What's New in Version 9.0.3
Secure Internet Traffic from LANs
As of the 9.0.3 release, administrators can configure Secure Internet Traffic from LANs on the Private Edge Service. By default, Secure Internet Traffic from LANs is disabled. The main advantages of using this feature are as follows:
You can secure Internet Traffic from the LANs of downstream Sites and downstream Private Edge Services on a Private Edge Service
Enables backhauling and securing of all Internet traffic from the downstream Site's LAN networks.
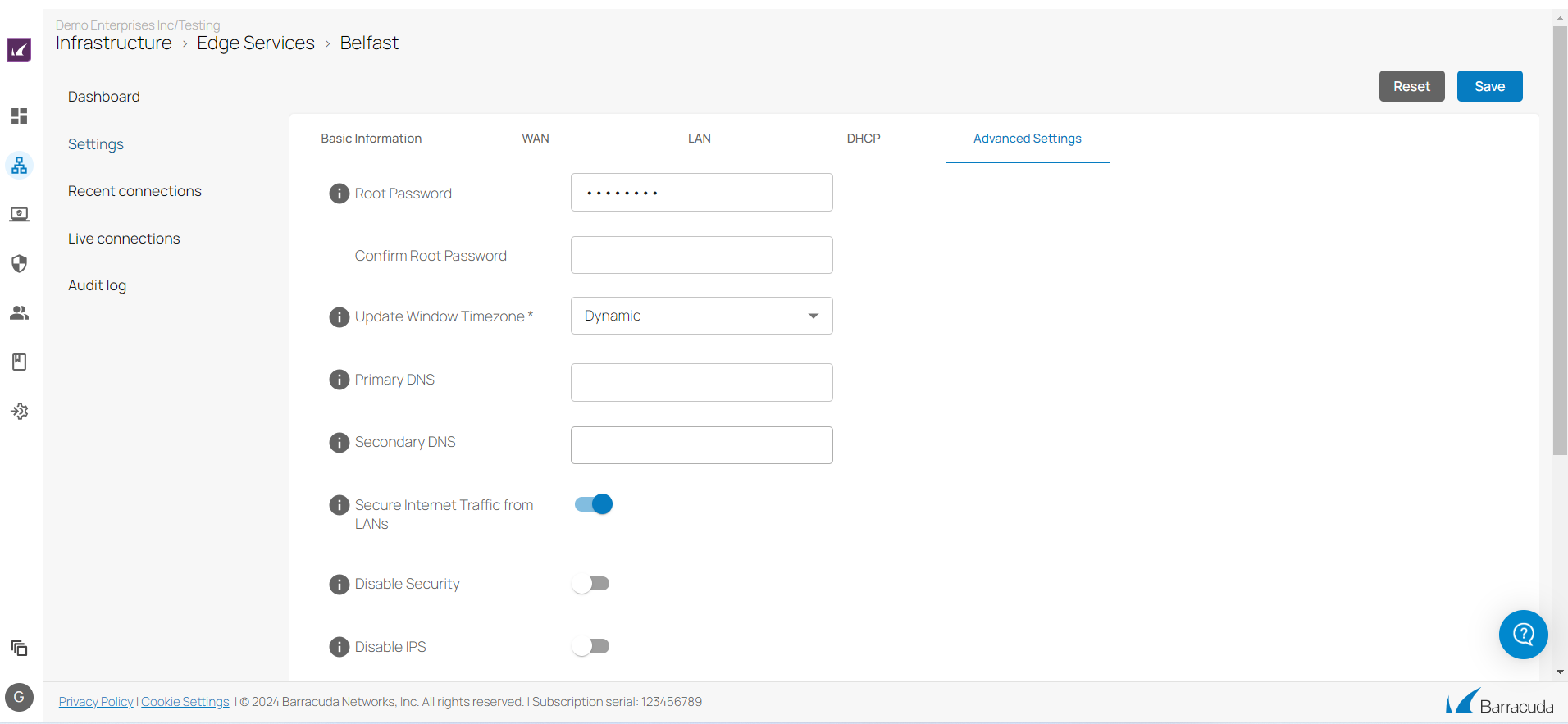
For more information, see How to secure Internet traffic of LANs over a private Edge Service.
