Inline authentication intercepts unauthorized users HTTP or HTTPS connections and redirects them to a login page on the Barracuda CloudGen Firewall. After successful authentication the user is forwarded to the original destination. This type of authentication is used to allow HTTP/HTTPS access to authenticated users. Access rules using inline authentication do not block non HTTP or HTTPS traffic even from unauthorized users. To avoid browser certificate errors, use a signed SSL certificate or install the root certificate of the self-signed certificate on all client computers using Inline Authentication.
Before You Begin
Choose and configure the authentication scheme. For more information, see Authentication.
Step 1. Configure the Firewall Authentication Settings
For a basic configuration, only a default HTTPS certificate and the corresponding key is required. Download and install the root certificate on all client computers to avoid browser certificate errors.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Settings.
- In the left menu, select Authentication.
- Click Lock.
- Click the Operational Settings Edit button. The Operational Settings window opens.
- (optional) Set Refresh auth every... min to the number of minutes the authentication is valid for. Default:
5 - (optional) Set Refresh auth tolerance... min to the number of minutes that a peer does not have to authenticate again after reconnecting.
- Click OK.
Import or create the Default HTTPS Private Key and Default HTTPS Certificate.
- In the Metadirectory Authentication section, select a previously configured Authentication Scheme. For more information, see Authentication.
- Click Send Changes and Activate.
Step 2. Create the Access Rule for Inline Authentication
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Create an access rule that allows HTTP+S connections to the web server.
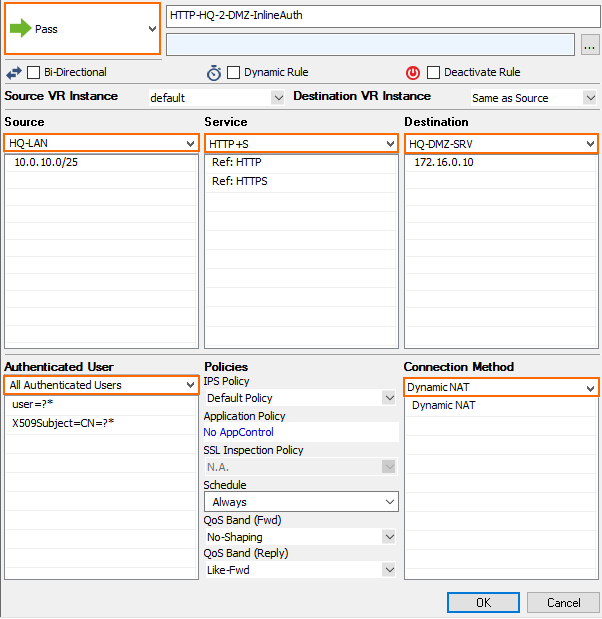
- In the left menu of the rule editor window, click Advanced.
- In the Miscellaneous section, select Login+Password Authentication from the Inline Authentication for HTTP and HTTPS list.
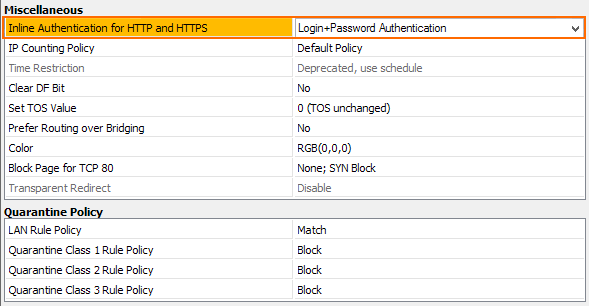
- In the left menu, click Rule.
- In the Authenticated User section, specify the users this rule should match for. You can either define a user group object or create an explicit user condition for this rule.
- To grant access to all authenticated users, select All Authenticated Users.
- To create an explicit user condition:
- Select <explicit-user>.
- Right-click the table and select Edit.
- In the Edit/Create User Object window, click New.
- In the User Condition window, specify all authenticated users that are allowed access to the web server.
- Click OK.
- Click Send Changes and Activate.
