You can use the Test Connectivity option on the Servers page to check if the server(s) associated with the application is accessible from the Application Security Enforcer (Traffic inspection module). The Barracuda WAF-as-a-Service uses the configured server settings to connect to the backend server.
To run the test separately on each server, click the three dots under MORE next to the server and select Test Connectivity.
After the completion of the test, the results are displayed under each server (in case of multiple servers). The Barracuda WAF-as-a-Service performs network layer and application layer tests:
- Network connectivity tests are performed using the SSL parameters configured in the Server configuration.
- Application connectivity tests are performed using the Health Check parameters configured in the Server configuration.
The server connectivity test can be used to validate:
- Network connectivity between the Application Security Enforcer and Application Server.
- Application connectivity to check if the connection is established with the configured server.
- SSL parameters such as TLS version, SNI, certificates, etc.
- Health check parameters (Application layer health check).
Response Errors and Solutions
Following are some of the errors and solutions.
Error 1: Test Parameters are not Configured
The following message is displayed when the application layer test is not configured.
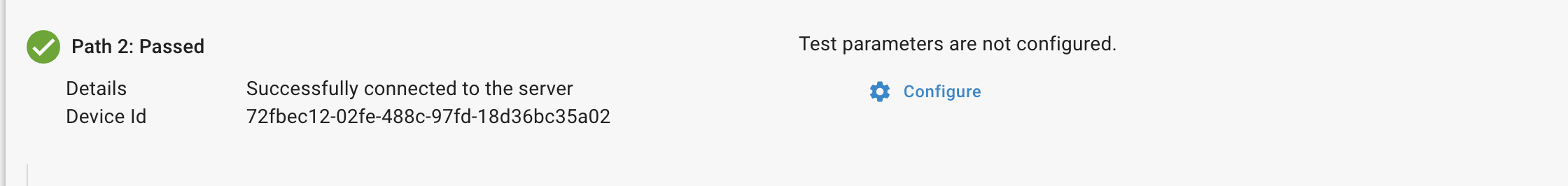
Solution
- Click the Configure option and provide the required values.
OR - Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the HEALTH CHECKS tab.
- Specify the URL in the Request URL field.
- Configure other parameters as required and click Save.
- Rerun the test.
Error 2: SSL_NO_PROTOCOLS_AVAILABLE
The error is displayed if the server uses HTTPS protocol and TLS versions are not enabled.
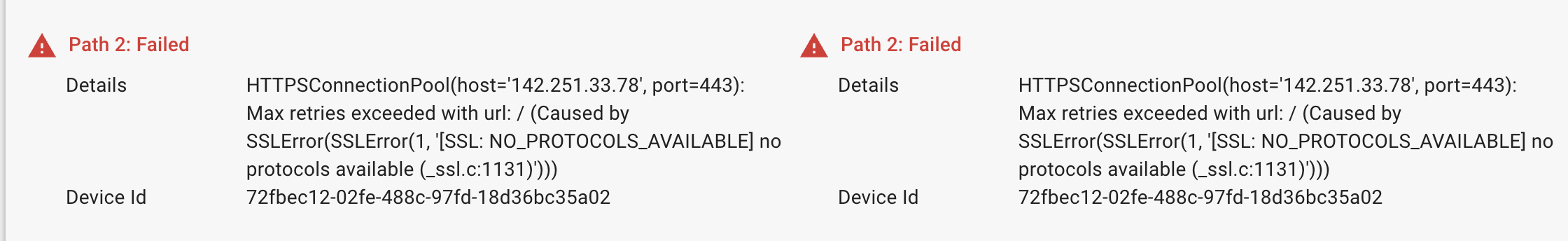
Solution:
- Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the SSL tab.
- Select the TLS versions that are supported by the server.
- Click Save.
- Rerun the test.
Error 3: SSLV3_ALERT_HANDSHAKE_FAILURE
The error is displayed when an unsupported TLS version is selected for the server.
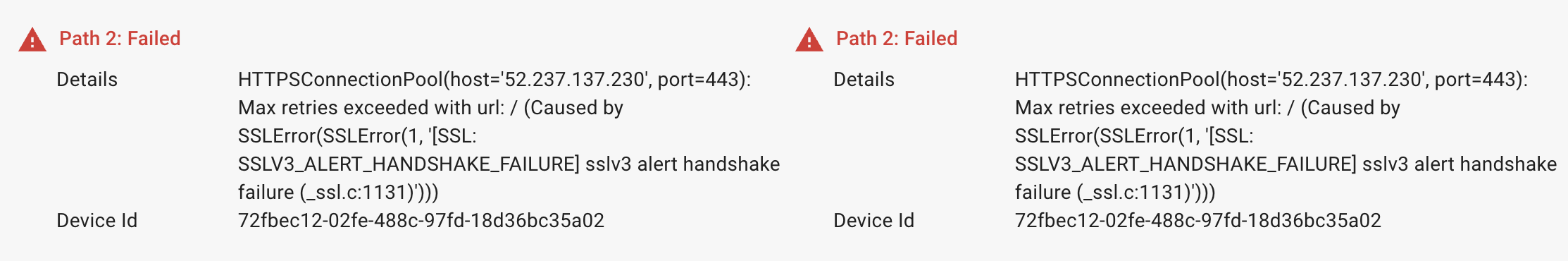
Solution:
- Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the SSL tab.
