The steps below outline integration between AWS CloudTrail and XDR Monitoring. AWS CloudTrail service helps monitor governances, compliance, and operational and risk auditing of AWS accounts. Customers who are looking to monitor their AWS environment should follow the implementation instructions listed below to enable XDR to monitor their AWS environment in real time.
To integrate AWS Cloudtrail
- If your Trail isn't set up, follow this link to set up a trail within cloudtrail: https://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-create-a-trail-using-the-console-first-time.htm
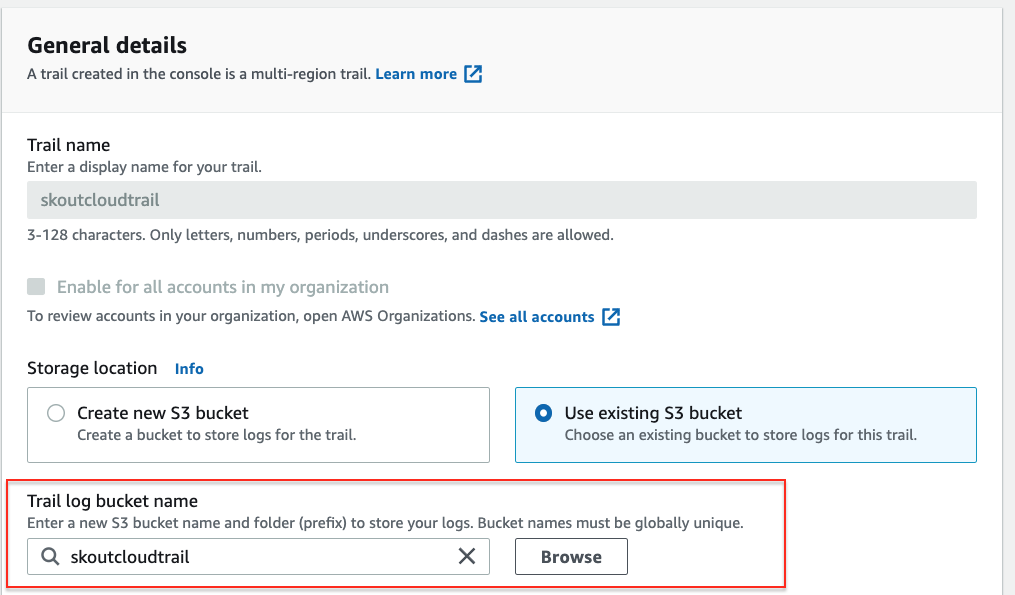
- Ensure the trail is logging to a S3 Bucket. If you edit the trail, you can see the name of the bucket it's writing log files to. Take note of the S3 Bucket Name:
- Set up an SQS Queue and use this template for its access policy:
Replace with the ARN of the SQS queue you just made
Replace with the name of the S3 Bucket that your CloudTrail is writing logs to
Afterwards hit save and then take note of the URL of the SQS Queue{"Version": "2012-10-17","Id": "__default_policy_ID","Statement": [{"Sid": "__owner_statement","Effect": "Allow","Principal": "*","Action": "SQS:*","Resource": "<SQS-queue-ARN>","Condition": {"ArnLike": {"aws:SourceArn": "arn:aws:s3:*:*:<bucket-name>"}}}]}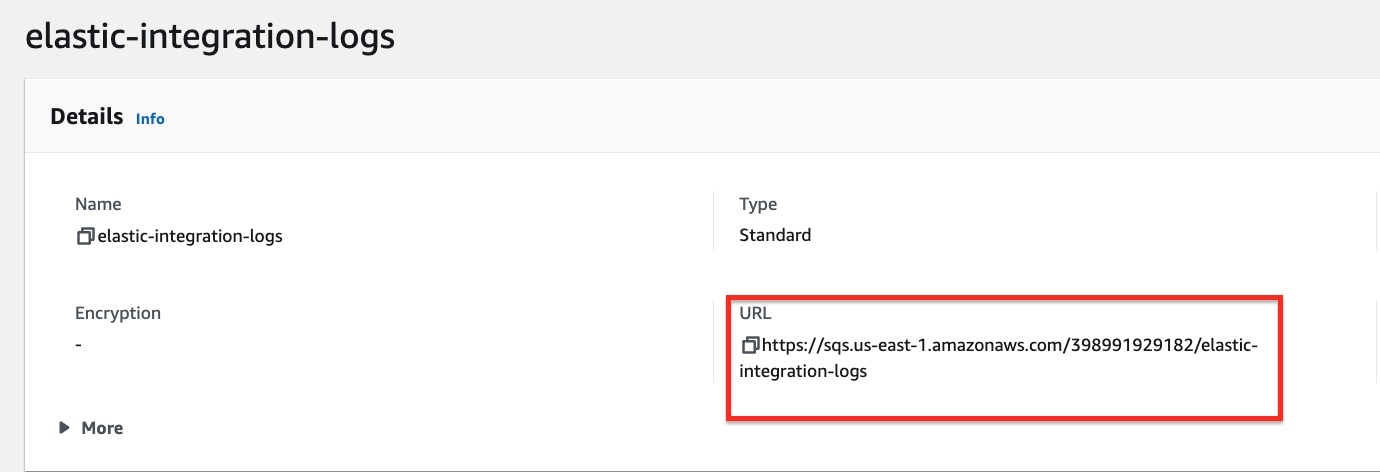