SIP Proxy
The Barracuda SecureEdge Manager now allows administrators to enable/disable the SIP Proxy feature for all connected infrastructures with respect to an individual workspace. In addition, the timeouts for UDP traffic is configurable. The main key features of the SIP Proxy are:
When SIP Proxy is enabled for the workspace, it uses a default timeout of 60 seconds. The option to provide UDP Timeout is disabled.
You can provide UDP Timeout only when the SIP Proxy is disabled.
The supported infrastructure includes: Barracuda-hosted Edge Service, Virtual WAN for Edge Service, and SecureEdge appliances such as Sites, Stand-alone Sites, and Private Edge Services.
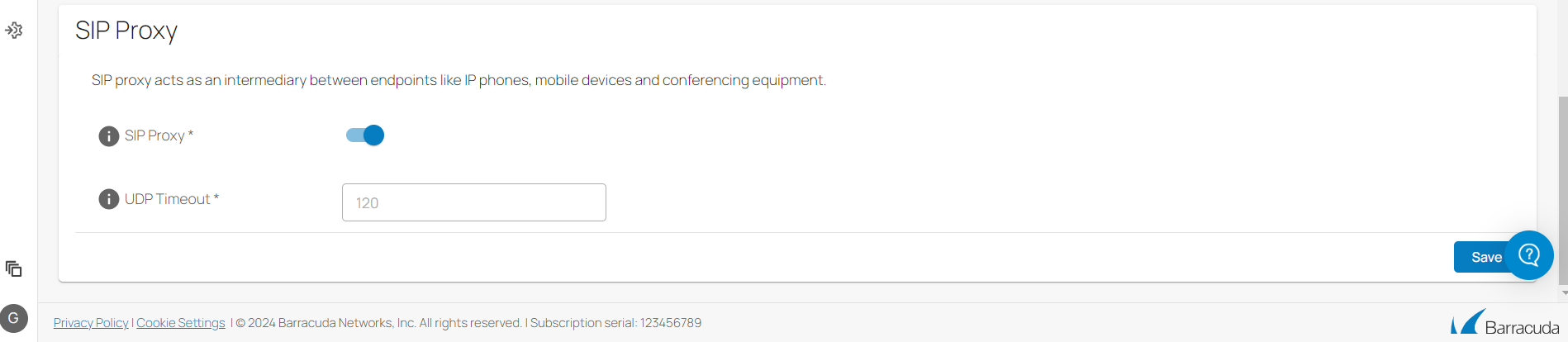
For more information, see How to Configure SIP Proxy.
Identity Management 1.1
A new, enhanced Identity Management 1.1 is now available. The following improvements have been added:
With SecureEdge Identity Management, you can now create local users and groups. For more information see, How to Create Local Users or Groups.
The Edit option is now available for both identity providers and user directories.
Enhanced filtering features, including the ability to apply a group filter to a directory.
With SecureEdge Identity Management, you can now configure and authenticate Okta Workforce.
You can now add multiple identity providers and user directories on the Identity > Settings page.
