The use case for this simulation is traffic detecting communication with a Malware IP address.
Malicious actors do not just enter your network quietly. Cyber attacks intend to exfiltrate data. Monitoring for unusual traffic patterns leaving a network is a primary indicator of a compromise. Compromised systems often “talk” to the command-and-control servers that provide commands to infected devices & these devices communicate to known Indicators of Compromise IOCs (Website/IPs).
Test Workflow
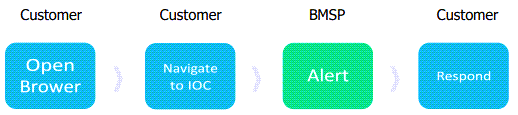
How to Test
From the network where you are spanning traffic, in the device's browser, navigate to cuda-labs.com.
This triggers a Barracuda XDR alarm that detects network traffic to the Malware Testing IP address.
Simulating Other Threats
You can simulate the following threats:
