To authenticate users connected to Aerohive access points, you must stream the syslog containing the authentication data to the Barracuda CloudGen Firewall F-Series.
Reference Devices/Versions:
- Aerohive AP230 802.11ac Wireless AP Version 6.4r1a
- Aerohive Networks HiveManager Online 6.4r1
Step 1. Enable Syslog Streaming on the Aerohive AP
- Log into the Aerohive Networks HiveManager.
- Go to Configuration > Advanced Configuration > Management Services > Syslog Assignments.
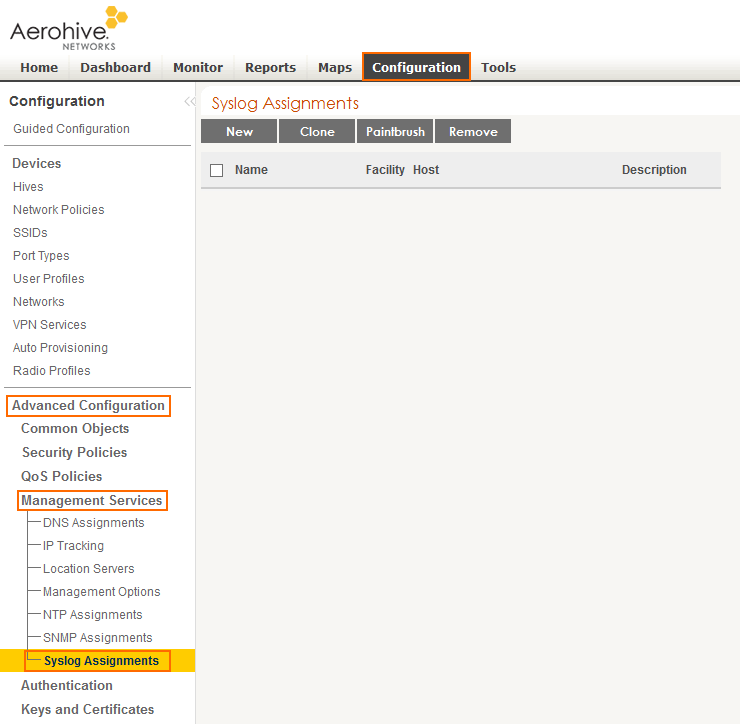
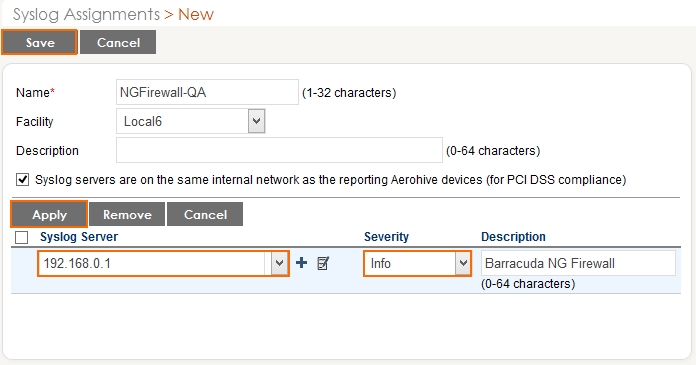
- Click New and configure syslog streaming:
- Syslog Server – Select the IP address of the firewall from the drop down.
- Severity – Select Info from the drop down.
- Click Apply.
- Click Save.
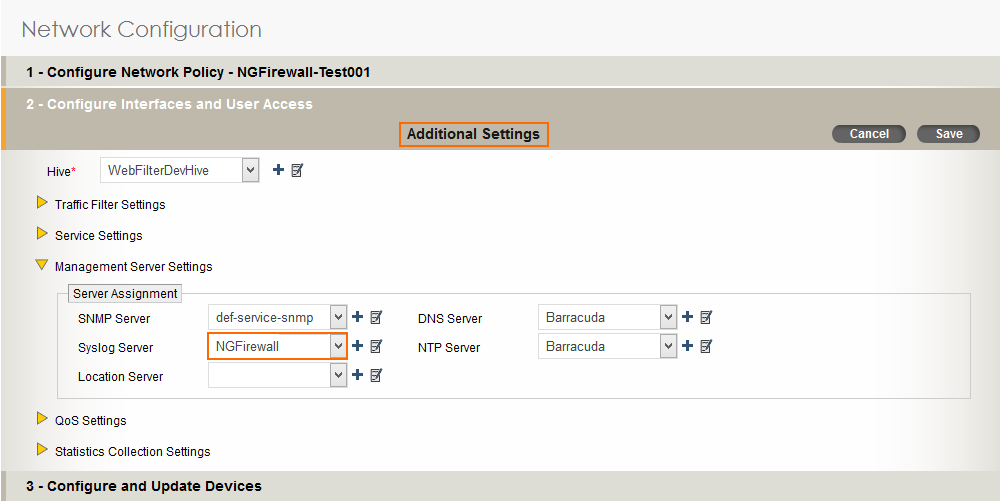
Step 2. Add Syslog Configuration to Network Policy on the Aerohive AP
Add the syslog configuration to the Network Policy you are using for your access points.
