If you are running multiple virtual routers on your CloudGen Firewall, each virtual router instance can be configured independently of any other one. Because the VPN service is available only to the default router, the traffic managed by an additional virtual router instance must be handed over to the VPN service running in the default router so that it can be encapsulated into the VPN TINA tunnel. This is achieved by a VPN interface index that binds the tunnel configuration and the traffic from the additional virtual router instance to the VPN interface running on the default router.
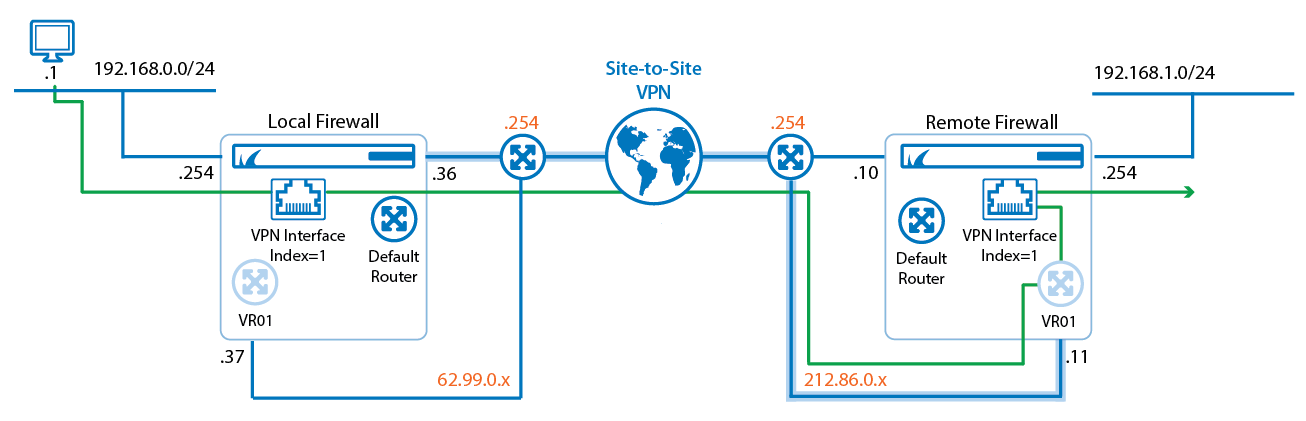
In the following example, a VPN TINA tunnel is used for forwarding traffic between two private networks that are located behind a local and a remote firewall. The local firewall actively initiates a TINA tunnel while the remote firewall passively listens for tunnel connection requests.
The first private network (192.168.0.0/24) is attached to an interface on the local firewall. This interface is managed by an additional virtual router instance (VR01). The second private network (192.168.1.0/24) is attached to an interface on the remote firewall. This interface is also managed by an additional virtual router instance (VR01). On the local firewall, the public IP of the VPN TINA tunnel is managed by the default router, on the remote firewall, the public IP of the VPN TINA tunnel is managed by the virtual router VR01. A client PC sends ping messages to the router address of the private network on the remote firewall (192.168.1.254).
Because the VPN service is only available on the default router, traffic which is coming in through a VPN TINA tunnel on the virtual router on the remote firewall has to be redirected to the VPN service. For this, an access rule has to be configured.
Although not required, it is recommended for a better overview to use the same number for the VPN interface index as the number of your additional virtual router. For example, VR01 should correspond to a VPN interface index equal to 1.
Before You Begin
- Configure an additional virtual router instance on both the local and remote firewall. For more information, see Virtual Routing and Forwarding (VRF) and How to Configure and Activate a Virtual Router Instance with Hardware, Virtual, VLAN or Bundled Interfaces.
- Configure the VPN service for general operation. For more information, see How to Assign Services.
Create a VPN Interface on the Local and Remote Firewall
Execute the following steps for both the local and remote firewall. Start with the local firewall.
- Go to CONFIGURATION > Configuration Tree > Box > your local firewall > Assigned Services > VPN > VPN Settings.
- Click Lock.
