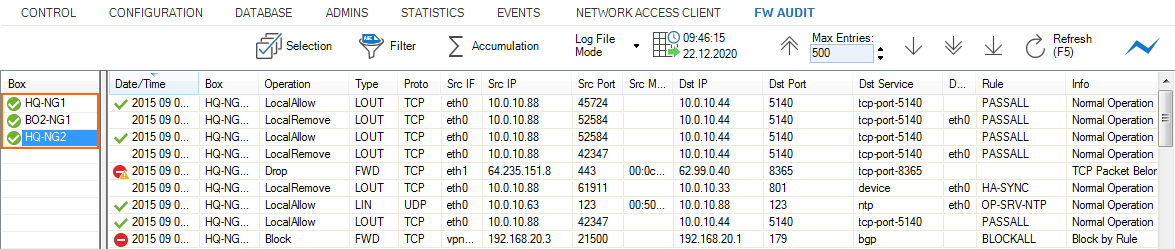
FW audit is a strictly chronological log of all sessions and events on your Barracuda CloudGen Firewall. Information written to this log may contain the following:
- Traffic – Forward, Local In, Local Out, and Loopback traffic
- Events – Allowed, Blocked, Dropped, Failed, and Removed events
- ARP
- IPS Hits
This data can be stored and viewed locally and/or centrally on the Barracuda Firewall Control Center depending on the audit delivery method configured on your firewall:
- Local-DB – Store audit log data locally in a database.
- Forward-Only – Forward audit logs to an Audit Collector service on the Control Center.
- Local-DB-And-Forward (default) – Store data in a local database and simultaneously send it to the Control Center.
- Send-IPFIX – Send audit logs via IPFIX exporter.
- Forward-and-Send-IPFIX – Forward audit logs to the Control Center and simultaneously send them via IPFIX exporter.
- Regular-Log-File – Write audit log to an ASCII log file.
- Syslog-Proxy – Generate syslog messages.
- Executable – Feed into a custom executable via STDIN.
- Send-UDP-Packet – Send a plain UDP stream.
Audit log viewers on both the firewall and Control Center allow you to view the collected data either as plain log files in Log File mode, or similar to the Firewall Live view in Accumulated Event view.
Limitations
- IPS Port scan information displayed on the Firewall > Threat Scan page are not included in the Audit logs.
- Keep in mind that the Control Center must receive and write data from a large number of firewalls, each of which may be capable of handling thousands of sessions. Accessing or writing FW Audit large data sets in the relational database is very CPU- and IO-intensive. Make use of the granular configuration options to limit the amount of data included in the audit log.
- The FW Audit Log Service does not synchronize Audit data within an HA cluster. For the CC Audit Info viewer and for the FW Audit Info collector, the service may run on the backup box to collect new data. In case of a failover to the backup box, new Audit data is stored on the backup box, and querying of this data needs to be performed on the backup box.
Step 1. Enable FW Audit on CloudGen Firewall
You must enable the audit log and choose where it is sent and/or stored. Repeat these steps for every firewall that should send audit logs to the Control Center.
- Go to YOUR CloudGen Firewall > Infrastructure Services > General Firewall Configuration.
- In the Configuration Mode section of the left menu, click Switch to Advanced View.
- In the left menu, click Audit and Reporting.
- Click Lock.
In the Log Policy section, click Edit next to Audit Log Data. The Audit Log Data window opens.
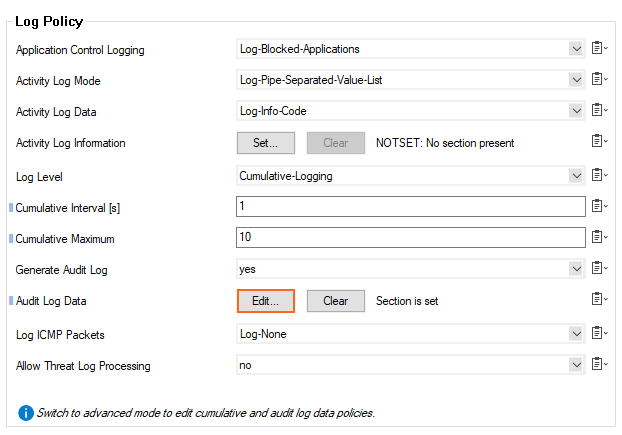
- Select the Audit Delivery method. E.g., Local-DB-And-Forward to send audit log to an Control Center while also storing them locally.
- Depending on the delivery method, you may have to configure additional settings.
For the default Local-DB-And-Forward and Forward-Only delivery methods, configure the following:- Send to IP Address – Enter the IP address of the Control Center.
