Offline Firewall Authentication works with all CloudGen Firewall services. The user is authenticated by the fwauth daemon. To implement offline firewall authentication, configure your firewall authentication settings and create an App Redirect access rule with the destination set to an internal firewall IP to let users access the fwauth service. The user can then use the Barracuda CloudGen Authentication Client or the browser login. The fwauth service listens on 127.0.0.1. Depending on the type of authentication required, use the following ports:
TCP 80 – Username/password authentication. (HTTP only) Use for external authentication servers (e.g., MSAD).
TCP 443 – Username/password (HTTPS with automatic redirect to HTTPS for HTTP requests). Use for external authentication servers (e.g., MSAD).
This is the classic method for offline authentication, where a user connects directly to the firewall for authentication. After the login, a success page is displayed and the browser tab needs to stay open as described in this article below.TCP 448 – Username/password (HTTP and HTTPS) with automatic redirection. Use for external authentication servers (e.g., MSAD).
This authentication method is intended to be used similarly to the guest access captive portal. Related rules are similar, and as a result any non-authenticated user will be first sent to fwauth and then be redirected back to the originating target URL.TCP 444 – X.509 certificate authentication (HTTPS with automatic redirect to HTTPS for HTTP requests).
TCP 445 – X.509 certificate plus username/password authentication (HTTPS with automatic redirect to HTTPS for HTTP requests).
Usage of Special Characters and Umlauts in Passwords
When configuring Offline Firewall Authentication, you must consider whether passwords may contain special characters, e.g., € or umlauts. Because characters will be translated between the web browser and the firewall and between the firewall and the authentication service using codepages, it is important to decide which client codepage will be used and which authentication scheme supports the appropriate character conversion.
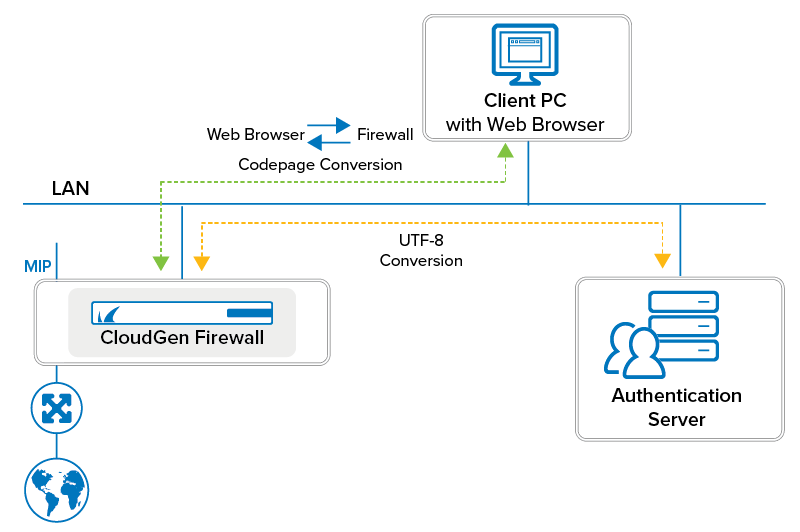
The following table shows if codepage will be used, under which constraints it will be used, and if special characters will be translated correctly:
Conversion of | Web Browser > | Firewall > | Authentication Scheme |
|---|---|---|---|
NO | 8859-1 | UTF-8 | Any |
YES | 8859-15 | UTF-8 | Any |
YES | UTF-8 | UTF-8 | Any |
YES | Windows 1252 | - | NGFLocal |
The codepage in the column Web Browser > CODEPAGE > Firewall can be configured.
(Optional) Step 1. Configure the Codepage if Special Characters Must Be Allowed in Passwords
Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Service > Authentication Service.
Click Lock.
In the left menu, click Configuration Mode.
In the left menu, click Switch to Advanced.
In the left menu, click Timeouts and Logging.
In the section Expert Settings, for Client Codepage, select the codepage according to the upper table and that best fits your requirements.
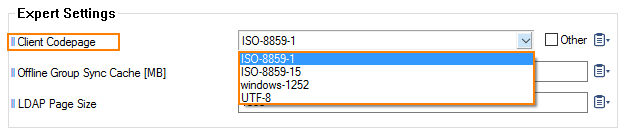
Click Send Changes.
