You can install the Barracuda CloudGen Firewall as a virtual machine in the Microsoft Azure public cloud. The Azure solution template deploys either a single firewall or a high availability cluster into a dedicated subnet of a new or existing virtual network. For more information on the deployment of a single firewall, see How to Deploy a CloudGen Firewall from the Microsoft Azure Marketplace. You can deploy a high availability cluster from the marketplace with Cloud Integration. In case of a failover, the Azure route table is rewritten to use the active firewall. Due to the limitation of Azure networking, all active sessions will time-out whenever a failover occurs. For more information on high availability and high availability in Azure, see High Availability and High Availability in Azure.
You can choose between the following images in the Azure Marketplace:
- Bring Your Own License (BYOL) – Uses licenses purchased directly from Barracuda Networks. Barracuda Networks offers a 30-day evaluation license.
- Pay As You Go (PAYG) – No dedicated licenses required. Licensing fees are included in the hourly price of the virtual machine. All charges are billed directly through your Microsoft Azure account.
Before You Begin
- Create a Microsoft Azure account.
- (BYOL images only) Purchase a Barracuda CloudGen Firewall or Control Center for Microsoft Azure license, or register to receive an evaluation license from the Barracuda Networks Evaluation page.
Deployment of the Firewall from Marketplace
Step 1. Basics
- Go to the Azure portal: https://portal.azure.com
- In the upper-left corner, click + Create a resource.
Search the Marketplace for
Barracuda CloudGen Firewall & SD-WAN for Azureand click Barracuda CloudGen Firewall & SD-WAN for Azure.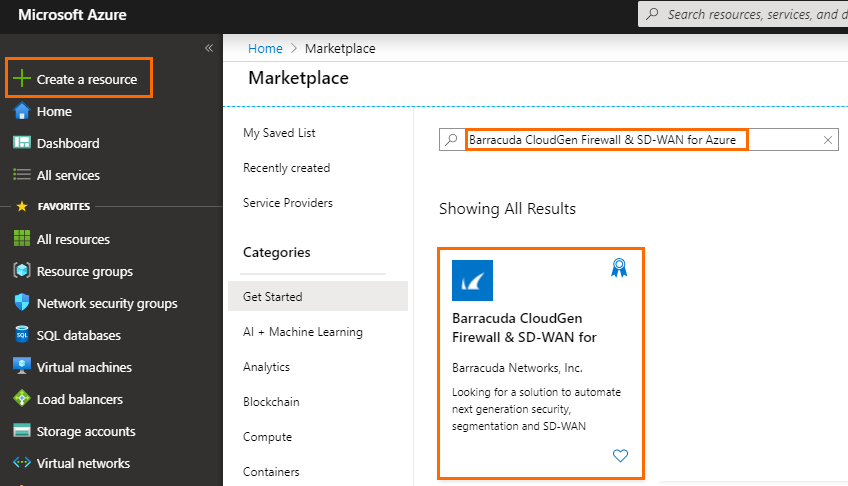
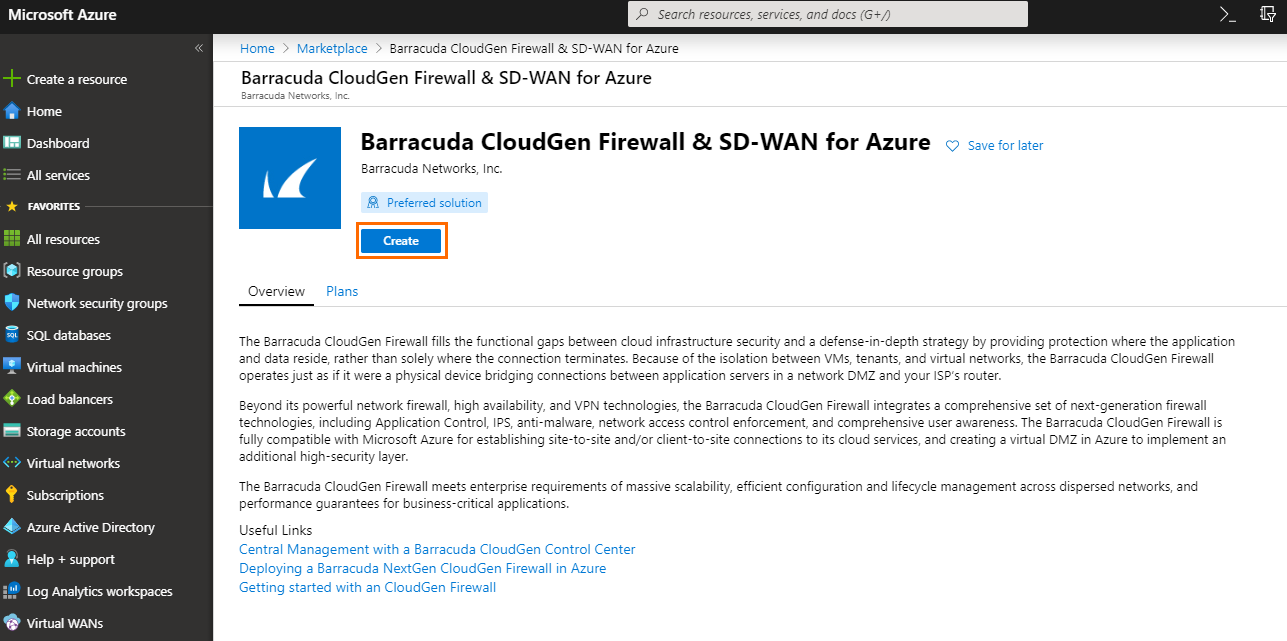
- In the next window, click Create.
- In the Basics blade, configure the following settings:
- Subscription – Select your subscription.
- Resource Group – Select an existing resource group to deploy to, or click Create new for a new resource group.
- Region – Select the desired location the firewall will be deployed to.
- Firewall Name – Enter the hostname for the CloudGen Firewall.
- License scheme – Select either PAYG or BYOL.
- Firmware version – Select one of the available firmware versions. Barracuda Networks recommends deploying the highest available version.
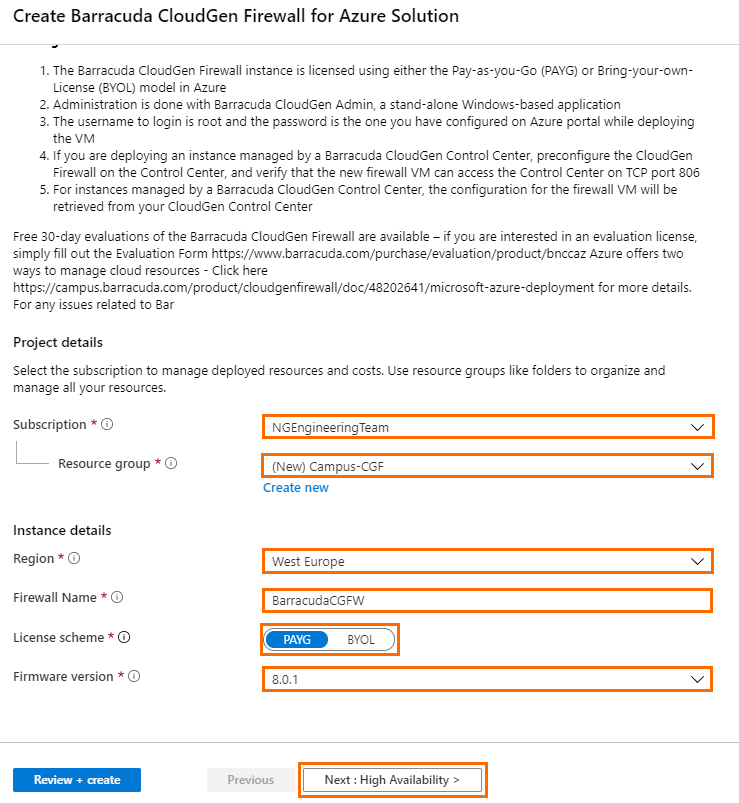
- Click Next : High Availability >.
Step 2. High Availability
In this blade, you can create either a high availability cluster or a single firewall.
- High availability mode – Select Active/passive HA cluster from the drop-down menu.
