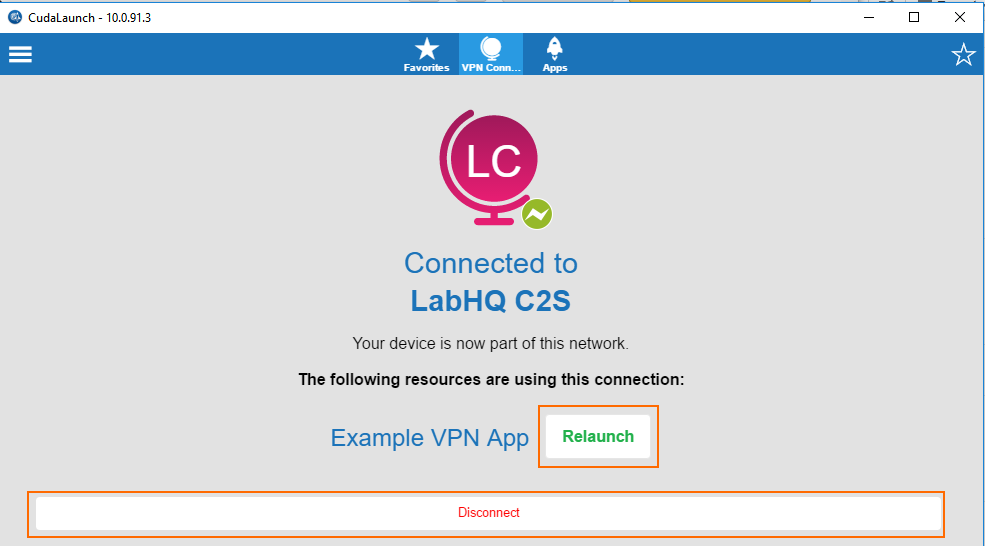
VPN Apps for the SSL VPN are used to allow users to connect to internal web applications not suitable for SSL VPN Web Apps or native apps. CudaLaunch transparently opens a client-to-site VPN tunnel and then opens the resource in the default browser. Depending on your requirements, you can restrict the VPN connection to be available only for VPN Apps. For Windows clients, both CudaLaunch and the Barracuda VPN client must be installed; for iOS and Android, CudaLaunch is required.
Before You Begin
- Configure both SSL VPN and client-to-site VPN:
- Configure a client-to-site VPN group policy. For more information, see How to Configure a Client-to-Site VPN Group Policy.
- Configure a VPN group policy for the SSL VPN. For more information, see How to Configure VPN Group Policies in the SSL VPN.
Step 1. Configure a VPN App for SSL VPN
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > SSL-VPN.
- Click Lock.
- In the left menu, select VPN Apps.
- In the VPN Apps section, click + to add a VPN App to the list.
Enter a Name and click OK. The VPN Apps window opens.
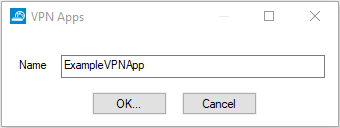
Configure the VPN App:
App Type – Select WebApp.
Visible Name – Enter the user-facing name for this app.
VPN Group Policy – Select the VPN group policy. This policy must already be uploaded as a VPN group policy for the SSL VPN service. For more information, see How to Configure VPN Templates in the SSL VPN.
Hostname – Enter the hostname for the internal web application in the following format: Protocol type (
http://orhttps://) followed by the FQDN or IP address of the web server. E.g.,http://your.domain.comorhttps://10.10.10.10
Launch Path – Enter "/" followed by the path and file name you want to request when starting the VPN App. Hash characters (#) in the launch path must be replaced by[hash]. You can also include user or session attributes in the launch URL. E.g.,/wiki/${session:username}/ or /lunchmenu/${user:location}/index.phpFor more information on attributes, see How to Use and Create Attributes.
- (optional) To restrict access to the web app by user group, replace the * entry in the Allowed User Groups list. Click + to add new user groups.
- (optional) Click Ex/Import to upload a custom icon.
