Attackers are abusing Microsoft 365’s Direct Send feature - originally intended to allow applications and multifunction devices to send emails without authentication - to send phishing emails that appear to come from legitimate internal users. This method bypasses standard email authentication protocols such as SPF, DKIM, and DMARC.
To protect against these threats and risk of exploitation, Barracuda Networks recommends the following:
Disable, or restrict, Direct Send entirely. If it must be used for legitimate purposes, implement strict controls on which IP addresses can use this feature.
Deploy advanced email security solutions that can detect and block phishing attempts beyond standard authentication checks.
Enable multi-factor authentication (MFA) for all Microsoft 365 accounts to prevent credential theft from resulting in account compromise.
Implement DMARC with a policy of ‘reject’ for your domains to reduce the effectiveness of spoofing attempts.
Full Tenant Restriction
To protect against all forms of gateway bypass, you will need to implement tenant restrictions on your inbound partner connector. Simply disabling Direct Send will only stop emails that use your own domain.
If you have not already deployed the Barracuda partner connector, see Step 2 - Configure Microsoft 365 for Inbound and Outbound Mail | Deploy Partner Connector.
Before implementing full tenant restrictions, it is recommended to validate your inbound mail flow first to ensure minimal disruptions. See https://campus.barracuda.com/product/emailgatewaydefense/doc/167977788/validating-mail-flow-before-restricting-access/ for more details.
Using one of the following methods, enable tenant restrictions to ensure all inbound mail comes from either Barracuda Networks or another trusted partner/application.
PowerShell
Run the following command within Exchange Online PowerShell
Set-InboundConnector -Identity "Barracuda Inbound Connector" -RestrictDomainstoIPAddresses $true
Web Interface
Click on Barracuda Inbound Connector, the partner connector you previously created in this article Step 2 - Configure Microsoft 365 for Inbound and Outbound Mail | Deploy Partner Connector.
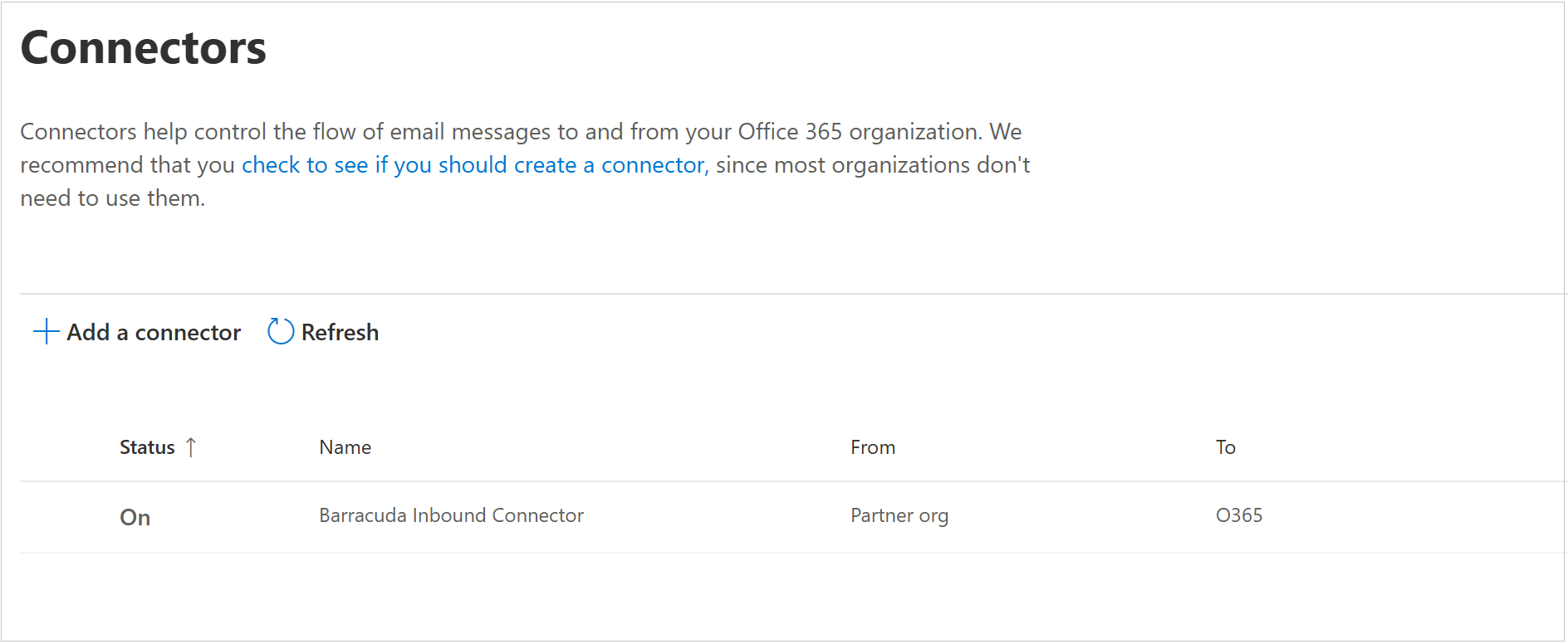
Click edit sent email identity.
