If you use the default rule set, all traffic is allowed from the LAN to the Internet. If you keep the rules that include the parameter Service set to Any, you might want to add access rules that BLOCK or RESET traffic with specific profiles. For example, you can deny specific service types or traffic from certain users. Using BLOCK causes the Barracuda NextGen Firewall X-Series to simply not respond to the connection request. The source client will then receive a timeout. To actively deny access, select RESET. The connection is then closed by the X-Series Firewall as soon as a connection attempt is made.
This article provides an example of how to configure an access rule that blocks all ICMP traffic from the local LAN to the Internet.
Step 1. Create an Access Rule to Block ICMP Traffic
- Go to the FIREWALL > Firewall Rules page.
- Click Add Access Rule to create a new access rule.
- In the Add Access Rule window, enter a name and description for the rule.
Specify the following settings:
Action Source Network Services Destination Block Trusted LAN ICMP Internet 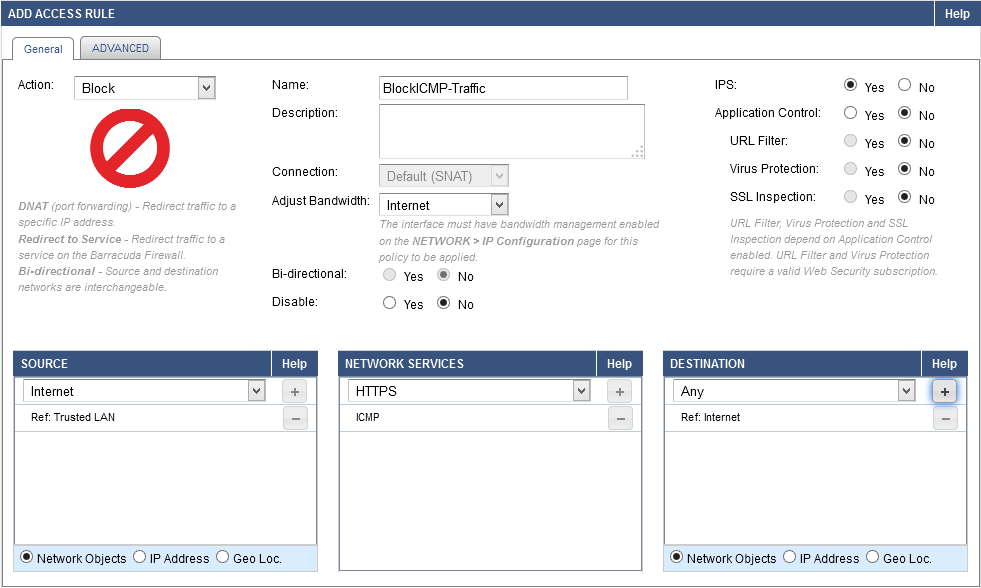
- At the top of the Add Access Rule window, click Save.
Step 2. Verify the Order of the Access Rules
New rules are created at the bottom of the firewall rule set. Rules are processed from top to bottom in the rule set. Drag your access rule to a slot in the rule list so that no access rules before it matches this traffic. Verify that your rules are placed above the BLOCKALL rule. Otherwise, the rule never matches.
After adjusting the order of rules in the rule set, click Save.
