The firewall audit service allows propagating firewall audit events to the Control Center for collection and analysis.
How to Configure Audit and Reporting
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > General Firewall Configuration.
- In the left menu, select Audit and Reporting.
- Expand the Configuration Mode menu and select Switch to Advanced View.
- Click Lock.
Configure Statistics Policy
In the Statistics Policy section, configure the following settings: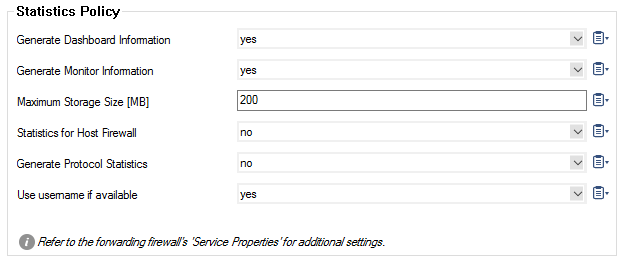
- Generate Dashboard Information – To enable the firewall dashboard, select yes.
- Generate Monitor Information – To enable the firewall monitor, select yes.
- Maximum Storage Size – Enter the amount of megabytes [MB] for the maximum size of the storage.
- Statistics for Host Firewall – Enable if you want to create statistics for the Host Firewall.
- Generate Protocol Statistics – Enable to create protocol- and P2P-specific statistics. These statistic can be seen using the event viewer under.
../BOX/proto–stat/. - Use username if available – Enable if usernames should be used for statistics instead of IP addresses.
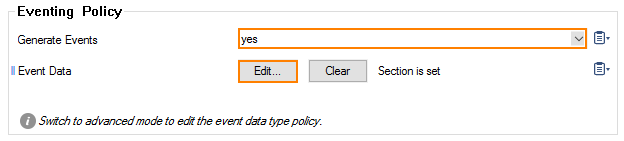
Configure Eventing Policy
In the Eventing Policy section, configure the following settings:
- Generate Events – To generate events, select yes.
- Event Data – Click Show.../Edit... to enable or disable specific events:
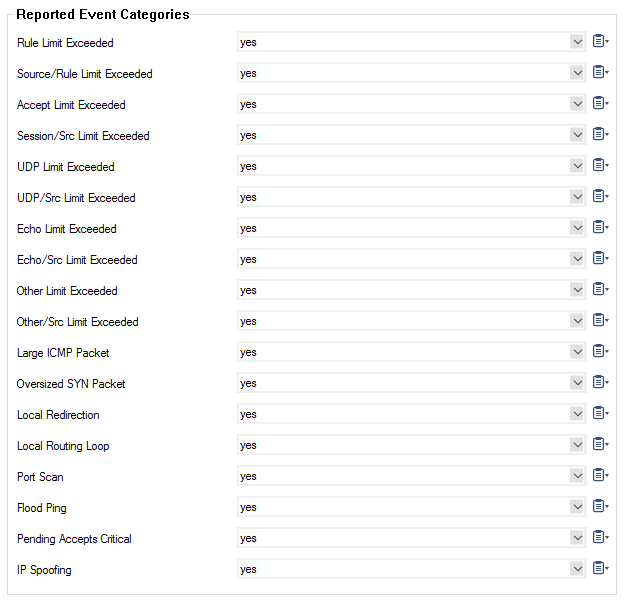
- Rule Limit Exceeded – Triggers event 'FW Rule Connection Limit Exceeded' [4016] when the allowed maximum number of connections for a rule has been exceeded.
- Source/Rule Limit Exceeded – Triggers event 'FW Rule Connection per Source Limit Exceeded' [4018] when the allowed maximum number of connections/src for a rule has been exceeded.
- Accept Limit Exceeded – Triggers event 'FW Pending TCP Connection Limit Reached' [4006] when the limit for 'Max Pending Accepts/Src' has been exceeded.
