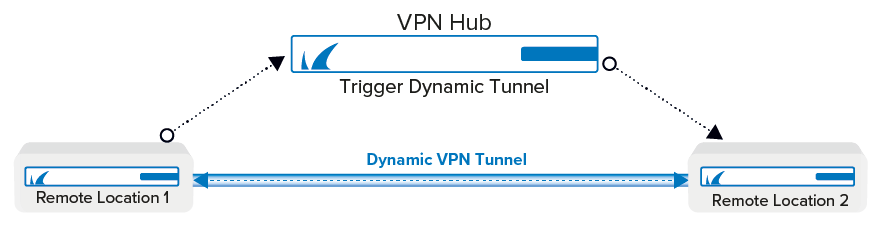
Create a Dynamic Mesh network for three or more stand-alone Barracuda CloudGen Firewalls with the central firewall acting as the VPN hub. Every firewall in the VPN Network must be configured to use Dynamic Mesh, and the VPN hub must be the SD-WAN primary and use a Dynamic Mesh-enabled connection object for the access rule matching the VPN relay traffic. Dynamic Mesh can only be used in combination with TINA Site-to-Site tunnels. The IPv6 envelope for the VPN tunnels is not supported.
Before You Begin
- Create IPv4 TINA VPN tunnels between all firewalls. For more information, see How to Create a TINA VPN Tunnel between CloudGen Firewalls.
- Create access rules for the VPN tunnels. For more information, see How to Create Access Rules for Site-to-Site VPN Access.
- Configure the CloudGen Firewall F acting as a VPN hub to forward VPN traffic from one remote firewall to the others.
Step 1. Enable Dynamic Mesh
Repeat this step on every firewall in the Dynamic Mesh VPN network.
- Open the VPN Settings page (CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service).
- Click Lock.
- In the TINA section, verify that Allow Dynamic Mesh is selected.
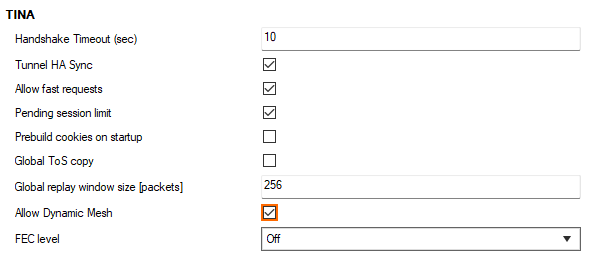
- Click OK.
- Click Send Changes and Activate.
Step 2. Enable Dynamic Mesh for the VPN Tunnels
For each TINA tunnel, edit the TINA VPN tunnel configuration on the VPN hub and the remote firewalls to use Dynamic Mesh.
- Open the Site to Site page (CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service).
- Click Lock.
- Double-click the Site-to-Site TINA tunnel. The TINA Tunnel window opens.
- Click on the Advanced tab.
- Enable Use Dynamic Mesh.
- (optional) Enter the Dynamic Mesh Timeout (s) in seconds. The timeout must be between 5 and 600 seconds.
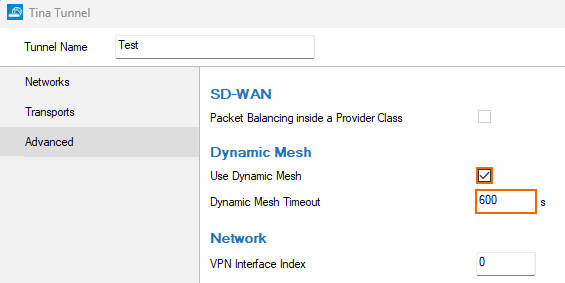
- Click OK.
- Click Send Changes and Activate.
Step 3. Create Three Custom Connection Objects on the VPN Hub
You must create three custom connection objects on the VPN hub: one that triggers a dynamic tunnel and resets the tunnel timeout, one for traffic going through the dynamic tunnel while not resetting the tunnel timeout, and one for the traffic that should always be relayed through the VPN hub.
Step 3.1 Dynamic Mesh Connection Object SD-WAN Primary with Idle Timeout Reset
Only connections matching an access rule with the Dynamic Mesh and SD-WAN primary options enabled in the SD-WAN settings of the custom connection object on the VPN hub will trigger a new dynamic VPN tunnel. All other traffic will continue to go through the VPN hub. The connection objects on the remote units (SD-WAN secondaries) do not need to be enabled because they are learned automatically from the VPN hub acting as the SD-WAN primary. For traffic matching access rules using this connection object to keep the dynamic tunnel open, Prevent tunnel timeout must be enabled.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Connections.
