XDR’s detection and response capabilities for high-risk incidents from Defender for Endpoint monitor your environment for a range of indicators. This approach includes critical threat categories such as Ransomware, along with high-severity Tactics, Techniques, and Procedures (TTPs) derived from our extensive threat intelligence platform.
Barracuda’s Managed XDR platform swiftly secures infected machines running Defender for Endpoint by isolating the endpoint from the network, ensuring all inbound and outbound network connectivity is severed. Our platform combines SOAR, threat intelligence, and Microsoft’s detection data to analyze activity and identify malicious behavior. Once a high-risk threat is detected, XDR initiates an automated response to isolate the computer via API, ensuring swift protection against advanced threats.
ATR for Microsoft Defender for Endpoint workflow
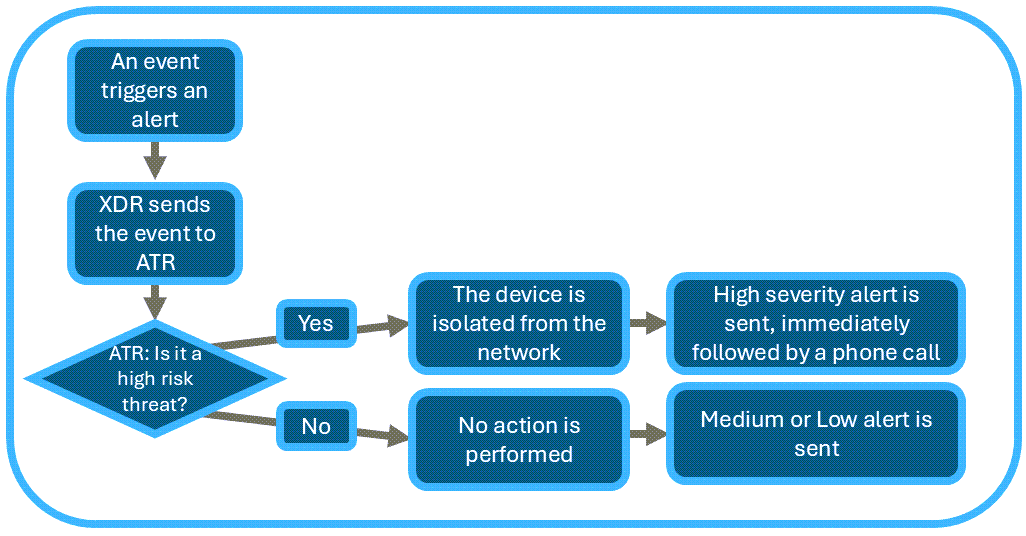
A Defender for Endpoint event occurs, triggering an alarm in Barracuda XDR.
The alarm is sent to the Barracuda XDR ATR.
ATR determines whether the incident is high severity.
If the event is identified as high severity, the endpoint is automatically isolated using the Defender
for Endpoint API. Then An alert is sent and followed by a phone call.If the alert is not identified as high severity, the endpoint is not isolated, and you will receive a Medium or Low severity alert.
To enable ATR for a Microsoft Defender for Endpoint, you need to:
If you haven’t already, integrate a single-tenant or multi-tenant Microsoft Defender for Endpoint application.
In Microsoft Entra, update the API permissions and grant admin consent
In Barracuda XDR, enable ATR.
Follow the procedures below.
To register a new application in Microsoft Entra ID for integration with Barracuda XDR
Do one of the following:
To set the API Permissions and grant admin consent
Sign into the Microsoft Entra Admin Center.
In the left menu, click Identity > Applications > Enterprise apps.
Click the link to your app.
Remove the User.Read API Permission by doing the following:
In the left menu, in the Manage section of your registered application, click API permissions.
Under Configured permissions, locate the default User.Read permission.
Next to User.Read, click the
 icon, then click Remove all permissions.
