New features
Google Workspace ATR is now available
Setting up ATR for Google Workspace gives you rapid containment of account-based attacks without manual intervention.
When ATR detects a Google Workspace account has been compromised, Barracuda XDR automatically responds by suspending the affected account through the API. This suspension restricts access to all Google services and triggers session invalidation, helping to contain threats in real time.
For more information, see Setting up ATR for Google Workspace.
Updated Self-Service Email Distributions Page
We’ve redesigned the Email Distributions page, found under the Administration tab. This page identifies what email addresses and distribution lists are notified for High, Medium, and Low XDR SOC alerts. Users can now update these addresses without needing to contact Barracuda Managed XDR.
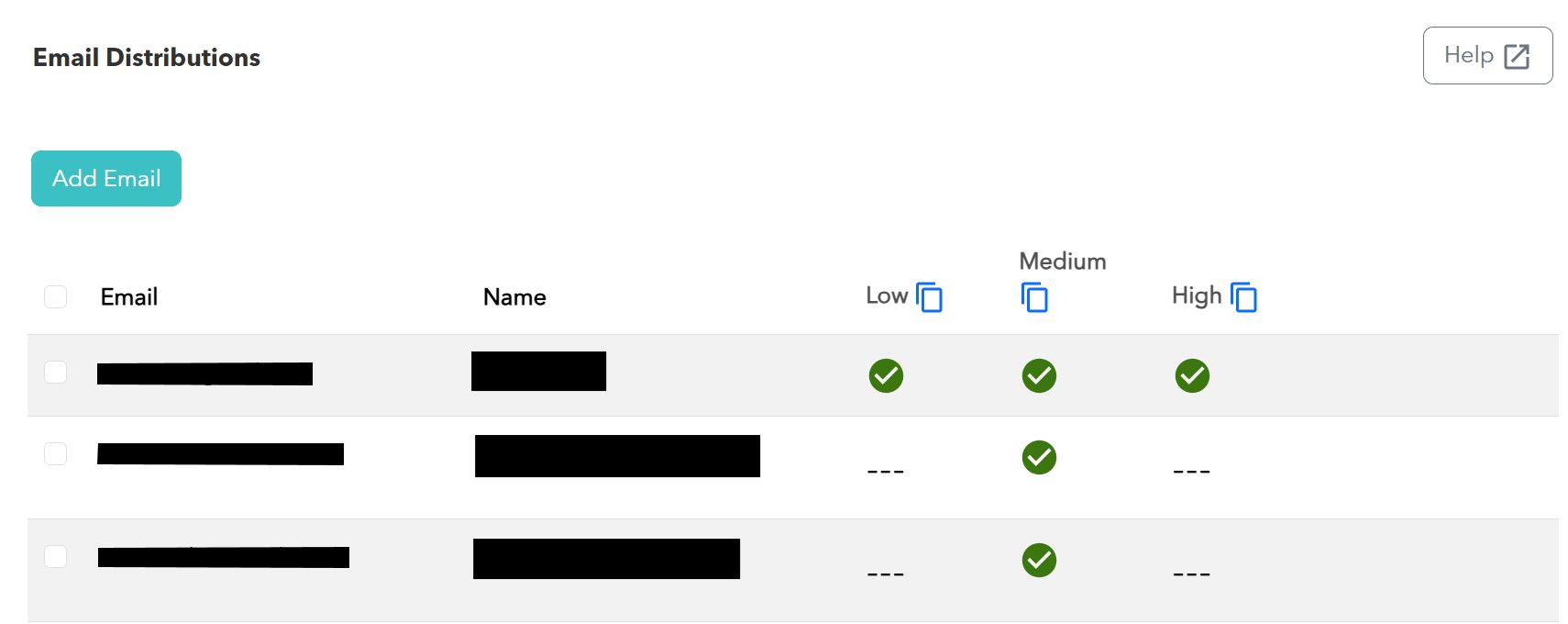
For more information, see Working with Email Distribution Contacts.
Improvements
Special characters and spaces not allowed when setting up SOAR/ATR
When you’re setting up ATR for firewalls, special characters and spaces are no longer allowed in the Firewall Group Name and Firewall Network Group Name fields.
Non-Rule Bug fixes
Bug Number | Description |
|---|---|
7367 | Resolved an issue where the world map view on the Intelligence > O365 Protection page did not show locations accurately after returning to the page after navigating to another page. |
7705 | Resolved an issue where some tenants would not appear in the account switcher when there were over 10000 records. |
Rules
New rules
FortiGate firewall administrator actions taken:
FortiGate Admin User Deleted On Firewall
FortiGate Local User Enabled
FortiGate System Config File Downloaded Via GUI
Microsoft 365 Defender has detected that a user’s valid credentials have been leaked
This rule triggers when Microsoft 365 Defender detects that a user’s valid credentials have been leaked — a capability recently added in the Defender.
Microsoft Defender for Cloud High Severity Incident Detected
Rule tuning and bug fixes
Improved Microsoft Office 365 Anomalous Login logic to always consider NULL geo-locations
Improved GLB.AU.CAS Google Workspace Unusual Login dynamic severity criteria to incorporate as part of Google Workspace ATR
Removed first time users from triggering Microsoft Office 365 Anomalous Login and Microsoft Office 365 Impossible Travel
Improved Google Drive Volume File Deletion
Ticket body was updated to reflect threshold increase from 50 to 200 file deletions.
Improved Microsoft Office 365 Email Forwarding Rule Created Modified or Deleted
UpdateInboxRules has been added as a new operation in addition to NewInboxRules and Set-Mailbox
Improved EGD Data Exfiltration Detected
Implemented historical lookback on the exfiltration reason if this is commonly done by the user. Certain reasons bypass this correlation such as creditcard info.
Improved FortiGate SSL VPN Password Spraying Activity
Implemented grouping of source IPs to reduce total number of alerts sent
Retired rules
Meraki Detected Multiple Communication To Russia
SophosXG Detected Multiple Communication to Russia
