What's New in Version 9.0.4
SecureEdge version 9.0.4 is a minor release. It contains new features and several important fixes.
Proxy Connect
With the new firmware release 9.0.4, administrators can now enable Proxy Connect settings and configure Proxy Connect sockets. When you enable the Proxy Connect settings, your SecureEdge appliance uses either the default listening sockets or user-configured listening sockets. By default, Proxy Connect settings are disabled. Some of the key features of Proxy Connect are:
It is configurable on your Sites and Private Edge services.
You can define optional Proxy Connect socket settings only when the Proxy Connect setting is enabled.
If Proxy Connect socket inputs are not provided, the LANs of the Site/Private Edge service will be used with the ports 3128 and 8080, instead. However, if you configure a Proxy Connect socket, the default sockets will not be used.
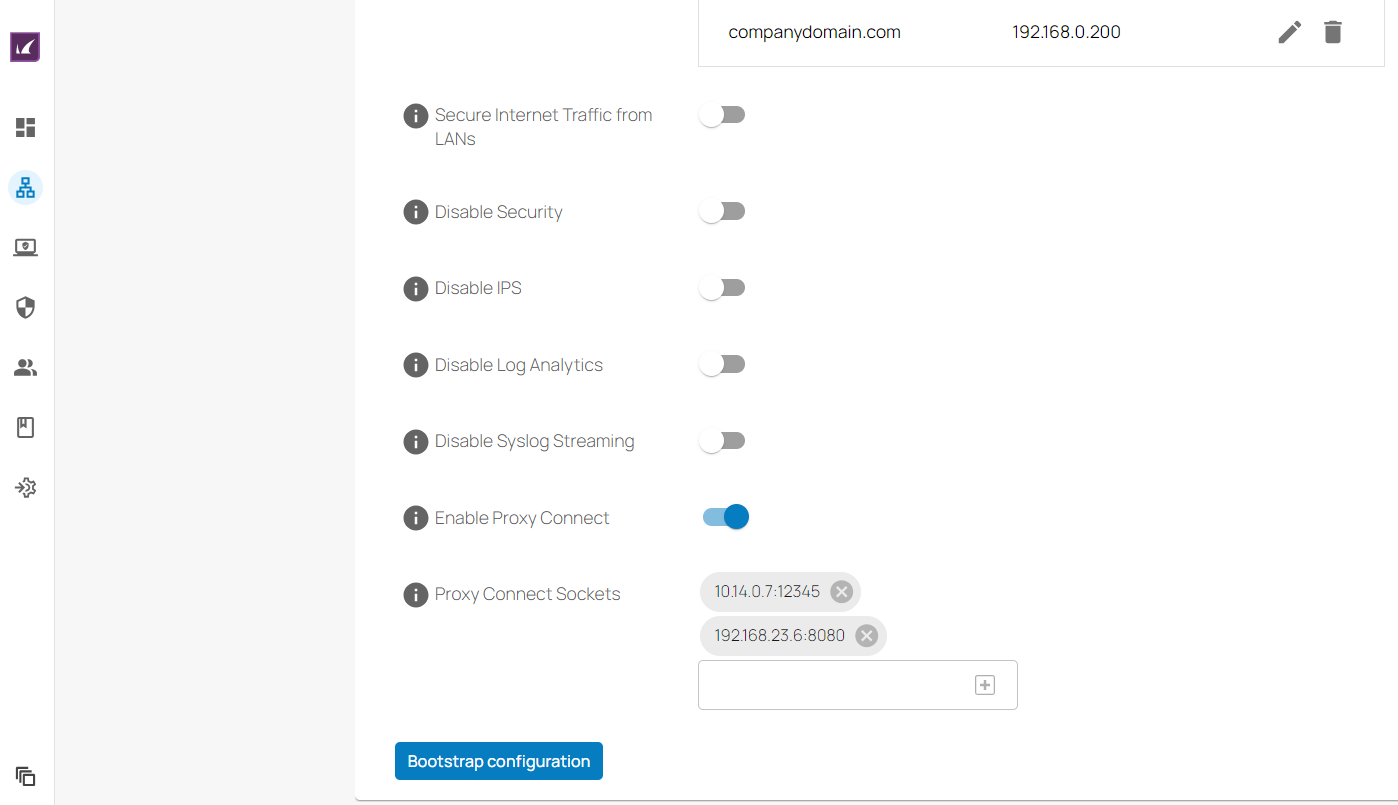
For more information, see How to Configure Proxy Connect.
