To enable dual-factor authentication for Barracuda WAF web interface access, perform the following steps:
- Log into the Barracuda Web Application Firewall web interface.
- Go to the ADVANCED > Admin Access Control page.
- In the External Authentication Services section:
- Select LDAP from the Add Authentication Services drop-down list. The Add LDAP Service page opens.
- On the Add LDAP Service page, enter your LDAP server details and click Save. For information about LDAP configuration, see How to Configure Authentication and Access Control (AAA).
- Select RADIUS from the Add Authentication Services drop-down list. The Add RADIUS Service page opens.
- On the Add RADIUS Service page, enter your RADIUS or RSA SecurID server details and click Save. For information about RADIUS configuration, see How to Configure Authentication and Access Control (AAA).
- Select LDAP from the Add Authentication Services drop-down list. The Add LDAP Service page opens.
- In the Administrator Account Settings section:
- Set Dual Authentication to Enable.
- Set Use RSA SecureID to Yes if you have specified RSA SecurID server details in the RADIUS service configuration. If not, keep the setting to No.
- Click Save.
Dual-Factor Authentication Flow with the Barracuda WAF Web Interface
When dual-factor authentication is enabled, the user is challenged to provide the username, password and passcode (RADIUS user password) to access the Barracuda Web Application Firewall.
Login screen when dual-factor authentication is enabled with LDAP and RADIUS authentication services
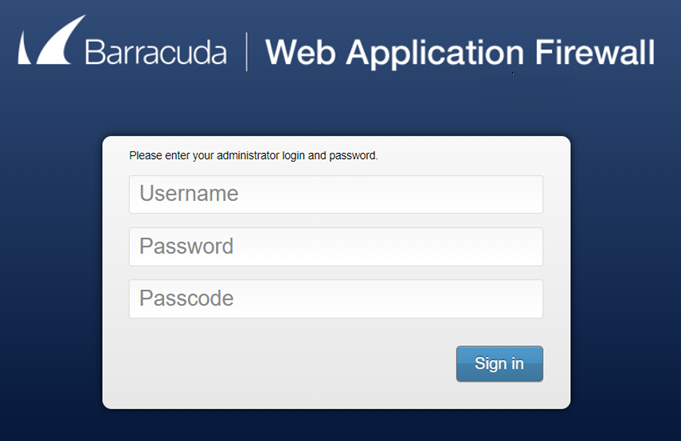
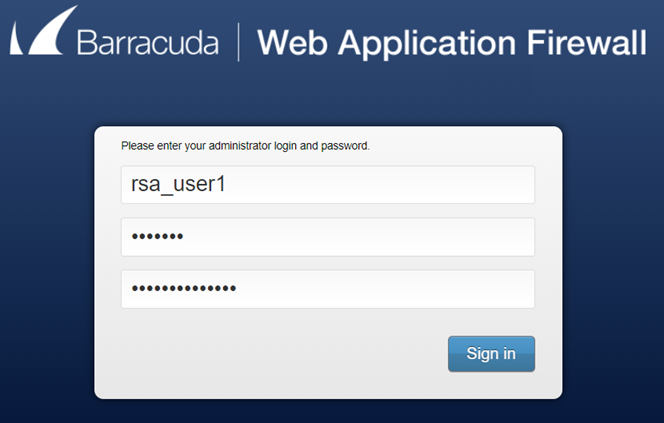
Login screen when dual-factor authentication is enabled with LDAP and RSA SecurID authentication services
The user is challenged to provide the username, password, and passcode (PIN followed by the RSA SecurID token code).
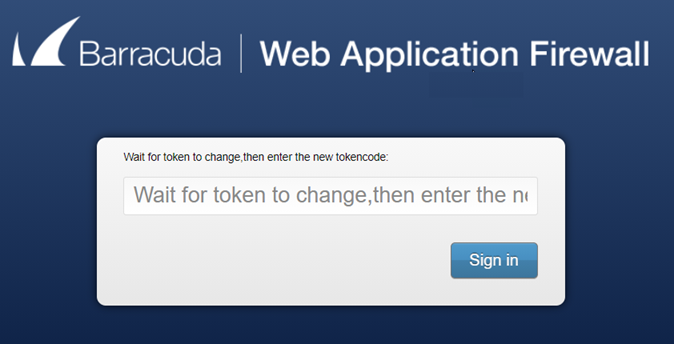
If the passcode is incorrect, the user is shown a challenge page to re-validate the passcode.
API Calls Required to Get the Session Token
To get a token for API when dual-factor authentication is enabled with LDAP and RSA SecurID authentication services, perform the following steps:
Login Request:
Send a login request with the username, password, and passcode (if RSA SecuID is configured).
curl http://<IP:PORT>/restapi/v3/login -X POST -H Content-Type:application/json -d '{"username":"krbtest2","password":"35HJ2ab", "passcode":"63445348"}'
Response :
{"challenge":"b0a123456adxxxx52fab93f7xxxx12ee","message":"Enter a new PIN having from 4 to 8 alphanumeric characters:\u0000"}
If you get a challenge back with a message, pass the challenge back as JSON along with the passcode to the login-dual-auth controller.
Dual Auth Request
curl http://<IP:PORT>/restapi/v3/login-dual-auth -X POST -H Content-Type:application/json -d '{"challenge":"b0a123456ad23a523f6e93f7xxxxxxee", "passcode":"xyz35"}'
Response :
{"challenge":"b0a123456ad23a523f6e93f7xxxxxxee","message":"\r\nPlease re-enter new PIN:\u0000"}
Re-enter the PIN and send the request again:
curl http://<IP:PORT>/restapi/v3/login-dual-auth -X POST -H Content-Type:application/json -d '{"challenge":"b0a123456ad23a523f6e93f7xxxxxxee", "passcode":"xyz35"}'
Response:
{"challenge":"b0a123456ad23a523f6e93f7xxxxxxee","message":"\r\nPIN Accepted.\r\nWait for the token code to change,\r\nthen enter the new passcode:\u0000”}
Request with the passcode:
curl http://<IP:PORT>/restapi/v3/login-dual-auth -X POST -H Content-Type:application/json -d '{"challenge":"b0a123456ad23a523f6e93f7xxxxxxee", "passcode":"xyz3545514106"}'
Response :
{"token":"eyJ1c2VyIjoia3JidGVzdDIiLCJldCI6Ixxxxxx3MzQwODIiLXxxxxxzd29yZCI6IjlkMzY0MzEx\nZGE0NWMyNTA4xxxxxxU5MTNkYmU1MGQyIn0=\n"}
If the PIN is already set, send the request with the PIN and new token:
curl http://<IP:PORT>/restapi/v3/login -X POST -H Content-Type:application/json -d '{"username":"krbtest2","password":"35HJ2ab", "passcode":"xyz3513637390"}'
Response :
{"token":"eyJldCI6IjE1MjQ3MzQ4NjMxxxxxx2VyIjoia3JidGVzdDIiLCJxxxxxxXxyZCI6ImZhZDhiMzc1\nYTE1ODkwZjFhNjc0MDM4XxxxXXxxYmI5In0=\n"}
