What ATR does
ATR determines whether an alert is malicious.
If the alert is identified as malicious, the IP Address is automatically added to the firewall or network security solution block list, depending on how malicious ATR determines it to be.
For more information about Automated Threat Response (ATR), see Setting up ATR.
Setting up ATR
The documentation below outlines the requirements for the Barracuda XDR Automated Threat Response (ATR) for Barracuda CloudGen Control Center Firewall. When you've set this up, all required data is uploaded to the Customer Security Dashboard in the ATR Settings > Firewalls section.
You'll have to do the following things to prepare your CloudGen Firewall for Barracuda XDR's Automated Threat Response:
To create a custom administrative role to access the REST API
To create an admin account to access the REST API
To create a firewall network object for Barracuda XDR Automated Threat Response
To enable the REST API for HTTPS
To generate an API token for authentication
To ensure communication is allowed from XDR ATR IP(s) to the CloudGen firewall
To configure the XDR Dashboard
To create a custom administrative role to access the REST API
In Barracuda Control Center, navigate to CONFIGURATION > Configuration Tree > Multi-Range > Global Settings > Administrative Roles.
Click Lock.
In the Roles section, click + to create a new role.
Enter a number for the role in the Name field and click OK.
The Roles configuration window opens.Enter the Role Name: BarracudaXDRAdmin.
(Optional) Enter a Description. Ex: Barracuda XDR Automated Threat Response.
Scroll down to add the REST API access rights to the administrative role:
In the REST API section, select the Access to REST API check box.
Click Set/Edit to configure detailed permissions.
Configure the Write Access – Provides write access on the selected interface.
To add the CC Configuration access rights to the administrative role, in the CC Configuration section, select the Access to CC Configuration check box.
Click OK.
Click OK.
Click Send Changes and Activate
To create an admin account to access the REST API
In Barracuda Control Center, navigate to the ADMINS tab.
Do one of the following:
Click + New Admin on the top right of the window.
Right-click the list, and select Create New Admin.
The Create New CC Admin window opens.
For local authentication, configure the username and password:
Login - BarracudaXDRAdmin
Full Name - BarracudaXDRAdmin
Authentication Level - select Password. Click the cogwheel icon next to the Password field, define a password for the administrative user, and click OK.
Configure the following additional settings:
Assigned Range - This option, in combination with linked ranges, controls which entries an administrator can see in CONFIGURATION > State Info > Sessions, in the Configuration Sessions window.
Login Event – Select Service Default.
ACL - Add the IP addresses 35.155.74.247 and 44.239.173.232 to the Peer IP Restriction list.
This specifies the IP addresses the admin can use to access the Barracuda CloudGen Firewall.
After creating the Admin account, one or more specific scope(s) must be defined to be associated with the administrator.
In the window, click the Administrator Scopes tab.
Click + next to Instances.
A new instance of the category Global is displayed.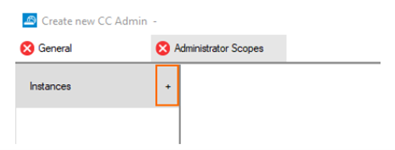
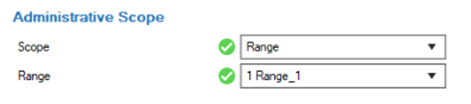
Configure the Administrative Scope.
Set the scope to Global, a specific Range, or Cluster. Alternatively, select Ranges and/or Clusters with the Global/Range Link option for the administrative scope.
Click + to add selected nodes to the Links list.
The options Global Linked and Range Linked associate the configured administrative rights with any individually selected node (in the Links list) at or below a configured Global Linked or Range Linked node (in the Range list).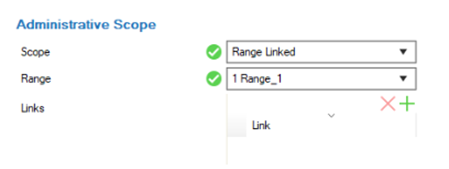
Configure Administrative Rights.
Configuration Level: A configuration level of 2 or lower means write access, 99 or lower means read access. Usually, the write level is lower than the read level. For more information on the configuration level: https://campus.barracuda.com/product/cloudgenfirewall/doc/96026459/control-center-admins .
Assign Roles: Click + and add the role created in To Create a Custom Administrative Role to Access the REST API: BarracudaXDRAdmin.
Shell Level: Select No.
Click OK.
The CC admin user you just created can now access the REST API interface for the ranges and clusters assigned to the user.
To create a firewall network object for the Barracuda XDR Automated Threat Response
Create a Firewall Network Object called Barracuda_XDR_Blocked_IPs. Barracuda XDR uses this network object to track of IPs blocked on the firewall. Add the network object to any preexisting firewall rules that were created to block traffic to/from anomalous IP addresses. Control Center ATR supports creating firewall objects for the range, cluster, or box level.
In Barracuda Control Center, navigate to Configuration > Configuration Tree > Multi-Range > (Range, Cluster, or Box Level) > Firewall Objects/Policies.
Based on the customer firewall set up, create a Firewall Network Object within the administrative scope that was chosen for the configuration.Click Lock.
In the left menu, scroll to Firewall Objects and click Networks.
Click + in the Networks section to create a network object.
For the Type, select Generic Network Object.
Type the name
Barracuda_XDR_Blocked_IPsfor the network object.(Optional) Type a description for the Network, for example, Barracuda XDR Automated Threat Response.
Click OK.
Click Send Changes and Activate.
