In September, the following features were changed or added to Barracuda XDR:
New features-In addition to the new integration with Barracuda Application Protection, Managed XDR released many new improvements including log search and analysis that includes AI, access BarracudaONE from Managed XDR Dashboard, new monitoring rule for Cisco FTD zero-day vulnerability, and many more.
New rules-Three new rules were added.
Tuning and bug fixes-Several rules have been refined and enhanced with ATR.
New Features
Powerful AI summary
Now when you log in to the Barracuda XDR Dashboard, you are presented with a summary of the important events that have happened in seven days. This useful, actionable data features threats, risks, and changed statuses for endpoint devices, tickets, and data sources, saving you time by doing the investigation for you.
At a glance, you can identify the most urgent tasks that will improve your security, and get more information on each one with a single click.
You have the choice to expand or collapse the summary by default, each time you visit the dashboard.
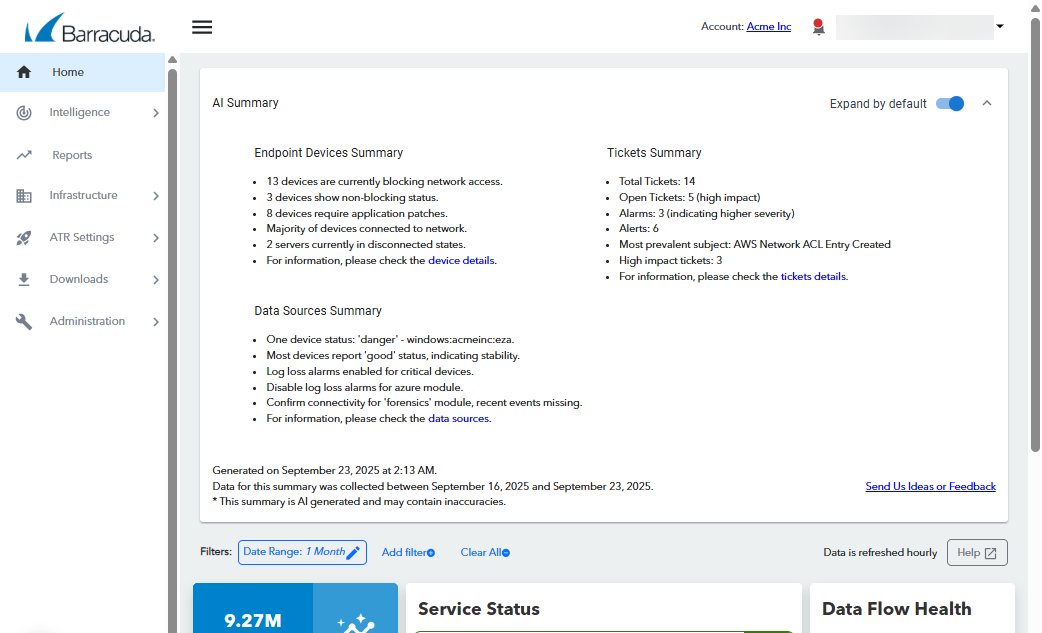
For more information, see Working with the AI summary.
NOTE You can give feedback on our AI features by clicking the Send Us Ideas or Feedback link.
AI Data source log query and analysis
Create powerful queries for your data source logs with the power of generative AI. Barracuda XDR takes queries written in natural language and uses AI to turn your words into robust SQL queries to identify data and trends in your data source logs.
This makes it easier for you to fulfill compliance/regulatory audits by giving you a fast way to get the required log data.
