Privileged Account Protection is a part of the Account Takeover Protection provided by the Barracuda Web Application Firewall. In Privileged Account Protection, various session data elements, such as the connecting entity’s geolocation, user agent, header value, and network details, are evaluated. If the risk score generated by Privileged Account Protection for connecting a client is within the configured permissible threshold, then the client is allowed to access the back-end application. If the risk score exceeds the threshold, a notification is sent to the administrator to flag the client for follow-up action. For details on the various types of follow-up actions, see Attacks Description - Action Policy.
Privileged Account Protection Workflow
Workflow of Privileged Account Protection When the Allowed Deviation is Within the Specified Threshold:
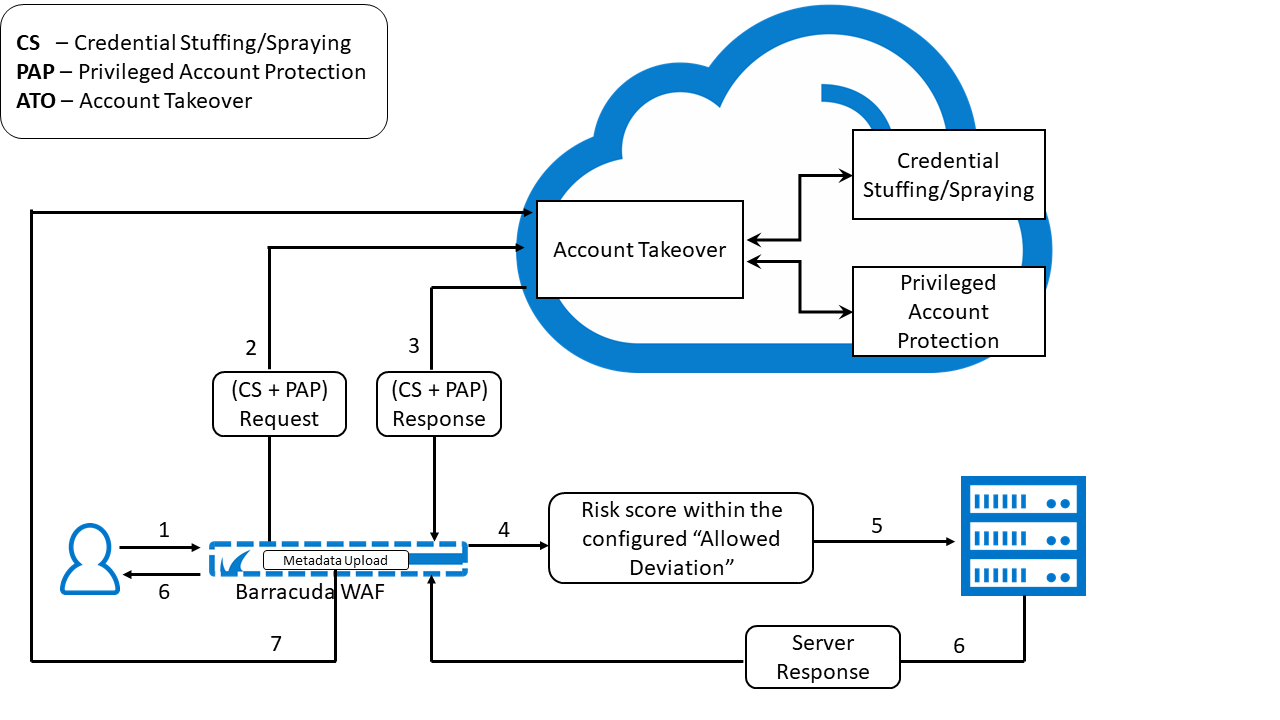
- User sends a login request to an application for which Client Profiling is enabled.
- The Barracuda Web Application Firewall sends the credential stuffing/spraying and Privileged Account Protection request to the Account Takeover (ATO) cloud service. The request is evaluated for risk, and a risk score is generated.
- The ATO service sends the response with the risk score to the Barracuda WAF.
- The Barracuda WAF checks the risk score.
- If the risk score is within the configured “Allowed Deviation” threshold, the request is forwarded to the server.
- The server sends the response to the Barracuda WAF, and the WAF forwards it to the user.
- The Barracuda WAF uploads the metadata to the ATO cloud service.
