The Intrusion Prevention System (IPS) actively monitors local and forwarding traffic for malicious activities and can also block suspicious traffic. The IPS engine analyzes the network traffic and continuously compares the bitstream with its internal signatures database for malicious code patterns. You can create, edit, and override the default and custom IPS signature handling policies. After configuring your IPS policies, you can also apply them to your access rules. IPS policies are based on SNORT rules.
Prerequisite for Running IPS (Only relevant for virtual systems)
IPS requires large amounts of data to be scanned in a very short time period. To do so, the CPU must support the SSE4.2 instruction set. If this instruction set is present in your firewall’s CPU, and your firewall is licensed, IPS will work as expected.
However, if this instruction set is not present, and even if IPS is licensed, the IPS module cannot be loaded and thus will not work. This will also be displayed in the Status Map of the CC and in the SUBSCRIPTION STATUS element in the firewall’s DASHBOARD, as shown in the following screenshot:
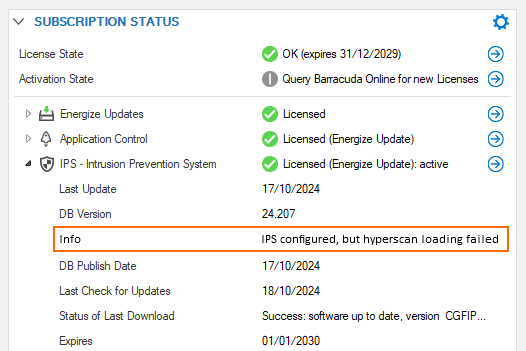
This is also reported with a corresponding error message in the firewall.log file:
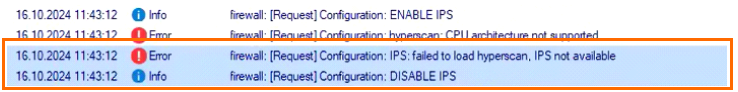
There are two possible reasons for this problem:
The virtualized CPU does not support the required instruction set (SSE4.2).
The hypervisor is not passing through the hyperscan instruction set properly.
If you are unsure of either of the following:
your firewall’s CPU supports the SSE4.2 instruction set
the hypervisor passes through the instruction set
You can check this via SSH. To do so, perform the following steps:
Log into your firewall.
Go to SSH.
Log into SSH.
Enter the following command into the terminal window:
cat /proc/cpuinfo | grep flags | grep sse4You will see an output similar to the following:
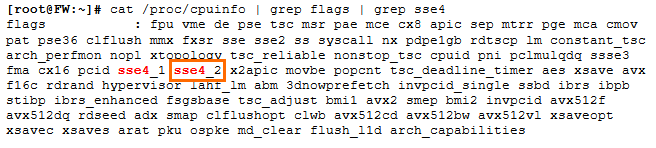
If the string sse4_2 is present, then IPS can be handled by the firewall.
If you see IPS configured, but hyperscan loading failed on the firewall's DASHBOARD, or if you see CPU architecture not supported in the Firewall log, make sure your hypervisor exposes the required CPU flags. For KVM/Proxmox, you must set the CPU Type to host in order to pass the required flags.
IPS Features
TCP Stream Reassembly
The firewall engine provides support for TCP Stream Reassembly (SRA). In general, TCP streams are broken into TCP segments that are encapsulated into IP packets. By manipulating how a TCP stream is segmented, it is possible to evade detection, for example, by overwriting a portion of a previous segment within a stream with new data in a subsequent segment. This method allows the hacker to hide or obfuscate the network attack. The firewall engine receives the segments in a TCP conversation, buffers them, and reassembles the segments into a correct stream, for example, by checking for segment overlaps, interleaved duplicate segments, invalid TCP checksums, and so forth. Afterward, the firewall engine passes the reassembled stream to the IPS engine for inspection.
URL Obfuscation
The IPS engine provides various countermeasures to avert possible network attacks based on the following URL encoding techniques:
Escape encoding (% encoding)
Microsoft %u encoding
Path character transformations and expansions ( /./ , //, \ )
Premature URL ending
Long URL
Fake parameter
TAB separation
FTP Evasion
The IPS engine can avert FTP exploits where the attacker tries to evade the IPS by inserting additional spaces and Telnet control sequences in FTP commands.