- In the left menu, select Routed VPN.
Next to the Interface Configuration table, click Add. The VPN Interface Properties window opens.
- For VPN Interface Index, enter a number. For a better overview, always use the same number as the number of your additional virtual router.
For example, in case your router instance name is VR01, enter1.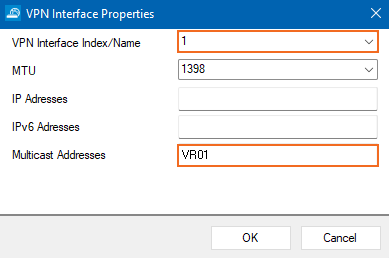
- From the VR Instance list, select your virtual router instance, e.g., VR01.
- Click OK.
- Click Send Changes and Activate.
If not yet done, repeat the previous steps on the remote firewall.
Create a VPN TINA Tunnel on the Local Firewall
- Go to CONFIGURATION > Configuration Tree > Box > your local firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Click the TINA Tunnels tab.
- Right-click the table and select Add new TINA Tunnel. Alternatively, you can click the + sign in the top-right corner of the window.
- Select Add Tunnel.
- In the Tunnel Name field, enter a name for the new VPN tunnel.
- Select a configured Scheme for the local network (optional), or select explicit. To configure a scheme, click the Local Networks tab and create a New Local Network. Then, enter a Name and add the network address.
- In the Local section, add the network address(es) of the private network(s) behind the local firewall, e.g.,
192.168.0.0/24. - In the Remote section, add the network address(es) for the private network(s) behind the remote firewall, e.g.,
192.168.1.0/24.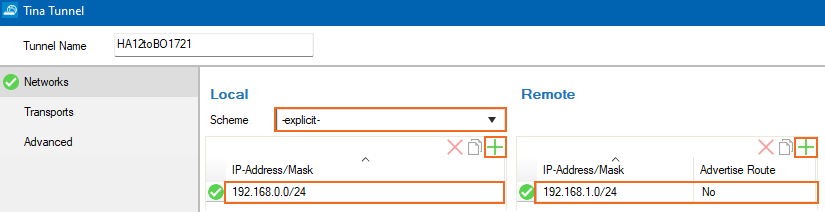
- In the left menu, click Transports.
- Click + to add a new transport for the VPN tunnel. The Edit Transport window opens, showing the Basic tab.
Set the Call Direction to Active.
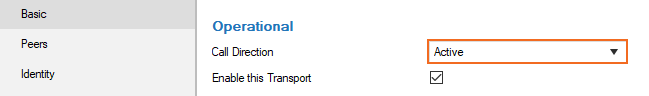
Configure the Basic transport settings. For more information, see TINA Tunnel Settings.
- (optional) Provider – If providers have been configured by a name in CONFIGURATION > Configuration Tree > Network > IP Configuration > Shared Networks and IPs, select a provider for the transport source and SD-WAN classification.ult.
- Transport – Select the transport encapsulation (recommended: UDP).
- Encryption – Select the data encryption algorithm.
- Authentication – Select the hashing algorithm for packet authentication.
In the left menu, click Peers .
Select a configured Template for the transport source, or select explicit and choose the IP address(es) or interface(s) that should be used to establish the VPN connection from the Transport Source list (To configure a template, click the Parameter Templates tab and create a New Tunnel Parameter Template. Then, enter a Name and add the tunnel address.):
- First Server IP – The connection gets established from the first shared IP address.
- Second-IP – The connection gets established from the second shared IP address.
- Dynamic (via routing) – The firewall uses a routing table lookup to determine the IP address.
- Explicit List – Enter one or more explicit IP addresses. Multiple IP addresses are tried in the listed order. Click + and add the IP address(es) or interface(s) used as tunnel address.
