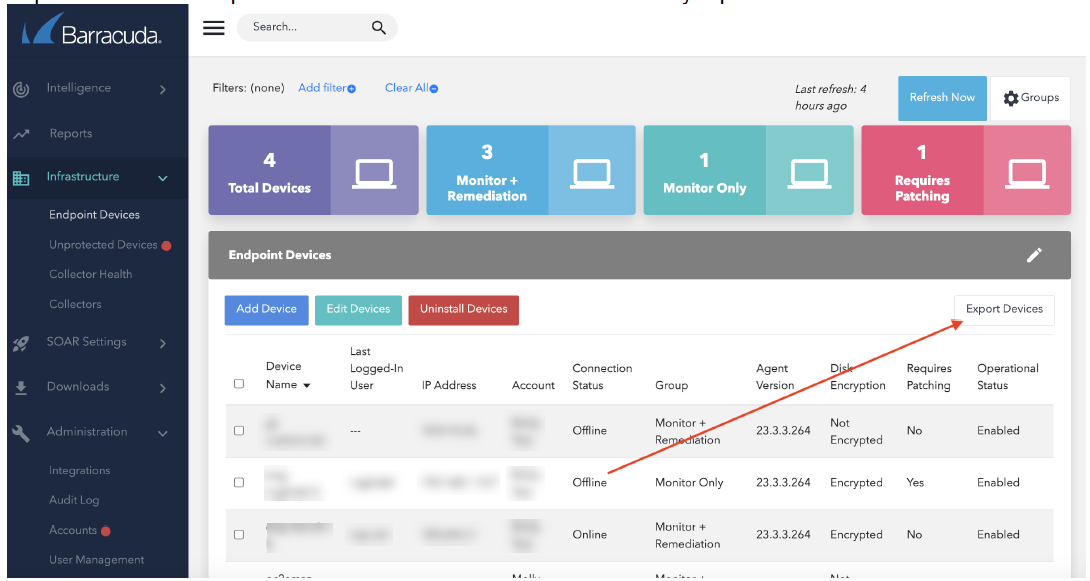
Ticket integration and other enhancements
To improve usability and minimize the learning curve, we've made the following changes:
- The configuration summary area now has a Not Configured status for better situational awareness.
- The UI text for deleting all settings for ConnectWise, ServiceNow, and AutoTask has been improved, making it clear that the user can only delete all settings and not an individual setting.
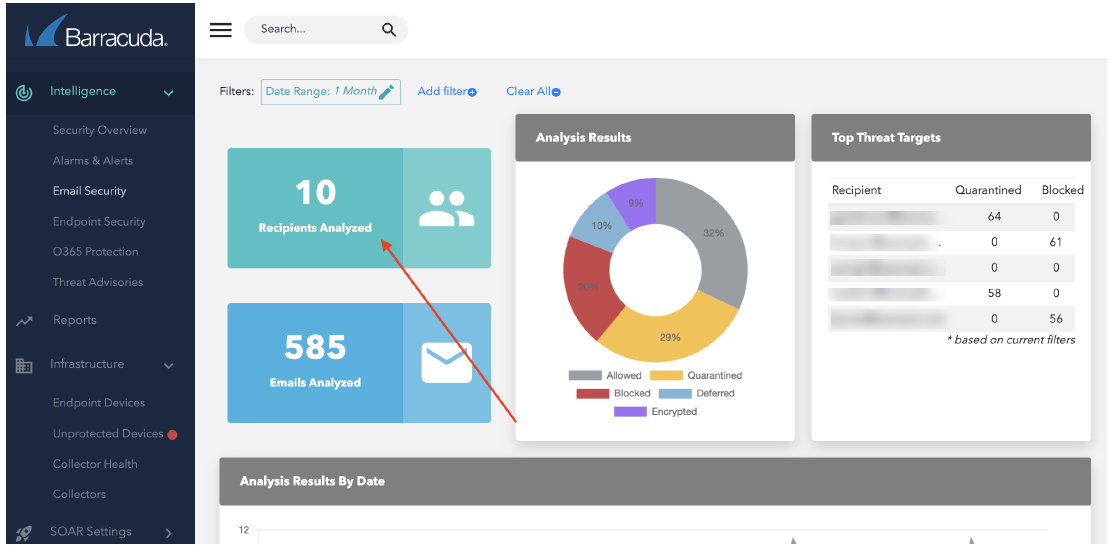
- In Intelligence > Email Security, the label has been changed from Users Protected to Recipients Analyzed to better reflect what is being represented.
- Under Administration > Integrations, Barracuda CloudGen has been renamed to Barracuda CloudGen Firewall.