icon, then click Remove all permissions.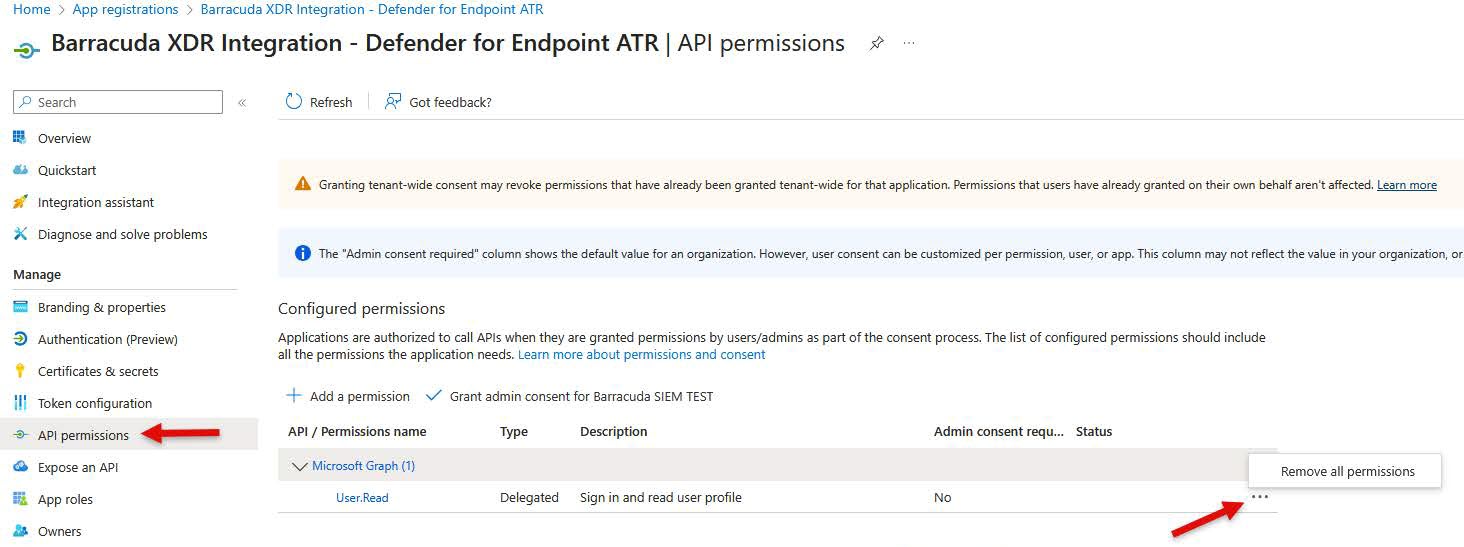
Click Yes, remove.
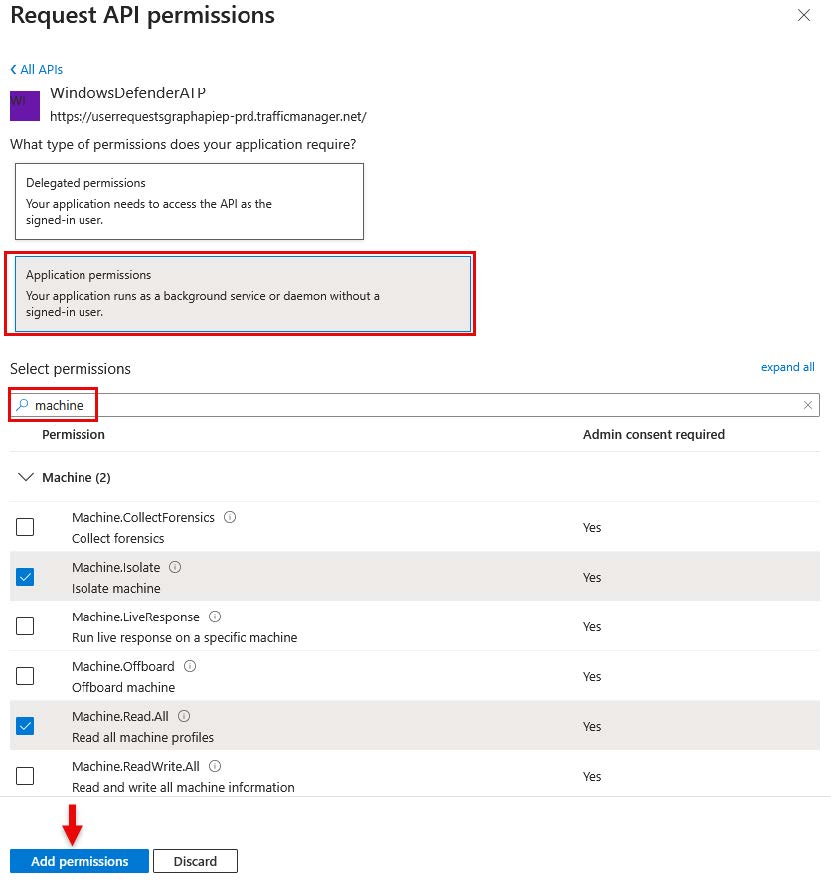
Add Microsoft Defender for Endpoint Permissions by doing the following:
In the Select an API section, click APIs my organization uses.