Identity Management 1.2
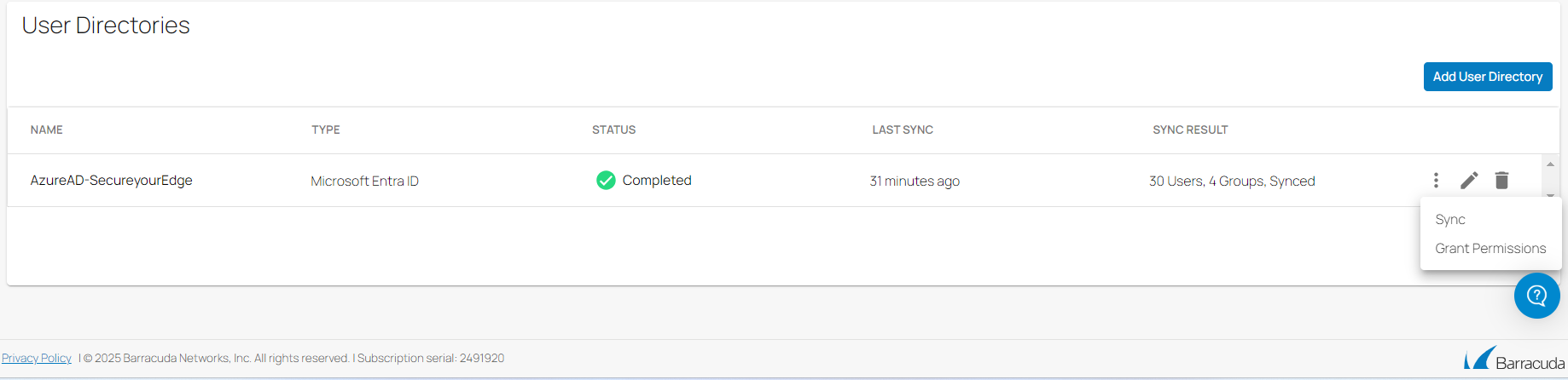
SecureEdge Identity Management 1.2 is now available. You can now configure the System for Cross-Domain Identity Management (SCIM) user directory for your selected workspace. The following improvements have been added:
With SecureEdge Identity Management, you can now configure an inbound SCIM user directory for Microsoft Entra ID.
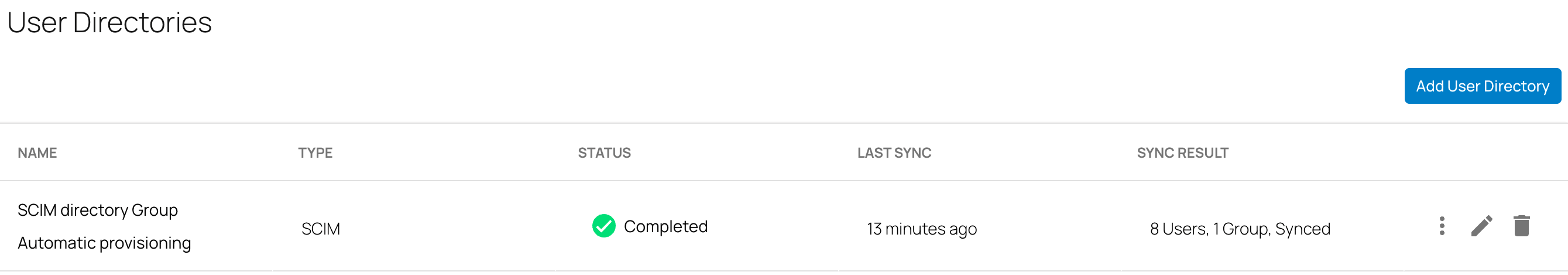
For more information, see How to Configure the Inbound SCIM User Directory for Microsoft Entra ID.
You can now add an inbound SCIM user directory for Okta.
