The features and controls of the configuration pages for the Host and Forwarding Firewall rulesets have a similar interface structure. The main rules section in these pages displays the access or application rules depending on the selected ruleset in the left menu. You can view, create, copy, paste, clone, and edit your access rules on this page.
The Forwarding Firewall Ruleset
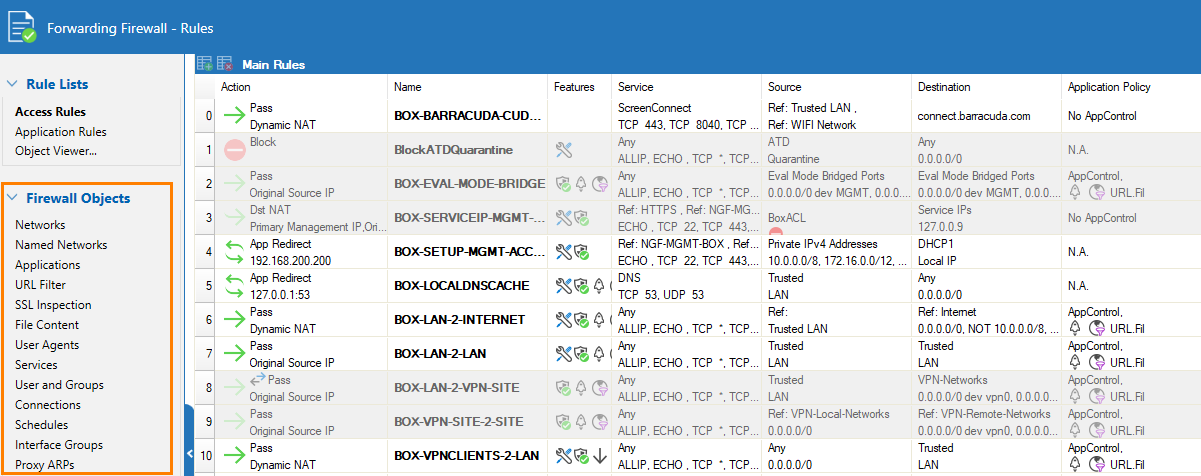
The Forwarding Firewall ruleset contains all forwarding access and application rules and provides access to the access and application rule configuration dialog. To open the Forwarding Firewall ruleset, go to CONFIGURATION > Configuration Tree > Box > Assigned Services > Firewall > Forwarding Rules.
The Forwarding Rules page is divided into the following sections:
Main Rules Table
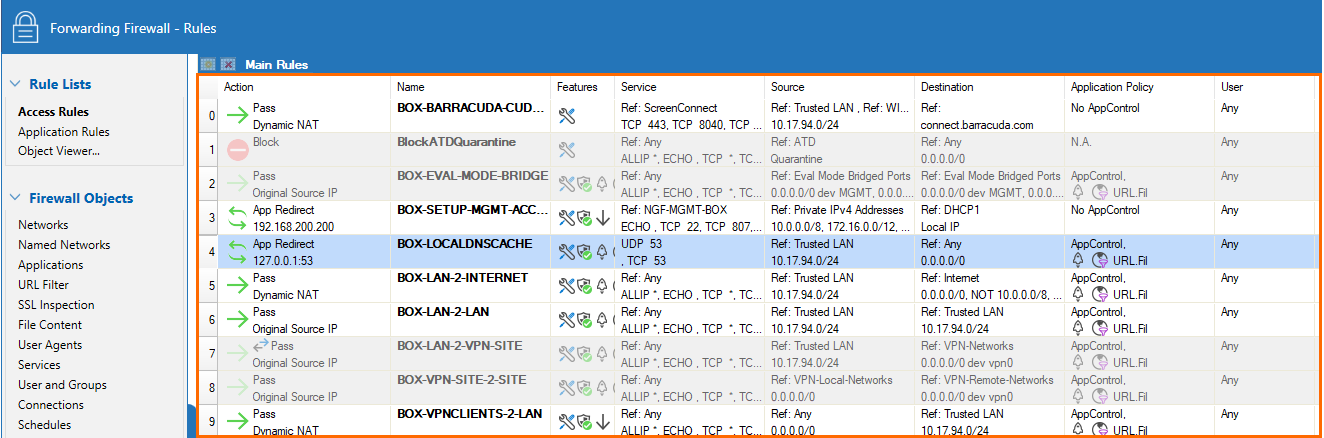
In the main rules table, you can view and edit the settings for your access or application rules. See below for icon descriptions.