In the search bar, type WindowsDefenderATP and select WindowsDefenderATP from the
results.Click Application permissions.
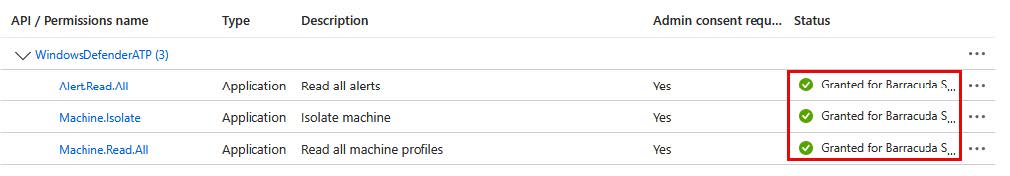
Find and select the following permissions:
NOTE You can use the search box to type keywords.Machine.Isolate
Machine.Read.All
Alert.Read.All
Click Add permissions.
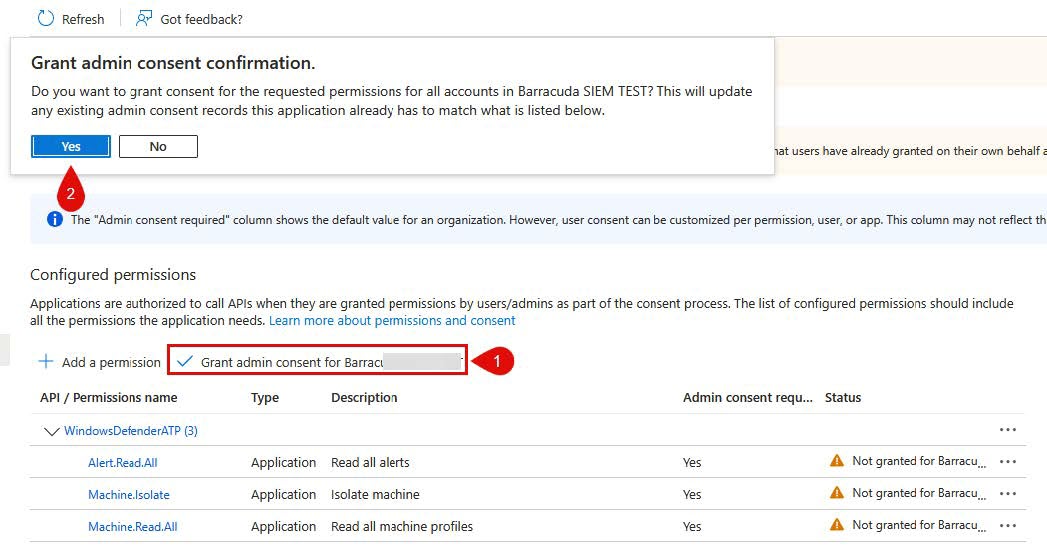
Grant Admin Consent by doing the following:
In the Configured permissions section, click Grant admin consent for <organization>.
In the confirmation dialog, click Yes.
To update the XDR Dashboard
In Barracuda XDR Dashboard, in the left navigation menu, click Administration > Integrations.
On the Microsoft Defender for Endpoint card, click Update.
NOTE You can search for the Microsoft Defender for Endpoint card, by typing Defender for in the search box and clicking Update.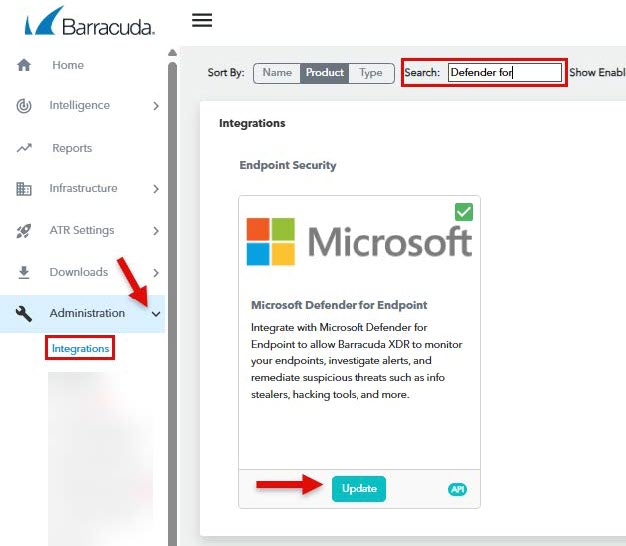
Select Enable Auto Remediation.
Click Save.