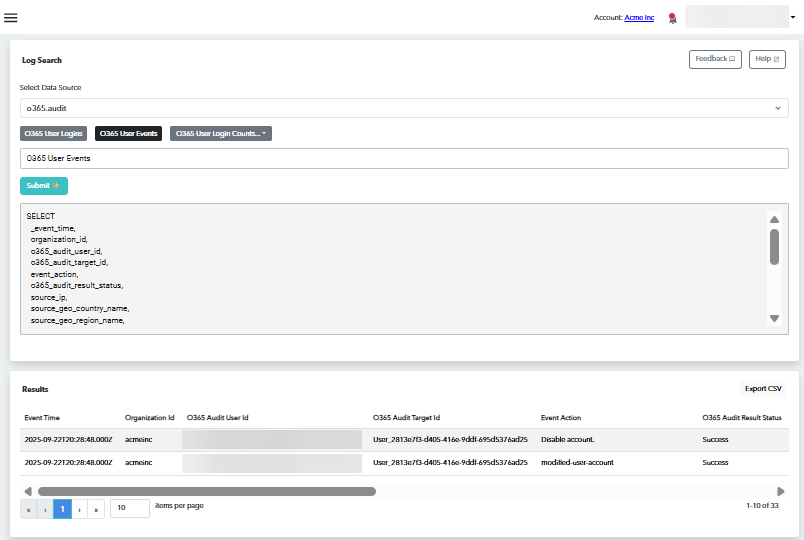
For more information, see Querying Data Source Logs with Generative AI.
NOTE You can give feedback on our AI features by clicking the Send Us Ideas or Feedback link.
Microsoft Defender for Endpoint ATR is now live
Setting up ATR for Microsoft Defender for Endpoint means XDR can now automatically isolate an endpoint from the network for all users.
When ATR detects a Microsoft Defender account has been compromised, Barracuda XDR automatically responds by suspending the affected account through the API. This suspension restricts access to all Microsoft services and triggers session invalidation, helping to contain threats in real time.
For more information, see Setting up ATR for Microsoft Defender for Endpoint.
Barracuda Application Protection/Web Application Firewall as a Service (WAFaaS) integration
To provide integrated protection against sophisticated attacks, you can now integrate Barracuda Application Protection, also known as Web Application Firewall as a Service (WAFaaS), with Barracuda XDR.
For more information, see https://campus.barracuda.com/doc/292895109/.
Access to Barracuda Managed XDR with Microsoft SSO
XDR users can now log in to the Dashboard with the Barracuda login app, using Microsoft Single Sign On credentials. Using this log in method lets you access BarracudaONE and other Barracuda products without the need to enter your credentials again.
If a user has multiple logins associated with their email, the login shows the username and name of the user to avoid confusion.
For more information about BarracudaONE, see the BarracudaONE help.
New internal tools
If multiple incidents of the same type occur within 72 hours of each other, they are automatically combined into a single alert. This makes it easier to identify patterns and correlations within environments while reducing fatigue and confusion.
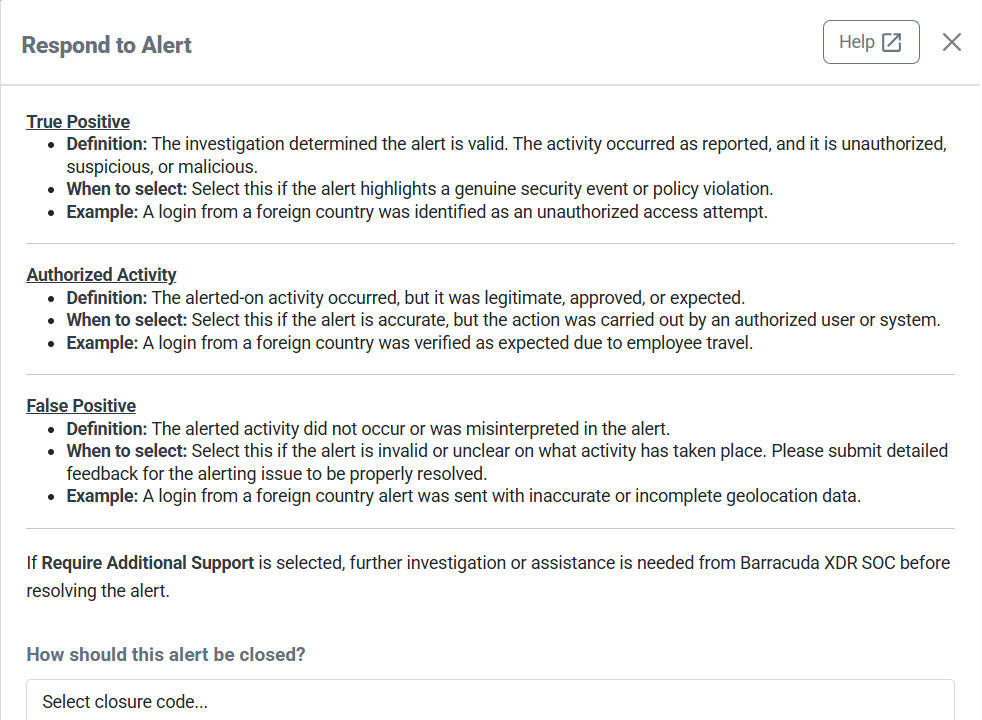
Improved closure codes
The closure codes are now clearer, including when you should select each and useful examples.
