When the SSL Inspection feature is enabled on the Barracuda Web Security Gateway, the administrator has granular control over what applications are blocked or allowed on websites like Google.com. This article explains how to apply block/allow policies by selecting some or all Google Consumer Apps to be inspected over HTTPS.
How to Block and Allow Google Consumer Apps
Step 1. Enable and Configure SSL Inspection
This is the first step required for SSL inspecting HTTPS traffic.
- Log into the Barracuda Web Security Gateway web interface as an administrator.
- On the ADVANCED > SSL Inspection page:
- For inline deployments on the 910 and above, set SSL Inspection Method to Transparent.
- For forward proxy deployments on the 610 and above, set SSL Inspection Method to Proxy.
- In the Inspected Domains field, enter Google.com and click Add.
- Install an SSL certificate. There are two recommended options:
- Select Create to generate your own signed SSL certificate and download it to install in or push out to each client browser. If you don't, users will see a warning each time they browse an HTTPS site when SSL Inspection is enabled. For detailed instructions on creating and installing the certificate, see How to Create and Install a Self-Signed Certificate for SSL Inspection.
- Use the Barracuda Default Certificate for SSL Inspection, available on the ADVANCED > SSL Inspection page. This is the simpler of the two methods. If you are only using one Barracuda Web Security Gateway (as opposed to clustering two or more systems using Linked Management), the private key is more secure as it never leaves the device. If you have a high availability deployment, you will need to install the same root certificate on each Barracuda Web Security Gateway. For detailed instructions on installing the certificate, see How to Use the Barracuda Networks Default Certificate for SSL Inspection.
Step 2. Block or Allow Google Consumer Apps
The Google Consumer Apps content category is used to block or allow traffic from Google domains and sub-domains. You can then create Exceptions to these policies for certain users or groups for access to all or some Google Consumer Apps.
- From the BLOCK/ACCEPT > Web App Control page, in the Allowed Applications box, select Google Consumer Apps under Category Filter.
- In the list box, you can either select Google Mail or Google Consumer Apps, and click the Block button to move it to the Blocked Applications list box. Click Save.
- On the BLOCK/ACCEPT > Exceptions page, create block/allow exceptions by user(s) and/or group(s). See example use cases in this article.
How to Block/Allow Google Hangout
To block Google Hangouts, you must block both of the following:
Use Case #1 – Allow Google Consumer Apps, While Blocking Google Wallet Students
This scenario allows access to Google Gmail and most other Google Consumer Apps, which are accessed via HTTPS. Exception to this policy is blocking Google Wallet over HTTPS. Since no time frame is specified on the BLOCK/ACCEPT > Exceptions page in this example, these policies would be enforced by the Barracuda Web Security Gateway 24/7 if configured as shown here.
Step 1. Configure SSL Inspection as described above
Step 2. Create the Block policy for Google Wallet
- On the BLOCK/ACCEPT > Exceptions page, in the Add Exceptions section, select the Block Action. See Figure 1.
- Select the type of users you want to block (Authenticated, Local Group, etc.) in the Applies To field. In this case we've chosen the Students Local Group.
Select Web App Control as the Exception Type.
Figure 1: Blocking Google Wallet for the Students group
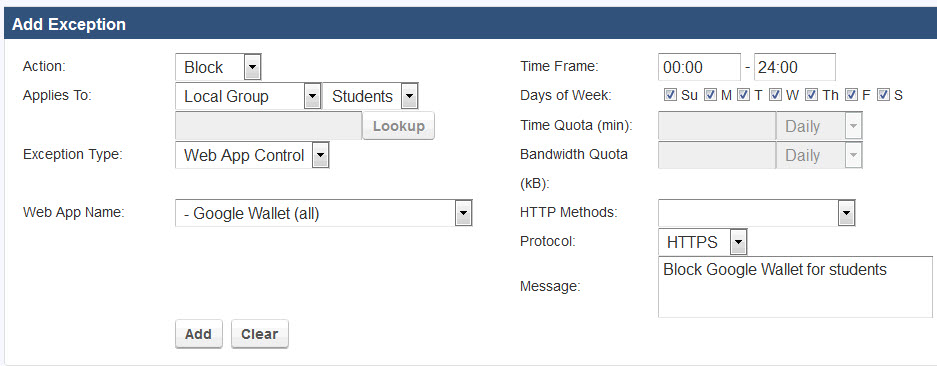
- In the Web App Name box, select Google Wallet (all).
- From the Protocol drop-down, select HTTPS.
- Click Add.
Use Case #2 – Restricting Use of Google Mail During Business Hours
You may want to allow managers access to Google Workspace business mail, while blocking Gmail access to non-managers. Here are the basic steps.
