With devices increasingly being moved over to the Windows 10 Kernel (Windows 10, Windows Server 2016, and Windows Server 2019), we have been noticing environments exhibiting patching issues. Devices are not checking in for patch status and are merely not patching overall. We can attribute it to Dual Scan within these operating systems.
To understand Dual Scan, please read the "Demystifying Dual Scan" Microsoft article found here: https://docs.microsoft.com/en-us/archive/blogs/wsus/demystifying-dual-scan
Within Barracuda RMM, if you are using Patch Management, you will need to ensure that Dual Scan is disabled. But how?
First option
Run the WSUS Client Diagnostic tool located on our Knowledge Base.
Second option
Check devices for Dual Scan by doing the following.
- Open PowerShell as Administrator
- Paste in this two-line script
$MUSM = New-Object -ComObject "Microsoft.Update.ServiceManager"
$MUSM.Services | select Name, IsDefaultAUService
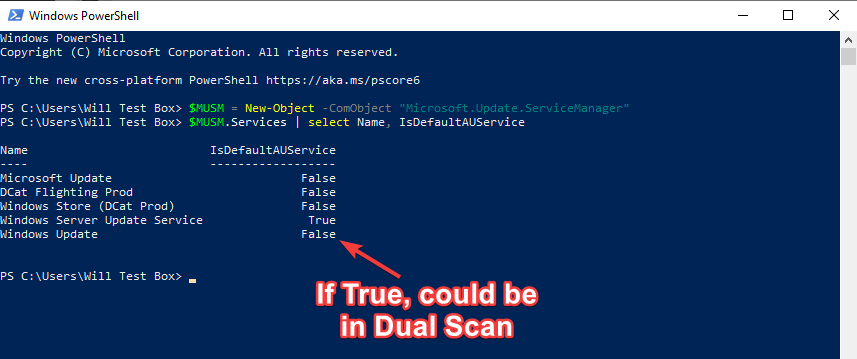
If Windows Server Update Service (WSUS) shows True and other options are false, then Dual Scan is not being utilized? If Windows Update is set as true, Dual Scan is likely enabled.
The Fix
Start by checking the latest version of the Domain Configuration Guide to ensure that you are compliant with those settings. If you are, then deploy the Disable Dual Scan for Windows Update script via Barracuda RMM.
You can now do the following to acquire the script:
- In your Service Center UI go to Update Center.
- Click Components.
- Click Get More.
- In the Search Box search for Dual Scan.
- Select the Disable Dual Scan for Windows Update script and Install.
- Run the script from the Automation Calendar against targeted Windows 10 Kernel devices.
If you are on-premise and want a copy of the script, you can contact the support desk or you can set up a custom script with the following Registry Key entry to disable the Dual Scan behaviour:
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate /v DisableDualScan /t REG_DWORD /d 1 /f