Editing Features
Use these icons to create, edit, and otherwise manipulate the access or application rules in the main ruleset. See below for icon descriptions.
![]()
Rule Lists
This ruleset cannot be deleted, although additional rulesets can be created. See below for icon descriptions.
Main Rules Section and Icons
In the main rules table, the settings for each access rule are organized in the following columns:
| Column | Description | |
|---|---|---|
| Action | The action performed by the access rule. | |
| Name | The name of the access rule. | |
| Features | The features that have been applied to the access rule, as indicated by the following icons: | |
| Icon | Feature | |
 | Dynamic Rule | |
 | Advanced rule parameter changed | |
 | Rule matches for swapped source and destination | |
 | Scheduled Rule | |
 | Generic TCP Proxy | |
 | Original Source IP | |
 | Authenticated User | |
 | No IPS | |
 | Custom IPS Policy | |
 | Default IPS Policy | |
 | Legacy Layer 7 Application Control | |
 | Continue on Device Mismatch | |
 | Proxy ARP | |
 | No Application Control Scan | |
 | Application Control Scan without SSL Inspection | |
 | Application Control Scan with SSL Inspection | |
 | AV scan | |
| The following icons apply to application rules only: | ||
| Icon | Feature | |
 | Application Filter Object | |
 | Application Object | |
 | Custom Application | |
 | Overridden Application | |
 | Native Application | |
| Service | The service that applies to the access rule. For example, the IP protocol used or, with TCP/UDP, the relevant IP protocol and the port for the traffic. | |
| Source | The source addresses selected for the access rule. | |
| Destination | The destination addresses selected for the access rule. | |
| Application Policy | The application policies applied to the access rule. For more information, see Application Control. | |
| User | The users affected by the access rule. | |
| Schedule | Displays the times when the rule is applied. | |
| QoS | Any traffic shaping settings. For more information, see How to Create and Apply QoS Bands. | |
| IPS Policy | The IPS policy that is applied to the access rule. For more information, see Intrusion Prevention System (IPS). | |
| Usage | This column shows when the rule was last used and how often. E.g.: 5 days (1234) – The rule matched certain traffic 5 days ago and matched 1234 times total. The Usage field is only filled with information in the read-only version of the ruleset. Go to FIREWALL > Forwarding Rules. | |
Main Rules Tab
The Main Rules tab allows you to create additional rule lists.
Editing Features and Icons
The editing features section on the top right of the page provides the following keyboard shortcuts that let you perform different actions:
| Shortcuts | Description |
|---|---|
 | Show/hide inactive rules |
 | Show/select overlapping rules |
 | Move a rule down in the ruleset |
 | Move a rule up in the ruleset |
 | Delete a rule |
 | Edit a rule |
 | Add a new rule |
 | Add a new IPv6 rule |
 | Insert a new rule section |
 | Clone a rule |
Editing Multiple Access Rules
If you need to change the Application Control, IPS, or QoS settings for multiple access rules, you can use inline edit multiple access rules. Hold down the CTRL key and click the rules you want to edit. The following settings can be changed for all selected access rules by clicking the mouse-over edit icon ( ):
):
- Application Control
- IPS Policy
- QoS
To change the following properties via multi-edit, click the mouse-over ( ) settings icon in the Name column:
) settings icon in the Name column:
- Set color
- Deactivate or activate rules
- Dynamic rule
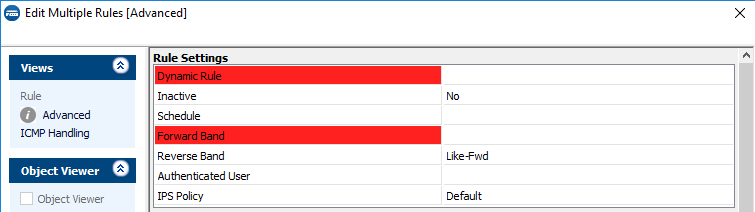
To change Advanced settings for multiple rules right-click the selected rules and click Edit. Entries highlighted in red differ between the selected rules.