- Click Send Changes and Activate
Step 2. Create a Network Object for the VPN App Resources
Create a network object containing all IP addresses, hostnames, and networks containing the servers and services that the user needs access to when accessing the VPN resource.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, cli ck on Networks.
- Click Lock.
- Right-click the table and select New. The Edit/Create Network Object window opens.
- For each VPN App, create a network object containing all IP addresses, hostnames and networks required by the VPN App.
- Type – Select List of IPv4 Addresses or Hostname (DNS resolved).
- Name – For hostname network objects, enter the FQDN; for a list of IPv4 addresses, enter the name.
- Include Entries – For each IP address, click + to add it to the list.
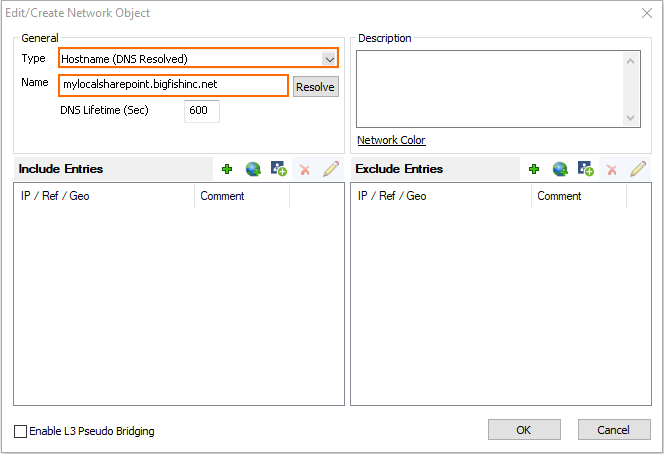
- Click OK.
- Click Send Changes and Activate.
Step 3. Add Access Rules for VPN App Resource
Add access rules to allow connections from the client-to-site VPN to the internal resource that is accessed through the VPN App. Since the user has access to all resources allowed via access rules when connected to the client-to-site VPN, these access rules should be as restrictive as possible.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- Either click the plus icon (+) at the top right of the ruleset, or right-click the ruleset and select New > Rule.

- Select Pass as the action.
- Enter a name for the rule.
- Specify the following settings that must be matched by the traffic to be handled by the access rule:
- Source – Select the network object containing the VPN client network.
- Service – Select HTTP+S.
- Destination – Select the network object configured in Step 2.
- Connection Method – Select Dynamic NAT.
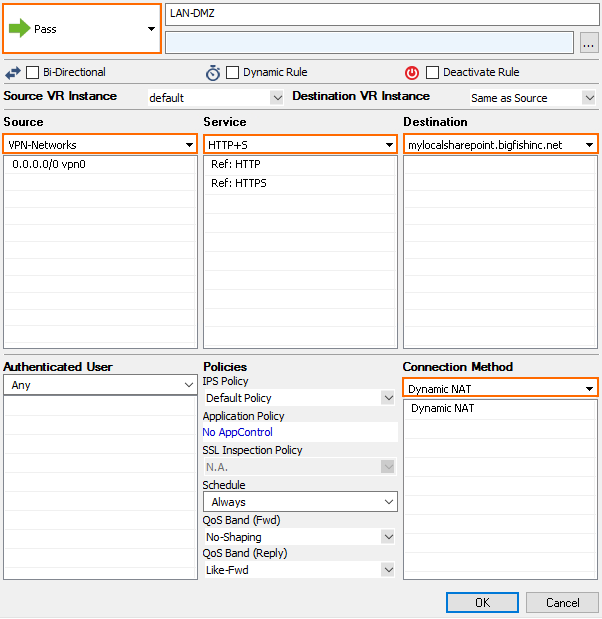
- Source – Select the network object containing the VPN client network.
- Click OK.
- Drag and drop the access rule so that it is the first rule that matches the traffic that you want it to forward. Ensure that the rule is located above the BLOCKALL rule; rules located below the BLOCKALL rule are never executed.
- Click Send Changes and Activate.
The users can now access the internal resource by clicking on the VPN App in CudaLaunch for Windows, iOS, or Android. After the connection is established, the web application is opened automatically in an external browser window. Go to the VPN Connections tab to disconnect from the client-to-site VPN.