- Navigate to the S3 Bucket that your cloudtrail is writing logs to.
Click Properties > Scroll down to Event Notifications and click Create event notification.
Type a name for the event name.
In Event Types, select everything to monitor all Cloudtrail updates.
For the Destination, enter the SQS queue you made.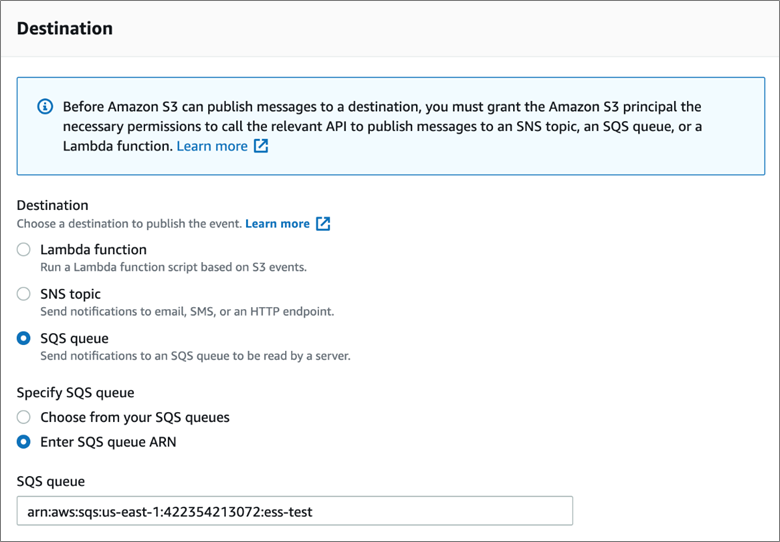
- For XDR to receive AWS SQS messages, an access key id and secret access key will need to be generated. A user permissioned in IAM with a role only allowed to read access from SQS queues:
- Setting up a new user in IAM – https://docs.aws.amazon.com/AWSSimpleQueueService/latest/SQSDeveloperGuide/sqs-setting-up.html
- SQS IAM permissioning JSON’s (Only need the SQS Send Message permission, first example) –https://docs.aws.amazon.com/AWSSimpleQueueService/latest/SQSDeveloperGuide/sqs-basic-examples-of-sqs-policies.html
- Once completed, provide XDR the following information -
- Queue Url: https://sqs.us-east-1.amazonaws.com/123/test-queue
- Access key id
- Secret Access Key
