Port Protocol Protection uses deep packet inspection to enforce the used protocol on a port. Port protocol detection can be configured with a positive or negative security model. The allow list policy allows only the selected protocols; the block list mode allows all protocols that are not selected.
Before You Begin
Create a service object. For more information, see Service Objects.
Step 1. Enable Port Protocol Protection
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > General Firewall Configuration.
- In the left menu, click Application Detection.
- From the Enable Protocol Detection list, select yes.
- Click Send Changes and Activate.
Step 2. Add Port Protocol Protection to a Service Object
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Services.
- Double-click the service object. The Edit/Create Service Object window opens.
- Double-click the service entry. The Service Entry Parameters window opens.
From the Action for prohibited Protocols list, select the Port Protocol Protection policy:
No Protocol Protection – Disable Port Protocol Protection.
Report – Report prohibited protocols on the FIREWALL > Live and FIREWALL > History pages.
Reset – Sessions using unallowed protocols are terminated with a TCP RST.
Drop – The session with the unallowed protocol is kept open, but the traffic is dropped.
- From the Detection Policy list, select Allow Listing or Block Listing.
- In the Allow Listed Protocol list, expand the menu items and double-click on every protocol you want to add to the Detection policy.
- Click OK
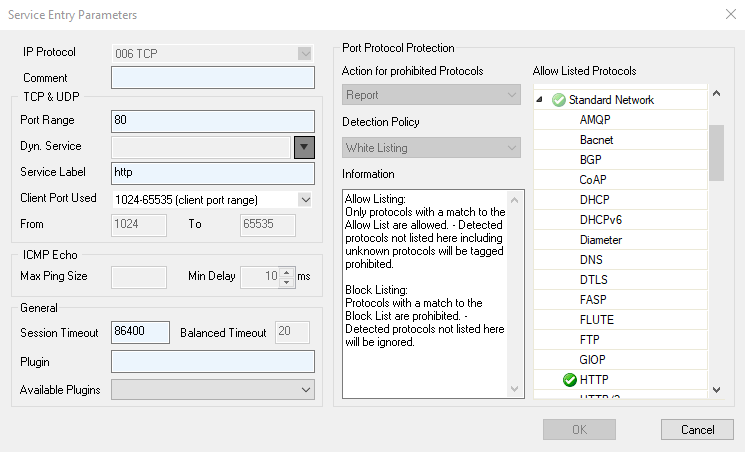
- Click OK.
- Click Send Changes and Activate.
