What ATR does
ATR determines whether an alert is malicious.
If the alert is identified as malicious, the IP Address is automatically added to the firewall or network security solution block list, depending on how malicious ATR determines it to be.
For more information about Automated Threat Response (ATR), see Setting up ATR.
Setting up ATR
The documentation below outlines the requirements for the Barracuda XDR Automated Threat Response (ATR) for Barracuda CloudGen Standalone Firewall. When you've set this up, all required data is uploaded to the Customer Security Dashboard in the ATR Settings > Firewalls section.
To configure ATR for Barracuda CloudGen Standalone Firewall, you must do the following:
To enable the REST API for HTTPS
To create an Admin Account for the REST API
To generate an API Token for authentication
To create a Firewall Network Object for the Barracuda XDR Automated Threat Response
To ensure communication is allowed from XDR ATR IP(s) to the CloudGen firewall
To ensure malicious IPs are blocked
To configure XDR Dashboard
To enable the REST API for HTTPS
Reference: https://campus.barracuda.com/product/cloudgenfirewall/doc/96025925/rest-api/
In Barracuda CloudGen, navigate to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > REST API Service.
Click Lock.
In the HTTP interface window, select Enable HTTPS
In the HTTPS Port field, enter the desired port for API calls.
(Optional) To enable API calls via management IP addresses instead of the loopback interface, select Bind to Management IPs.
Click New Key to create a private key of the desired length or import your personal private key.
Click Ex/import to create a self-signed certificate or import an existing one.
NOTE If creating a new self-signed certificate, it is recommended to use the public IP of the box as the name. (A hostname can also be used if that correlates with the public IP of the box).Click Send Changes and Activate.
To create an Admin Account for the REST API
Go to CONFIGURATION > Configuration Tree > Box > Administrators.
Click Lock.
In the Administrators section, click + to add an administrator account.
Type the name BarracudaXDRAdmin for the account and click OK.
The Administrators window opens. This account name is used to log into the firewall.Type the Full Name of the administrator or a description for the account (BarracudaXDRAdmin).
In the Assigned Roles table, add the Manager administrative role for the user.
From the System Level Access list, select No OS Login.
For the Authentication Level, choose Password.
When using a password, select the corresponding scheme from the Password Validation list.
Enter the password for the Barracuda Firewall Admin login. When creating an account, the new password must be entered in both the Current and New fields, even though the password has not yet been created. The password must be confirmed by re-entering it in the Confirm field.
Use the Peer IP Restriction table to set an access restriction on IP address and/or subnet level on which Barracuda Firewall Admin runs.
NOTE Add the IP addresses 35.155.74.247 and 44.239.173.232 to the Peer IP Restriction list. This specifies the IP address the admin can use to access the Barracuda CloudGen Firewall.
From the Login Event list, select Service Default (default).
Click Send Changes and Activate.
To generate an API Token for authentication
Navigate to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > REST API Service.
Click Lock.
In the left menu, click Access Tokens.
In the Access Tokens section, click +.
Type the name BarracudaXDRAPI for the token and click OK.
The Access Tokens window opens.Click Generate new token.
Enter the Admin name for the user used for authentication.
This will be the name of the admin account created in To create an Admin Account for the REST API above (BarracudaXDRAdmin).
In the Time to live field, enter the number of days the token should be valid for.
Click OK.
Click Send Changes and Activate.
To create a Firewall Network Object for the Barracuda XDR Automated Threat Response
Create a Firewall Network Object called Barracuda_XDR_Blocked_IPs. Barracuda XDR uses this network object to track of IPs blocked on the firewall. Add the network object to any preexisting firewall rules that were created to block traffic to/from anomalous IP addresses.
NOTE Don’t include a space in the Network Group Policy name or ATR won’t function properly. We highly recommend using Barracuda_XDR_Blocked_IPs.
Navigate to CONFIGURATION > Configuration Tree > Box > Assigned Services > NGFW (Firewall) > Forwarding Rules.
Click Lock.
In the left menu, scroll down to Firewall Objects and click Networks.
In the Networks section, click + to create a network object.
For the Type, select Generic Network Object.
Type the name Barracuda_XDR_Blocked_IPs for the network object.
(Optional) Enter a description for the Network.
Click OK.
Click Send Changes and Activate.
Add the Network Object to any preexisting firewall policies created to block traffic to/from anomalous IP addresses.
