Sophos can be integrated with the Barracuda SecureEdge SASE platform. Integration is done via the IPsec VPN and successfully tested using Sophos XG-SFOS 21.0 (VM) and SecureEdge 9.0.3 ( Barracuda Edge Service).
Step 1. Configure the SecureEdge Side
On Barracuda SecureEdge, do the following:
Go to https://se.barracudanetworks.com and log in with your existing Barracuda Cloud Control account.
In the left menu, click the Tenants/Workspaces icon and select the workspace you want to configure the IPsec IKEv2 tunnel for.
Go to Integration > IPsec VPN.
The IPsec VPN page opens. To add a tunnel, click Add IPsec Tunnel.
The Create IPsec Tunnel window opens.
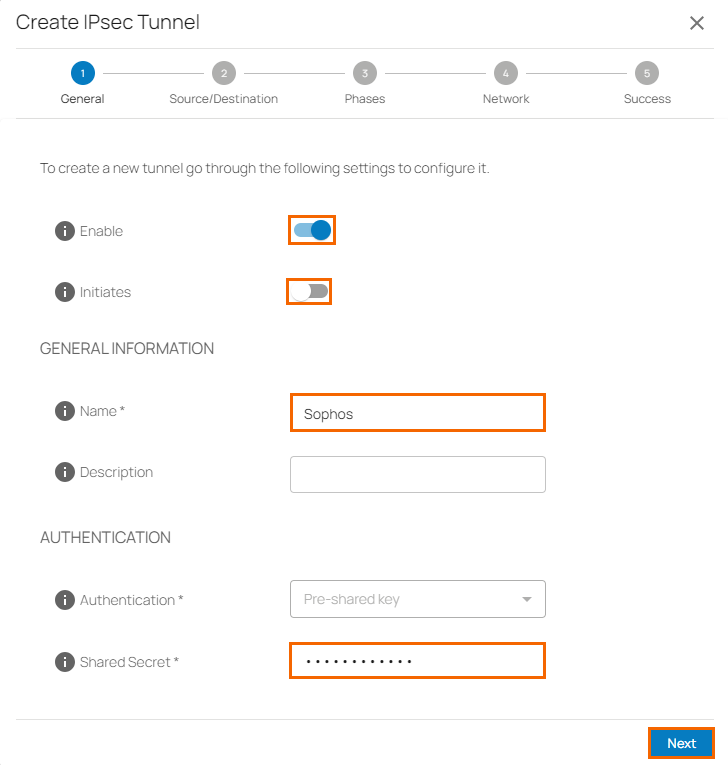
In the General tab, specify values for the following:
Enable – Click to enable.
Initiates – Click to disable.
In the GENERAL INFORMATION section, specify values for the following:
Name – Enter a unique tunnel name.
In the AUTHENTICATION section, specify values for the following:
Shared Secret – Enter the shared secret to use a shared passphrase to authenticate. Note: You must keep the pre-shared secret under 20 characters and must not include the hash symbol (#).
Click Next.
The Source/Destination tab opens.
In the SOURCE section, specify values for the following:
Type – Select Edge Service.
Peer – Select the peer the tunnel will be configured on from the drop-down list. For example, in this case, CudaEdge is selected, a Barracuda-hosted Edge Service.
Peer Gateways – Automatically added as
20.254.226.88. Note: You required this value in Step 2.Network Addresses – Enter the local network and click +. For example, in this case, enter
10.13.0.4/32. Note: You must allow DNS Forwarding from the Barracuda Edge Service to work. You can substitute this with the local IP of your Private Edge Service or Edge Service for Virtual WAN (Azure).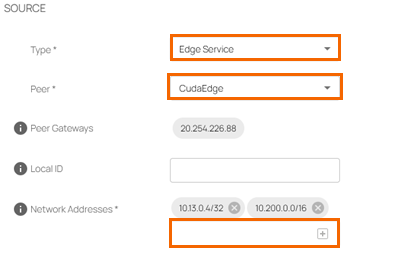
Note: On the source side, enter your SecureEdge Access Agent Device IP range subnet via Access > Settings. If you have not set this manually, you will be required to do so to be able to accurately specify this during the IPsec tunnel creation.