- Right-click in the Connections and click New > Connection.
- Enter a Name. E.g.,
DynMeshNoSNAT Select Original Source IP.
- In the SD-WAN VPN Settings section, click Edit/Show. The SD-WAN Settings window opens.
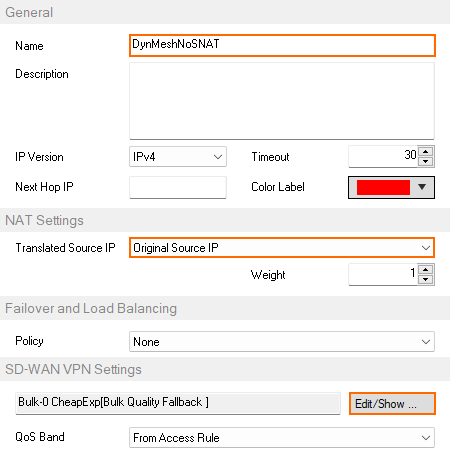
- Set the SD-WAN Learning Policy to Primary (propagate SD-WAN settings to partner).
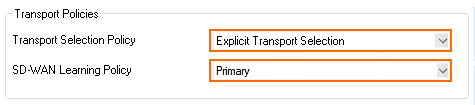
- In the Dynamic Mesh section, enable Allow Dynamic Mesh and Trigger Dynamic Mesh.
- Enable Prevent tunnel timeout.
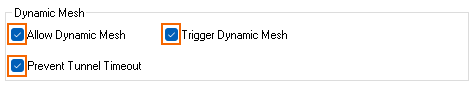
- Click OK.
- Click OK.
- Click Send Changes and Activate.
Step 3.2 Dynamic Mesh Connection Object SD-WAN Primary with no Idle Timeout Reset
Only connections matching an access rule with the Dynamic Mesh and SD-WAN primary options enabled in the SD-WAN settings of the custom connection object on the VPN hub will trigger a new dynamic VPN tunnel. All other traffic will continue to go through the VPN hub. The connection objects on the remote units (SD-WAN secondaries) do not need to be enabled because they are learned automatically from the VPN hub acting as the SD-WAN primary.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Connections.
- Right-click in the Connections and click New > Connection.
- Enter a Name. E.g.,
DynMeshNoTimeout Select Original Source IP.
- In the SD-WAN VPN Settings section, click Edit/Show. The SD-WAN Settings window opens.
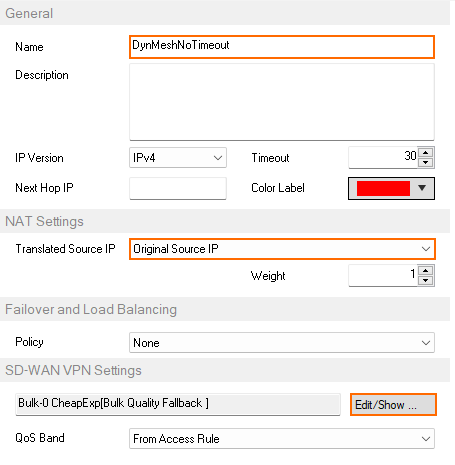
- Set the SD-WAN Learning Policy to Primary (propagate SD-WAN settings to partner).

- In the Dynamic Mesh section, enable Allow Dynamic Mesh.
- Disable Prevent tunnel timeout.
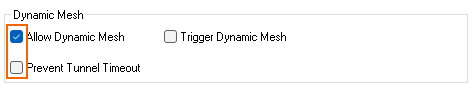
- Click OK.
- Click OK.
- Click Send Changes and Activate.
Step 3.3. Create an SD-WAN Primary Connection Object for the VPN Hub
For all services that should not go through the VPN tunnel, use a custom connection object with the SD-WAN Learning Policy set to Primary. Traffic matching an access rule that uses this connection object will not trigger a dynamic tunnel. Instead, it continues to go through the VPN hub.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Connections.
- Right-click in the Connections and click New > Connection.
- Enter a Name. E.g.,
TIPrimaryNoSNAT Select Original Source IP.
- In the SD-WAN VPN Settings section, click Edit/Show. The SD-WAN Settings window opens.