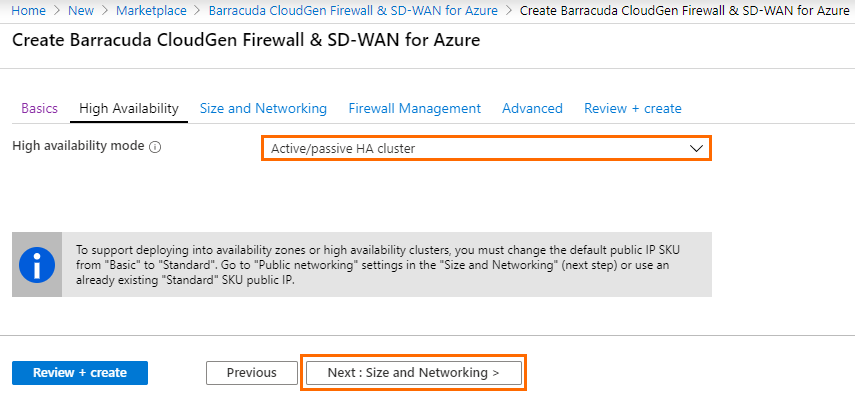
- Click Next : Size and Networking >.
Step 3. Size and Networking
- In the Size and Networking blade, configure the following settings:
Choose a firewall VM size – Select the size of the virtual machine.
- VM disk type – Select the disk type of your firewall virtual machine.
- Virtual network – Select an existing Virtual network , or create a new one.
- HA firewalls cluster subnet – Select an existing subnet, or create a new one. This subnet will host your firewalls. The firewalls must be placed in a different subnet than the protected instances.
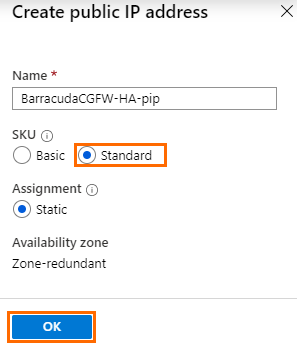
Primary firewall's public IP address name – Select an existing Public IP address, or create a new one.
To create a new public IP address, click Create new and select Standard SKU. Click OK.
- Primary firewall's domain name label – Enter a domain name for your primary firewall.
Secondary firewall's public IP address name – Select an existing Public IP address, or create a new one.
To create a new public IP address, click Create new and select Standard SKU. Click OK.
- Secondary firewall's domain name label – Enter a domain name for your secondary firewall.
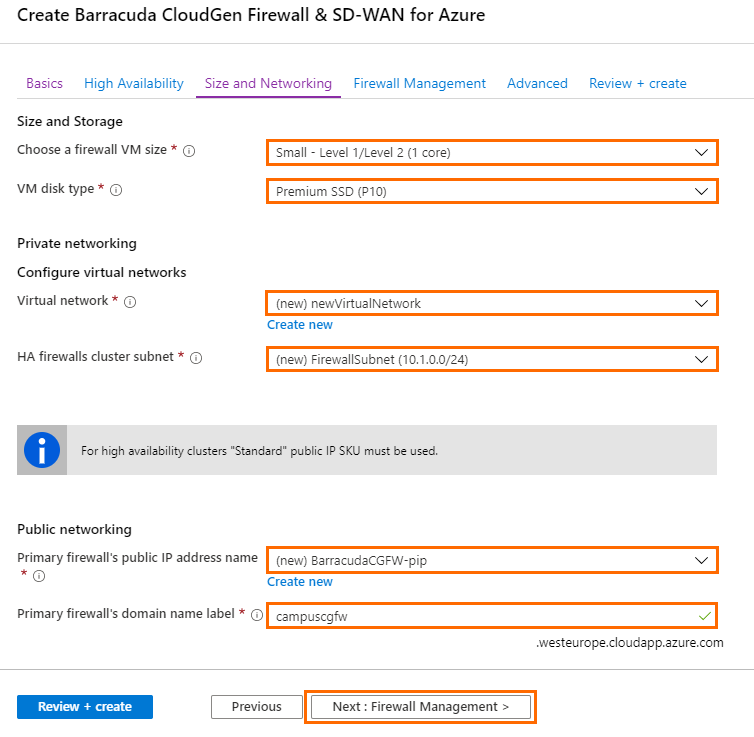
- Click Next : Firewall Management >.