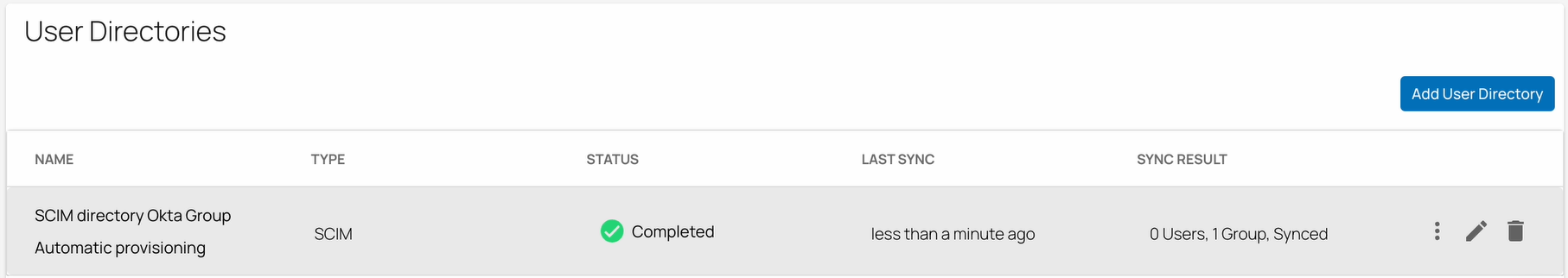
For more information see, How to Configure the SCIM User Directory for Okta.
To differentiate between enabled and disabled users for your workspace, an Enabled column has been added on the Identity > Users page. For example, when you enable (or disable) a user in Microsoft Entra ID and sync this directory to your SecureEdge environment, you can see that the user is enabled (or disabled) on the Users page.
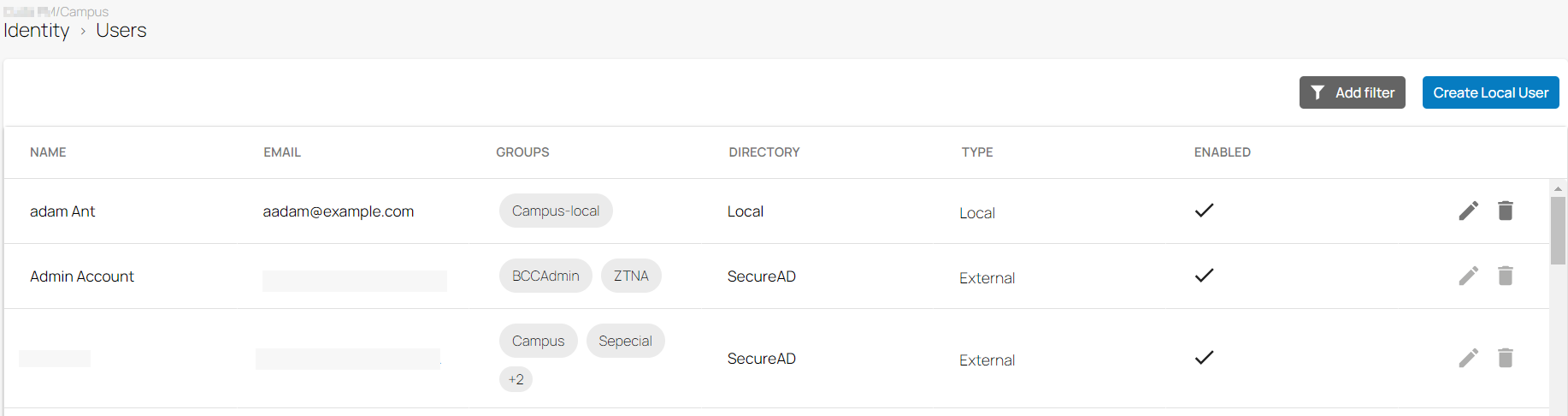
For more information, see How to Verify Identity Management Users or Groups.
A Grant Permissions option is now available for both the Microsoft Entra ID user directory and identity provider. The benefits of using Grant Permissions include:
It allows you to update requested permissions for user profiles to sync additional attributes.
It allows you to reconsent to update permissions if you need the enabled/disabled feature to work for Microsoft Entra ID.