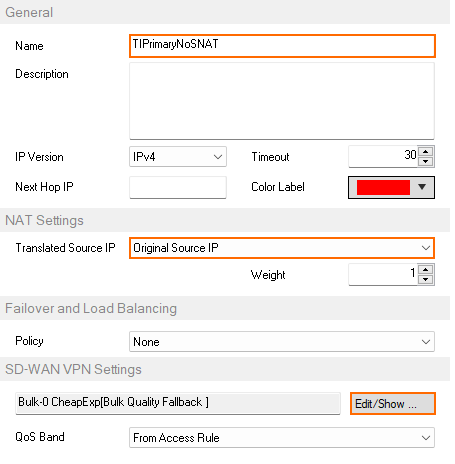
- Set the SD-WAN Learning Policy to Primary (propagate SD-WAN settings to partner).

- Verify that all checkboxes in the Dynamic Mesh section are cleared.
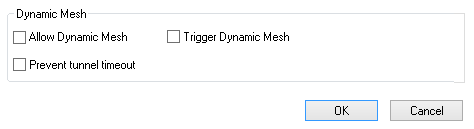
- Click OK.
- Click OK.
- Click Send Changes and Activate.
Step 4. Create Three Access Rules on the VPN Hub
Create an access rule that triggers the dynamic tunnel and another that relays the rest of the traffic.
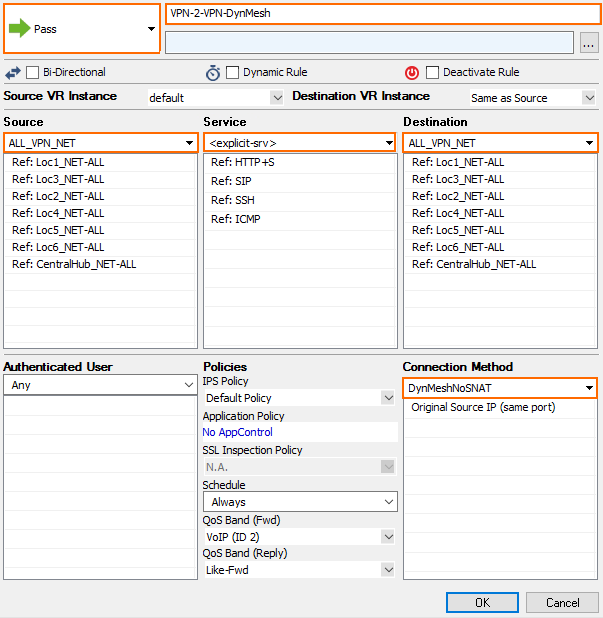
Step 4.1. Create an Access Rule on the VPN Hub to Trigger a Dynamic Tunnel
Create an access rule on the VPN hub that will trigger a dynamic tunnel.
- Action – Select PASS.
- Source – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Service – Select the services that should trigger a dynamic tunnel.
- Destination – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Connection Method – Select the DynMeshNoSNAT custom connection object created in Step 3.1.
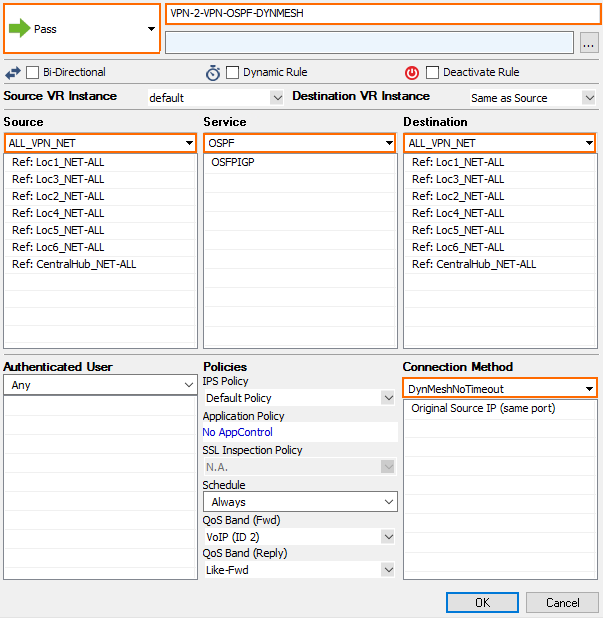
Step 4.2. Create an Access Rule on the VPN Hub to Trigger a Dynamic Tunnel without Resetting the Idle Timeout of the Dynamic Tunnel
Create an access rule on the VPN hub that will trigger a dynamic tunnel.
- Action – Select PASS.
- Source – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Service – Select the services that should go through the dynamic tunnel if it is up, otherwise go through the VPN Hub.