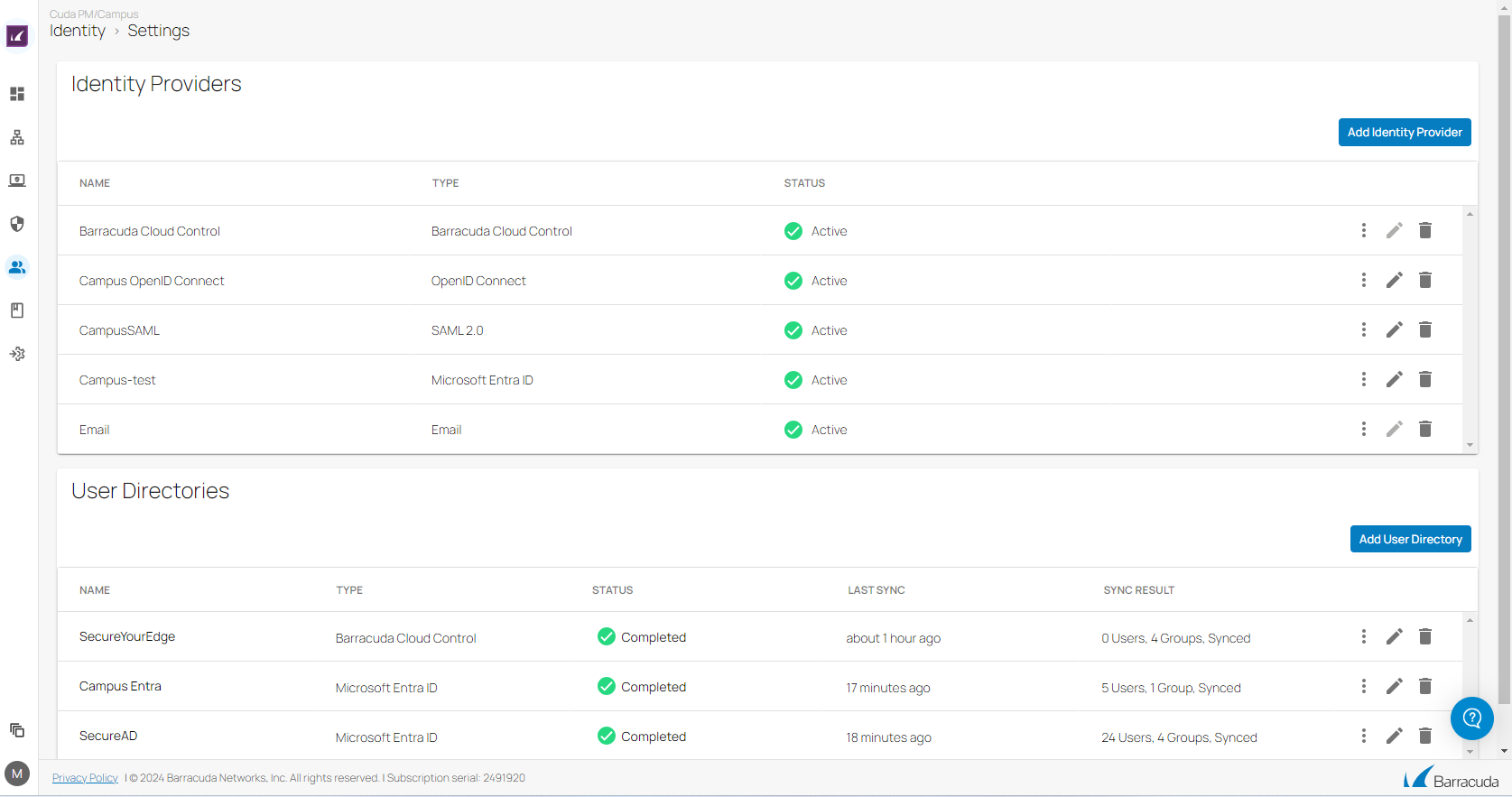
For more information, see Identity Management.
Zero Trust Network Access Set Up Wizard
SecureEdge is introducing the Zero Trust Network Access (ZTNA) set up wizard, a step-by-step process to set up all your components or infrastructures required in SecureEdge for ZTNA use cases. The main advantages of using this feature are as follows:
The Zero Trust Network Access set up wizard provides the entry point into the wizard via the Status dashboard and Quick Start page.
With the Set up Zero Trust Network Access card, you can see an overview of your existing complete/incomplete configuration. You can open the wizard from your previous point of configuration.
After completing an individual wizard step, you will see that each step receives a green check mark, indicating that the step has been successfully completed. If a wizard step displays a green check mark, you can proceed with next step.