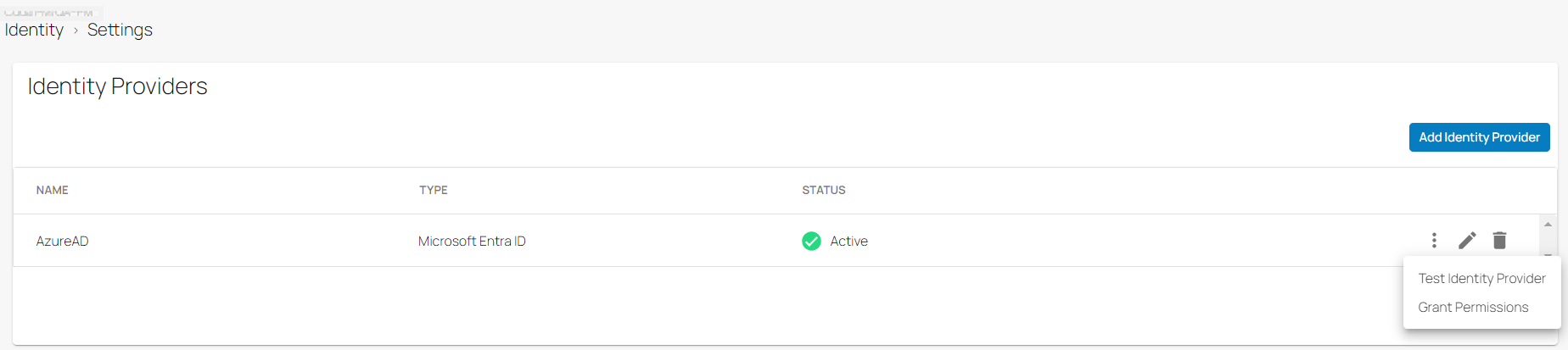
For more information on Grant Permissions, see:
ATR Configuration
Administrators can now enable Automated Threat Response (ATR) in SecureEdge and integrate it with the Barracuda XDR service. Each block action within Barracuda XDR creates a new ACL rule within SecureEdge. By enabling and configuring ATR in SecureEdge, malicious traffic can be blocked automatically for a given IP address or address range for users, URLs, and both public and private IPs in the network.
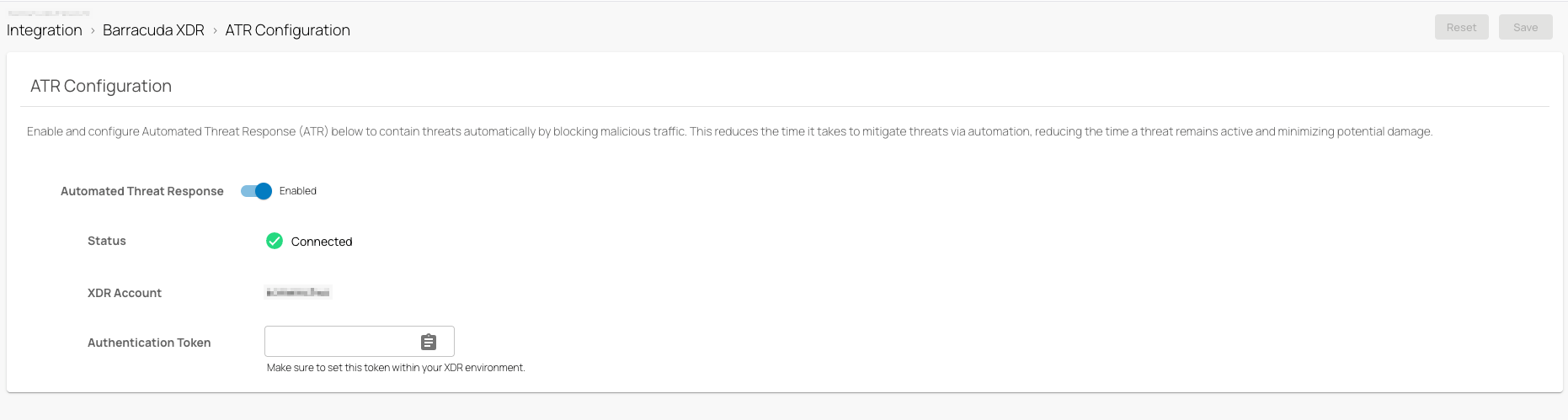
For more information, see How to Configure Barracuda XDR Automated Threat Response (ATR) in SecureEdge.
Unattended Enrollment on Windows Devices
Administrators can now enroll your device using client certificates. For Unattended Enrollment to work, you must configure a globally unique domain and upload CA certificates via the SecureEdge Manager. The admin will pre-configure this domain and add a client certificate generated from the uploaded CA on the device. This is performed using a Mobile Device Management (MDM) solution such as Microsoft Intune on Windows devices. The benefits of using Unattended Enrollment include:
Agents can be enrolled without any user interaction, which means no enrollment link needed and no user authentication required.
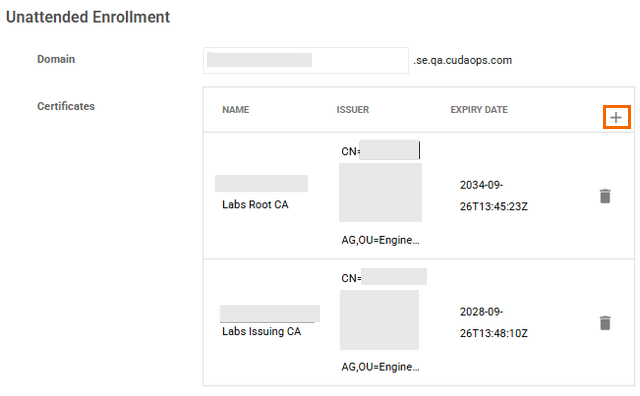
For more information, see How to Configure Unattended Enrollment on a Windows Device Using Microsoft Intune.
