The following sections provide additional details on the client-to-site VPN server parameter settings.
Group Policy Tab
The VPN Group Policy specifies the network IPsec settings. You can group patterns to require users to meet certain criteria, as provided by the group membership of the external authentication server (e.g., CN=vpnusers*). You can also define conditions to be met by the certificate (e.g., O (Organization) must be the company name).
Setting | Description |
Mandatory Client Credentials | Select the credentials required for client authentication:
Select Login must match AltName in Certificate if certificate lookup is done by Alternative Name. |
Primary Authentication Scheme | Select an authentication scheme from the list to be used by all client-to-site VPN connections. |
Default Authentication Scheme | The default or fallback authentication scheme used to authenticate VPN clients. Select the Ras Login permission required check box if Remote Access login is required. As soon as Ras Login permission required is activated, only an MSAD user with this option can connect. Users in other authentication databases, for example, LDAP, do not have this option as default and will not be able to connect. As a workaround, the user can be assigned a Boolean attribute with the name msNPAllowDialin in the directory. The VPN server itself does not distinguish between directories when querying. |
Secondary Authentication Scheme | When using multi-factor authentication, select the secondary authentication scheme from the list. This feature requires an Advanced Remote Access subscription. |
Enable SAML support | Allows VPN clients to connect using the SAML authentication. Note that this option requires a valid SAML configuration in the Authentication Service. |
Ras Login permission required | Select this option if you want to enforce that only users with a RAS permission are allowed to be authenticated. |
Server Certificate | (Optional) Select the server certificate used by the VPN server to authenticate to the VPN client, or use the default server certificate configured in the VPN settings. |
Server Protocol Key | Select your X.509 server certificate. |
Used Root Certificate | (Optional) Select the root certificate used to validate client certificates. |
X509 Login Extraction Field | Extract the username from the selected client certificate field. The X.509 Login Extraction Field is only used for pre-authentication. |
IP Attribute Name | Set the VPN client IP address to the attribute configured in the LDAP, MSAD, or RADIUS server. |
VPN Group Policy Name Attribute | Name of the attribute field on the authentication server that contains group information. The VPN group policy is pinned to the value returned by the LDAP, MSAD, or RADIUS server. |
Preauthentication Scheme | Attributes from LDAP, MSAD, or TACACS+ authentication schemes are used to determine the default authentication scheme for the user. As soon as only a username is used, the configured default authentication scheme will be used. The username must also exist in LDAP (or the corresponding authentication scheme) or the option Alternative Login Name Field must be used.
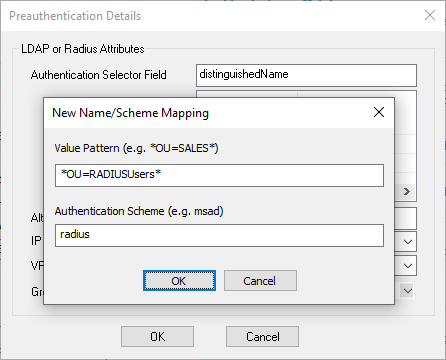
|
Group Policy Settings
Common Settings
Setting | Description |
Name | Enter a name for the policy. For example,
|
Statistic Name | Enter a name to better allocate statistics entries. |
Network | Select the VPN client network the group policy applies to. |
DNS | Enter the IP address of the DNS server used for the clients. |
WINS | If applicable, enter the IP address of the WINS server. |
Network Routes | Add all networks that should be reachable by the VPN clients. Enter |
Access Control List (ACL) | Add an Access Control List. |
Group Policy Condition | Right-click the Group Policy Condition field and select Create New Policy. |
Group Policy Condition
Right-click the Group Policy Condition field and select New Rule. In the X509 Certificate Conditions section of the Group Policy Condition window, set filters for the certificate. For each certificate condition, select the certificate field from the drop-down list, enter the required value, and click Add/Change.