Change the selection to By verifying that the sender domain matches one of the following domains. For the domain, enter an * (asterisk), and then click the + button.
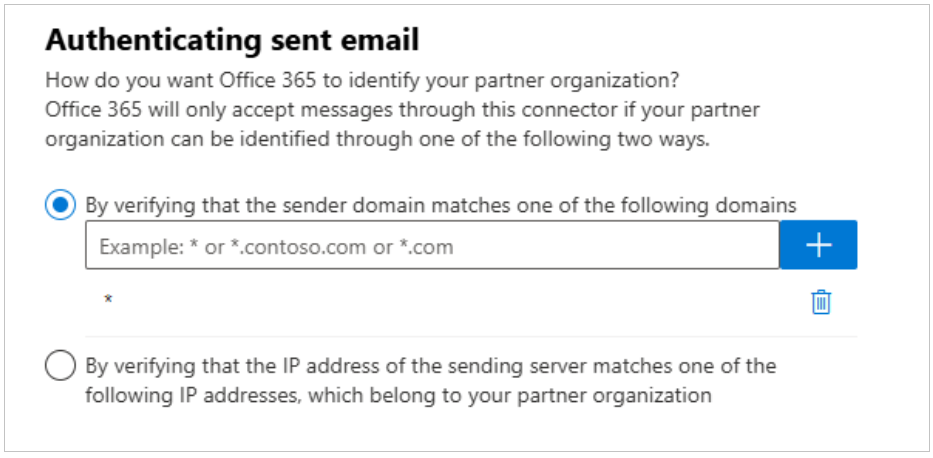
Click Save, and then click the back arrow.
Click Edit restrictions.
Check Reject email messages if they aren’t sent from this IP range.
Enter the IP range for your specific region, and then click the + button.
This is the region selected when setting up your Barracuda Networks instance. Refer to the Email Gateway Defense IP Ranges Used for Configuration for the IP ranges corresponding to your region.
For example, for the US region, enter 209.222.82.0/24.
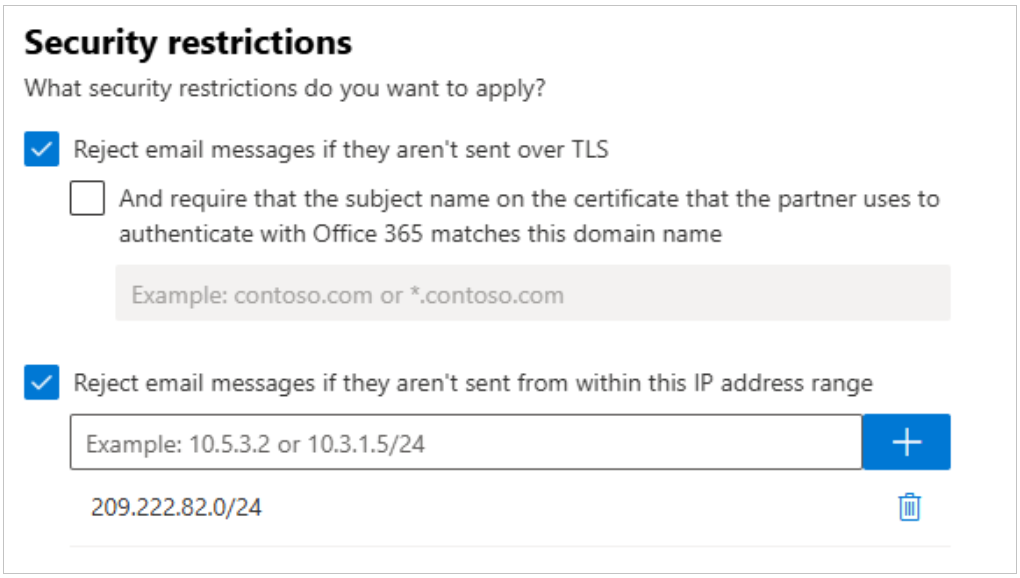
Click Save.