- Session/Src Limit Exceeded – Triggers event 'FW Global Connection per Source Limit Exceeded' [4024] when the limit for either 'Max Local-In Sessions/Src' or 'Max. Forwarding Sessions/Src' has been exceeded.
- UDP Limit Exceeded – Triggers event 'FW UDP Connection Limit Exceeded' [4009] when the limit for 'Max UDP (%)' has been exceeded.
- UDP/Src Limit Exceeded – Triggers event 'FW UDP Connection per Source Limit Exceeded' [4008] when the limit for either 'Max Local-In UDP/Src' or 'Max. Forwarding UDP/Src' has been exceeded.
- Echo Limit Exceeded – Triggers event 'FW ICMP-ECHO Connection Limit Exceeded' [4027] when the limit for either 'Max Echo (%)' has been exceeded.
- Echo/Src Limit Exceeded – Triggers event 'FW ICMP-ECHO Connection per Source Limit Exceeded' [4026] when the limit for either 'Max Local-In Echo/Src' or 'Max. Forwarding Echo/Src' has been exceeded.
- Other Limit exceeded – Triggers event 'FW OTHER-IP Session Limit Exceeded' [4029] when the limit for either 'Max Other (%)' has been exceeded.
- Other/SrcLimit exceeded – Triggers event 'FW OTHER-IP Connection per Source Limit Exceeded' [4028] when the limit for either 'Max Local-In Other/Src' or 'Max. Forwarding Other/Src' has been exceeded.
- Large ICMP Packet – Triggers event 'FW Large ICMP Packet Dumped' [4012] when the service object specific limit of 'Max Ping Size' has been exceeded.
- Oversized SYN Packet – Triggers event 'FW Oversized SYN Packet Dumped' [4010] when an oversized SYN packet has been detected and dropped.
- Local Redirection – Triggers event 'FW Local Redirection Suppressed' [2502] when the firewall redirects traffic to itself.
- Local Routing Loop – Triggers event 'FW Forwarding Loop Suppressed' [2500] when the firewall detects a routing loop.
- Port Scan – Triggers event 'FW Port Scan Detected' [4000] when the 'Port Scan Threshold' has been exceeded by a particular source.
- Flood Ping – Triggers event 'FW Flood Ping Protection Activated' [4002] when the service object specific limit of 'Min Delay' has been violated.
- Pending Accepts Critical – Triggers event 'FW Activating Perimeter Defence (inbound mode)' [4004] when limit for 'Inbound Threshold (%)' has been exceeded.
- IP Spoofing – Triggers events 'FW IP Spoofing Attempt Detected' [4014] or 'FW Potential IP Spoofing Attempt' [4015]. This only applies to firewall rules where 'Source/Reverse Interface' policies have been set to 'matching'.
Configure Log Policy
In the LogPolicy section, configure the following settings:
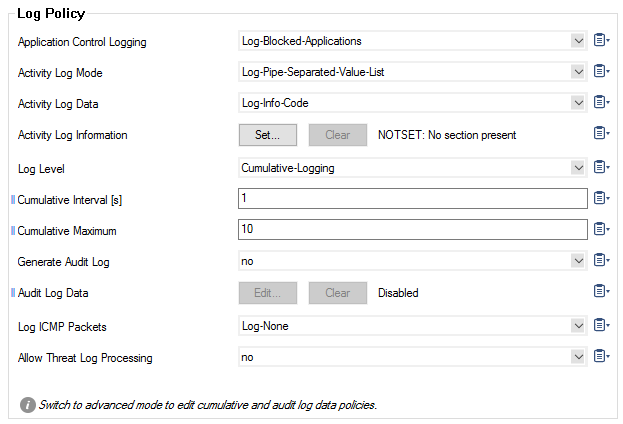
- Application Control Logging – Select which Application Control data should be logged.
- No-Log-Entry – No information about applications will be logged.
- Log-Blocked-Applications – Blocked applications will be logged.
