Barracuda Assistant is now available!
Barracuda Assistant makes Barracuda knowledge more accessible than ever by bringing the power of Barracuda Campus right into the product experience
Instant expertise: Provides fast, accurate answers drawn directly from trusted Barracuda Campus content.
Simplifies complexity: Translates technical documentation into clear, conversational guidance.
Saves time: Eliminates the need to search across multiple pages or platforms for answers.
Always available: Delivers 24/7 access to Barracuda knowledge across all products where adopted.
Cisco Umbrella ATR is now live
Cisco Umbrella ATR checks IP addresses of allowed traffic to see if XDR Threat
Intelligence classifies the IP as malicious. The domain of malicious IP addresses are automatically blocked, also blocking any questionable IP addresses.
For more information, see Setting up ATR for Cisco Umbrella.
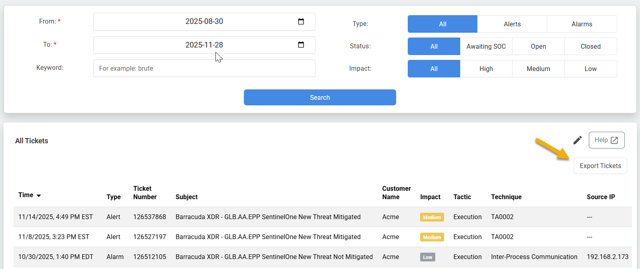
Export All Tickets table
You can now export the contents of the All Tickets table on the Alarms & Alerts page. On Intelligence > Alarms & Alerts, click the Export Tickets  button.
button.
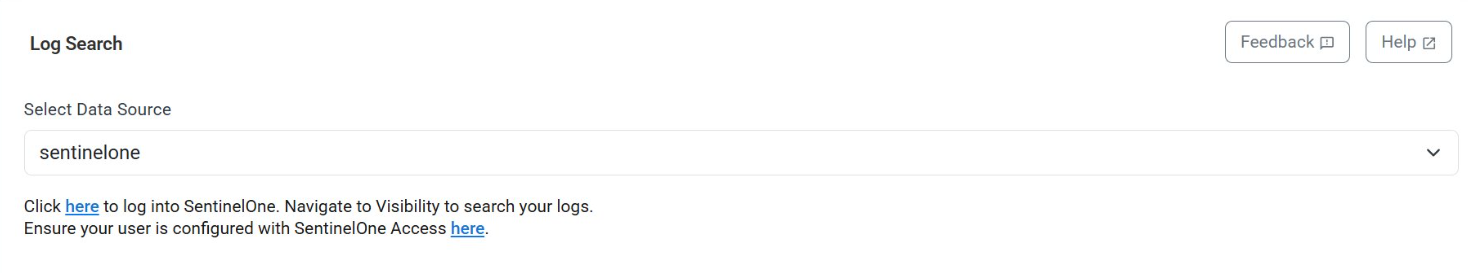
Easily SentinelOne Log Search
You can now easily navigate to a full SentinelOne log search from Barracuda Managed XDR. On the Intelligence > Log Search page, select sentinelone. You can then click the link to go to the SentinelOne console for full log search functionality.