TCP Split Handshake
The IPS engine provides an evasion countermeasure technique that can block the usage of TCP split handshakes attacks. Although the TCP split handshake is a legitimate way to start a TCP connection (RFC793), it can also be used by hackers to execute various network attacks by gaining access to the internal network by way of establishing a trusted IP connection, thereby evading firewall and IPS policies.
IPS in the DASHBOARD
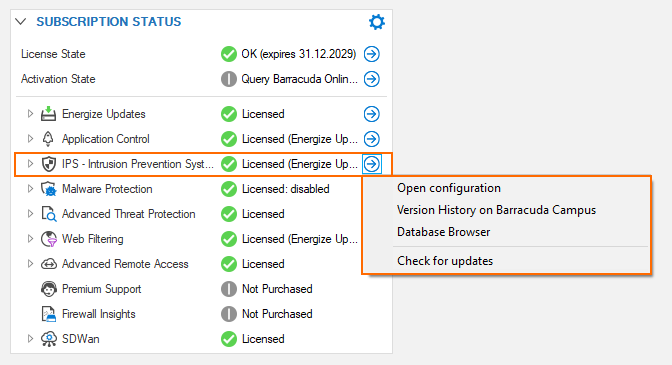
Because the IPS system is part of a subscription license, its status is displayed in the related DASHBOARD element SUBSCRIPTION STATUS. When clicking the blue arrow icon to the right of IPS license status, a menu list displays the available options for IPS. Clicking one of these options will trigger different actions:
Open Configuration – Opens the view for configuring the IPS system.
Version History on Barracuda Campus – Opens a browser window displaying the version history on a Campus web page.
Database Browser – Opens a window that lets you inspect the IPS database.
Check for Updates – Checks for updates.
Version History on Barracuda Campus
You can inspect a version history on Barracuda Campus by clicking this link: https://campus.barracuda.com/to/ipsversions.
Database Browser
The database browser displays a list of known, common vulnerabilities and exposures (CVEs) that could be or become a threat. The list view provides the option of filtering and searching certain CVEs based on the string which you can enter at the top of a related column category.
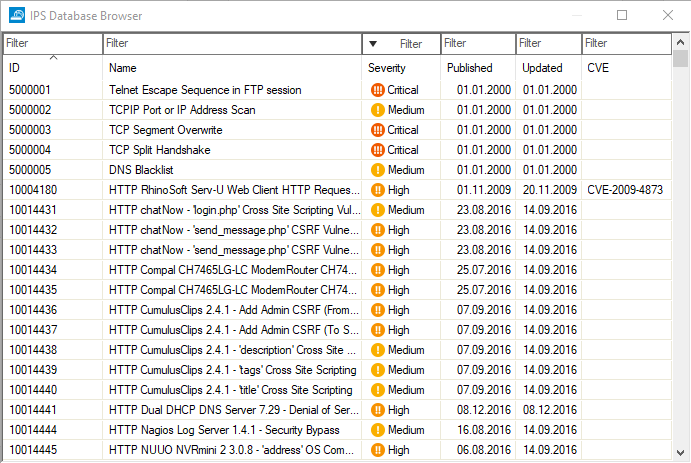
Clicking the tiny blue arrow to the right of a CVE entry makes another list display that contains numerous links that are directly associated with the CVE entry:
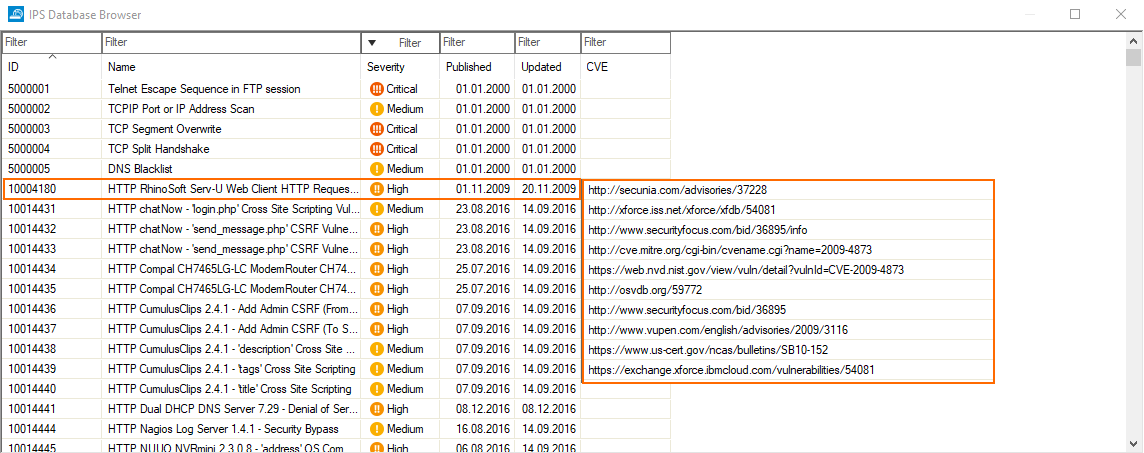
Clicking one of the links opens the favorite browser that will then try to load the associated web page.
