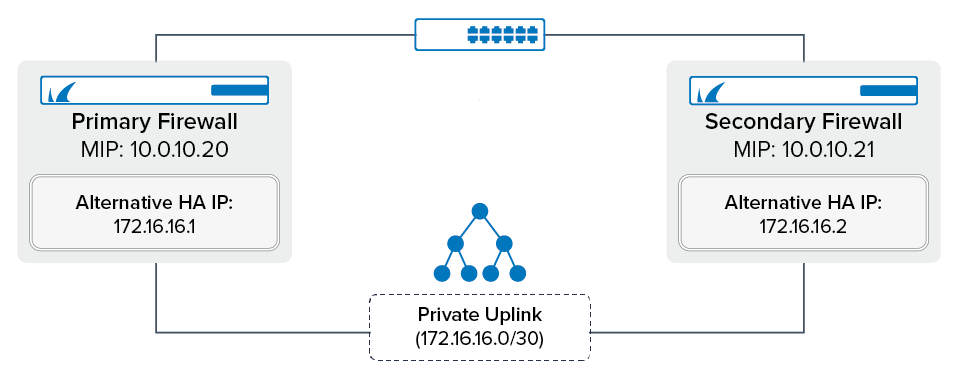
After setting up an HA cluster, you can also configure a private uplink to safeguard against failure of the switch connecting the two HA units. For the private uplink, you must configure a network (at least 2-bit) as a subnet and configure the CloudGen Firewall to use this connection to send the HA sync packets.
The configuration of the private uplink must be done on the primary firewall for the HA pair. The configuration is automatically transmitted to the secondary firewall.
Before You Begin
Barracuda Networks recommends directly connecting both firewalls with a network cable for the private uplink.
A /30 network is required. E.g., 172.16.16.0/30
Step 1. Define the Alternative HA IP Addresses for the Primary and Secondary Firewall
Log into the primary firewall.
Go to CONFIGURATION > Configuration Tree > Box > Network.
Click Lock.
In the left menu, expand the Configuration Mode section and click Switch to Advanced View.
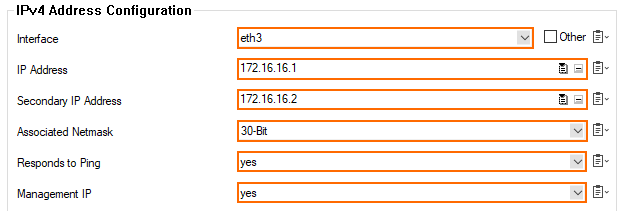
Click + to add the private IP address as an Additional Local IP. The IP Address Configuration window opens.
Interface – Select the interface the crossover cable is connected to.
IP Address – Enter the Alternative HA IP address for the unit. E.g.,
172.16.16.1Associated Netmask – Select /30.
Responds to Ping – Set to yes.
Management IP – Set to yes.
Click OK.
Click Send Changes and Activate.
Step 2. Activate the Private Uplink
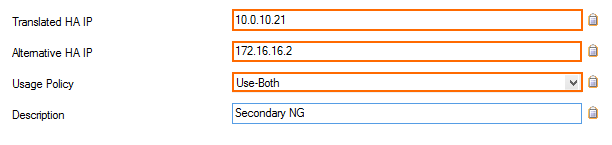
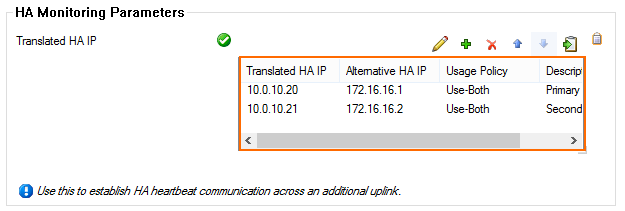
For the HA sync to work over the private link, you must associate the private link IPs with the corresponding management IP addresses. The UI label Translated HA IP stands for the management IP address of each firewall in HA pair. The UI label Alternative HA IP stands for the respective private uplink IP address.
Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Control.
Click Lock.
In the HA Monitoring Parameters section, add entries for the primary unit and secondary unit:
Translated HA IP – Enter the management IP address E.g., 10.0.10.20 for the primary unit
Alternative HA IP – Enter the additional local network IP of the unit. E.g., 172.16.16.1 for the primary unit
Usage Policy – Select from the following options:
Use-Both – Sends the HA sync and heartbeat over both the management IP link and the private uplink.
Use-Alternative-Only – Sends the HA sync and heartbeat only over the private uplink.
Disabled – The HA sync and heartbeat are sent over the management IP link only.
Click OK.
Click Send Changes and Activate.
Step 3. Add the Alternative HA IP Address to the ACL List
To grant administrative access rights for Alternative HA IP address usage, add the Alternative HA IP address to the ACL list.
Go to CONFIGURATION > Configuration Tree > Box > Administrative Settings.
Click Lock.
Add the /30 network containing the alternative HA IP addresses.
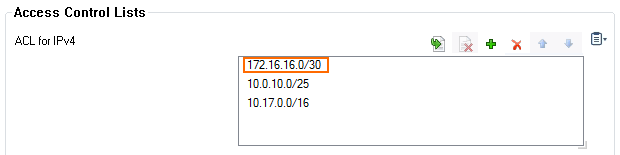
Click Send Changes and Activate.
Step 4. Activate the Network Configuration
Activate the network configuration on the primary and secondary CloudGen Firewall.
Go to CONTROL > Box.
In the menu, expand Network and click Activate new network configuration.
Select Failsafe as the activation mode.