Step 3. Create a Service Object for TCP 514 in Host Firewall
Create a service object for TCP 514. Do not use the RCMD service object, as the rsh firewall plugin.
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Host Firewall Rules.
- Click Lock
- In the left menu click Services.
- Right-click the table and select New. The Edit/Create Service Object window opens.
- Enter a Name.
- Click New Object . The Service Entry Parameters window opens.
- IP Protocol – Select 006 TCP.
- Port Range – Enter
514.
- IP Protocol – Select 006 TCP.
- Click OK.
- Click New Object . The Service Entry Parameters window opens.
- IP Protocol – Select 017 UDP.
- Port Range – Enter
514.
- IP Protocol – Select 017 UDP.
- Click OK.
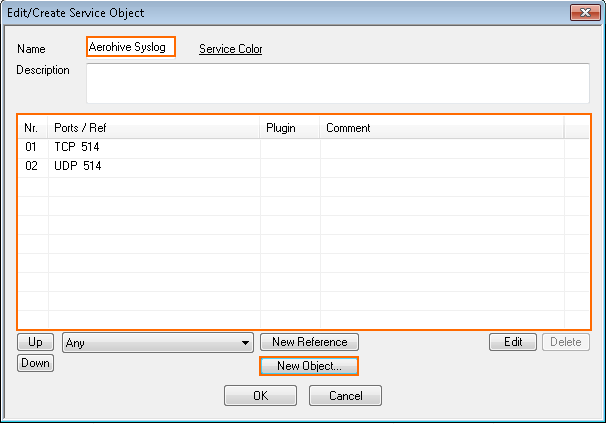
- Click OK.
- Click Send Changes and Activate.
Step 4. Create a Host Firewall Rule
Create a host firewall rule that matches incoming TCP/UDP 514 traffic without using the rsh firewall plugin.
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Host Firewall Rules.
- Click Lock.
- Either click the plus icon (+) at the top right of the rule set, or right-click the rule set and select New > Rule.
- Select Pass as the action.
- Enter a name for the rule. For example,
LAN-DMZ. - Specify the following settings that must be matched by the traffic to be handled by the access rule:
- Source – The source addresses of the traffic.
- Destination – The destination addresses of the traffic.
- Service – Select a service object, or select Any for this rule to match for all services.
- Click OK.
- Drag and drop the access rule so that it is the first rule that matches the traffic that you want it to forward. Ensure that the rule is located above the BLOCKALL rule; rules located below the BLOCKALL rule are never executed.
- Click Send Changes and Activate.
Verify that the Firewall is Receiving the Syslog Data
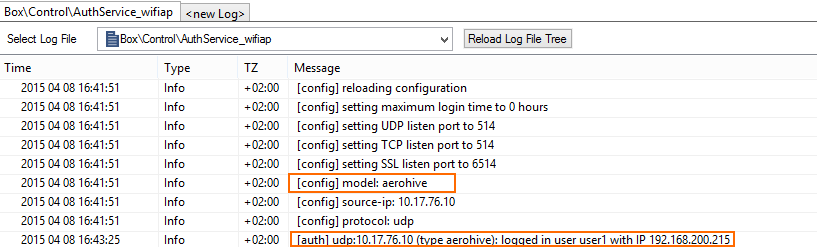
On the Barracuda CloudGen Firewall F-Series, go to LOGS and open the Box > Control > Serviceable_wifiap.log . After a successful authentication, you will see a logged in user <username> with IP <IP address> line in the log. The Wi-Fi access point name is also listed.