In the DESTINATION section, specify values for the following:
Remote Gateway – Enter the public IP address of your Sophos side, e.g.,
80.80.80.80Remote ID – Enter the public IP address of your Sophos side, e.g.,
80.80.80.80Network Addresses – Enter any subnet addresses local to your Sophos that you wish to be accessible through SecureEdge (e.g., server subnets) and click +. E.g.,
192.168.202.0/24.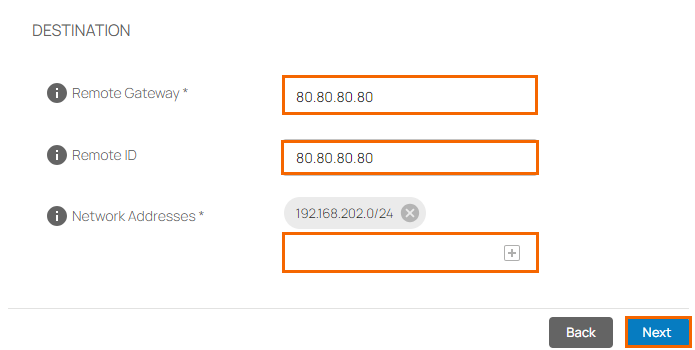
Click Next.
In the Phases tab, configure the following settings:
You can select your desired Phase 1 and Phase 2 settings. However, note that these parameters must match your chosen profile on Sophos. In this case, for example, the selected values are AES256 and SHA256 with Group 14 DH Group because these values match the Branch Office profile on Sophos. Enter the following values:
Ensure that Proposal Handling is set to Strict on both Phase 1 and Phase 2. Note that because the Sophos profile also includes weaker proposals, you must ensure that, for Proposal Handling, you select Strict on SecureEdge.
Set the Phase 1 Lifetime value to
10800.Set the Phase 2 Lifetime value to
3600.Example PHASE 1
Encryption – Select AES256.
Hash – Select SHA256.
DH-Group – Select Group 14.
Proposal Handling – Select Strict.
Lifetime – Enter
10800
Example PHASE 2
Encryption – Select AES256.
Hash – SHA256.
DH-Group – Select Group 14.
Proposal Handling – Select Strict.
Life time – Enter
3600
If there are any compatibility issues, see the tested and working settings in the screenshot below: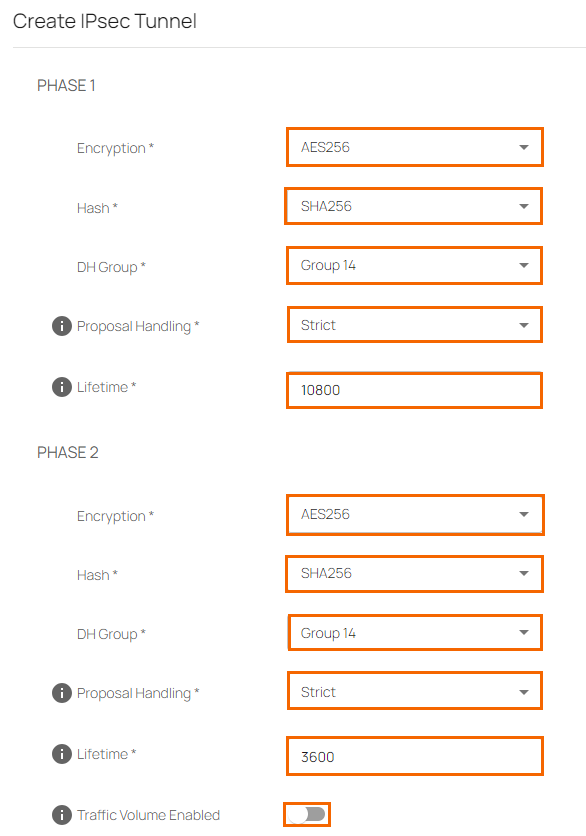
Click Next.