- Destination – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Connection Method – Select the DynMeshNoTimeout custom connection object created in Step 3.2.
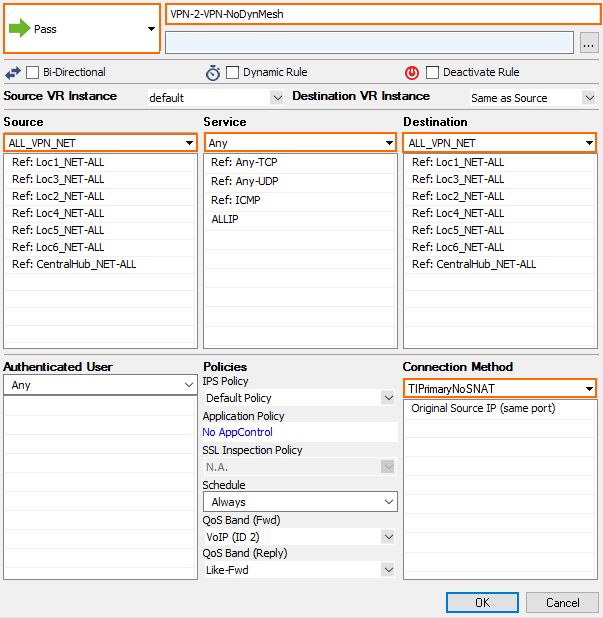
Step 4.3. VPN Relaying without Triggering a Dynamic Tunnel
Create an access rule on the VPN hub that allows the remote firewalls to send traffic to other remote firewalls through the VPN hub. Place this access rule below the rule triggering the dynamic tunnels.
- Action – Select PASS.
- Source – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Service – Select Any.
- Destination – Enter all Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Connection Method – Select the TIPrimaryNoSNAT custom connection object created in Step 3.3.
Step 5. Create Custom Connection Objects on the Remote Firewalls
On every remote firewall in the Dynamic Mesh VPN network, create an SD-WAN secondary connection object to allow the dynamic mesh.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- In the left menu, click Connections.
- Right-click in the Connections and click New > Connection.
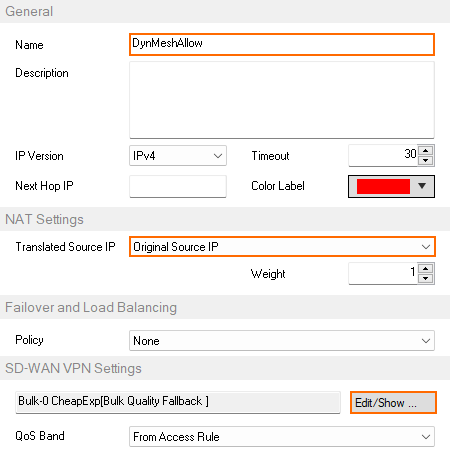
- Enter a Name. E.g.,
DynMeshAllow - Select Original Source IP.
- In the SD-WAN VPN Settings section, click Edit/Show. The SD-WAN Settings window opens.
- Set the SD-WAN Learning Policy to Secondary (learn SD-WAN settings from partner).
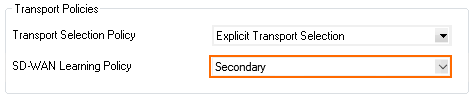
- In the Dynamic Mesh section, enable Allow Dynamic Mesh.

- Click OK.
- Click OK.
- Click Send Changes and Activate.
Step 6. Modify the VPN Access Rule on the Remote Firewalls
On every remote firewall, create or modify the access rule that allows traffic through the dynamic tunnel. Apply the connection object to allow the dynamic mesh.
- Action – Select PASS.
- Bi-Directional – Select the check box to apply the rule in both directions.
- Source – Enter all local networks used for the VPN tunnel.
- Service – Select the services that should go through the dynamic tunnel if it is up, otherwise go through the VPN hub.
- Destination – Enter the Local Networks for all remote firewalls and the Local Networks for the VPN hub.
- Connection Method – Select the DynMeshAllow custom connection object created in Step 5.
You now have a Dynamic Mesh VPN network that automatically creates dynamic VPN tunnels when traffic matches an access rule using a Dynamic Mesh-enabled connection object. Go to VPN > Site-to-Site to see all dynamic tunnels on the remote firewalls or on the VPN hub. Dynamic tunnels are terminated automatically after no traffic has passed through them for the Dynamic Mesh Timeout defined in the Site-to-Site configuration for each tunnel.