- Log-Allowed-Applications – Allowed applications will be logged.
- Log-All-Applications – All applications will be logged.
Notifications for application ruleset blocks which were logged with type "Detect" and only contain the block information in the info-text are now logged with type "Block". See the following tables with the correspondig codes and reasons:
- Activity Log Mode
Log-Pipe-Separated-Value-List – Select this option if you require value based log entries separated by a pipe symbol, e.g.
2018 01 30 08:14:47 Info +00:00 Detect: IPRX|TCP|eth0|10.17.33.202|29289|00:00:00:00:00:00|74.208.236.242|80||eth0||0|10.17.33.201|74.208.236.242|0|1|0|0|0|0|user15|HTTP direct|Web browsing|www.noiseaddicts.com||Social Networking
Log-Pipe-Separated-Key-Value-List – Select this option if you require key-value pairs of log entries separated by a pipe symbol, e.g.
2018 01 30 13:12:21 Security +01:00 Block: type=FWD|proto=UDP|srcIF=eth0|srcIP=10.17.34.12|srcPort=54915|srcMAC=18:db:f2:13:ca:9c|dstIP=10.17.34.255|dstPort=54915|dstService=|dstIF=|rule=BLOCKALL|info=Block by Rule|srcNAT=0.0.0.0|dstNAT=0.0.0.0|duration=0|count=1|receivedBytes=0|sentBytes=0|receivedPackets=0|sentPackets=0|user=|protocol=|application=|target=|content=|urlcat=
Activity Log Data
Log-Info-Code – In "Log-Info-Code" mode, additional information is written as a number, e.g.
2018 01 30 12:58:09 Info +00:00 Detect: FWD|TCP|eth0|10.17.33.202|44973|00:00:00:00:00:00|74.208.236.242|80||eth0|| 4045 |10.17.33.201|74.208.236.242|0|1|0|0|0|0|user11|HTTP direct|Web browsing|www.noise addicts.com||Social Networking (46)Log-Info-Text – In "Log-Info-Text" mode, the additional information is written as full text, e.g.
IPRX|TCP|eth0|10.17.33.202|57037|00:00:00:00:00:00|31.13.84.36|443||eth0|| URL Category Blocked by Policy |10.17.33.201|31.13.84.36|0|1|0|0|0|0|user2|HTTPS direct|Facebook Base| facebook.com ||Social Networking (46)
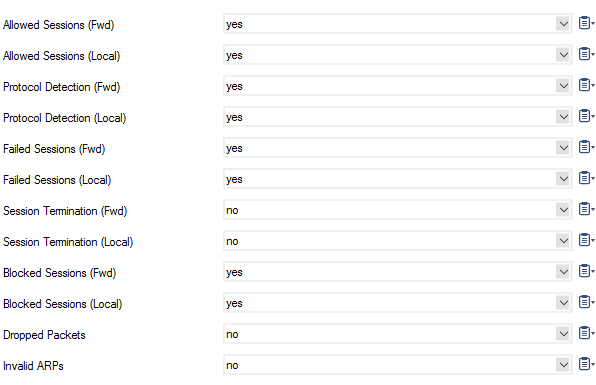
Activity Log Information – Click Set.../Edit to enable or disable specific activities:
Allowed Sessions (Fwd) – Log each newly established forwarding session.
Allowed Sessions (Local) – Log local traffic, e.g., HTTP proxy or DNS.
Protocol Detection (Fwd) – Log protocol detection for each newly established forwarding session.
Protocol Detection (Local) – Log protocol detection for each newly established local session, e.g., HTTP proxy or DNS.
Failed Sessions (Fwd) – Log each allowed request that failed to be established.
Failed Sessions (Local) – Log local traffic.
Session Termination (Fwd) – Log each finished forwarding session.
Session Termination (Local) – Log finished local sessions.
Blocked Sessions (Fwd) – Log each blocked forward session request. This is relevant for auditing.