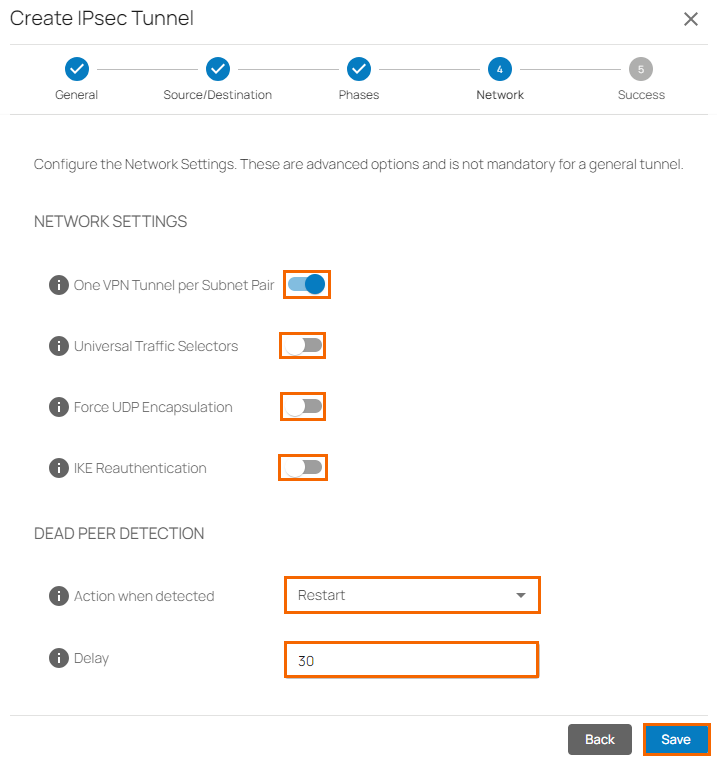
The Network blade opens.
In the NETWORK SETTINGS section, specify values for the following:
One VPN Tunnel Per Subnet Pair – Click to enable.
Make sure that you have disabled the following parameters:
Universal Traffic Selectors – Click to disable.
Force UDP Encapsulation – Click to disable.
IKE Reauthentication – Click to disable.
In the DEAD PEER DETECTION section, specify values for following:
Action When Detected – Select Restart.
Delay – Enter
30.
Click Save.
Verify that your IPsec tunnel configuration has been created successfully and click Finish.
Step 2. Configure the Sophos Side
Log into the Sophos firewall you wish to initiate the IPsec tunnel from to your SecureEdge Edge Service (gateway).
Go to Configure > Site-to-site VPN.
In the IPsec connections section, click Add.

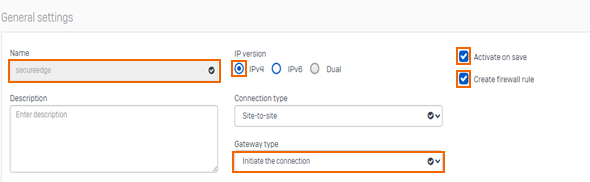
In the General settings section, specify values for the following:
Name – Enter the name. You must give the tunnel a suitable name to help you identify the tunnel later.
Activate on save – Click to select the box.
Create firewall rule – Click to select the box.
Gateway type – Set Gateway type to Initiate the connection.
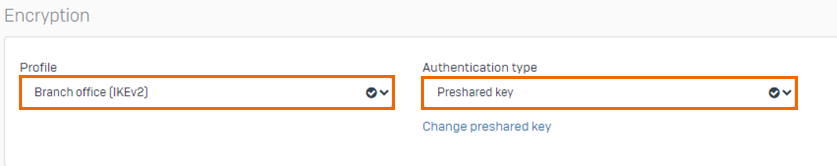
In the Encryption section, specify values for the following:
Profile – Set to Branch office (IKEv2).
Authentication type – Set to Preshared key.
In the Gateway settings, specify values for the following:
In the Local gateway section, enter values for the following:
Listening interface – Ensure that the listening port is set to your WAN interface. E.g.,
Port2- 192.168.0.3Local ID type – Set to IP address.
Local ID – Enter your Sophos public IP address. E.g.,
80.80.80.80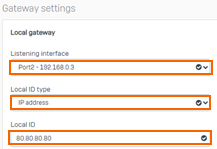
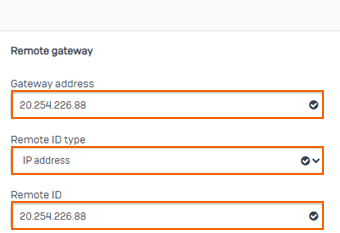
In the Remote gateway section, specify values for the following:
Gateway address – Enter your SecureEdge Edge Service public IP address as the gateway address. E.g.,
20.254.226.88Note: Ensure that the Gateway address matches the Peer Gateways value you set on the SecureEdge side (Step 1).Remote ID type – Set to IP address.