In addition, as of Barracuda SecureEdge Access Agent 2.0.0, the following new features have been added to the Zero Trust Access settings:
Trusted Platform Module (TPM) enforcement.
Support for Breakout Domains.
For more information, see How to Configure SecureEdge Access Global Settings and How to Configure SecureEdge Access User Settings.
Multiple IP Support for DC Agent
Administrators can now set multiple IPs for a DC Agent. In addition, this feature allows you to override the IPs for a specific Site or Private Edge Service.
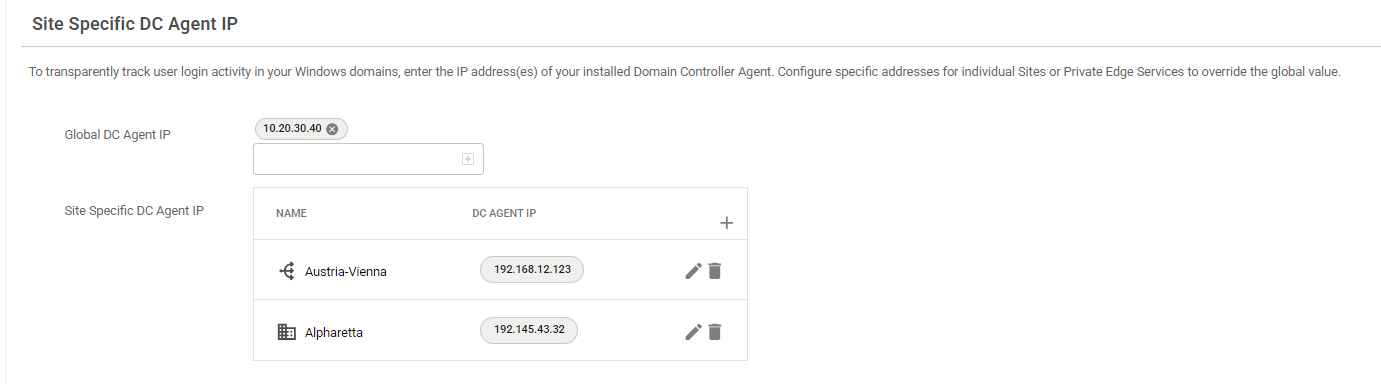
For more information, see How to Configure the DC Client in Barracuda SecureEdge.
Region Chooser
When creating a Barracuda Service subscription, you can now select as your region either Europe or North America. Note that the Region Chooser option is available only for new Barracuda Cloud Control (BCC) accounts. The selected region applies at the account level and will be the same for all workspaces that you create.
For more information, see SecureEdge Trial Guide.
SecureEdge Reporting
Barracuda SecureEdge now has enhanced reporting capabilities. SecureEdge Reporting allows you to collect data for reports for your connected Sites when Web Filtering is enabled. The Reporting data is streamed according to your selected region. Currently, you can select either Europe or North America, with Europe set as the default. SecureEdge Reporting lets you do the following:
Visualize reports on a monthly, weekly, daily, or hourly basis by using logs collected on Sites.
Create bar or line graphs. You can also switch between these two options.
Search for, sort, and filter any type of report.
Choose the columns you want to be visible using the “Edit Columns” option.
Create and save custom reports.
Rename and delete existing custom reports.