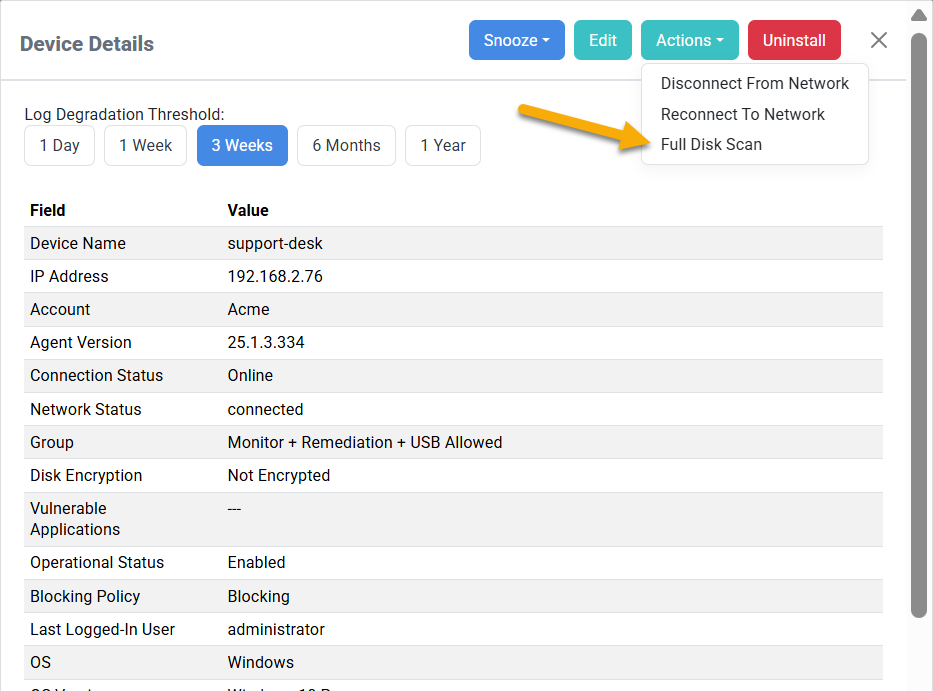
Full Disk Scan added to Device Actions button on the Endpoint Devices tab
You can now perform a full disk scan from the Device Actions button. Click Infrastructure > Endpoint Devices, then click a device. Click the Actions button, then click Full Disk Scan.
Resolved issues
Resolved issues |
|---|
Resolved an issue where ticket status labels weren’t consistent. |
Resolved an issue where IP addresses were missing in the ATR settings for Cisco Meraki. |
Resolved an issue where certain fields were missing information on the following pages:
|
Resolved an issue where Microsoft 365 login events didn’t show on the map on the Intelligence > O365 Protection page. |
Resolved an issue where certain users didn’t see all their data sources on the Intelligence > Log Search page. |
Resolved an issue on the Microsoft Defender for Endpoint integration page where users saw a message that only admin users could enable the integration, in error. |
Resolved an issue where the last login date was showing incorrectly in the XDR Dashboard. |
New Rules
Description | |
|---|---|
Fortigate Malware Traffic Detected | Detected malware categories (Virus, Trojan, Ransomware, Adware, File Hash) on Fortinet firewall, indicating potential evasion or misconfiguration |
Fortigate RDP Logon From New Source | New-terms rule check the user history from last 90 days and generate an alert when user perform RDP activity from new source ip. |
Watchguard Metasploit Signature Match Detected | This event is triggered whenever Metasploit payloads or exploits are identified. Adversaries make use of Metasploit to deploy exploits and payloads. |
Sonicwall Threat Signature Detected | A potential threat has been identified by SonicWall through its attack signature detection. |
Sonicwall Config Change Detected from Public IP | A configuration change is detected on Sonicwall Firewall from Public IP. |
Sonicwall RDP Logon From New Source | We detected a new login from an IP we have not seen before. |
Sonicwall Admin Login from Suspicious Public IP | This alert detects successful external logins from malicious Public IPs to Sonicwall Firewall. Note: Malicious determination is made by Barracuda XDR Risk Scoring in Tines. This rule simply collects logins for further analysis. An alert will go to the customer if the risk score is greater than 30 for a given source IP. |
Sonicwall Admin User Added On Firewall | Detects the modification in Administrator group list. |
XDR Managed Endpoint Security Data Exfiltration STAR rule | Detects common indicators of data exfiltration techniques occurring on an endpoint. These indicators are based on activities observed by the Barracuda XDR SOC team during real-world ransomware incidents, as well as open source threat intelligence resources. Data exfiltration is a common step in a ransomware attack lifecycle, occurring before impact/execution. This rule helps alert our customers of an attack that may be unfolding prior to it ultimately reaching the point of ransomware detonation, which aids in limiting data loss and eventual encryption. |
Rule Tuning and Bug Fixes
Barracuda IDS - Removed old and outdates signatures from alerts due to poor security value.
Microsoft Defender for Endpoint Malicious Threat Detected Not Remediated - Improved deduplication and alert stitching to not create multiple tickets for a single incident
Windows User Deleted/Added from High Risk Security Group - Added correlation on user logins.
Rules Enhanced with SOAR
Rule Automations:
Over 57 existing rules automated with SOAR across Microsoft 365, CrowdStrike, Firewalls and windows, reducing time to detect and time to respond.