Click Activate.
Step 2. Configure the Firewall Authentication Settings
Set the HTTPS private key and certificate to activate firewall authentication.
Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Settings.
In the left menu, click Authentication.
Click Lock.
(optional) Edit the Operational Settings.
Upload or create the HTTPS Private Key and Certificate.
Select the Authentication Scheme from the list, e.g., MS Active Directory. For more information, see Authentication.
Click Send Changes and Activate.
Step 3. Create Access Rules for Offline Authentication
To let users go directly to the firewall login page to log out or log in, set the Destination IP to an internal firewall IP (not the management IP).
Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
Click Lock.
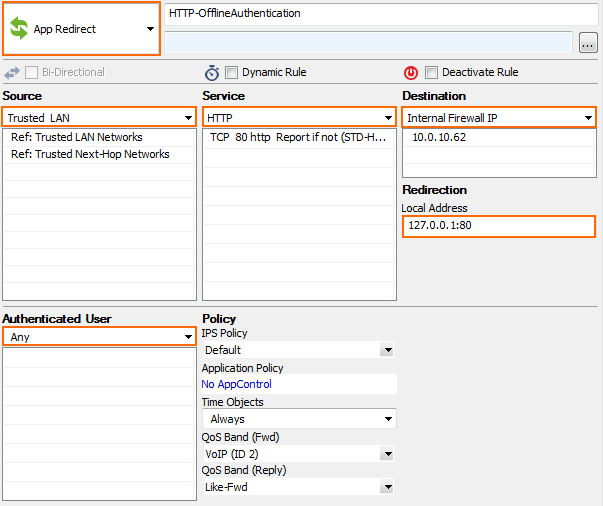
Create an App Redirect access rule for HTTP traffic:
Source – Select Trusted Networks, or enter the internal network for the clients who need to authenticate.
Service – Select HTTP.
Destination – Enter an internal IP used by the firewall service. Do not use the management IP.
Redirection – Enter
127.0.0.1:<port>. Enter the port of the authentication method supporting HTTP: 80, 444,445,448 - see list at the top of the page.Authenticated User – Select Any.
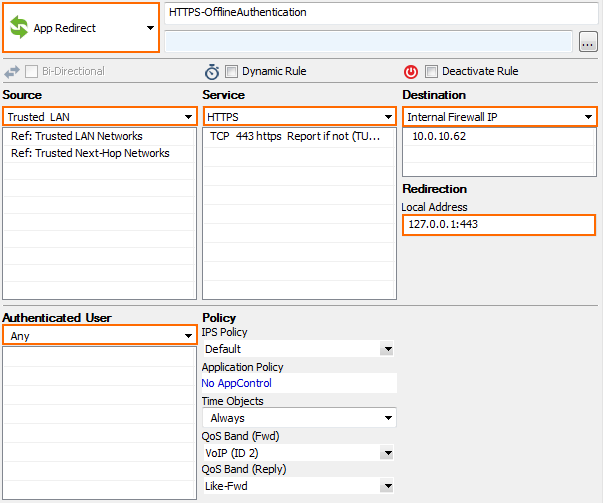
(optional) Create an App Redirect access rule for HTTPS traffic:
Source – Select Trusted Networks, or enter the internal network for the clients who need to authenticate.
Service – Select HTTPS.
Destination – Enter an internal IP used by the firewall service. Do not use the management IP.
Redirection – Enter
127.0.0.1:<port>. Enter the port of the authentication method supporting HTTP: 443, 444, 445, 448 - see list at the top of the page.Authenticated User – Select Any.
Move the redirect rules above the INTERNET-2-LAN rule.
Click Send Changes and Activate.
Step 4. Authenticate to the Barracuda CloudGen Firewall
After implementing offline authentication, you can use it to log into the CloudGen Firewall.
Go to http://<IP address used as destination in the access rule>
On the login screen, enter your user credentials, and click Login.
Keep the authentication page open for as long as you need to be connected to the Barracuda CloudGen Firewall. If you close the browser, you are automatically logged out after five minutes. This limitation does not apply if you are using the Authentication Client to log in.