NAT Information
Use the NAT Information view to display the access rules based on translated IP addresses. To access the NAT view, expand the 'modify view' icon and select Show NAT information.
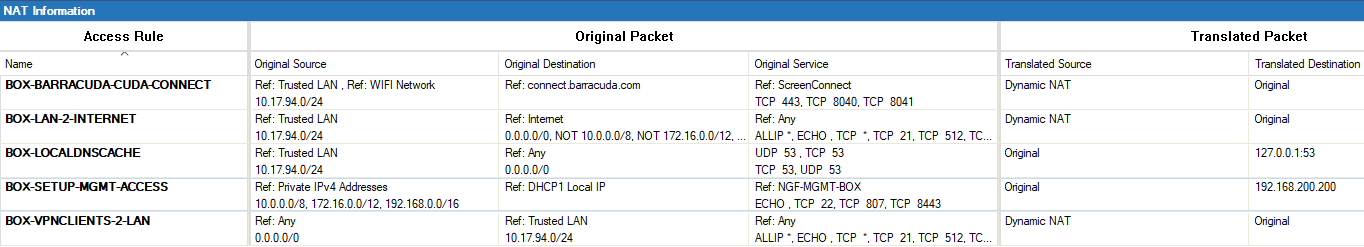
The NAT Information window displays the following details.
- Access Rule – This column lists all access rules with a connection method of source or destination NAT. To display or edit a rule from the NAT view, double-click it.
- Original Packet – The columns in this section display the original source, destination, and service object that apply to the access rule.
- Translated Packet – The columns in this section display the selected NAT method. This can be source NAT or destination NAT. This section also shows whether source or destination is translated and displays the translated IP address.
For more information on the functionalities of the Forwarding Firewall ruleset, see Forwarding Firewall.
Firewall Objects
Firewall objects are used to reference networks, services, applications, user groups, or connections in order to simplify the management and maintenance of rules and network setups. You can use predefined and custom objects when configuring routes, or when creating access- and application rules. For more information, see Firewall Objects.
Host Access Ruleset
You can view the host access ruleset on the Host Firewall - Rules page. To open this page, go to Config > Box > Infrastructure Services > Host access rules.
The Host Firewall - Rules page provides an interface very similar to the Forwarding Firewall and is divided into the following sections:
- Configuration Menu – The left navigation pane of the page provides you with menu sections to configure your access rules.
- Inbound and Outbound Table – In the table, you can view and edit the settings for all inbound and outbound host access rules. To switch between viewing the inbound and outbound rulesets, click the following tabs:
- Inbound – Shows all inbound host access rules.
- Inbound-User – (Bound to the Inbound set) Shows a subset of inbound host access rules.
- Outbound – Shows all outbound host access rules.
- Outbound-User tab – (Bound to the Outbound set) Shows a subset of outbound host access rules.
Main Rules Section and Icons
Below the Inbound and Outbound tabs, the settings for each access rule are organized into the following columns:
| Column | Description | |
|---|---|---|
| Action | The action performed by the access rule | |
| Name | The name of the access rule | |
| Features | The features that have been applied to the access rule, as indicated by the following icons: | |
| Icon | Description | |
 | No IPS | |
 | Original Source IP | |
 | Legacy Layer 7 Application Control | |
| Service | The service that applies to the access rule | |
| Source | The source selected for the access rule | |
| Destination | The destination selected for the access rule | |
| Comment | (Optional) Comment | |
| User | The users affected by the access rule | |
| QoS | Any traffic shaping settings. For more information, see How to Create and Apply QoS Bands. | |
| Schedule | Displays the times when the rule is applied. | |
| Usage | This column shows when the rule was last used and how often. E.g.: 5 days (1234) – The rule matched certain traffic 5 days ago and matched 1234 times total. The Usage field is only filled with information in the read-only version of the ruleset. Go to FIREWALL > Host Rules. | |
For more information on the functionalities of the host access ruleset, see Host Firewall.
Allowed Characters in the Firewall Ruleset
All text configuration elements in the firewall ruleset are restricted to use only the following characters, number and symbols:
- Letters - a-z, A-Z
- Numbers – 0-9
- Symbols – # \r \n . _ / : , ; * + -
