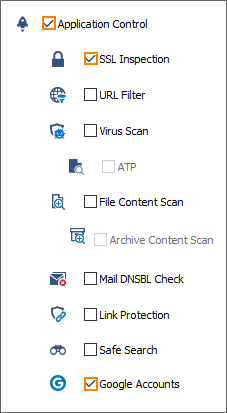
The CloudGen Firewall can filter traffic to Google services based on the domain attached to the Google Workplace account. This allows you to block access to personal Google accounts and other non-allow-listed Google Workplace accounts, while still allowing your allow-listed Google Workplace domains. Google accounts are enforced on a per-access-rule basis. Since Google requires HTTPS for almost all services, TLS Inspection is required. Google Chrome uses the QUIC protocol by default to communicate with Google servers. To force Chrome to use the HTTPS fallback, you must block QUIC traffic.
Before You Begin
- The Feature Level of the Forwarding Firewall must be 7.2 or higher.
- Enable Application Control. For more information, see How to Enable Application Control.
- Enable TLS Inspection. For more information, see How to Configure Outbound TLS Inspection.
Step 1. Add Your Domains to the Google Domain Allow List
Google accounts using the domains in the allow-list will be exempted from filtering when a Google-account-enabled access rule matches.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Security Policy.
- Click Lock.
- In the Google Personal Accounts section, click + to add domains to the Domain Allow List.
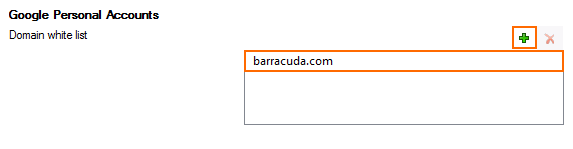
- Click Send Changes and Activate.
Step 2. Create an Access Rule to Block Non-Allow-Listed Google Accounts
You can block Google accounts not on the allow-list for all web traffic that matches an access rule by enabling Google Accounts in the Application Control settings of the access rule.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- Either click the plus icon (+) at the top right of the ruleset, or right-click the ruleset and select New > Rule.

- Select Pass as the action.
- Enter a Name for the rule.
- Specify the following settings to match your web traffic:
- Source – The source addresses of the traffic.
- Service – Select HTTP+S.
- Destination – Select Internet.
- Connection Method – Select Dynamic NAT.
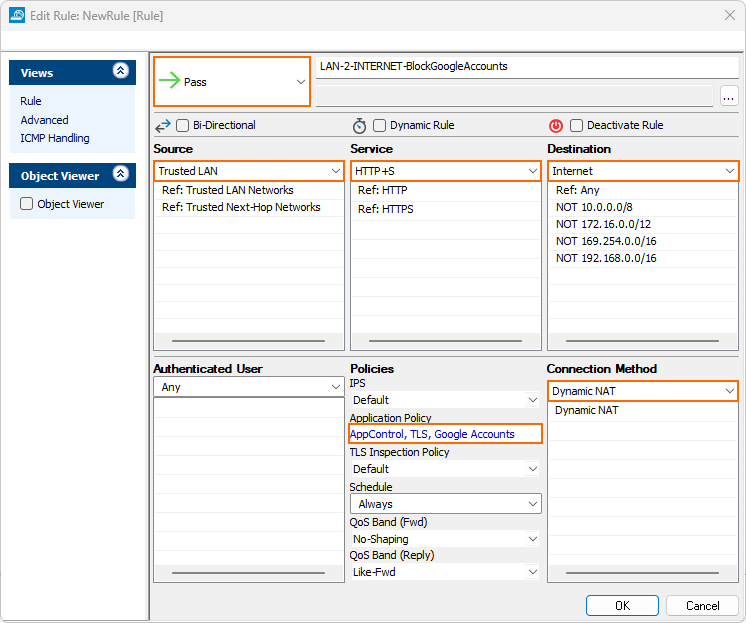
- Click on the Application Policy link and select:
- Application Control – Required.
- TLS Inspection – Required, since Google services are available exclusively via HTTPS.
- Google Accounts – Required.
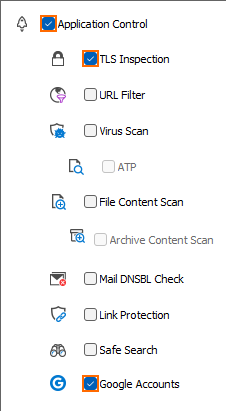
- Application Control – Required.
- Select a policy from the TLS Inspection Policy drop-down list.
- (optional) Set additional matching criteria:
- Authenticated User – For more information, see User Objects.
- Schedule Object – For more information, see Schedule Objects.
- Click OK.
- Place the access rule via drag-and-drop in the ruleset, so that no access rule above it matches this traffic.
- Click Send Changes and Activate.
Step 3. Block QUIC for Google Chrome Browsers
To force Google Chrome browsers to use HTTPS instead of QUIC on UDP port 443, you must create a BLOCK access rule.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
- Click Lock.
- Either click the plus icon (+) at the top right of the ruleset, or right-click the ruleset and select New > Rule.

- Select Block as the action.
- Enter a Name for the rule.
- Specify the following settings to match your web traffic:
- Source – The source addresses of the traffic. Use the same source as the access rule in Step 2.
- Service – Create and select the service object for UDP 443. For more information, see Service Objects.
- Destination – Select Internet.
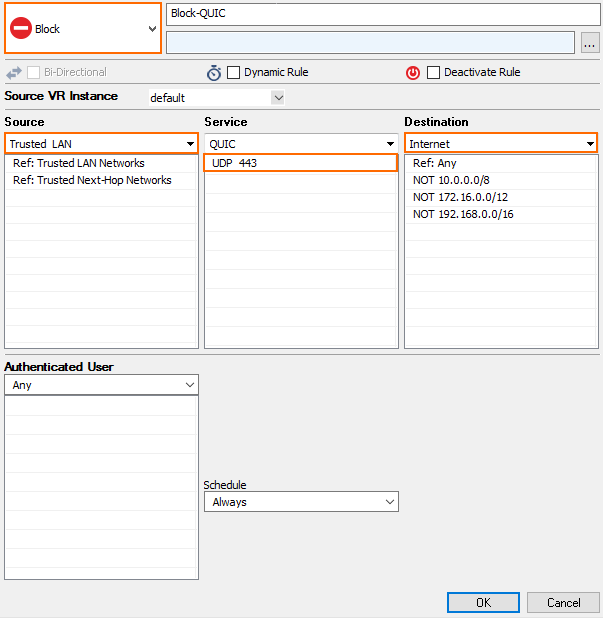
- (optional) Set additional matching criteria:
- Authenticated User – Use the same user object as in Step 2.
- Schedule Object – Use the same schedule object as in Step 2.
- Click OK.
- Place the access rule via drag-and-drop before the rule created in Step 2.
- Click Send Changes and Activate.
Web traffic matching this rule can now only access Google accounts for domains that are included in the allow-list. When users access a non-allow-listed domain, they are automatically redirected to a Google block page.