To better organize the access rule set, you can create additional rule lists . At the point in the rule list where you want to evaluate another rule list create a Cascade access rule. If none of the rules in the additional rule list you cascaded to matched, create a Cascade Back access rule to continue evaluating the rules in the main rule list. If you do not define a Cascade-Back rule in the additional rule list and none of the rules match, the default policy (BLOCK or ALLOW) is executed at the end of the rule list.
Before you Begin
- Create one or more rule lists. For more information, see How to Create New Rule Lists.
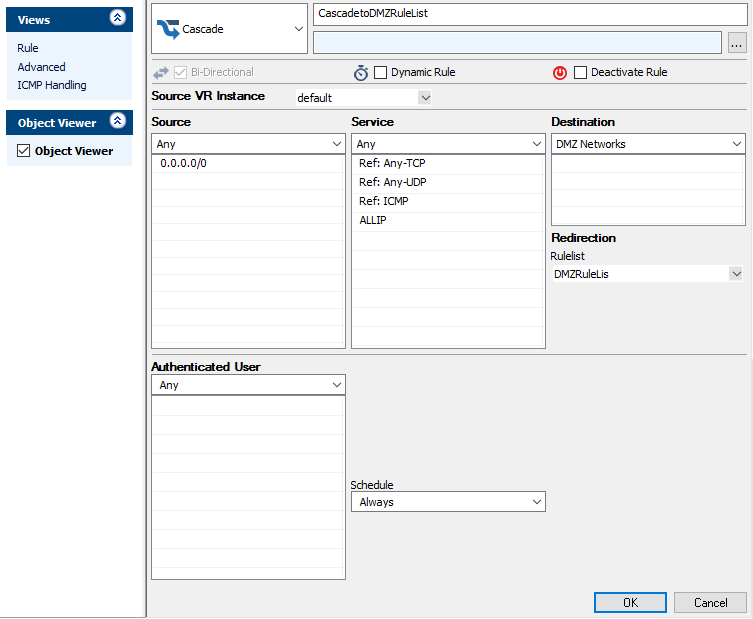
Create a Cascade Access Rule
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- Either click the plus icon (+) in the top right of the rule set, or right-click the rule set and select New > Rule.

- Select Cascade as the action.
- Enter a Name for the rule. For example,
CascadetoDMZRuleList. - Specify the following settings that must be matched by the traffic to be handled by the access rule:
- Source – The source addresses of the traffic.
- Destination – The destination addresses of the traffic.
- Service – Select a service object, or select Any for this rule to match for all services.
- Select the Rulelist that you want to also evaluate the traffic. E.g., DMZRuleList.
- Click OK.
- Drag and drop the access rule so that it is the first rule that matches the traffic that you want it to forward. Ensure that the rule is located above the BLOCKALL rule; rules located below the BLOCKALL rule are never executed.
- Click Send Changes and Activate.
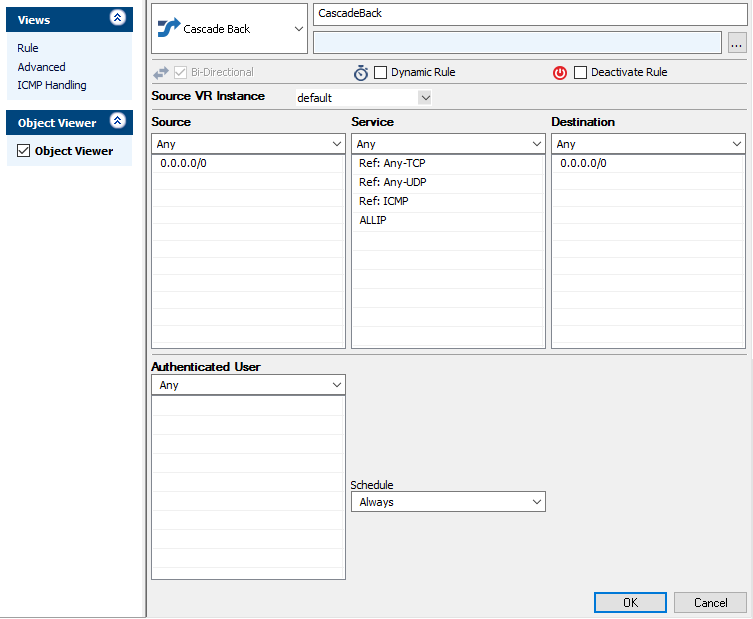
Create a Cascade Back Access Rule
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- Either click the plus icon ( + ) in the top right of the rule set, or right-click the rule set and select New > Rule .

- Select Cascade Back as the action.
- Enter a Name for the rule. For example,
CascadeBack. - Specify the following settings that must be matched by the traffic that will be handled by the access rule:
- Source – The source addresses of the traffic.
- Destination – The destination addresses of the traffic.
- Service – Select a service object, or select Any for this rule to match for all services.
- Click OK.
- Drag and drop the access rule to the order that you want. Usually this rule is placed last in the rule list, but you can drag it further up the rule list as well.
- Click Send Changes and Activate.
Additional Matching Criteria
- Authenticated User – For more information, see User Objects.
Additional Policies
- Time Objects – For more information, see Schedule Objects.