Step 4. Firewall Management
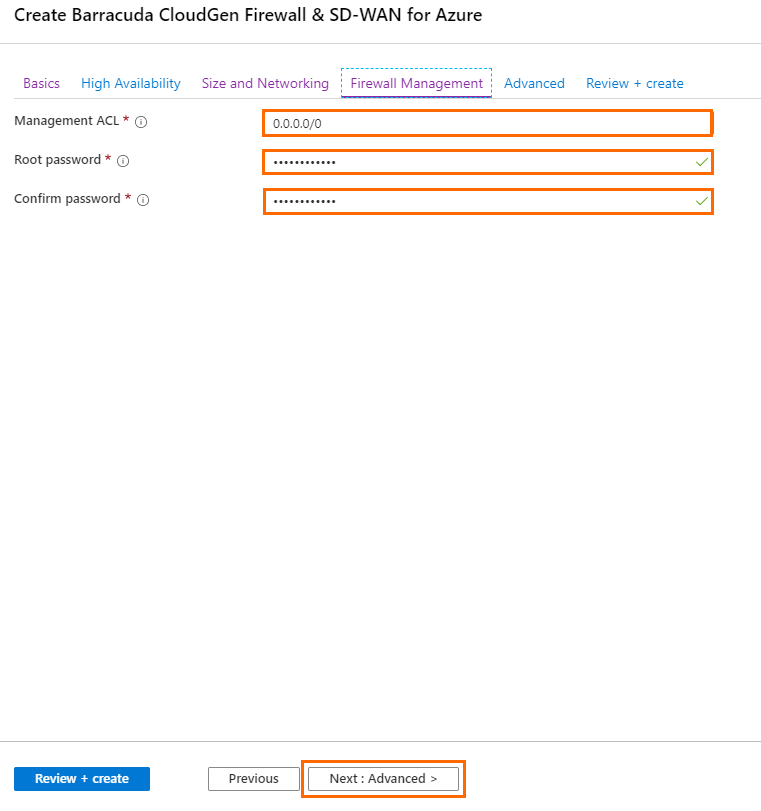
- In the Firewall Management blade, configure the following settings.
Management ACL – Introduces a network security group that restricts access to management ports of the firewall. Enter
0.0.0.0/0to allow access from any network and to skip creating a network security group.Root password – Enter the password for the root user of the firewall.
- Confirm password – Retype the password for the root user of the firewall.
- Click Next : Advanced >.
Step 5. Advanced
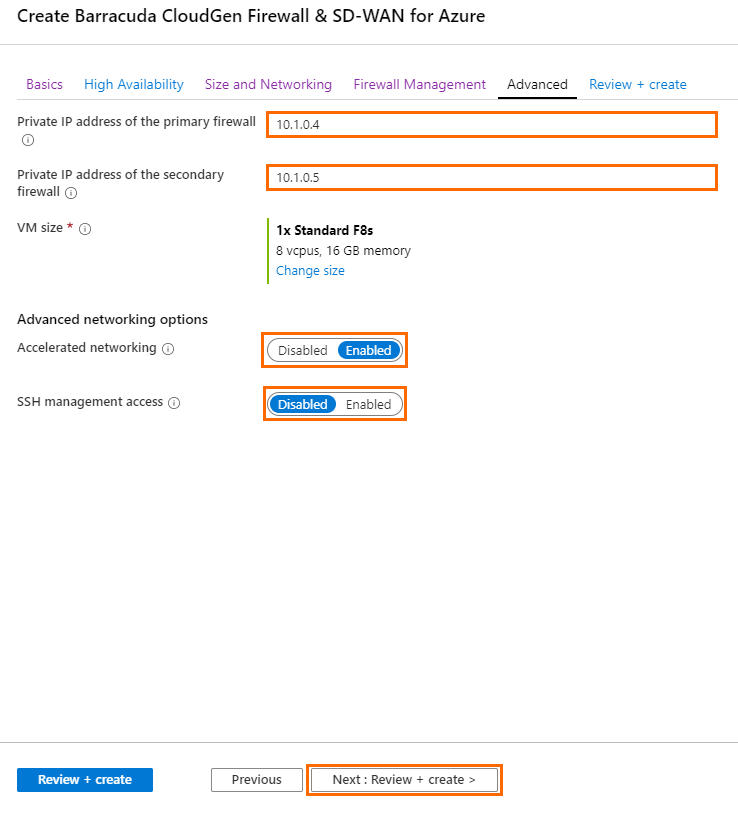
- In the Advanced blade, configure the following settings.
- Private IP address of the primary firewall – Enter a static private IP address from the subnet the firewalls are deployed to. The first four and the last IP addresses in the subnet are reserved by Azure.