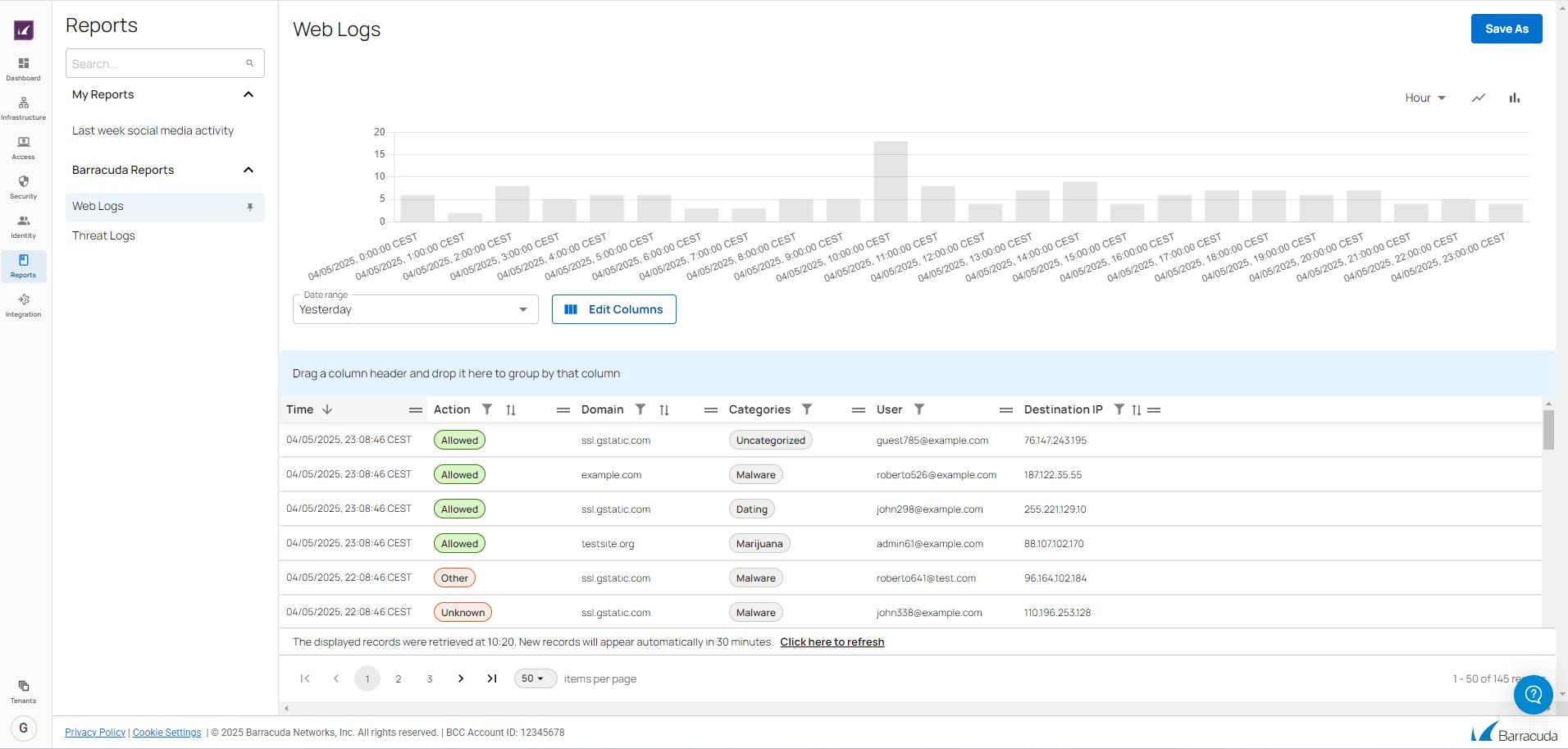
For more information, see SecureEdge Reporting.
Token-Based Unattended Enrollment
Administrators can now enroll devices using tokens. For Token-Based Unattended Enrollment to work, you must configure a globally unique domain, enable the Token-Based Enrollment, and generate a token via the SecureEdge Manager. Token-Based Enrollment is supported across all operating system platforms.
