These release notes include the following:
New features and upgrades
New detections
SOAR Enhancements
Decommissioned Rules
Alert Enhancements
New features and upgrades
New Integration: Microsoft 365 Defender
To provide integrated protection against sophisticated attacks, you can now integrate Microsoft 365 Defender with Barracuda XDR. The powerful combination of Microsoft 365 Defender and Barracuda XDR will monitor alerts, incidents, and events to natively coordinate detection, prevention, investigation, and response across endpoints, identities, email, and applications.
This new integration covers Email, Cloud, and Endpoint data, depending on what Microsoft 365 Defender products are purchased and configured.
To integrate Microsoft 365 Defender
In XDR Dashboard, click Administration > Integrations.
Click the Setup button on the Microsoft 365 Defender card.

New Detections
Detection Name | Description |
|---|---|
FortiGate Threat IP Communication Detected on Critical Protocol | Added rule to protect Fortinet FortiGate firewall customers when malicious IPs (per Barracuda Managed XDR threat intelligence) attempt to communicate through the firewall over commonly-used, critical protocols including SSH, FTP, SMB, RDP, SIP, Telnet, and VNC. |
SonicWall Threat IP Communication Detected on Critical Protocol | Same as above, for SonicWall firewall customers (SonicOS and SonicOSX 7.0). |
Meraki Threat IP Communication Detected on Critical Protocol | Same as above, for Cisco Meraki firewall customers. |
Microsoft 365 Login from Malicious IP Address | Added rules that alert on Microsoft 365 logins matching known malicious IP addresses per Barracuda Managed XDR threat intelligence. |
Microsoft 365 Suspicious SharePoint File Deletion Activity | Added rules that detect user attempts to delete a significant volume of Microsoft SharePoint files within a narrow time period. |
TOR Activity to the Internet | Added rules for customers with Barracuda Managed XDR Endpoint Security (Managed) that leverage SentinelOne telemetry to detect outbound connections from the TOR browser. |
SOAR Enhancements
Category | Description |
|---|---|
Azure Conditional Access Policy Modified | Added a new automated rule that formerly required manual investigation and action determination from a SOC analyst. Automating the rule reduces alert fatigue and features advanced correlation of Barracuda Managed XDR threat intelligence, deduplication on a variety of fields, and domain enrichment (e.g., checking the domain in Shodan.) |
Azure Owner Added to Group | Added a trigger to filter out Microsoft Azure alerts that do not contain high privilege group names. |
ESET Medium Severity Detection | Added a trigger to drop alerts when ESET detects and blocks a medium severity event. For medium severity events are detected but permitted, Barracuda Managed XDR alerts on such events. |
Decommissioned Rules
Detection Name |
|---|
Microsoft 365 SharePoint Site Permissions Modified |
AWS Internet Gateways Described by External Source |
ATP Blocked Malicious Attachment Multiple Times |
Barracuda Incident Response – Potential Incident: Post Delivery Threat |
SentinelOne User Added White Hash |
Alert Enhancements
Change | Description |
|---|---|
Alert Formatting | Removed “How we Detect” section from tickets. |
Alert Formatting | Added “Data Source” to alert header (as in Figure 1 below). |
Email Notifications | Added an “Alert Summary” to automated alert emails sent to customers (in Figure 2 above the “Click to view” button). |
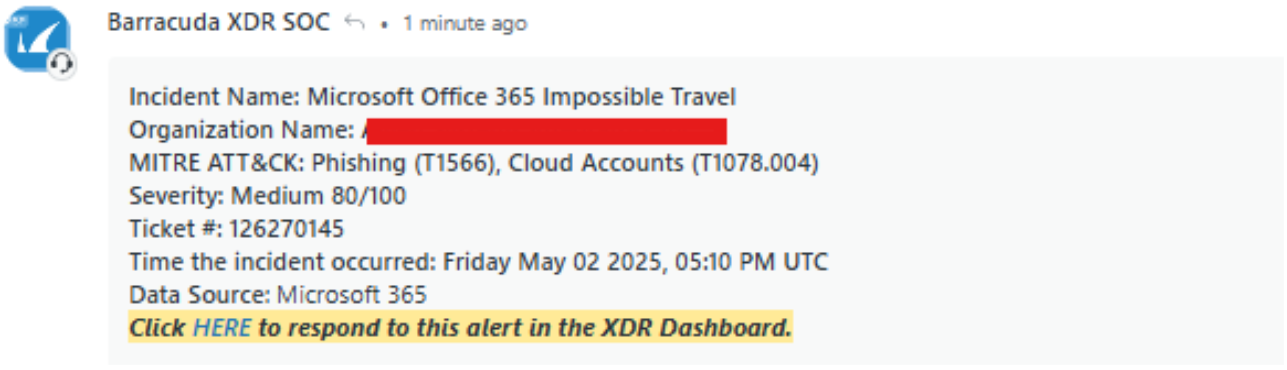
Figure 1: Alert Header

Figure 2: Sample Email Alert Summary