Remote ID – Enter the same public address as your gateway address
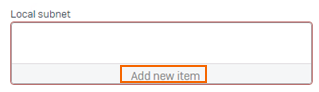
In the Local subnet, click Add new item.
To configure the Local subnet on Sophos, you can do the following:
If you already have an object for your local network(s) on Sophos, you can select the local network from the list.
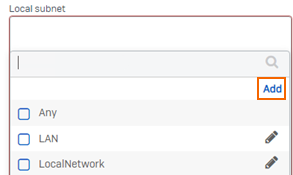
To add a new subnet(s) you want to be accessible from SecureEdge, click Add. Specify values for the following:
Name – Enter name of an object. E.g.,
SophosServersIP Version – Select IPv4.
Type – Select Network.
IP address – Enter IP address. E.g.,
192.168.202.0/24.Subnet – Select
/24 (255.255.255.0).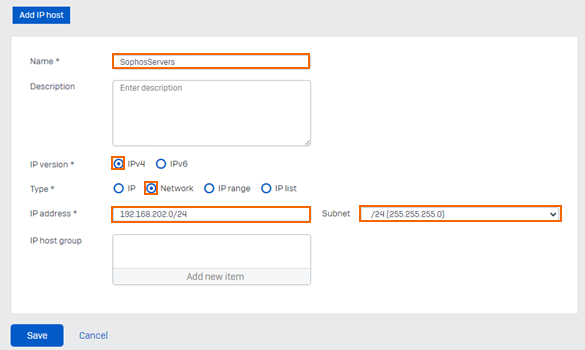
To configure the Remote subnet on Sophos, follow the same procedure as described in the local subnet. In the Remote subnet section, you must create an object called SecureEdge-Edge. Specify values for the following:
Name – Enter name of an object. E.g.,
SecureEdge-Edge.IP Version – Select IPv4.
Type – Select IP.
IP address – Enter IP address as either
10.13.0.4.or the IP address of your Edge service. However, this is always the IP address of Barracuda-hosted Edge services.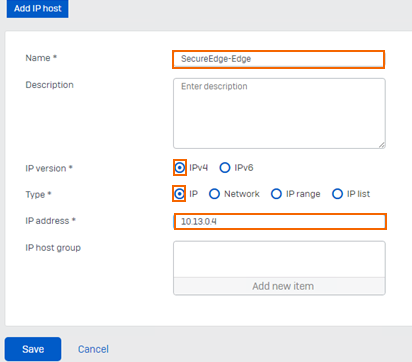
Repeat the process for your SecureEdge-Agent subnet. Specify values for the following:
Name – Enter the name of an object. E.g.,
SecureEdge-Agent.IP Version – Select IPv4.
Type – Select Network.
IP address – Enter the subnet of your Access Agent Network configuration, e.g.,
10.200.0.0.Subnet – Select
/24 (255.255.255.0). Note: Ensure that this value matches the subnet from the network addresses you set in Step 1.8.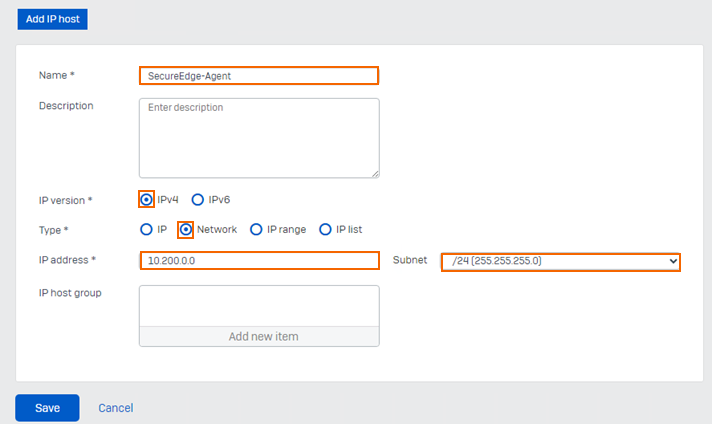
You must ensure that both SecureEdge-Agent and SecureEdge-Edge are selected. Click Apply 2 selected items.
Click Save to complete the setup.

Sophos XG now establishes a connection to the SecureEdge gateway and provides feedback that all your subnets are connected. If any of your subnets fail to connect, you must double-check your settings on both sides.
After the configuration is complete, the tunnel is established and, if there are suitable resources and Zero Trust Access policies, users can access resources from the Sophos LAN via SecureEdge.