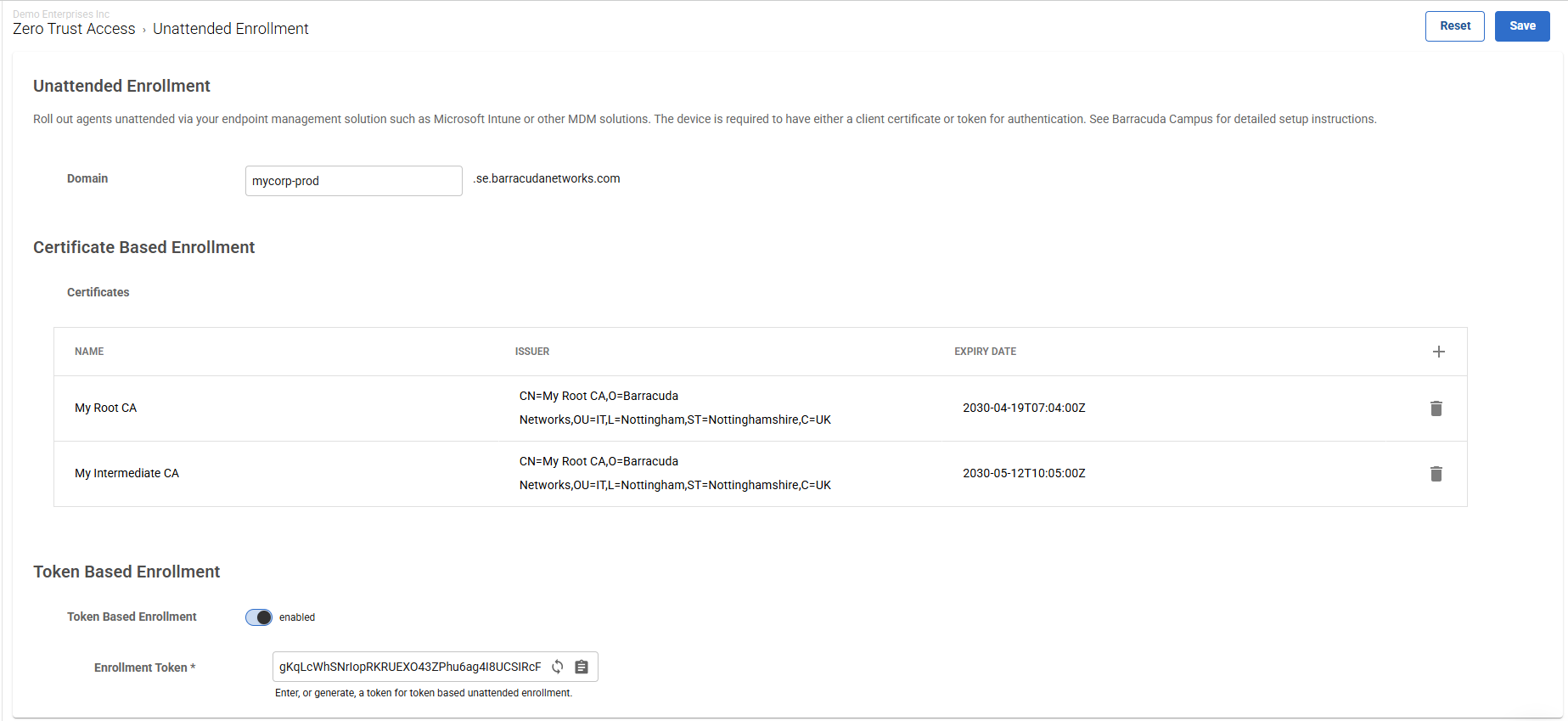
For more information, see How to Configure Token-Based Unattended Enrollment Using Microsoft Intune.
Enable Reporting on Edge Services
SecureEdge Reporting can now be enabled on all Edge Services: Edge Service for Virtual WAN, Edge Service (SaaS), and Private Edge Service.
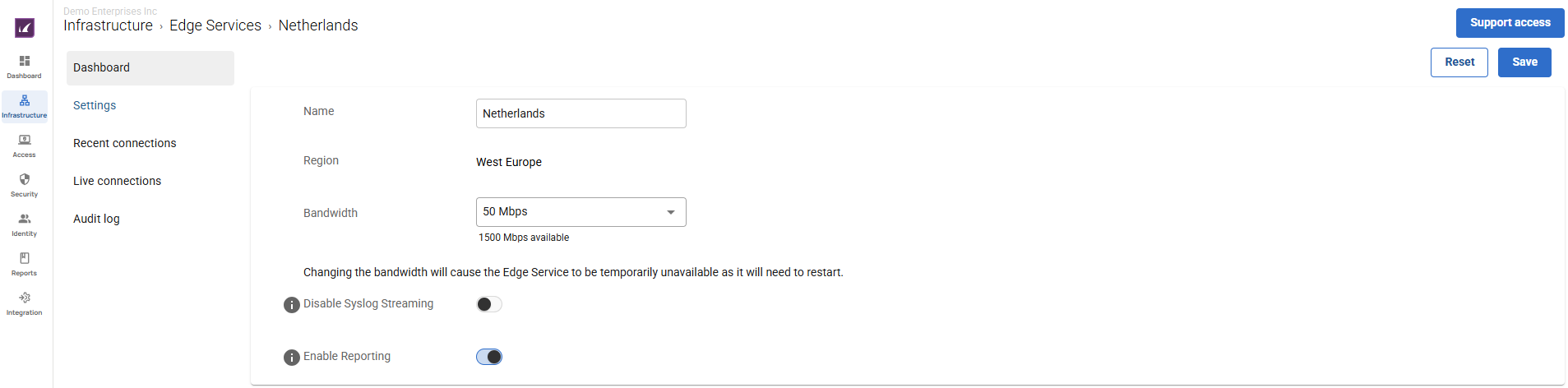
For more information, see How to Enable Reporting in SecureEdge.