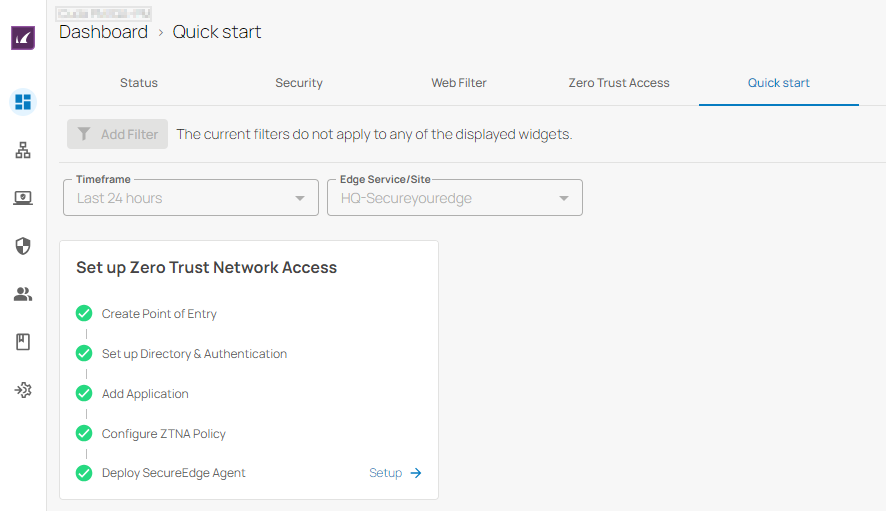
For more information, see Zero Trust Network Access Set Up Wizard.
Connector
An enhanced SecureEdge Connector is now available. The Barracuda SecureEdge Manager allows administrators to configure the SecureEdge Connector, a software solution that can be installed on Windows or Linux servers to keep your devices secure by redirecting their traffic through a secure VPN connection. The following improvements have been added:
You can now deploy the Connector in Routed mode. This requires Routed mode to be activated.
You can use the Connector for app-to-app communication between Connectors or between a Connector and the SecureEdge environment.
For more information, see How to Configure the SecureEdge Connector and How to Configure the Connector on a Linux Client.
Solved Bugs and Improvements in Release 9.0.3
Barracuda OS
Reconfiguring DHCP no longer causes memory failures in certain situations. [BNNGF-92531]
Firewall
SecureEdge SIP now works as expected after update to firmware 9.0.1. [BNNGF-94172]
Custom network apps that match any protocol now work as expected. Such apps now have the same precedence as network apps with a fixed protocol. [BNNGF-94900]
VPN
If the administrator has deposited a client-to-site certificate, it will be used instead of the SecureEdge VPN certificate. [BNNGF-94372]
Barracuda OS
SecureEdge devices now retrieve the configuration as expected after the update to 9.0.2. [BNNGF-94655]
Known Issues 9.0.3
General Known Issues
ACL Rule – Setting up the source or destination criteria to all sites and all private Edge Services results in the same networks configured on the box. [SWCS-3988]
Dashboards – For SecureEdge appliances running firmware < 9.0.3, adding more than one filter may either not apply the extra filter(s) or return no results.
Identity Management – The Barracuda SecureEdge identity app for Google Workspace is currently awaiting official approval from Google.
REST – Policy profile rulesets are currently not supported by the REST API. [BNNGF-94123]
SIP – The use of a SIP proxy with SecureEdge still might require manual adjustments in configuration files depending on the SIP setup. [BNNGF-95603]
VPN – Ingress NAT rules on port 443 (UDP, TCP) will not be applied anymore for SecureEdge Sites and Edge Services due to a regression introduced in version 9.0.3. A fix will be available in 10.0. and 9.0.5. An EA version based on 9.0.4 is available. [BNNGF-95712]
Known Issues Related to Azure Log Analytics (OMS)
On boxes with Azure Log Analytics (OMS) activated, the phibs service does not restart automatically after update. To get the service running, a reboot is required.