- Private IP address of the secondary firewall – Enter a static private IP address from the subnet the firewalls are deployed to. The first four and the last IP addresses in the subnet are reserved by Azure.
- VM size – If not already configured, change the virtual machine size.
Accelerated networking – Enable or disable Azure accelerated networking if the size of your virtual machine meets the requirements of Microsoft.
- SSH management access – Select Enabled to allow SSH access to the Barracuda CloudGen Firewall, and enter the SSH public key.
- Click Next : Review + create >.
Step 6. Summary
- The basic configuration of the Barracuda CloudGen Firewall is validated, and if no errors are found, the virtual machine is ready for provisioning. For automated deployments, you can download the configuration template.
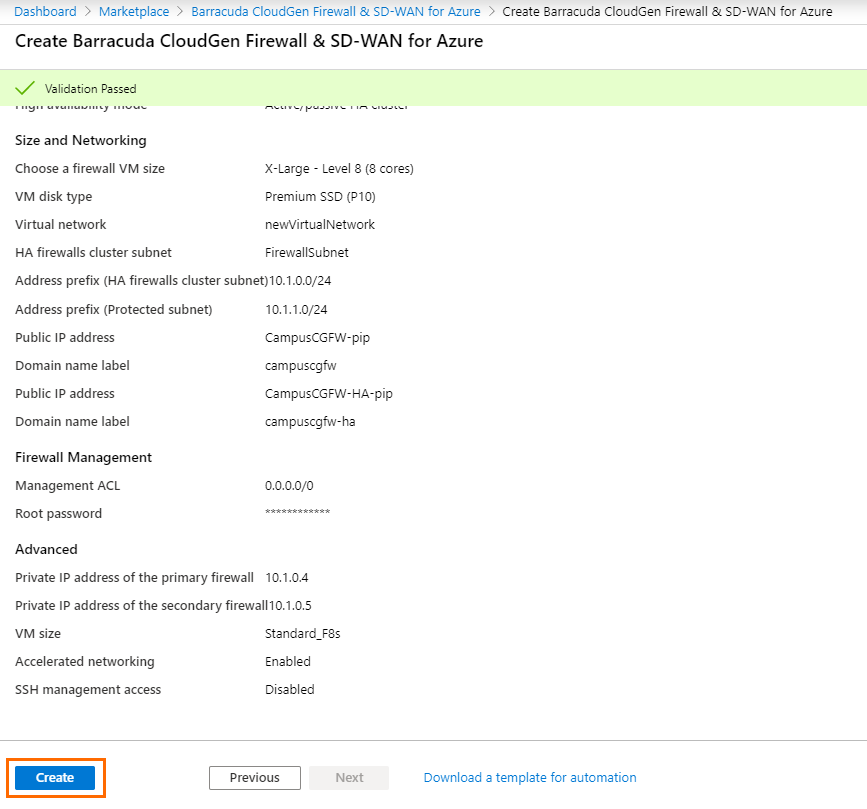
- Click Create.
- Wait for Microsoft Azure to finish the deployment of your firewalls.
- Go to Virtual machines, click on the primary firewall VM, and locate the Public IP address used to connect to your firewall. Use this IP address to connect to your firewall via Barracuda Firewall Admin. The username is root and the password is the password you configured in Step 4.
Configure Cloud Integration
Configure the Cloud Integration to automatically rewrite the Azure routing table in case of a failover to use the active firewall.
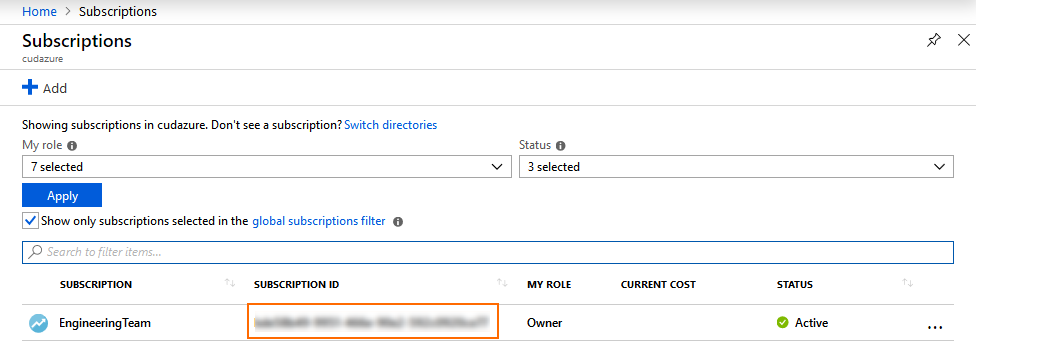
Step 1. Get Your Subscription ID
- Log into the Azure portal: https://portal.azure.com
- In the left menu, click Subscriptions.