- Select the TLS versions that are supported by the server.
- Click Save.
- Rerun the test.
Error 4: SSL_CERTIFICATE_VERIFY_FAILED
The error is displayed when certificate validation and SNI is enabled but a wrong SNI domain name is configured or there is a domain mismatch.
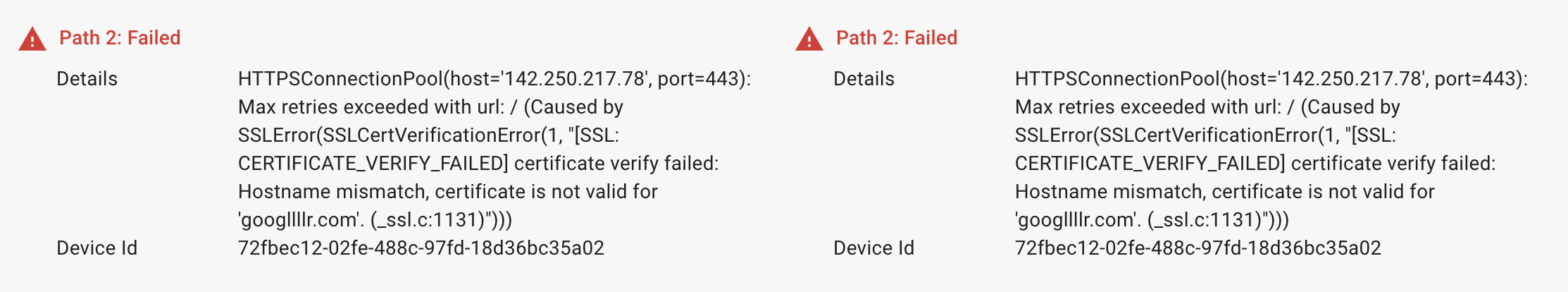
Solution:
- Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the HEALTH CHECKS tab.
- Specify the correct domain name in the SNI Domain field.
- Click Save.
- Rerun the test.
Error 5: Expected status code is 301 and response status code is 200
The error is displayed when the expected status code does not match with the response code.
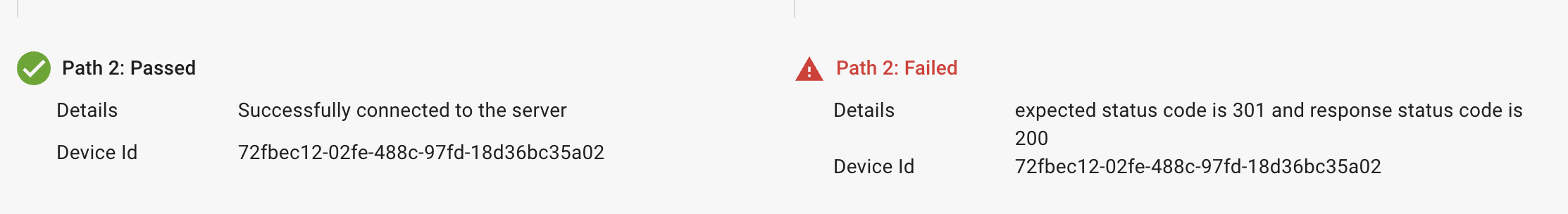
Solution:
- Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the HEALTH CHECKS tab.
- Specify the correct code in the Expected Status Code field.
- Click Save.
- Rerun the test.
Error 6: Expected string not found in response
The error is displayed when the expected string is not found in the response HTML content.
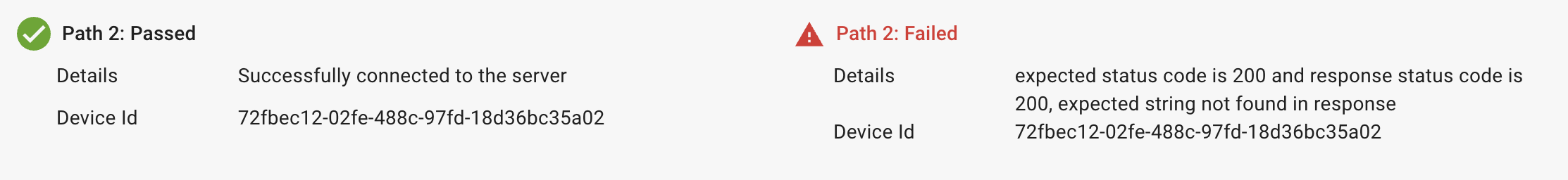
Solution:
- Click the three dots under MORE next to the server and select Edit Server.
- On the Edit Server window:
- Select the HEALTH CHECKS tab.
- Specify the correct string in the Expected String in Response field.
- Click Save.
- Rerun the test.