Blocked Sessions (Local) – Log blocked local traffic.
Dropped Packets – Log each silently dropped packet.
Invalid ARPs – Log each invalid ARP request.
- Log Level – Select the log level. Cumulative logging allows some reduction of log file lengths and tries to avoid indirect denial of service (DoS) attacks.
- Cumulative Interval [s] – Interval in seconds for which cumulative logging is activated for either matching or similar log entries. To enter cumulative logging, the entries need to be identical in all of the identifiers of a log entry except the source port (min: 1; max: 60; default: 1).
- Cumulative Maximum – Maximum number of log entries within the same rule and which results in cumulative logging to be triggered (default: 10).
- Generate Audit Log – Enables Firewall Audit.
An audit event entry consists of a CR-terminated line of ASCII characters. Each line holds 23 pipe ("|") separated values. The values can be built up as a pipe-separated-value-list or as a pipe-separated-key-value-pair-list.Example: 1129102500|Block:|FWD|eth0|ICMP|BLOCKALL|10.0.3.80|0|10.0.3.73|0||4002|Block by Rule|0.0.0.0|0|0.0.0.0|0||00:07:e9:09:04:30|0|0|0|0|0|4552264444
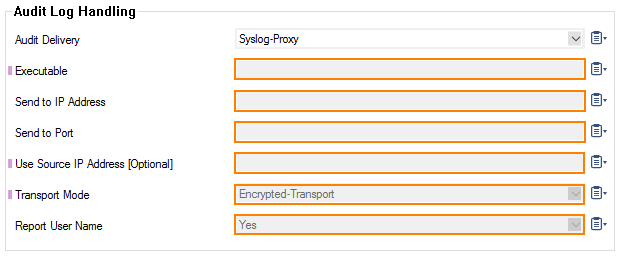
- Audit Log Data – Click Set.../Edit to configure Firewall Audit settings:
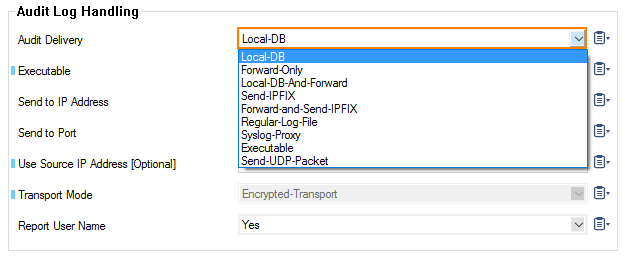
- Audit Delivery – Select how audit log data is stored or transferred:
- Local-DB – Store audit data within a local sqlite3 DB.
- Forward-Only – Forward natively to an audit collector service.
- Local-DB-And-Forward – The combination of both.
- Send-IPFIX – Hand off data to separate IPFIX exporter.
- Forward-and-Send-IPFIX – Combination of forwarding and send data to an IPFIX exporter.
- Regular-Log-File – Plain ascii based log file.
- Syslog-Proxy – Generate syslog messages.
- Executable – Feed into custom executable on stdin.
- Send-UDP-Packet – Send via plain UDP stream.
- Executable – Enter the path of the executable file the data is sent to.
- Send to IP Address – Enter the IP address of the audit service the data is sent to.
- Send to Port – Enter the port the data is sent to. If not specified, port 680 is used.
- Use Source IP Address [Optional] – Enter the source IP address. If not specified, the management IP / Virtual IP address is used.
- Transport Mode – Select whether transported data should be encrypted or not.
- Report User Name – Optionally include the username into the session information if available.
