Microsoft Active Directory (MSAD) is a directory service that allows authentication and authorization of network users. On the Barracuda CloudGen Firewall you can configure MSAD as an external authentication scheme. MSAD is included with all Windows Server operating systems as of the Windows 2000 Server. For MSAD authentication, you can also configure the Barracuda DC Agent, which allows transparent authentication monitoring with the Barracuda CloudGen Firewall and Microsoft® domain controllers. The MSAD authentication service can handle a maximum of 20 AD servers at a time. MSAD authentication fetches the user principal name (UPN) and returns it to the USER attribute field during authentication. The UPN is then applied to filtering and firewall rules. For attributes to match, e.g., in VPN client-to-site filtering, the UPN format in AD must be user@domain.com.
Before You Begin
Deactivate Kerberos Pre-authentication
If MSAD is running in native mode on a Windows 2003 Server domain, you must deactivate Kerberos pre-authentication for each user.
Gather Group Information
To use services such URL Filter, VPN, or Firewall Authentication and Guest Access, you might need to gather group information. The distinguished name (DN) containing the group information is needed for external authentication using MSAD and LDAP (see also How to Configure LDAP Authentication). To gather group information from MSAD:
- Go to My Network Places > Search Active Directory.
- Select the searching domain.
- Enter the name of the user you are searching for and click Find Now.
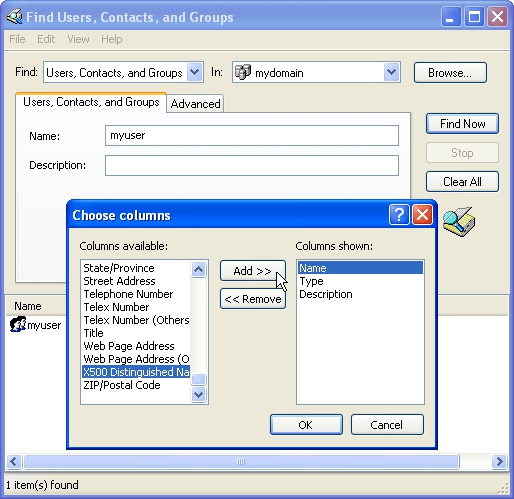
- After you have found the user, add the X500 Distinguished Name column.
- Select View > Choose columns.
- Select X500 Distinguished Name.
- Click Add.
 | 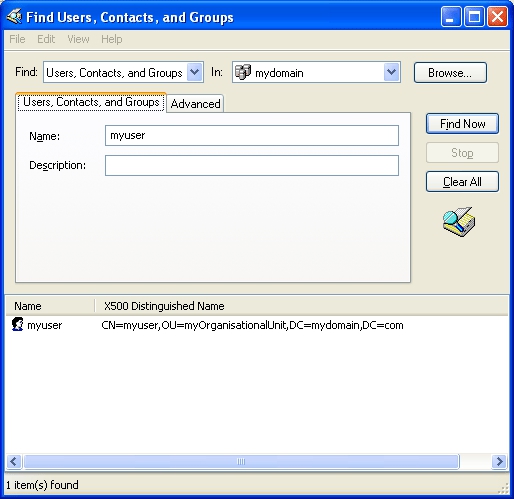 |
The DN is displayed in the search results.
Delegate a Service User
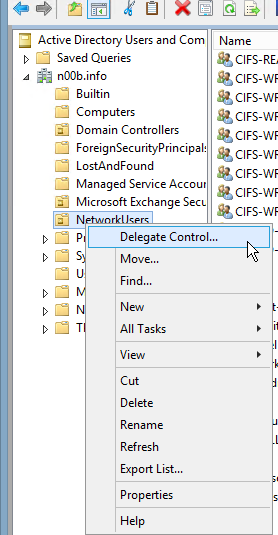
You must delegate the 'serviceuser' to Read all user information in the specific OU:
- Select the OU: in this example NetworkUsers.
- Select Delegate Control.
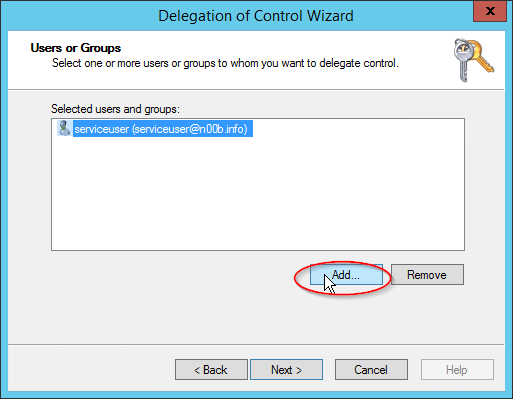
- Add your 'serviceuser'.
- Click Next.
- Select Read all user information.
