Rule
Microsoft 365 Impossible Travel
Purpose
The impossible travel detection identifies two user activities (in a single or multiple sessions) originating from geographically distant locations within a period shorter than the time it would have taken the user to travel from the first location to the second, indicating that an unauthorized actor is accessing the same account. This is a key indicator that an account has been compromised.
Objective
Detect impossible travel between two geolocations within a short period of time.
Test Workflow
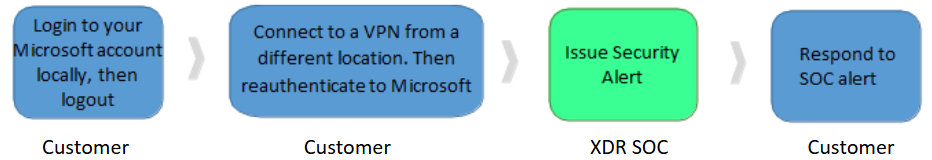
How to test
Choose a VPN Tool such as ExpressVPN, NordVPN, etc. Download and install the VPN client on your device.
In a VPN tool (such as ExpressVPN or NordVPN), connect to a VPN server from a foreign location.
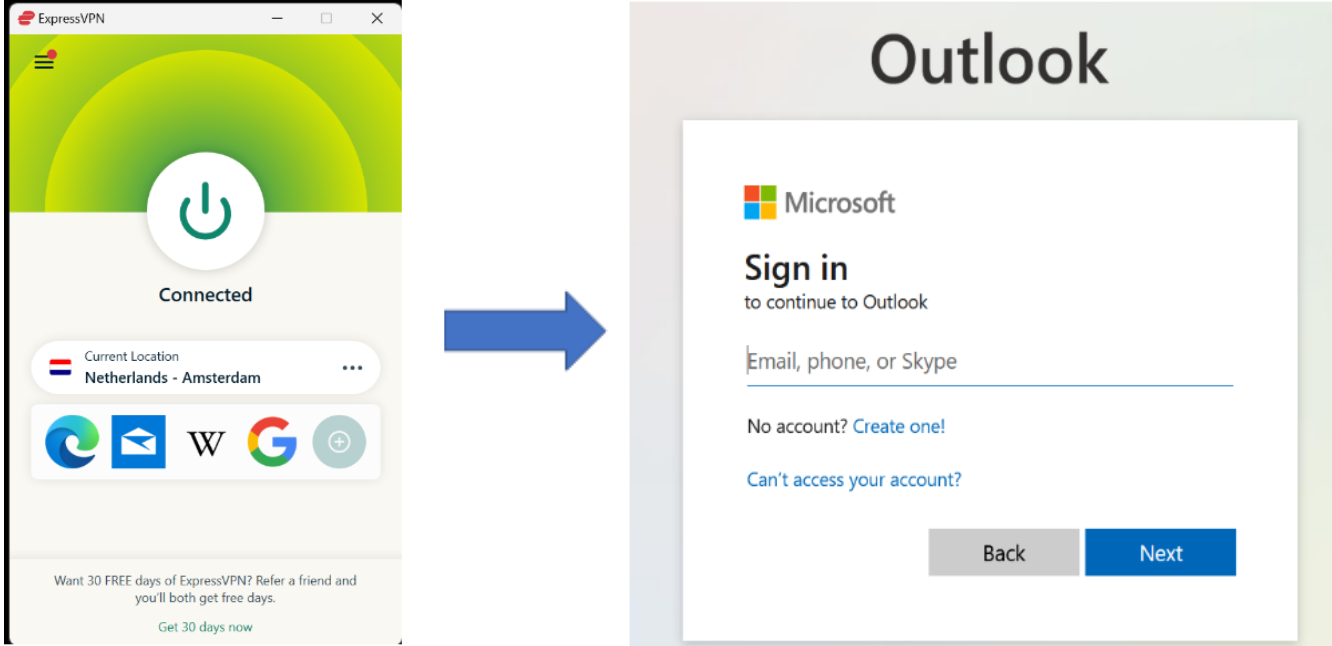
Once connected, login to your Microsoft 365 account. After successfully authenticating, log out of your Microsoft account.
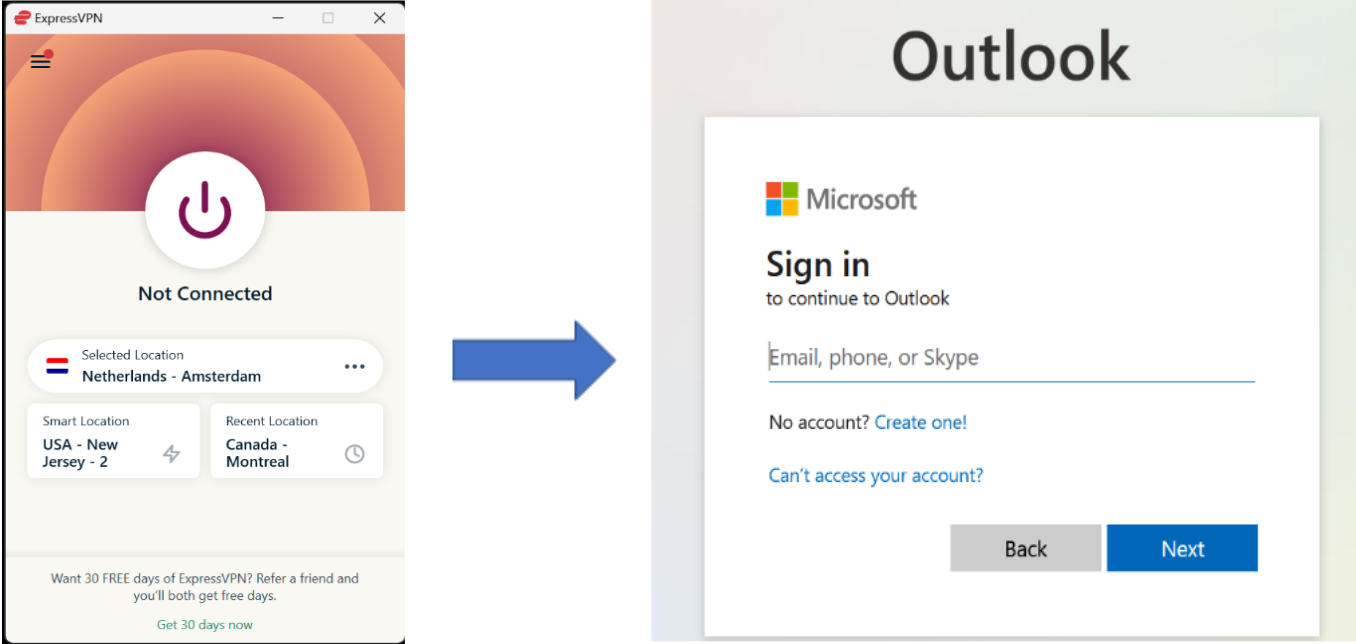
Disconnect the VPN, and immediately login to your Microsoft 365 account from your current location.
A Barracuda XDR alert triggers from the SOC, describing this impossible travel scenario. You can view the alert from the Barracuda XDR Security Dashboard.
We request that you reply to the security alert stating that the reported activity was associated with authorized security testing.
The SOC team closes the incident, marking the conclusion of this threat simulation test.