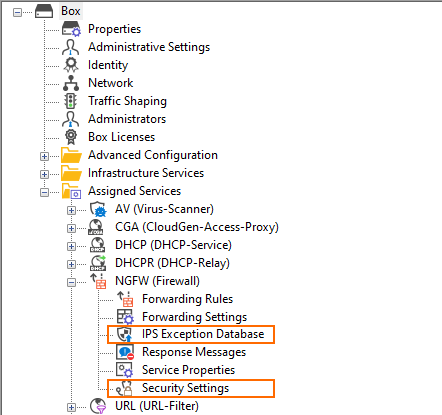
IPS in the Configuration Tree
There are 3 special nodes in the configuration tree that are affected by the improvements of firmware 8.3.0.
IPS Policies
IPS Exception Database
Security Policy
Some of these nodes have been renamed:
Firmware Version | IPS Policies | Security Policy |
|---|---|---|
< 8.3.0 (old naming) | IPS Policies | Security Policy |
= 8.3.0 (new naming) | IPS Profiles | Security Settings |
Compare the old and new nodes in the configuration tree:
Configuration Tree Nodes with Old Naming | Configuration Tree Nodes with New Naming |
|---|---|
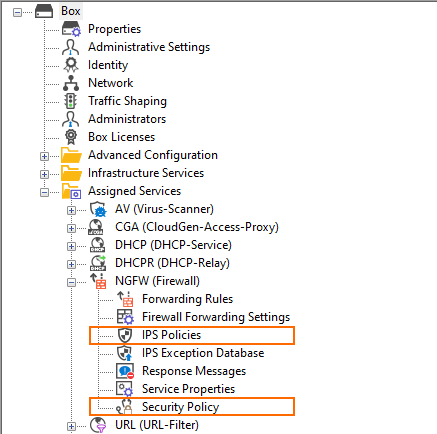 | 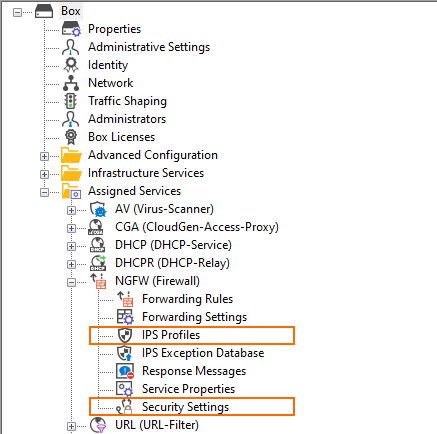 |
Because the IPS correlates with the CGF-Policies feature, the visibility of the IPS Profiles node in the configuration tree depends on the activation status of that feature. If the CGF-Policies feature is activated, then the node IPS Profiles will disappear in the configuration tree and only the nodes IPS Exception Database and Security Settings will remain visible:
Configuring and Managing IPS
For step-by-step instructions on how to configure and manage IPS, see the following articles:
