This topic contains the following Threat Simulations:
Microsoft 365 Login from a Suspicious Country
External Forwarding Rule Creation
Microsoft 365 Login from a Suspicious Country
This use case tests for the ability to detect when a threat actor logs in from a suspicious country. Once a threat actor logs in to an Office 365 account, they have full access to the email account.
Test Workflow
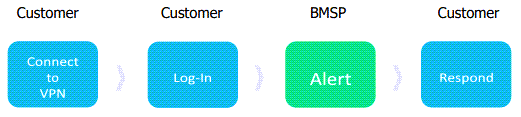
How to Test
When onboarding for Office 365 Monitoring, there are various actions that we can monitor to make sure users are abiding by your company’s protocols and standards. Making sure users are logging in from their known, authorized countries will ensure the safety and security of all within the organization.
The alarm for “GLB.AU.CAS Successful Office 365 Login from a Suspicious Country” detects successful logins from a country with a known reputation of suspicious activity based on SOC threat intelligence.
To test this rule, a user can use a VPN to log in from the Ukraine, Vietnam, Russia, etc.
Start your VPN application and connect to a VPN server located in the country you want websites to think your located in.
Connect to a server from a country outside the United States, for example Ukraine.
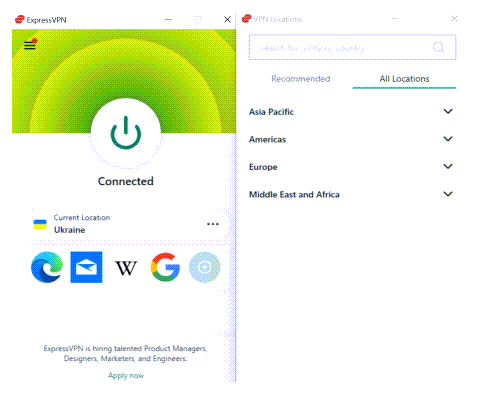
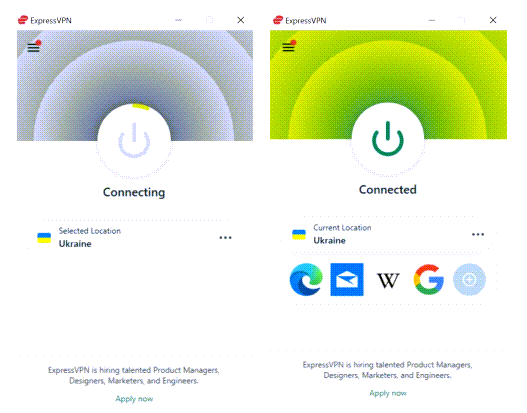
Once you choose the country, click the power button to connect to the VPN. Wait until it is connected to the current location.
The expected result is that Barracuda XDR triggers to the SOC if you log on to your Microsoft 365 account from outside the US and the country is on our Suspicious Country list classified within our threat environment.
External Forwarding Rule Creation
This use case tests the ability to detect an email forwarding rule. Auto forwarding enables an attacker to secure a foothold inside an account even after they lose direct access. It is often a stepping stone to execute lateral movement within your environment. This threat vector is usually financially motivated.
Test Workflow
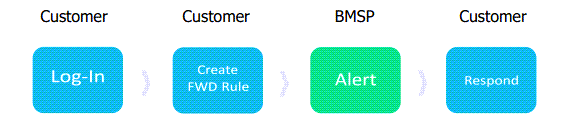
How to Test
An Office 365 Forwarding rule lets you forward email messages sent to a user’s mailbox to another user’s mailbox inside or outside of your organization. This activity should always be escalated, since these actions could be performed by the user themselves or an unauthorized threat actor.
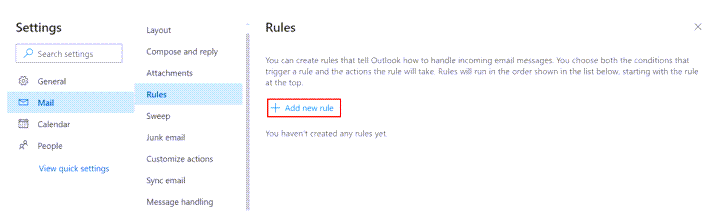
At the top right of the page in the Outlook Web App, select Settings.
Click View All Outlook Settings.
Choose the Mail tab, then Rules, and Add New Rule.
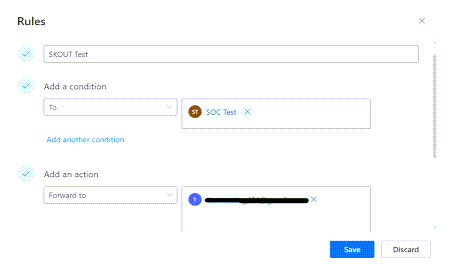
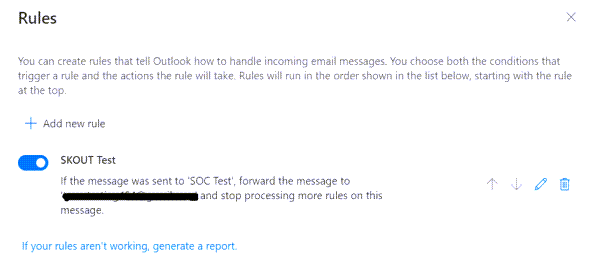
Create a new rule to forward email from your account to another email address. Once complete, save your changes.
Simulating Other Threats
You can simulate the following threats:
