What ATR does
ATR determines whether an alert is malicious.
If the alert is identified as malicious, the IP Address is automatically added to the firewall or network security solution block list, depending on how malicious ATR determines it to be.
For more information about Automated Threat Response (ATR), see Setting up ATR.
Setting up ATR
To set up ATR for Sophos Firewall, do the following:
To enable the API configuration on the firewall
To add an Administrator profile
To add an Administrator User and add the the Administrator profile to it
To allow API access
To create an IP Host Group for Barracuda XDR Blocked IPs
To create a Firewall Rule to ensure the traffic from malicious IPs gets blocked on the Firewall
To enable ATR in XDR Dashboard
To enable the API configuration on the firewall
The Sophos API is disabled by default. You will need to enable it and allow access to specific IP addresses.
In Sophos Firewall, navigate to Backup and firmware > API.
Select the API configuration check box.
In Allowed IP address, add the following XDR ATR IPs, as well as any other local IPs/networks required to use the API configuration.
44.239.173.232
35.155.74.247
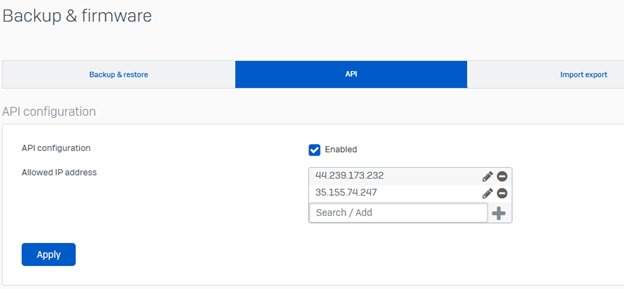
Click Apply.
To add an Administrator profile
You can create an admin profile and allow API access to administrators with specific read-write permissions.
In Sophos Firewall, navigate to Profiles > Device access and create an administrator profile with specific rights.
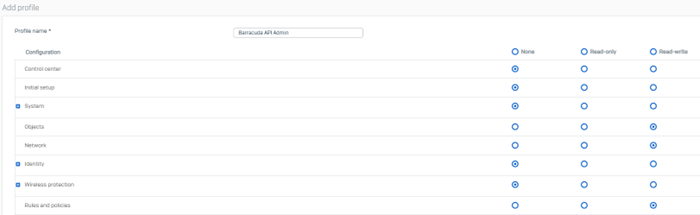
Click Save.
To add an Administrator User and add the the Administrator profile to it
When you add a user with the API administrator profile, you can limit the administrator's rights based on the profile.
In Sophos Firewall, navigate to Authentication > Users.
Click Add.
Enter a username to use for authentication.
You can't change the username later.Enter a name for the user record.
Enter a password.
Set User type to Administrator.
Select the API administrator profile you created.
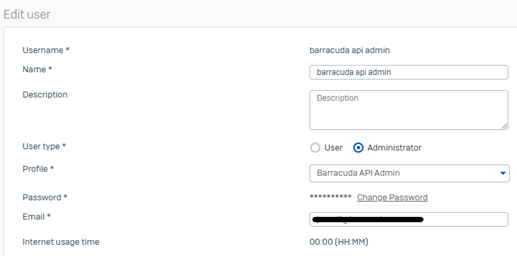
At the bottom of the page, click Administrator advanced settings and specify the following settings:
Schedule for device access Allows sign-ins to the web admin console during the schedule you select.
Login restriction for device access Allows sign-ins only from specified IP addresses. Add the following Barracuda XDR ATR IPs, along with any other local IPs/networks required to use the admin user:
44.239.173.232
35.155.74.247
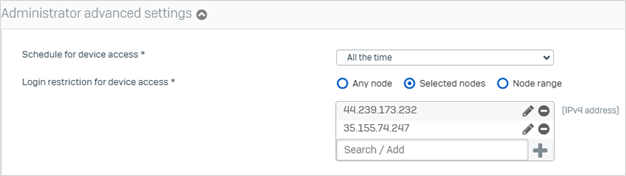
Click Save.
To allow API access
Turn on the API configuration and allow API access from the administrator's IP addresses. (Similar action might have already been completed in step 1.)
In Sophos Firewall, navigate to Backup and firmware > API.
Select API configuration.
For Allowed IP address, enter the following ATR IP addresses:
44.239.173.232
35.155.74.247
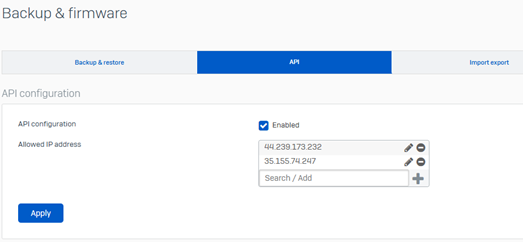
Click Apply.
To create an IP Host Group for Barracuda XDR Blocked IPs
Barracuda XDR uses this Group to keep track of the IPs that are automatically blocked on the firewall. Add this group to any preexisting security rules/policies created to block traffic to/from anomalous IP addresses. If no security policy exists on the Sophos firewall, see follow the To create a Firewall Rule to ensure the traffic from malicious IPs gets blocked on the Firewall below.
In Sophos Firewall, navigate to Hosts and services > IP host group and click Add.
Type a name for the host group.
NOTE Don’t include a space in the IP host group name or ATR won’t function properly. We highly recommend using Barracuda_XDR_Blocked_IPs.Select the IP version.
NOTE You can't create a host group that contains both IPv4 and IPv6 hosts.)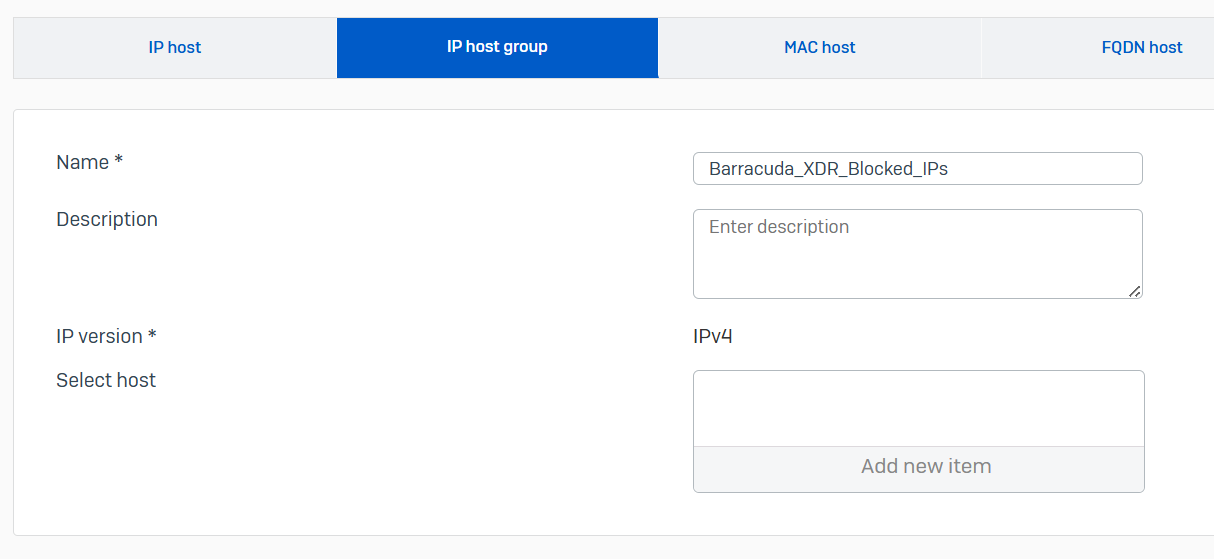
Click Save.
To create a Firewall Rule to ensure the traffic from malicious IPs gets blocked on the Firewall
For Barracuda XDR to successfully block IPs on your firewall, you need to add the IP Host Group to a firewall rule that blocks this type of traffic. If you do not have a preexisting rule(s) in place, create one and add the IP host group to the firewall rule.
Go to Rules and policies > Add firewall rule > New firewall rule.
Create a firewall rule that blocks traffic from the IPs that are in the IP Host Group you created for XDR.