- Copy the Subscription ID in the Subscription ID column.
Step 2. Enable Managed Identities for Azure Resources
- Go to the Azure portal: https://portal.azure.com.
- Go to the resource group containing your high availability cluster.
- Open the virtual machine of your primary firewall.
- Click Identity.
- Set System assigned to On.
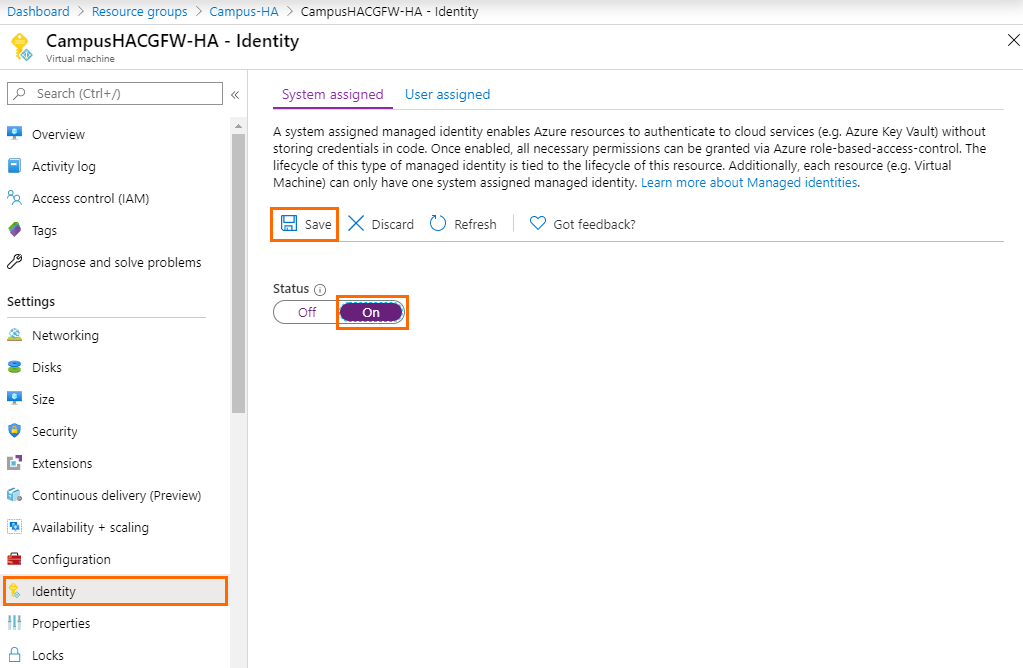
- Click Save.
- Open the virtual machine of your secondary firewall.
- Click Identity.
- Set System assigned to On.
- Click Save.
- Go to the resource group containing your high availability cluster.
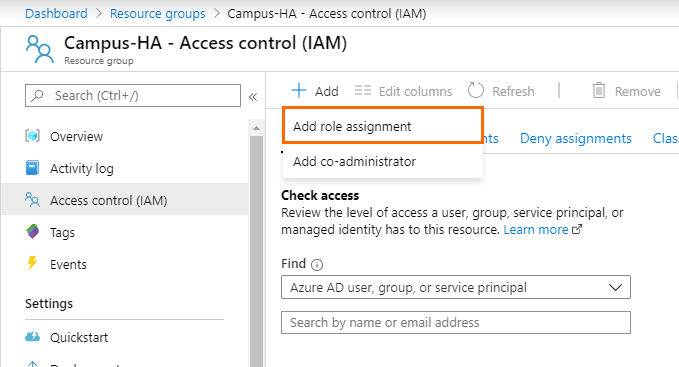
- Click Access control (IAM).
