The simplest site-to-site TINA VPN tunnel setup is a transparent connection of two networks with different address ranges. This setup should not be noticeable by the connected networks. The following figure illustrates a fully transparent VPN tunnel. This article provides example settings for creating a site-to-site TINA VPN tunnel for this environment. The article does not cover the routing configuration between both VPN servers. Unless overlapping addresses are used, the VPN tunnels do not interfere with the routing configuration.
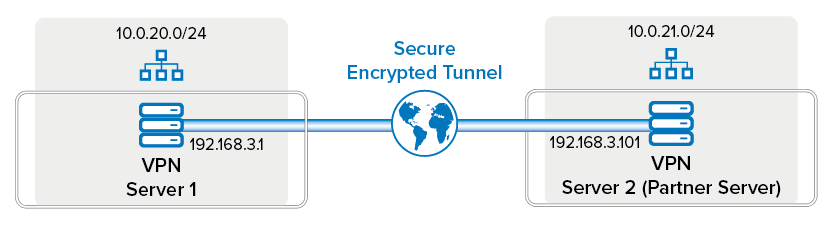
VPN Server 1 Settings
| Tab | Setting | Value | Comment |
|---|---|---|---|
| Basic | Transport | UDP&TCP (or whatever is needed) | - |
Encryption | AES (or whatever is needed) | May be unencrypted for intranet connections only aiming at routing assistance. | |
| Advanced | Tunnel Timeout |
| - |
| Local Networks | Call Direction | Active or Passive | Converse to the partner’s configuration. |
| Network Address | 10.0.20.0/24 | - | |
| Local | IP Address or Interface Used for Tunnel Address | Dynamic (via routing) | Only one IP address is assumed on the outside interface. |
| Remote Networks | Remote Network | 10.0.21.0/24 | - |
| Remote | Remote Peer IP Addresses | 192.168.3.101 | - |
VPN Server 2 Settings
| Tab | Setting | Value | Comment |
|---|---|---|---|
| Basic | Transport | UDP&TCP (or whatever is needed) | - |
Encryption | Same value as on the local side | May be unencrypted for intranet connections only aiming at routing assistance. | |
| Advanced | Tunnel Timeout |
| - |
| Local Networks | Call Direction | Active or Passive | Converse to the partner’s configuration. |
| Network Address | 10.0.21.0/24 | - | |
| Local | IP Address or Interface Used for Tunnel Address | Dynamic (via routing) | Only one IP address is assumed on the outside interface. |
| Remote Networks | Remote Network | 10.0.20.0/24 | - |
| Remote | Remote Peer IP Addresses | 192.168.3.1 | - |
Access Rules
You must create Pass access rules on both systems to allow traffic between the local and partner networks.