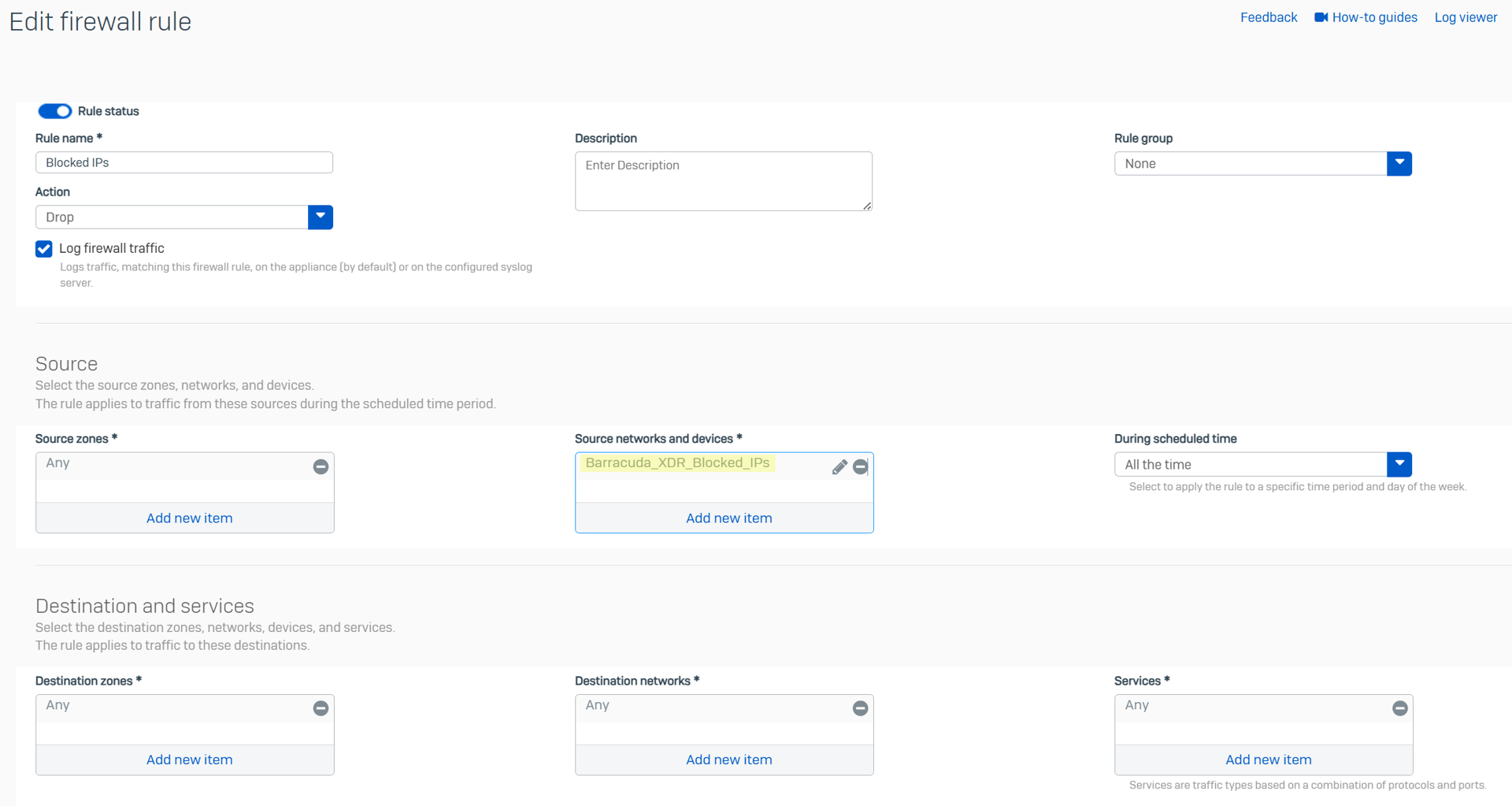
Click Save.
To enable ATR in XDR Dashboard
Navigate to the ATR Settings > Firewalls.
In the Firewall table, click the Sophos XG/XGS row.
Click Edit Config.
Upload the following data:
External IP
Port (Admin console HTTPS port. Typically, the default port is “4444”.)
Admin Username
Admin Password
IP Host Group Name
Click Save.