- Sent to Port – Enter
680. This is the listening port of the CC Audit Service on the Control Center.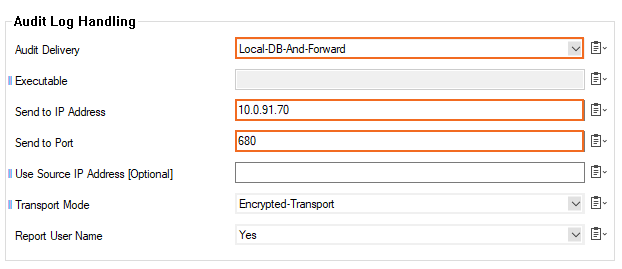
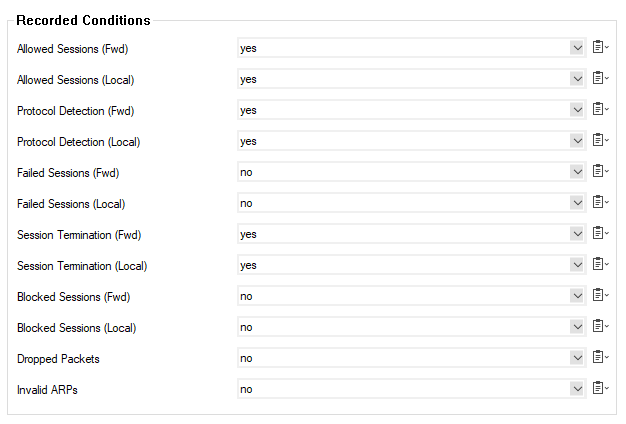
- In the Recorded Conditions section, select the type of data is included in the audit log.
- In the Log File Rotation and Removal section, configure the retention period of the audit logs (default: 3 days).
- Click OK.
- Click Send Changes and Activate.
Step 2. Create CC Audit Service on the Control Center
- Log into the box level of your Control Center.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services.
- Right-click on Assigned Services and click Create Service. The Wizard window opens.
- Enter the Service Name.
- Select CC FW Audit Log Service from the Software Module list.
- Click Finish.
- Click Activate.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > CC-Audit-Service > Central Firewall Audit.
- Click Lock.
- (optional) To receive audit logs from unmanaged firewalls, add the public keys of the box certificate to the Explicit Box Keys list.
- (optional) For large deployments, select Multiple Box Handler from the Box Handler Method drop-down list.
- Click Send Changes and Activate.
The Control Center will now receive and store all audit log data sent by firewalls using the Forward-Only and Local-DB-And-Forward delivery methods.
Local FW Audit Viewer on the CloudGen Firewall
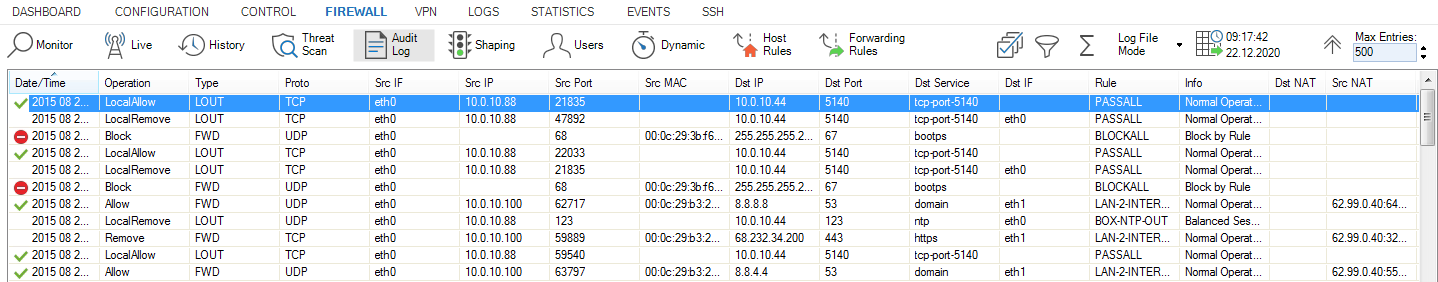
To view the audit log directly on the firewall, you must use the Local-DB delivery method. Go to FIREWALL > Audit Log to view the audit log. For more information, see Audit Log Page.
FW Audit Info Viewer on the Control Center
To view audit log data on the Control Center, you must use the Forward-Only or Local-DB-And-Forward delivery methods. Only selected firewalls (green check mark) are included in the FW Audit log viewer. In the left menu, double-click on the CloudGen Firewall to add the units audit log to the viewer. For more information, see CC FWAUDIT Tab.