- In the Remote section, add the external peer IP Address / Hostname for the tunnel destination, e.g.,
212.86.0.11.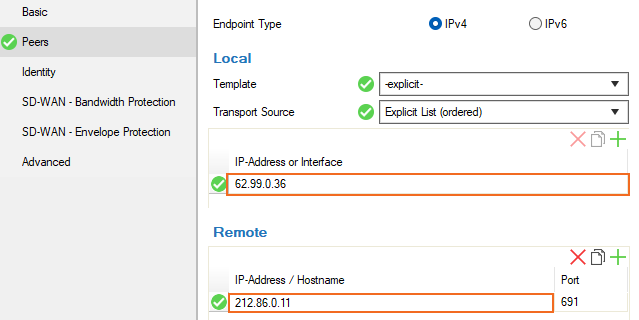
Configure SD-WAN and Advanced transport settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK. The TINA Tunnel configuration window opens.
- Click Advanced.
- Enter the index number, e.g.,
1for the VPN Interface Index.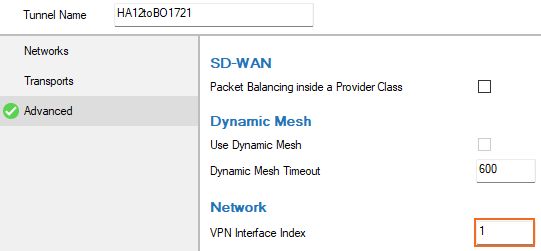
- Configure the remaining tunnel settings to match the settings configured for the local firewall. For more information, see the lower section in TINA Tunnel Settings.
- Click OK.
- Click Send Changes and Activate.
When you are informed that the identification information between the two sites has not been set, click OK to proceed. This information will be configured in a following step.
Create a VPN TINA Tunnel on the Remote Firewall
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Click the TINA Tunnels tab.
- Right-click the table and select Add new TINA Tunnel. Alternatively, you can click the + sign in the top-right corner of the window.
- Select Add Tunnel.
- In the Tunnel Name field, enter a name for the new VPN tunnel.
- Select a configured Scheme for the local network, or select explicit.
- In the Local section, add the network address(es) of the private network(s) behind this firewall, e.g.,
192.168.1.0/24. - n the Remote section, add the network address(es) for the private network(s) behind the other firewall, e.g.,
192.168.0.0/24. - In the left menu, click Transports.
- Click + to add a new transport for the VPN tunnel. The Edit Transport window opens, showing the Basic tab.
Set the Call Direction to Passive.
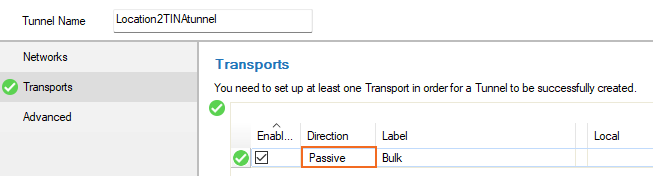
- In the left menu, click Peers.
- In the Local section, chose a configured Template or select explicit and choose the IP address or interface that should be used to establish the VPN connection from the Transport Source list, e.g.
212.86.0.10. - In the Remote section, add the Remote Peer IP Address, e.g.,
62.99.0.36. - Click OK. The TINA Tunnel configuration window opens.
- Click Advanced.
- Enter
1for the VPN Interface Index.
- Configure the remaining transport and tunnel settings to match the configuration for Location 1. For more information, see the lower section in TINA Tunnel Settings.
- Click OK.
- Click Send Changes and Activate.
Exchange the Public Keys Between the Local and Remote Firewall
Start with exporting the public key in the displayed window on the remote firewall.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Edit the transport for the TINA tunnel.
- In the left menu, click Identity.
- From the Identification Type list, select Public Key.
- In the Local section, click the cog wheel icon next to Server Protocol Key, and export the public key to clipboard.