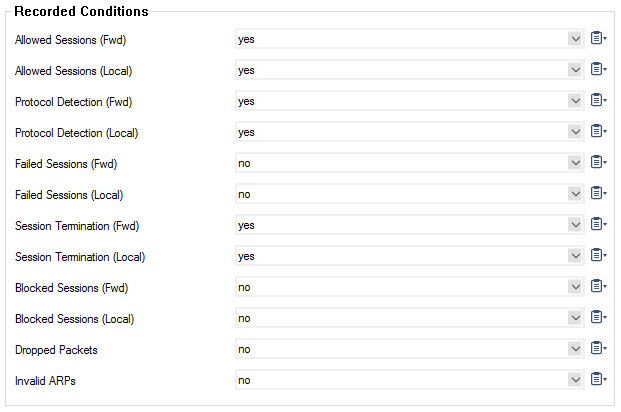
- Allowed Sessions (Fwd) – Create a record for each newly established forwarding session. This is relevant for auditing.
- Allowed Sessions (Local) – Same for local traffic, e.g., HTTP proxy or DNS.
- Protocol Detection (Fwd) – Enable protocol detection for each newly established forwarding session.
- Protocol Detection (Local) – Enable protocol detection for each newly established local session, e.g., HTTP proxy or DNS.
- Failed Sessions (Fwd) – Create an entry for each allowed request that failed to be established. This is relevant for troubleshooting.
- Failed Sessions (Local) – Same for local traffic.
- Session Termination (Fwd) – Create a record on session removal for each finished forwarding session.
- Session Termination (Local) – Create a record on session removal for each finished local session.
- Blocked Sessions (Fwd) – Create a record for each blocked forward session request. This is relevant for auditing.
- Blocked Sessions (Local) – Create a record for each blocked local session request. This is relevant for auditing.
- Dropped Packets – Create an entry for each silently dropped packet.
- Invalid ARPs – Create an entry for each invalid ARP request.
- After Number of Days – Number of days until log file entries will be purged.
- [Optional] Exceeding MBytes – Enter the maximum size of log files in MB until purging starts.
- [Optional] Move Files to Directory – Specify the directory where purged log data is moved to.
- [Optional]Restore Files from Directory – If required, specify the directory from where to restore previously purged log data.
- Forward Buffer [Messages] – Number of messages that can be buffered when forwarding.
- Forward Buffer [KBytes] – Number of KBytes that can be buffered when forwarding.
- ACPF Allowed Msg Buffer [Bytes] – Number of ACPF buffered bytes for allow messages.
- ACPF Blocked Msg Buffer [Bytes] – Number of ACPF buffered bytes for block messages.
- ACPF Dropped Msg Buffer [Bytes] – Number of ACPF buffered bytes for drop messages.
- Audit Delivery – Select how audit log data is stored or transferred:
Log ICMP Packets
- Log-All – Log all ICMP packets except type ECHO.
- Log-Unexpected – Log all ICMP packets except ECHO and UNREACHABLE.
- Log-None – Disable ICMP logging.
Allow Threat Log Processing – Allow other processes to access threat log information for further processing.
Configure IPFIX Streaming
In the IPFIX Streaming section, configure the following settings:
- Enable IPFIX/Netflow – Internet Protocol Flow Information Export (IPFIX, RFC 3917) is based on NetFlow version 9. You can use this to stream the Firewall Audit logs via IPFIX.
- Enable intermediate reports – Select yes to enable sending of intermediate reports with delta counters.
- IPFIX reporting interval [m] – Use the IPFIX reporting interval [m] option to determine how often intermdiate reports are sent.
- IPFIX Template – If set to Extended, includes additional information, such as delta coutners, to the IPFIX export.
If your collector does not support reverse flows, select Uniflow templates, these templates will duplicate the traffic against the collector. - Collectors – Click + to add collectors.
Configure Connection Tracing
- Click Set.../Edit to configure the Connection Tracing settings.
- Data Limit [kB] – Maximum number of bytes of a traced connection (max. 4096kB).
- File Limit – Maximum number of traced connections (max. 1024).

Activation
To activate changes made to the audit and reporting configuration, you must perform a firmware restart.
- Click Send Changes and Activate.
- Go to the CONTROL > Box.
- Expand the Operating System section.
- Click Firmware Restart.