Add the Network Object to any preexisting firewall policies created to block traffic to/from anomalous IP addresses.
Save the Network Object Name to use in the To configure the XDR dashboard procedure below.
To enable the REST API for HTTPS
Reference: https://campus.barracuda.com/product/cloudgenfirewall/doc/96025925/rest-api/
On the Firewall layer of the Barracuda Control Center, navigate to Configuration > Configuration Tree > Box > Infrastructure Services > REST API Service.
Click Lock.
In the HTTP interface window, select Enable HTTPS interface.
In the HTTPS Port field, enter the desired port for API calls.
(Optional) To enable API calls via management IP addresses instead of the loopback interface, select Bind to Management IPs.
Click New Key to create a private key of the desired length or import your personal private key.
Click Ex/import to create a self-signed certificate or import an existing one.
NOTE If creating a new self-signed certificate, it is recommended to use the public IP of the box as the name. (A hostname can also be used if that correlates with the public IP of the box).Click Send Changes and Activate.
Save the port number to use in the To configure the XDR dashboard procedure below.
To generate an API token for authentication
On the Firewall layer of the Barracuda Control Center, navigate to Configuration > Configuration Tree > Box > Infrastructure Services > REST API Service.
Click Lock.
In the left menu, click Access Tokens.
Click + in the Access tokens section.
Type the name BarracudaXDRAPI for the token and click OK.
The Access tokens window opens.Click Generate new token.
Enter the Admin name for the user used for authentication.
This is the name of the Admin Account previously created (BarracudaXDRAdmin)In the Time to live field, enter the number of days the token should be valid for.
Click OK.
Click Send Changes and Activate.
To ensure communication is allowed from XDR ATR IP(s) to the CloudGen firewall
If you have a firewall in front of your CloudGen device, you must set up an App Redirect rule on the firewall to allow traffic from the ATR endpoint to the management IP of the Control Center or (if it’s a Standalone FW) the management IP of the box.
The procedure for setting up the App Redirect rule depends on your firewall – consult the documentation for your firewall for more information. The procedure below is provided as an example for the CloudGen data source only.
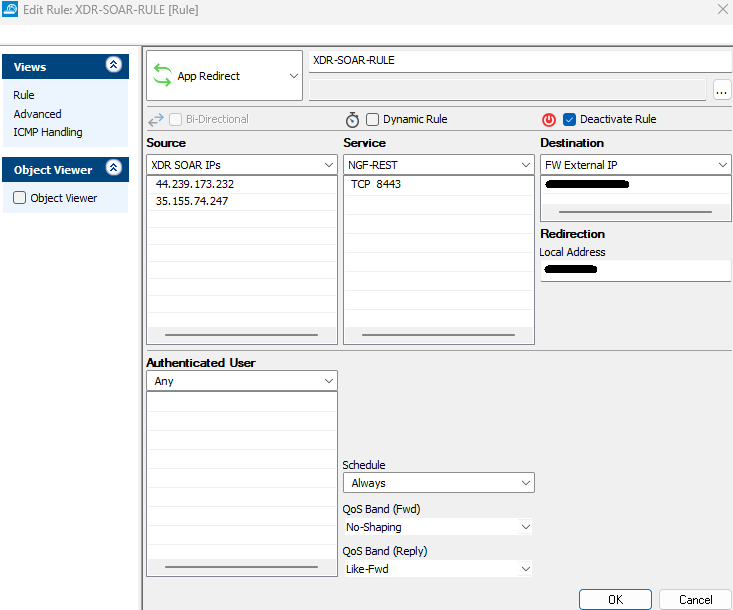
For example, if the firewall in front is also a CloudGen, you could create an App Redirect rule where:
The type – App Redirect
The source is the ATR endpoint(s) – 35.155.74.247 and 44.239.173.232
The service – TCP 8443
The destination – firewall’s public IP address
The redirection – the management IP of the firewall (This will be the management IP if "Bind to management address" is selected in the API service setup. If not, use the lookback IP address.)
To configure XDR dashboard
In Barracuda XDR Dashboard, click ATR Settings > Firewalls.
In the Firewalls table, click the Barracuda CloudGen Firewall row.
Click Edit Config.
Enter the following data:
External IP
API Access Port
Credential (API Key)
Group Name
NOTE This data must match the name of the Network Object.
In Firewall Type, select Control Center.
In Group Level, select one of the following options:
Range, then type the range name
Cluster, then type the range name and the cluster name
Box, then type a name for the range, the cluster name, and the service container name
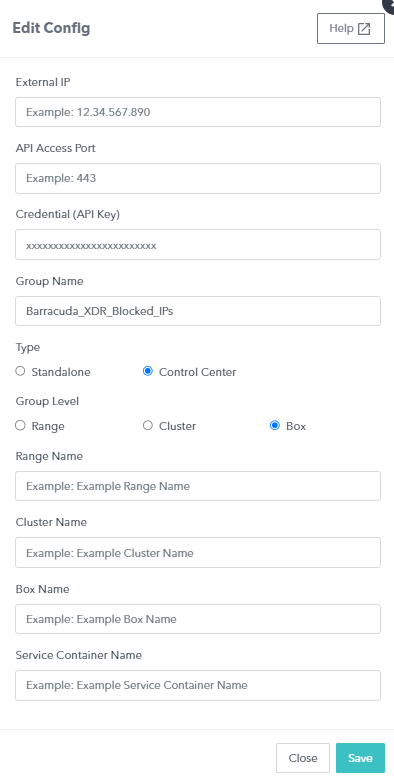
Click Save.