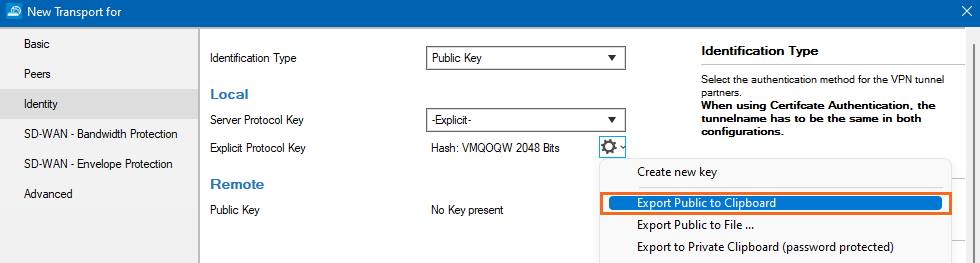
Click OK and close the TINA Tunnel configuration.
- Go to CONFIGURATION > Configuration Tree > Box > your local firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Select TINA Tunnels.
- Open the configuration for the site-to-site tunnel transport created in Step 1.
- In the left menu, click Identity.
- In the Remote section, click the cog wheel icon next to Public Key, and import the key from the clipboard.
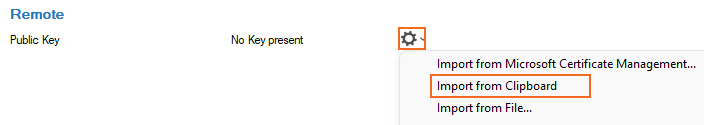
- Click OK.
- Click Send Changes and Activate.
- In the Local section, click the cog wheel icon next to Server Protocol Key, and export the key to clipboard.
- Click OK to close the TINA Tunnel window.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > VPN > Site to Site.
- Click Lock.
- Select TINA Tunnels.
- Open the configuration for the site-to-site tunnel transport.
- Click the Identity tab.
- In the Remote section, click the cog wheel icon next to Public Key, and import the public key from the clipboard.
- Click OK and close the TINA Tunnel window.
- Click Send Changes and Activate.
Verify that the VPN TINA Tunnel is up
- Log into your local firewall.
- Go to VPN > Site-to-Site.
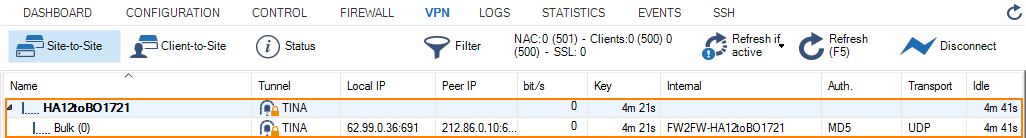
- Log into your remote firewall.
- Go to VPN > Site-to-Site.
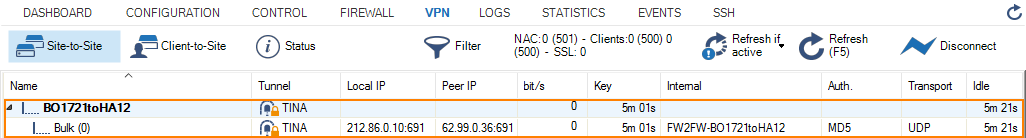
Create a Redirection Rule for the Remote Firewall
The incoming traffic through the VPN TINA tunnel on the remote firewall is received on the public IP (212.86.0.11), which is handled by the virtual router, and therefore must be redirected because the VPN service is available only on the default router . From there, the traffic will be redirected back through the VPN interface to the target IP address (192.168.1.254), which is also assigned to the virtual router VR01. For this, an access rule must be configured.
- Go to CONFIGURATION > Configuration Tree > Box > your remote firewall > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
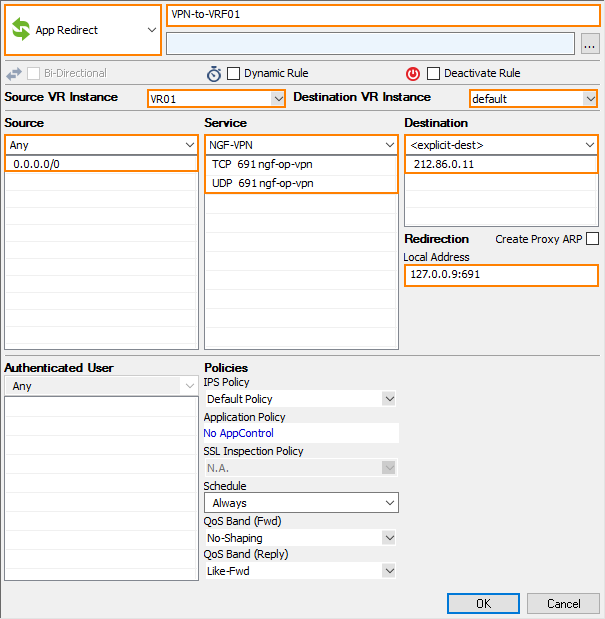
- Click + to add a new access rule.