Step 1. Configure SSL Inspection as described above
Step 2. Create the Block policy for Gmail
- Create a group called Managers on the USERS > USERS/GROUPS page. Assign appropriate users to this group.
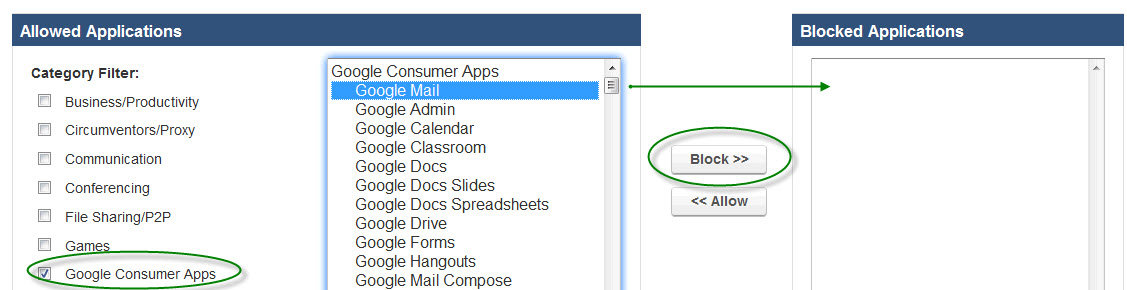
- Go to the BLOCK/ACCEPT > Web App Control page and, in the Allowed Applications box, select Google Consumer Apps under Category Filter.
- In the list box, you can either select Google Mail or Google Consumer Apps (to block ALL Google Consumer Apps), and click the Block button to move it to the Blocked Applications list box. Click Save.
Step 3. Create the Allow policy for business Gmail for Managers
- Go to the BLOCK/ACCEPT > Exceptions page and select the Allow action.
- Select the Local Group in the Applies To field. In the drop-down menu to the right, select Managers.
- Select the Web App Control Exception Type.
- Select Google Mail for the Web App Name.
- In the Allowed Domains text box, enter, separating by commas, the Google sub domain(s) from which managers can access Google Mail. This will be the domain(s) with which they log into their business Google accounts.
- Click the Add button to see the exception added to the List of Exceptions table below.
Use Case #3 – Blocking Personal Gmail, While Allowing Business Gmail Access to All Users
Suppose you want to allow access for Authenticated Users to Google Workspace business mail 24/7, but block personal Gmail during business hours.
Step 1. Configure SSL Inspection as described above under Enable and Configure SSL Inspection.
Step 2. Create the block policy for Gmail
- Go to the BLOCK/ACCEPT > Web App Control page and, in the Allowed Applications box, select Google Consumer Apps under Category Filter.
- In the list box, select Google Mail, and click the Block button to move it to the Blocked Applications list box. Click Save.
Step 3. Create the Allow policy for business Gmail for Authenticated Users 24/7
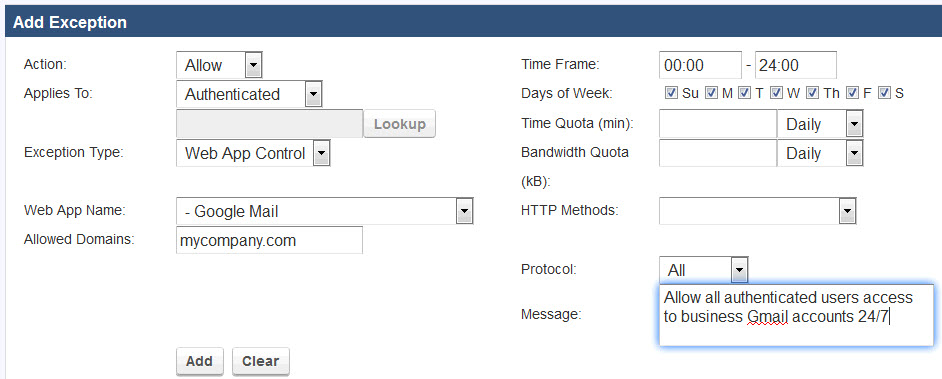
- Go to the BLOCK/ACCEPT > Exceptions page and select the Allow action.
- Select Authenticated in the Applies To field.
- Select the Web App Control Exception Type.
- Select Google Mail for the Web App Name.
- In the Allowed Domains text box, enter, separating by commas, the Google sub-domain(s) from which users can access their business Google Mail accounts. This example uses mycompany.com and limits authenticated users to only access Gmail accounts with logins from that domain.
- Click the Add button to see the exception added to the List of Exceptions table.
Step 4. Create the Allow policy for personal Gmail account access OUTSIDE of business hours
- Follow #1-4 in Step 3 above.
- Select a Time Frame of Monday - Friday, 17:00 - 08:00 (or whatever constitutes hours outside of typical business hours).
- Click the Add button to see the exception added to the List of Exceptions table.