SentinelOne agent upgrade to 25.1
The SentinelOne agent has been upgraded to 25.1. For more information, see https://campus.barracuda.com/product/xdr/doc/648329155/barracuda-xdr-sentinelone-agent-release-notes .
New Rules
The following are rules added in September 2025:
XDR Managed Endpoint Security STAR rule - ScreenConnect DNS Query for Suspicious TLD. This rule is designed to detect threat actors early on in an attack lifecycle, when they are staging the attack by abusing remote connection tools either with a LOTL (living off the land) strategy and/or abusing legitimate tools. This rule has ATR enabled so that when detected, impacted endpoint(s) are isolated from the network to remove the threat actor from the environment.
Cisco FTD Zero-Day Vulnerability: CVE-2025-20333 (CVSS score: 9.9) - An improper validation of user-supplied input in HTTP(S) requests vulnerability that could allow an authenticated, remote attacker with valid VPN user credentials to execute arbitrary code as root on an affected device by sending crafted HTTP requests.
GLB.AA.NET Cisco FTD Suspicious VPN Login (WMIC)
GLB.AA.NET Cisco FTD Suspicious SSL-VPN Login (Elastic Agent)
Email Gateway Defense Unusual Volume of Emails Sent - detect mass emails sent from internal users.
Tuning and Bug Fixes
GLB.AU.CAS Microsoft Defender for Office 365 High Severity Incident Detected - A potentially malicious URL click was detected.
An alert is no longer be sent if the incidents Defender status is resolved and classified as informational or a false positive.
Incidents with all listed message, mailbox, and URL evidence with remediation status removed (remediated) or blocked (prevented) are de-escalated to a Medium Severity.
Alert has been modified to correctly identify the affected user.
Remove hostname from alert correlation if hostname is a browser. This is to improve the quality of the correlation.
Microsoft Office 365 Suspicious New Inbox Rule Created - Added an explanation in the alert to provide reasoning behind which inbox rules are considered suspicious.
Microsoft Office 365 Anomalous Login Logic Updated
Querying device names that appear with the IP address surrounding the login to see if the user had used this device before.
Incorporated Azure correlation to drop alerts for successful MFA from Azure AD joined devices.
Included a /24 subnet CIDR lookback to prevent alerts from the same CIDR range in a short period of time.
Non-malicious ISP logins have the ability to be dropped based on the user’s history of logging in from that ASN.
Suricata Internal Permitted Traffic - Alerting criteria was changed to only alert on signatures created since 2023.
Okta High Number of Okta User Password Reset or Unlock Attempts - Alerting was changed to focus on the user which requested the password reset and not the system user.
Rules Enhanced with ATR
New Rule Automation in ATR “GLB.AA.ADS Azure Service Principal Granted High Risk Permissions”
New new automation in ATR “Barracuda EGD Unusual Volume of Emails Sent”