Reboot the Private Edge Service
The SecureEdge Manager now lets you easily reboot a Private Edge Service. In addition, you have the option to either shut down or restart specific services instead of rebooting the whole appliance.
For more information, see How to Reboot a Private Edge Service.
Domain Lookup
The Custom Categories page displays the Domain Lookup option. You must enter a domain to look up the predefined category and custom category classification.
For more information, see How to Create Custom Categories.
Available Hotfixes
Hotfix 1144
Summary:
This hotfix is required to update to SecureEdge firmware version 10.0.0.
To download the package, go to https://dlportal.barracudanetworks.com/#/packages/6262/SecureEdge-1144-9.0.4-254387506.tgz
Hotfix 1140
Summary:
The time sync now works as expected when loopback addresses other than 127.0.0.1 are used as source for the NTP sessions.
To download the package, go to https://dlportal.barracudanetworks.com/#/packages/6147/NTP-1140-9.0.4-243077050.tgz
Hotfix 1137 - Security Update (Timezone for Updates)
Summary:
This hotfix fixes an issue with the timezone for update windows in SecureEdge.
To download the package, go to https://dlportal.barracudanetworks.com/#/packages/6136/secureedge-1137-9.0.4-239459594.tgz
Hotfix 1136 - Cumulative 9.0.4 for CloudGen Firewall and SecureEdge.
Summary:
This hotfix now fixes DNS object stalls in fail status.
To download the package, go to https://dlportal.barracudanetworks.com/#/packages/6131/cumulative-1136-9.0.4-236875007.tgz
Solved Bugs and Improvements in Release 9.0.4
Barracuda OS
Client DHCP monitoring now works as expected. [BNNGF-95596]
Weblog streaming now works as expected. [BNNGF-95562]
Overall memory usage is stable. [BNNGF-95162]
HA sync UDP sessions are now cleared as expected. [BNNGF-94803]
Network speed is no longer compromised when handling PPPoE traffic. [BNNGF-83386]
The WAN/LAN configuration can now be set to Read/Set as expected for fresh virtual boxes. [BNNGF-95160]
Firewall
Force refresh of DNS objects now works as expected. [BNNGF-95662]
The firewall no longer crashes in certain situations under heavy loads. [BNNGF-95575]
Errors related to ICMP frames violating RFC-792 are not logged. [BNNGF-95563]
Application Control no longer slows down web traffic. [BNNGF-95197]
VPN
Client-to-site configuration changes no longer cause established site-to-site tunnels to reload. [BNNGF-94491]
Hardware
The new hardware model T900 Rev. C is now available. [BNNGF-94905]
For more information, see T900 Revision C.
Known Issues 9.0.4
General Known Issues
Authentication – Failure of AzureAD info lookup at client login breaks ZTA traffic. [BNNGF-98480]
ACL Rule – Setting up the source or destination criteria to all Sites and Private Edge services results in the same networks configured on the box. [SWCS-3988]
Dashboards – For SecureEdge appliances running firmware < 9.0.3, adding more than one filter might either cause the other filter(s) not to be applied or return no results.
DNS – DNS Forwarder does not work for DNS server behind IPsec/IKEv2 tunnel. [BNNGF-94375]
DNS – Duplicate zone entries prevent the Edge service from connecting to the config service portal. [BNNGF-96785]
Identity Management – The Barracuda SecureEdge Identity app for Google Workspace is currently awaiting official approval from Google.
REST – Policy profile rulesets are currently not supported by the REST API. [BNNGF-94123]
SIP – The use of a SIP proxy with SecureEdge still might require manual adjustments in the configuration files depending on the SIP setup. [BNNGF-95603]
Proxy Connect – Proxy Connect Block pages are not visible to the end user. [BNNGF-96048]
VPN – Ingress NAT rules on port 443 (UDP, TCP) will not be applied anymore for SecureEdge Sites and Edge Services due to a regression introduced in version 9.0.3. A fix will be available in 10.0. and 9.0.5. An EA version based on 9.0.4 is available. [BNNGF-95712]
Currently, Edge Services (SaaS) do not log DNS Filtering results in the Web log.
Known Issues Related to Azure Log Analytics (OMS)
On boxes with Azure Log Analytics (OMS) activated, the phibs service does not restart automatically after update. To get the service running, a reboot is required.