To ensure communication is allowed from XDR ATR IP(s) to the CloudGen firewall
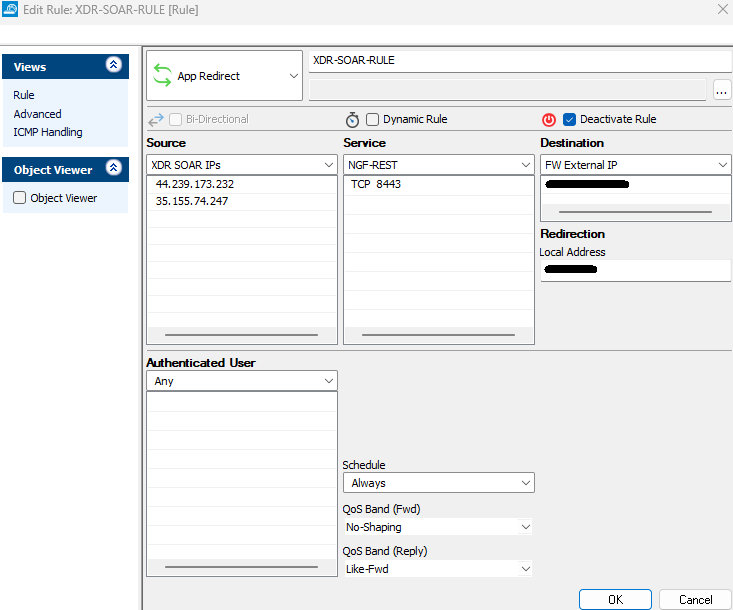
Set up an App Redirect rule on the firewall to allow traffic from the ATR endpoint to the management IP of the Control Center or (if it’s a Standalone FW) the management IP of the box.
The procedure for setting up the App Redirect rule depends on your firewall – consult the documentation for your firewall for more
information. The procedure below is provided as an example for the CloudGen data source only.
For example, if the firewall in front is also a CloudGen, you could create an App Redirect rule where:
The type – App Redirect
The source is the ATR endpoint(s) – 35.155.74.247 and 44.239.173.232
The service – TCP 8443
The destination – firewall’s public IP address
The redirection – the management IP of the firewall (This will be the management IP if "Bind to management address" is selected in the API service setup. If not, use the lookback IP address.)
To ensure malicious IPs are blocked
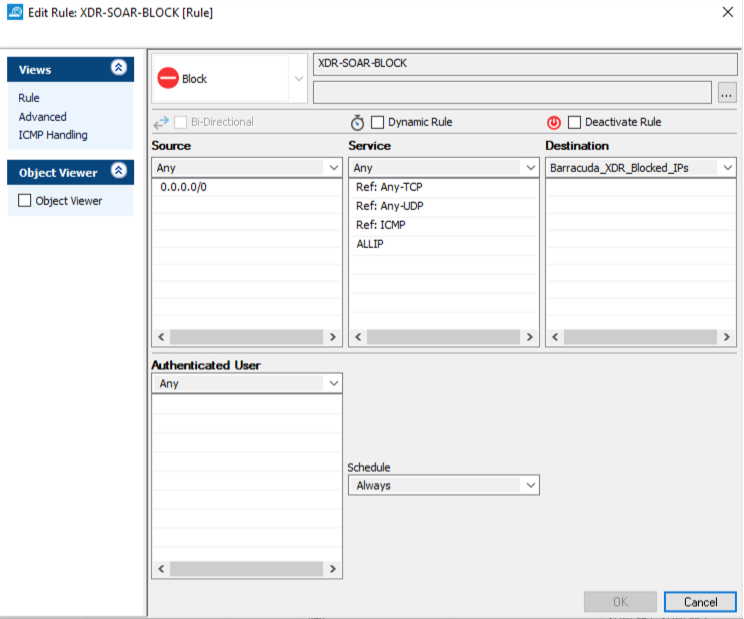
To ensure malicious IPs are blocked, add the Barracuda_XDR_Blocked_IPs to a deny policy on the firewall. For example, your policy could look like this:
The type – Block
The source is any
The service is any
The destination is the Barracuda_XDR_Blocked_IPs group created earlier
To configure XDR Dashboard
In Barracuda XDR Dashboard, click ATR Settings > Firewalls.
In the Firewall table, click the Barracuda CloudGen Firewall row.
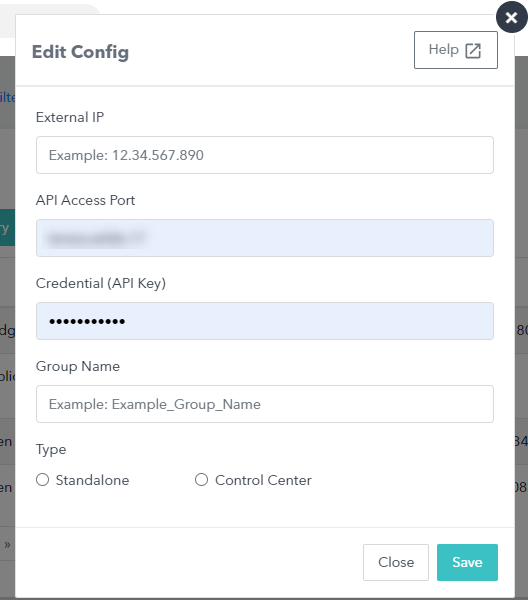
In the Edit Config dialog box, enter the following:
External IP
API Access Port
Credential (API Key)
Group Name
Firewall Type
Click Save.