- For the access rule type, select App Redirect.
- Enter the name for the access rule, e.g., VPN-to-VRF01.
- For Source VR Instance, select VR01 from the list.
- For Destination VR Instance, select default from the list.
- For Source, select Any.
- For Service, select NGF-VPN from the list.
- For Destination, enter the public IP address of the virtual router. Select <explicit-dest> from the list and enter the IP address, e.g., 212.86.0.11.
- For Redirection, enter
127.0.0.9:691to redirect traffic to the VPN server in the default router. - Click OK.
- Click Send Changes.
- Click Activate.
Create an Access Rule for the Local and Remote Firewall to let VPN Traffic Pass
Traffic originating from the private network behind the local firewall must be able to reach the private network behind the remote firewall. The access rule must be configured to be Bi-Directional. In order to forward traffic from the interfaces that are assigned to the additional virtual router instance, the access rule must be applied to this virtual router instance, e.g., VR01. The access rule must be created on both the local firewall and the remote firewall.
- On the local firewall, go to CONFIGURATION > Configuration Tree > Box > your local firewall > Assigned Services > Firewall > Forwarding Rules.
- The Forwarding Rules window is displayed.
- Click Lock.
- Click + to add a new access rule.
- For the access rule type, select Pass.
- Enter the name for the access rule, e.g.,
VPN-S-2-S. - Click Bi-Directional.
- Select the virtual router instance for Source VR Instance and Destination VR Instance, e.g., VR01.
- For Source, click <explicit-src> from the list, and enter the network address for the private network behind the local firewall, e.g.,
192.168.0.0/24. - For Service, select Any from the list.
- For Destination, click <explicit-src> from the list, and enter the network address for the private network behind the remote firewall, e.g.,
192.168.1.0/24. - For the Connection Method, select Original Source IP.
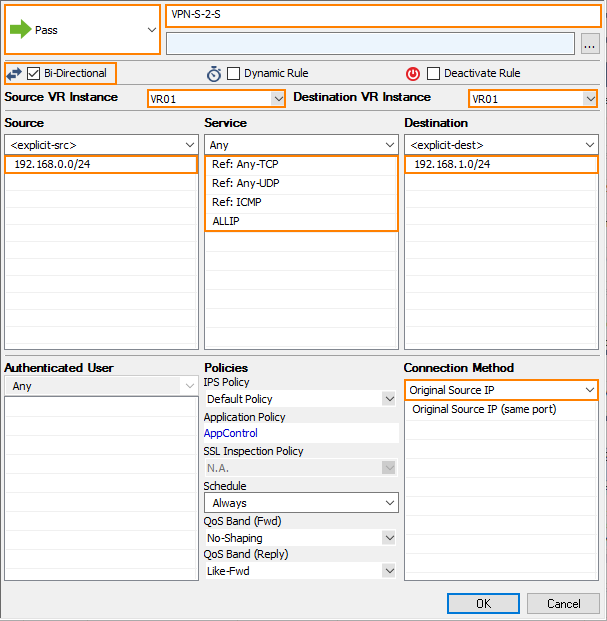
- Click OK.
Repeat the previous steps for the remote firewall.
Verify that the Virtual Tunnel is Forwarding Traffic
- Attach a client host to the private network behind the local firewall, and configure the standard route pointing to the interface that is managed by the additional virtual router instance, e.g., 192.168.0.254.