Workflow of Privileged Account Protection When the Allowed Deviation Exceeds the Configured Threshold:
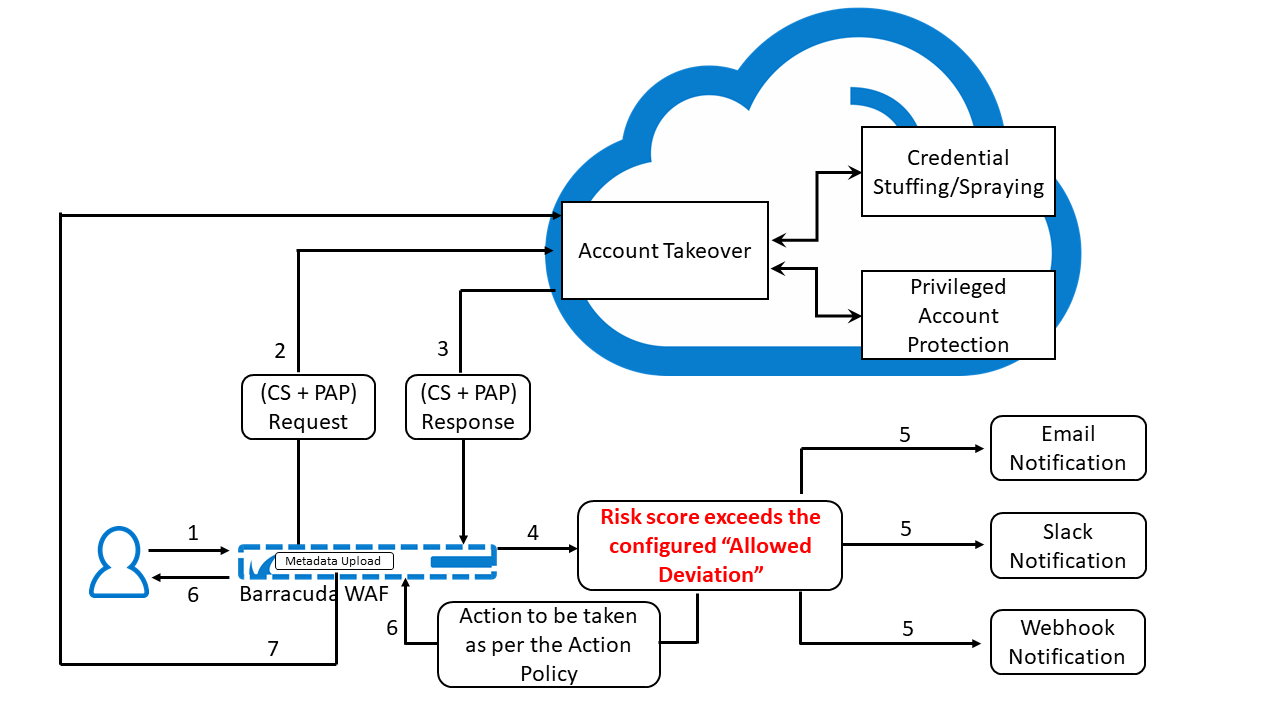
- User sends a login request to an application for which Client Profiling is enabled.
- The Barracuda Web Application Firewall sends the credential stuffing/spraying and Privileged Account Protection request to the Account Takeover (ATO) cloud service. The request is evaluated for risk, and a risk score is generated.
- The ATO service sends the response with the risk score to the Barracuda WAF.
- The Barracuda WAF checks the risk score.
- If the risk score exceeds the configured “Allowed Deviation” threshold, an attack event alert is generated. Also, if Slack/Email and Webhook are configured, a notification is sent to the WAF administrator over Slack/email and by HTTP POST request to the configured Webhook URL.
- The Barracuda WAF responds to the user as per the action policy configured for that attack event.
- The Barracuda WAF uploads the metadata to the ATO cloud service.
To configure Privileged Account Protection:
- Go to the BOT MITIGATION > Bot Mitigation page.
- Select Edit under Options next to the URL policy for which you want to configure Privileged Account Protection.
- On the Edit URL Policy page, scroll down to the Account Protection section and do the following:
- Enable User Account Profiling – When set to Yes, Privileged Account Protection is enabled and parameters, such as a user's geolocation, user agent, network, are evaluated for the client before allowing the request.
- Allowed Deviation – Set the deviation to Low, Medium or High. When Allowed Deviation is set to Low and the risk score of the client exceeds the low deviation threshold, an ATO_DEVIATION_LOW_EXCEEDED attack is raised, and a notification with violation parameters is sent to the admin on the configured Webhook.
- Webhook for Profile Deviation – Specify the Webhook to receive notifications about the violations that occurred from the client. Webhook configuration can be any HTTPS application endpoint where notification messages can be sent using HTTP POST. Apart from the Webhook notification, a separate notification will be sent to admin’s email address or Slack channel, if configured.
- Webhook Passphrase Option - Select how you want to send the passphrase (Header, Parameter or Not Required) to the Webhook endpoint. Based on the option selected, the passphrase is sent through the header or query parameter in the name value pairs.
- Passphrase Name - Specify the name of the passphrase to be used in the name value pair.
- Passphrase Value - Specify the value of the passphrase to be used in the name value pair.
- Specify values for other parameters as required and click Save.