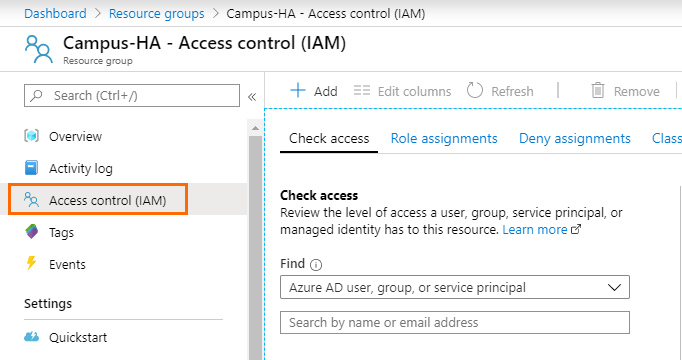
- Click +Add and click Add role assignment.
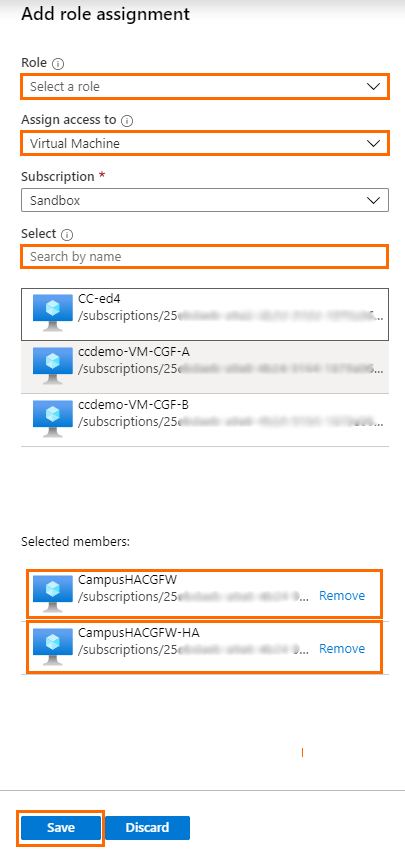
- For Role, select Contributor from the list.
- For Assign access to, select Virtual Machine from the list.
- For Select, enter the name of the primary firewall and click on the corresponding entry.
- Click in the Select field again.
- Enter the name of the secondary firewall, and click on the corresponding entry.
- Click Save.
Step 3. Configure Cloud Integration on Your CloudGen Firewall
- Locate the public IP address of the virtual machine of your primary firewall in Azure.
- Log into the primary firewall of your high availability cluster with user root. For the password, see Step 4 of the deployment.
- Go to CONFIGURATION > Configuration Tree > Advanced Configuration > Cloud Integration.
- On the left side, click Azure Networking.
- Click Lock.
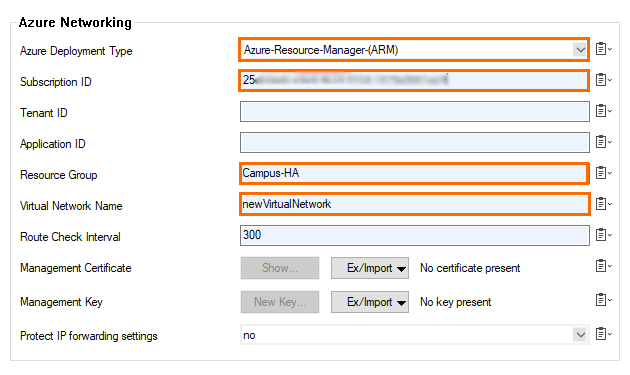
- In the Azure Networking section, specify values for the following:
- Azure Deployment Type – Select Azure Resource-Manager-(ARM) from the drop-down menu.
- Subscription ID – Enter your subscription ID.
- Resource Group – Enter the name of the resource group containing the high availability cluster.
- Virtual Network – Enter the name of the virtual network the high availability cluster is attached to.
- Click Send Changes and Activate.
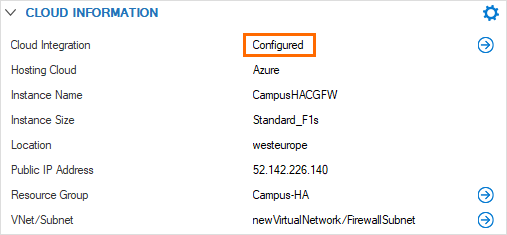
- (Optional) Go to DASHBOARD and verify that Cloud Integration is Configured in the CLOUD INFORMATION section.
Next Steps
Configure a user-defined routing table for the backend VMs to send traffic through the firewall.