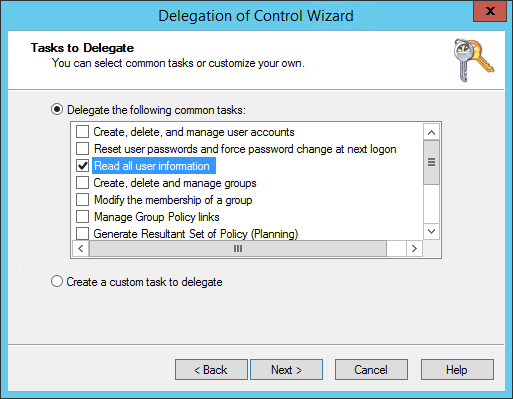
- Click Next.
- Click Finish.
Configure MSAD Authentication
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Authentication Service.
- In the left navigation pane, select MSAD Authentication.
- Click Lock.
- Enable MS Active Directory as external directory service.
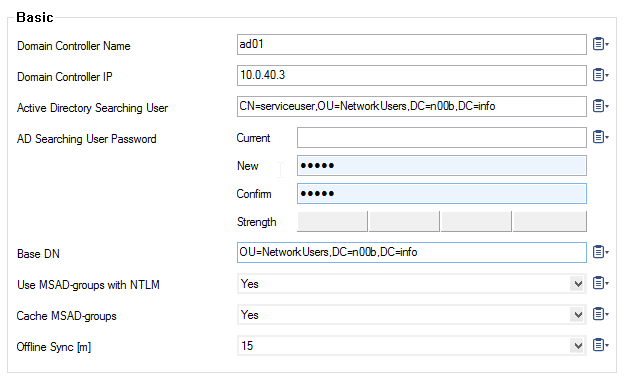
- In the Basic table, add an entry for the domain controller.
- (optional) In case you want to provide MSAD-group access information to the HTTP proxy via MSCHAP, set Use MSAD-groups with NTLM to Yes in the Basic window.
- Enter the name and IP address or hostname of the primary domain controller, without the domain suffix. Hostnames must be DNS-resolvable.
- In the Active Directory Searching User field, enter the Distinguished Name (DN) of the 'serviceuser' (a user with permission to search the Active Directory and to view group information). For example:
CN=username,OU=development,DC=domain,DC=localor:DOMAIN\usernameor: username@domain.local In the Active Directory Searching User Password field, enter a password for the user with permission to search the Active Directory.
In the Base DN field, specify where to search for user information. Define the Base DN as specific as possible in order to increase the speed of the lookup and avoid timeouts.
- When using NTLM authentication, enable Use MSAD-groups with NTLM to periodically synchronize user groups from MSAD and let the Barracuda CloudGen Firewall handle them offline.
When using MSAD-groups with NTLM, enable Cache MSAD-groups to reduce network traffic and load on the MSAD server.
- Use Offline Sync [m] to specify the interval of the synchronization in minutes of the offline database of the MSAD-groups, if enabled.
- With Timeout [s] you can specify the timeout in seconds for requests to the MASD server.
To search additional LDAP attributes for mail addresses, enter a comma-separated list of LDAP attributes in the Additional Mail Fields.
Select Use SSL when establishing the connection to the LDAP directory using SSL.
- Select Follow referrals to search the MSAD global catalog and follow LDAP referrals. It is recommended to enable this setting.
- Specify Max. Hops for Referrals to define the maximum number of LDAP referrals to be used.
- Enable Check Domain Name to let your CloudGen Firewall additionally check the domain name of the user who tries to authenticate. This setting is recommended if you have more than one domain in your network.
Set Add User-DN as Group name to yes if you want to add the user distinguished name to the list of groups.
- Click OK.
- If group information is queried from a different authentication scheme, select the scheme from the User Info Helper Scheme list.
In the Group Filter Patterns table, you can add patterns to filter group information from the directory service.
Example:- Group Filter Pattern:
*SSL* - User01:
CN=foo, OU=bar, DC=foo-bar, DC=foo - User02:
CN=SSL VPN, DC=foo-bar, DC=foo
In this example, User01 does not have the
*SSL*pattern in its group membership string and will not match in group-based limitations.- Group Filter Pattern:
- Click OK.
- Click Send Changes and Activate.
MSAD Authentication through the Remote Management Tunnel
To allow remote CloudGen Firewalls to connect to the authentication server through the remote management tunnel, you must activate the outbound BOX-AUTH-MGMT-NAT host firewall rule. Per default this rule is disabled.
MSAD Authentication against Microsoft Entra ID
MSAD authentication against Microsoft Entra ID is possible when Entra ID is configured to use secure LDAP. Use the Active Directory Searching User and Base DN as supplied by Microsoft.
For more information, see the Microsoft article Entra ID - Configure Secure LDAP.