- Start sending ping messages to the gateway address interface on the remote firewall that is managed by the additional virtual router instance, e.g., 192.168.1.254.
- On the local firewall, go to FIREWALL > Live.
- Set the filter for Src. VR Instance to the name of your additional virtual router instance, e.g., VR01.
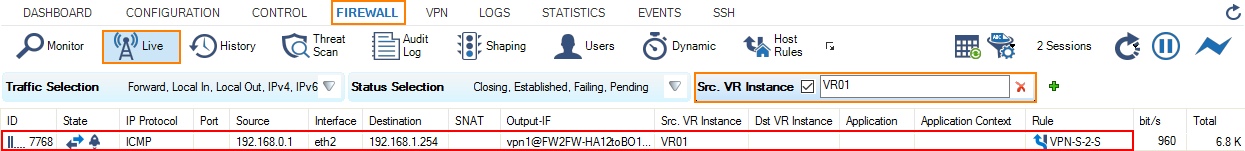
- In the column Output-IF, the firewall displays the name of the VPN tunnel connection, e.g., vpn1@FW2FW-..... Note that the number 1 is part of vpn1@..., indicating the VPN Interface Index that was set to 1 at the beginning. The client PC is sending ping messages from its IP address 192.168.0.1.
- On the remote firewall, go to FIREWALL > Live.
- Set the filter for Dst. VR Instance to the name of your additional virtual router instance, e.g., VR01.
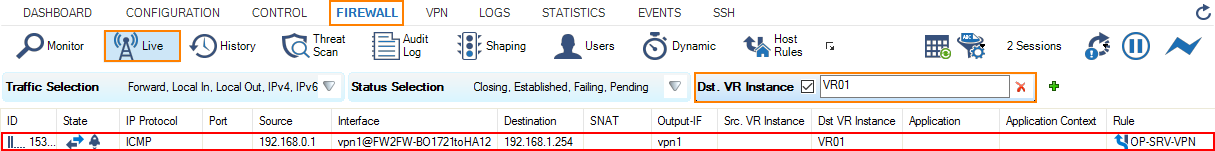
- In the column Interface, the firewall displays the name of the VPN tunnel connection, e.g., vpn1@FW2FW-..... Note that the number 1 is part of vpn1@..., indicating the VPN Interface Index that was set to 1 at the beginning. The column Output-IF displays the name of the VPN tunnel, e.g., vpn1.
(Optional) Verify that a Client Host on the Remote Private Network Can Be Reached
- Attach a client host to the private network behind the remote firewall and configure its IP address, e.g., 192.168.1.1.
- Ensure that there is no local firewall running on the client host. If so, disable the firewall completely on the client host so that all packages can reach the client host.
- Start sending ping messages from the local client host to the remote client host: On your client host, enter
ping 192.168.1.1 - On the remote firewall, go to FIREWALL > Live.
- Set the filter for Dst. VR Instance to the name of your additional virtual router instance, e.g., VR01.
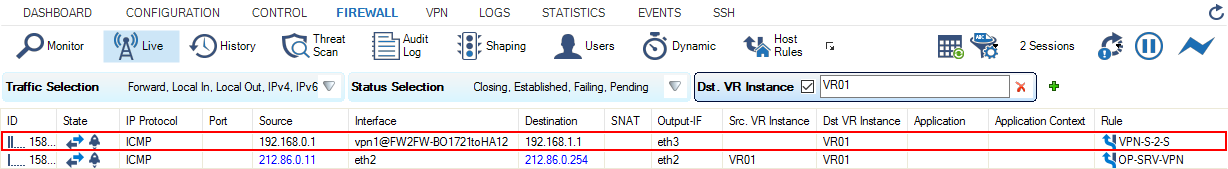
- In the column Interface, the firewall displays the name of the VPN tunnel connection, e.g., vpn1@FW2FW-. Note that in this case the access rule is now VPN-S-2-S, which indicates that the ping packages are now forwarded from the VPN service on the remote firewall to the remote client host while traversing the interface eth3 on the virtual router VR01.