Setting | Description |
External Group | Define the groups on the authentication server that will be assigned the policy. E.g., |
Client | Enter the IP address of the client network. |
X509 Subject | To let everyone with a valid certificate log on, click Edit/Show and add the following condition to the Subject field: |
Cert Policy / OID | (Optional) Enter an OID to allow only certificates with a specific key usage. E.g., Client Authentication (1.3.6.1.5.5.7.3.2) |
Peer | Enter the IP address of the peer network. |
Barracuda Tab - Barracuda Settings
IPsec IKEv1 Tab - IPsec IKE1 Phase II Settings
Setting | Description |
Disable | Clear the check box, and then select Group Policy Name (Create New). |
Edit Phase 1 | Click to edit the Phase 1 settings. |
Encryption | The data encryption algorithm. |
Hash Meth | The hash algorithm. |
DH-Group | The Diffie-Hellman Group that specifies the type of key exchange. DH Group1 to Group18 are supported. |
Time | The re-keying time in seconds that the server offers to the partner. |
Minimum | The minimum re-keying time in seconds that the server accepts from its partner. |
Maximum | The maximum re-keying time in seconds that the server accepts from its partner. |
IPsec IKEv2 Tab - IPsec IKE1 Phase I Settings
Configure the same settings for IPsec Phase I that you selected for IPsec Phase II.
Rules Tab
The Rules tab lets you edit the group VPN settings. For parameters, see the Group Policy Tab section above. To create a rule, right-click in the window and select New Rule.
Setting | Description |
Assigned VPN Group | Select the VPN group the rule should apply to. |
Group Pattern | Enter the group pattern, or click Lookup to perform an AD lookup and search for the group pattern. |
Use One-Time Password | Select the check box to enable one-time password authentication for users in the VPN group. |
Subject | Click Edit/Show to open the Certificate Condition window. Configuration may contain patterns (*,?). Equal keys are slash delimited: To match for DC=foo, DC=bar, you have to enter DC=bar/foo. The order of the distinguished name parts is reversed. |
Certificate Policy | Enter the certificate policy (OID 2.5.29.32). It will be checked if the transmitted certificate contains the certificate policies extension (OID 2.5.29.32) and if one of the contained values matches the configuration. For more information, see http://oid-info.com/get/2.5.29.32. |
Generic v3 OID / Content | Enter an OID to allow only certificates with a specific key usage. E.g., Client Authentication (1.3.6.1.5.5.7.3.2). You can enter an OID of an arbitrary X.509 v3 extension that will then be searched in the extensions of the transmitted certificate and checked against the value configured in the Content field. V_ASN1_IA5STRING and V_ASN1_OCTET_STRING entries can be entered as value, entries of another type will be configured as hexadecimal DER-encoded chain: e.g., for presence of the attribute |
Peer Condition | Select the check boxes for the client types used by the peer.
|
Peer Address/Network | Click Add to add the IP address of the peer network. |
Common Tab
See Common Settings section above.
Barracuda Tab
Setting | Description |
Name | Enter a name for the Barracuda Client connection. |
Enable VPN Client NAC | Enables the Barracuda Network Access Client. For more information, see Barracuda Network Access and VPN Client. |
ENA | Possible values are:
|
VPN Rules | Assigns an online ruleset configured in the VPN FW tab. |
Offline Rules | Assigns an offline ruleset configured in the Offline FW tab. |
Message | Welcome messages can be used to display customized messages to welcome users to the corporate network, inform them about security policies, or display administrator contact details. Create a custom welcome message in the Message tab of the Client to Site page, and then select the message in this section. |
Bitmap | Upload a 150x80 pixel, 256 color BMP bitmap in the Pictures tab of the Client-to-Site page, and then select the custom bitmap in this section. |
Firewall Always ON | The Network Access Client needs to be installed with Firewall Always ON enabled to allow VPN connections. |
VPN Always ON | If enabled, users cannot disconnect manually from the VPN. |
Key Time Limit | The period of time after which the re-keying process is started. |
Key Traffic Limit | The keys of the VPN tunnel are renewed after this amount of traffic. |
Tunnel Probing | The interval between tunnel probes. If probes are not answered in the time period specified by the Tunnel Timeout setting, the tunnel is terminated. |
Tunnel Timeout | The length of time in which tunnel probes must be correctly answered before the tunnel is terminated. If, for some reason, the enveloping connection breaks down, the tunnel must be re-initialized. This is extremely important in setups with redundant possibilities to build the enveloping connection. |
Accepted Ciphers | The ciphers that can be used to establish the connection. |
Enforce Windows Security Settings | Enforce Windows security features:
|
Disk Encryption | If checked, a client will be able to connect only if he has disk encryption enabled. |
IPsec Tab
See IPsec IKEv1 Tab - IPsec IKE1 Phase II Settings section above.