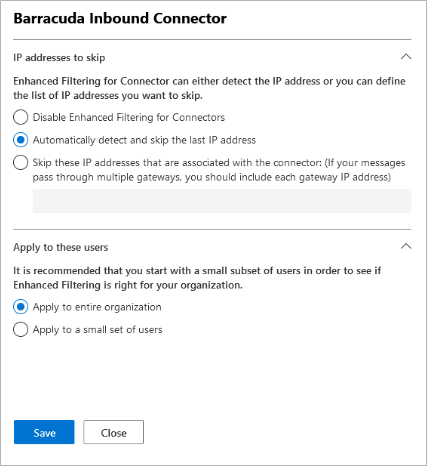
Ensure you have enabled Enhanced Filtering for Connectors:
Click on Barracuda Inbound Connector, the partner connector you previously created in this article Step 2 - Configure Microsoft 365 for Inbound and Outbound Mail | Deploy Partner Connector.
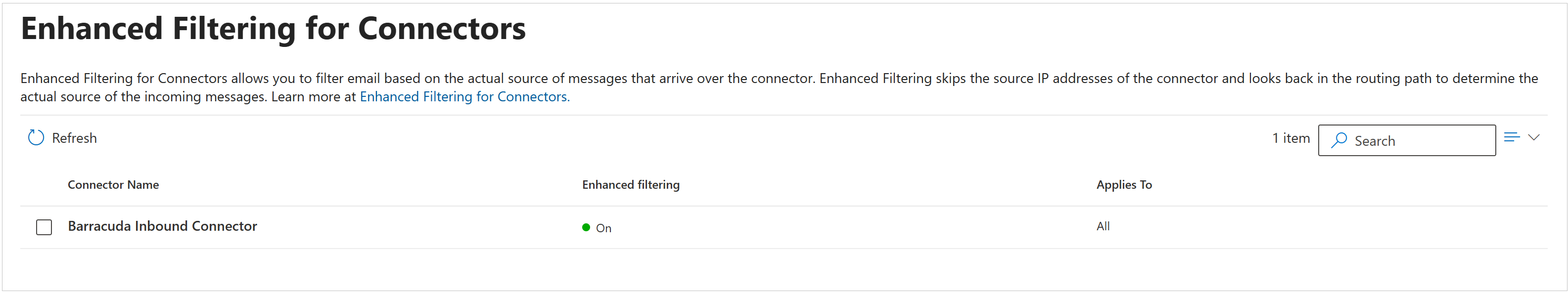
Select Automatically detect and skip the last IP address and Apply to entire organization.
Click Save.
By following these steps, you will successfully configure your Microsoft tenant to exclusively accept emails sent from Barracuda Networks. Any attempts to bypass this setup and send emails directly to Microsoft will result in the following error message:
550 5.7.51 TenantInboundAttribution; Rejecting. Recipient has a partner connector with RestrictDomainsToIPAddresses or RestrictDomainsToCertificate set.
Disable Direct Send
To disable Direct Send, which prevents the spoofing of your own domain, connect to Exchange Online and run the following command via Exchange Online PowerShell:
Install Exchange Online module.
If you have already installed Exchange Online module, proceed to the next step.
To install Exchange Online module, open Windows PowerShell as an administrator and enter the following command:
Install-Module -Name ExchangeOnlineManagement
Connect to Exchange Online Powershell and log in with your Microsoft 365 administrator account using the following command:
Connect-ExchangeOnline
Run the following PowerShell command:
Set-OrganizationConfig -RejectDirectSend $true
Once configured, Microsoft will no longer allow the direct sending of emails that use one of your accepted domains in the From address.
For more information, see the Microsoft article https://techcommunity.microsoft.com/blog/exchange/introducing-more-control-over-direct-send-in-exchange-online/4408790.
Enabling Direct Email Sending from Trusted External Sources
If you have external applications that require the ability to send inbound mail directly to your Microsoft tenant, bypassing your external MX record, it is essential to create additional inbound partner connectors.
These partner connectors can be configured to recognize the sender either by their connecting IP address or by the sending domain, depending on what best suits your application’s needs.
These additional connectors will override the restrictions set on the Barracuda Inbound connector, ensuring that mail is successfully delivered. Any email attempts that do not go through your designated inbound partner connectors will be rejected.
